Once again, John Kerry’s attempt to restart the peace talks between Israel and Palestine failed again yesterday with no progress. Talks are slated to go another round in June, all of this is a fool’s errand.
While Kerry is on his way to log as many travel miles as Hillary flew during her term at SecState, Kerry has abandoned concentration on several fronts least of which is Iran’s nuclear program. Rouhani is moving completely unchecked and quite aggressively against the United States with regard to declaring victory in Syria, his nuclear weapons program and signing deals all over the globe. Diplomatic efforts by Barack Obama and John Kerry are folly. Yet, what else is Iran doing that should terrify America? One victory Iran is having is their clandestine cyber war, titled Saffron Rose.
A group of Iranian hackers have allegedly been targeting American defense contractors, and attempting to quell dissent in Iran itself, in an elaborate and technically advanced campaign![]() that American security researchers call “Operation Saffron Rose.” The attacks began in October 2013 and continued until at least April 8, according to Milpitas, California-based security company FireEye, which documented the operation in a report released yesterday (May 13).
that American security researchers call “Operation Saffron Rose.” The attacks began in October 2013 and continued until at least April 8, according to Milpitas, California-based security company FireEye, which documented the operation in a report released yesterday (May 13).
FireEye suspects that the group behind Saffron Rose is Ajax Security Team, whose members are thought to have conducted politically-motivated website defacements for several years. The group’s “graduation” from vandalism to espionage shows that Iranian actors in the cyber attack space are becoming more sophisticated, FireEye says.
The “proxy software” was, of course, malicious.
According to FireEye, Ajax Security Team often uses a type of spyware that FireEye calls “Stealer.” Stealer often arrives as a Trojan horse, secretly bundled into other software such as proxies or VPN clients![]() .
.
Once a target installs an infected program, Stealer runs a program called IntelRS.exe, which snoops on infected computers in a variety of ways. These methods include keylogging, taking screenshots, gathering system information (IP addresses, usernames, hostnames, open ports, installed applications), collecting email and instant messaging information, and collecting browser-based information such as login credentials, browsing history, cookies and bookmarks.
Stealer encrypts the data it gathers, then sends it to a command-and-control server![]() . FireEye said one such server contained information on 77 individuals targeted in Operation Saffron Rose.
. FireEye said one such server contained information on 77 individuals targeted in Operation Saffron Rose.
Many of the programs used to conceal Stealer are anti-censorship programs such as Psiphon, which don’t seem to be targeted toward the American defense companies that have been Ajax Security Team’s most recent targets. (One of Psiphon’s lead developers at the University of Toronto was Nart Villeneuve, who went on to become a malware researcher and is lead author of FireEye’s Saffron Rose report.)
The anti-censorship programs often appeared to be set to Iran Standard Time (which is uniquely three and a half hours ahead of Greenwich Mean Time) and had a Persian-language setting. FireEye believes that Ajax Security Team may also be targeting Iranians who use anti-censorship programs to dodge Iran’s strict Internet regulations.
Interestingly, FireEye’s report observed that Ajax Security Team has not been spotted using zero-day exploits, or secret vulnerabilities in program code, although the team has been seen using publicly known and unpatched exploits in its cybervandalism activities.
“It is unclear if they or other Iranian actors are capable of producing or acquiring exploit code,” FireEye’s researchers wrote.
FireEye’s report compared Saffron Rose to Shamoon, a highly destructive espionage campaign that targeted the Saudi Arabian oil company Saudi Aramco in August 2012. The Shamoon spyware gathered company data from infected computers, then disabled them by overwriting their master boot records, which PCs need to start up. Some experts suspected Shamoon came from Iran, but nothing has been proven.
The relationship between Ajax Security Team and the Iranian government is unclear, but FireEye said that Saffron Rose is proof that Iran’s online capabilities are becoming more sophisticated.
“There is increasing evidence to suggest that the hacker community in Iran is engaged in a transition from politically motivated defacements and denial-of-service attacks to cyberespionage activities,” its report concluded.
As Iran continues unchecked, it is important to know what else Iran is doing.
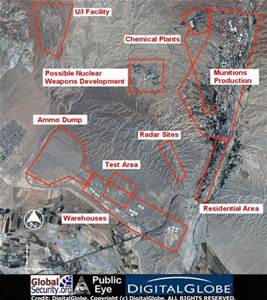
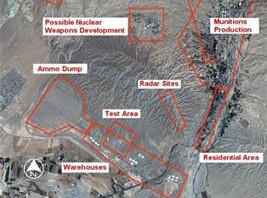
Washington-based analysts say Iran has pressed ahead with operations at a military base suspected to have hosted nuclear weapon-related experiments.
An April 25 satellite image of Iran’s Parchin installation suggests the nation, since January, has moved “possible building material and debris” near a building that the International Atomic Energy Agency has sought unsuccessfully for more than two years to visit, according to a Monday assessment by the Institute for Science and International Security. The U.N. nuclear watchdog believes the structure may once have been capable of hosting explosion tests relevant to nuclear-arms development.
“Two trucks or containers have been removed from the area surrounding the suspected high-explosives test building, while a larger object, possibly a truck or large container, appears slightly north of it,” ISIS analysts David Albright and Serena Kelleher-Vergantini said in their report.
Iran, which insists that its atomic ambitions are strictly peaceful, began altering the Parchin facility weeks after IAEA officials began seeking access to the location, the independent experts said.
The nation last year undertook a months-long pause in activities at the site, but a January image analysis revealed an apparent resumption of operations there, the analysis says.
This week’s findings came as Iran launched a new round of multilateral talks aimed at defusing international fears over Tehran’s suspected nuclear-arms aspirations.
“By continuing to modify the site and denying the IAEA access, Iran is reducing the chances of reaching a comprehensive solution by the initial deadline of July 20,” when an interim nuclear agreement with major powers is scheduled to expire, the ISIS report says.
Certain specialists have questioned the U.N. agency’s rationale for pressing to visit the Parchin compound. The evidence prompting those requests — intelligence gathered and furnished to the agency by IAEA member governments — remains confidential.