Anyone ever see that Jack Ryan movie ‘Shadow Recruit’? It is playing out in a more nefarious form in real time.
May 2016: Director of National Intelligence James Clapper said today that presidential campaigns are a target for cyber intruders and that this political season has already seen some attempted hacks.
“We have already had some indications of that,” he said in response to a question about campaign website hacking, after speaking at the Center for Bipartisan Policy in Washington, D.C.
“I anticipate as the campaigns intensify, we will probably have more of it,” he added. He did not provide specifics about any attacks, but it has been reported that some hacking groups, such as Anonymous, have threatened to launch “total war” against Donald Trump‘s presidential campaign. Read more from ABC here.
Related reading: Clinton Foundation Said to Be Breached by Russian Hackers
**** So –>> Director of National Intelligence James Clapper says the FBI is helping campaigns tighten up to protect against the threat and how has that worked out so far?
*****
Via ThreatConnect: In our initial Guccifer 2.0 analysis, ThreatConnect highlighted technical and non-technical inconsistencies in the purported DNC hacker’s story as well as a curious theme of French “connections” surrounding various Guccifer 2.0 interactions with the media. We called out these connections as they overlapped, albeit minimally, with FANCY BEAR infrastructure identified in CrowdStrike’s DNC report.
Now, after further investigation, we can confirm that Guccifer 2.0 is using the Russia-based Elite VPN service to communicate and leak documents directly with the media. We reached this conclusion by analyzing the infrastructure associated with an email exchange with Guccifer 2.0 shared with ThreatConnect by Vocativ’s Senior Privacy and Security reporter Kevin Collier. This discovery strengthens our ongoing assessment that Guccifer 2.0 is a Russian propaganda effort and not an independent actor.
Analyzing the Headers from Guccifer 2.0 Emails
On June 21, 2016, TheSmokingGun reported they communicated with Guccifer 2.0 via a French AOL account. We examined the French language settings observed in Guccifer 2.0’s Twitter metadata as well as a pattern of Twitter follows that suggested Guccifer 2.0’s account was created from a French IP address. We hypothesized at the time that Guccifer 2.0 might be using French infrastructure to interact with the media.
During the Email Import process ThreatConnect analyzes an email message header and highlights indicators of interest with a color code that reveals if the indicators already exist within the platform. This helps overburdened eyes or greenhorn analysts quickly understand what they are seeing. At the same time ThreatConnect excludes legitimate or benign details that are not of value to our investigation.
As we can see here within ThreatConnect, Guccifer 2.0’s AOL email message reveals the originating IP address as 95.130.15[.]34 (DigiCube SaS – France). This is the IP address of the host which authenticated into AOL’s web user interface and sent the email. We can also tell this IP was not spoofed because the metadata was added by AOL when sent from within their infrastructure with appropriate DomainKeys Identified Mail (DKIM) configurations.
The fact that Guccifer 2.0 is indeed leveraging a French AOL account stands out from a technical perspective. Very few hackers with Guccifer 2.0’s self-acclaimed skills would use a free webmail service that would give away a useful indicator like the originating IP address. Most seasoned security professionals will be familiar with email providers that are more likely to cooperate with law enforcement and how much metadata a provider might reveal about their users. Taken together with inconsistencies in Guccifer 2.0’s remarks that make his technical claims sound implausible, this detail makes us think the individual(s) operating the AOL account are not really hackers or even that technically savvy. Instead, propagandist or public relations individuals who are interacting with journalists.
Drilling into Guccifer 2.0 Infrastructure: Picture of a VPN Starts to Emerge
As we focused in on IP Address 95.130.15[.]34 we queried public sources such as Shodan as well as Censys to discover what services might be enabled on this host. The goal of this was to better understand if this infrastructure is owned and operated, leased or co-opted by Guccifer 2.0 and how the infrastructure might be used to create space between an originating “source” network and investigators, or curious journalists.
According to Shodan, OpenSSH (TCP/22), DNS (UDP/53) and Point-to-Point Tunneling Protocol (PPTP) (TCP/1723) services have been enabled on this host. Secure shell (SSH) and point-to-point tunneling protocol services strongly suggest a VPN and/or a proxy, both of which would allow the Guccifer 2.0 persona to put distance between his originating network and those with whom he is communicating.
The SSH fingerprint can be used as an identifier, linking other IP addresses that use the same SSH encryption key. The SSH fingerprint for 95.130.15[.]34 (DigiCube SaS – France) is Fingerprint: 80:19:eb:c8:80:a1:c6:ea:ea:37:ba:c0:26:c6:7f:61. Searching for other servers that share this fingerprint at the time of writing, we discovered six additional IP Addresses over the course of our research (95.130.9[.]198; 95.130.15[.]36; 95.130.15[.]37; 95.130.15[.]38; 95.130.15[.]40; 95.130.15[.]41).
Each IP address falls within the 95.130.8.0/21 network range. This range is assigned to Digicube SAS, a French hosting provider which is assigned the Autonomous System AS196689. An IP address is analogous to the apartment numbers in an apartment building. The entire building is owned and operated by AS196689, but certain IP addresses may be let out to other companies and organizations.
The fact that Guccifer 2.0 would use a proxy service is not surprising, and our first stop was to check with various TOR proxy registration sites. None of these seven IP addresses are part of reported TOR infrastructure from what we were able to uncover. Read the full comprehensive detailed cyber investigation as published here by ThreatConnect.
*****
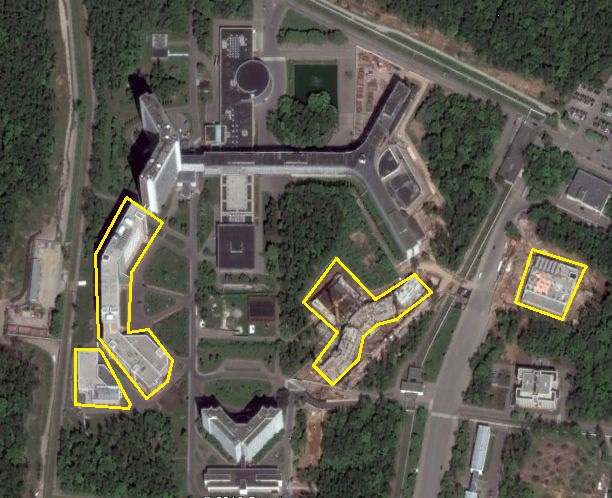
Meanwhile: FAS: The headquarters complex of the Foreign Intelligence Service (SVR) of the Russian Federation has expanded dramatically over the past decade, a review of open source imagery reveals.
Since 2007, several large new buildings have been added to SVR headquarters, increasing its floor space by a factor of two or more. Nearby parking capacity appears to have quadrupled, more or less.
The compilation of open source imagery was prepared by Allen Thomson. See Expansion of Russian Foreign Intelligence Service HQ (SVR; Former KGB First Main Directorate) Between 2007 and 2016, as of July 11, 2016.
Whether the expansion of SVR headquarters corresponds to changes in the Service’s mission, organizational structure or budget could not immediately be learned.
Russian journalist and author Andrei Soldatov, who runs the Agentura.ru website on Russian security services, noted that the expansion “coincides with the appointment of the current SVR director, Mikhail Fradkov, in 2007.” He recalled that when President Putin introduced Fradkov to Service personnel, he said that the SVR should endeavor to help Russian corporations abroad, perhaps indicating a new mission emphasis.