If there is no transportation, there is no food, medicine or basic supplies….what country is ready to deal with this?
British cities would be uninhabitable within days and the country is only a few meals from anarchy if the National Grid was taken down in a cyber attack or solar storm, disaster and security experts have warned.
Modern life is so reliant on electricity that a prolonged blackout would quickly lead to a loss of water, fuel, banking, transport and communications that would leave the country “in the Stone Age”.
The warning comes weeks after the Defence Secretary, Gavin Williamson, said Russia had been spying on the UK’s energy infrastructure and could cause “thousands and thousands and thousands” of deaths if it crippled the power supply.
***
The U.S. government has just released an important cybersecurity alert that confirms Russian government cyberattacks targeting energy and other critical infrastructure sectors in the United States.
While there has recently been a significant rise in cyberattacks in these industries, up to now we’ve only been able to speculate on who the actors are, or what their motives may be. In this case the threat actor and their strategic intent has been clearly confirmed, something the U.S. government rarely does publicly.
In addition, the US-CERT alert provides descriptions of each stage of the attack, detailed indicators of compromise (IOCs), and a long list of detection and prevention measures. Many of the attack tactics are like Dragonfly 2.0, so much so that one might call this an expanded playbook for Dragonfly. The Nozomi Networks solution ships today with an analysis toolkit that identifies the presence of Dragonfly 2.0 IOCs.
This article is intended to help you gain perspective on this recent alert, provide additional guidance on what security measures to take, and describe how the Nozomi Networks solution can help.

U.S. energy facilities, like this one, are one of the critical infrastructure targets of the Russian cyberattacks.
Multi-Stage Campaigns Provide Opportunities for Early Detection
The US-CERT alert characterizes this attack as a multi-stage cyber intrusion campaign where Russian cyber actors conducted spear phishing and gained remote access into targeted industrial networks. After obtaining access, the threat vectors conducted network reconnaissance, moved laterally, and collected information pertaining to Industrial Control Systems (ICS).
This pattern of behavior is typical of APTs (Advanced Persistent Threats). APTs occur over an extended period, meaning there is an opportunity to detect and stop them before damage is done. With the right technology monitoring the industrial network, it is much harder for them to go unobserved before their final attack.
In this case the Russian cyberattacks started by infecting staging targets, which are peripheral organizations, such as trusted third-party suppliers, as pivot points for attacking the final intended targets.
The attackers used a multitude of tactics involving information relevant to industrial control professionals for initial infection of the staging targets. Examples include:
- Altering trade publication websites
- Sending emails containing resumes for ICS personnel as infected Microsoft Word attachments
- Analyzing publicly available photos that inadvertently contained information about industrial systems
The credentials of staging targets’ staff were in turn used to send spear phishing emails to the staff of the intended targets. They received malicious .docx files, which communicated with a command and control (C2) server to steal their credentials.
The SMB (Server Message Block) network protocol was used throughout the spear phishing phases to communicate with external servers, as was described for the Dragonfly 2.0 attacks.This is a distinctive tactic. SMB is usually only used to communicate within LANs, not for outbound communications. Now that this is known, asset owners should ensure their firewalls are locked down for outbound service restrictions.
The credentials of the intended targets were used to access victim’s networks. From there, the malware established multiple local administrator accounts, each with a specific purpose. The goals ranged from creation of additional accounts to cleanup activity. For the report, click here.
***
What Is Known
Forensic analysis shows that the threat actors sought information on network and organizational design and control system capabilities within the organization. In one instance, the report says, the threat actors downloaded a small photo from a publicly accessible human resource page, which, when expanded, was a high-resolution photo that displayed control systems equipment models and status information in the background. The threat actors also compromised third-party suppliers to download source code for several intended targets’ websites. They also attempted to remotely access corporate web-based email and virtual private network (VPN) connections.
Once inside the intended target’s network, the threat actors used privileged credentials to access domain controllers via remote desktop protocols (RDP) and then used the batch scripts to enumerate hosts and users, as well as to capture screenshots of systems across the network.
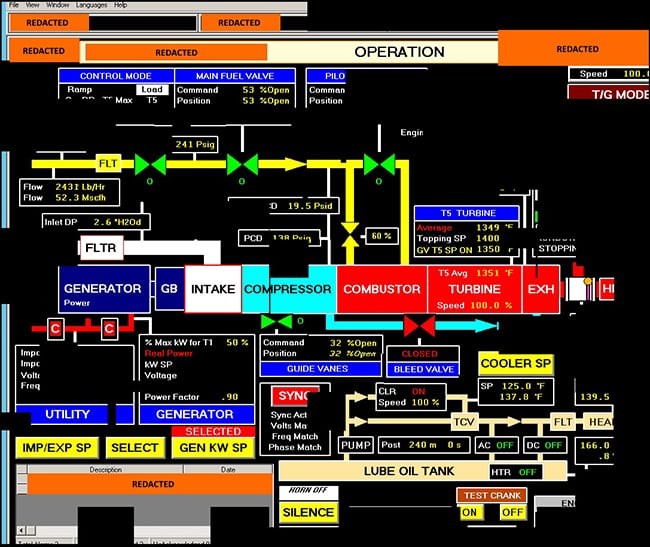
The threat is inside. US-CERT on March 15 warned that threat actors associated with the Russian government had infiltrated ICS and SCADA systems at power plants using a variety of tactics. This image is a DHS reconstruction of a screenshot fragment of a human machine interface (HMI) that the threat actors accessed. Source: US-CERT
Along with publishing an extensive list of indicators of compromise, the DHS and FBI recommended that network administrators review IP addresses, domain names, file hashes, network signatures, and a consolidated set of YARA rules for malware associated with the intrusion authored by the National Cybersecurity and Communications Integration Center. YARA is an open-source and multiplatform tool that provides a mechanism to exploit code similarities between malware samples within a family.

