As President Trump meets with Xi Jinping of China at Mar A Lago, perhaps he should point to these two conditions in earnest.
By Lee Yong-soo: (the item posted below is copyright protected)
Chosun: One government source said Defense Ministry investigators questioned around 40 people over the hacking attack and it appears that part of the masterplan, dubbed OPLAN 5027, “leaked.” A Defense Ministry source said the hackers accessed reports containing portions of the plan, not the entire document.
Defense Minister Han Min-koo and other military officials last year downplayed the seriousness of the hacking attack, saying that only a small number of sensitive military secrets leaked out.
OPLAN 5027 was first drawn up in 1978, when the South Korea-U.S. Combined Forces Command was established, and updated every two years since 1994. It includes troop deployment plans, key North Korean targets, strategies and military control of facilities in the North.
A military official said “discussions are still taking place” whether the plan has to be overhauled now the North has seen chunks of it.
The ministry found out about the leak while investigating a new computer virus in September that attacked the vaccine server at the military cyber command.
Investigators discovered that the Defense Ministry’s Internet and Intranet servers were infected with the same malware, affecting the minister’s own computer and around 2,500 computers with Internet access and 700 connected to the Intranet.
At the time, the ministry said only that hackers accessed “some military information, including sensitive information” and that North Korea appears to be responsible.
The hackers tried to attack the main server of the Defense Integrated Data Center, which serves as the cyber nerve center of South Korea’s defense system.
***
China’s Information Warriors Are Growing More Disciplined, Say US Cyber Leaders
And some U.S. cyber leaders worry that the American military’s approach is too reactive and defensive.
When President Trump meets this week with his Chinese counterpart, President Xi Jinping, he’ll be engaging with a leader who commands an increasingly disciplined and persistent information-warfare force.
In December 2015, the Chinese military stood up a Strategic Support Force as part of a larger series of reforms. Essentially a Chinese version of U.S. Cyber Command, the new force focuses on war in the electromagnetic spectrum, space, and cyberspace. “All these are the new fields that determine whether the PLA can win in the future battlefield,” Chinese officials told state media.
The new force’s key focus is building capabilities to disrupt U.S. military operations, according to Martin Libicki, who leads cybersecurity studies at the U.S. Naval Academy. In January China announced that the country will develop the world’s first exascale super computer by the end of the year.
The move follows years of steady and incremental improvements in information operations, Vice Adm. Tim White, commander of the U.S. Cyber National Mission Force, said Tuesday at the Navy League’s Sea-Air-Space conference. “They are building what I would call campaigns. They are being very thoughtful about it and being purposeful in their approach and there is some design that they are organizing themselves,” he said of adversarial nations such as China but also Russia. “It’s not just a single mission, point of time, or place. It’s interwoven together to achieve a national purpose.”
By contrast, White worries the U.S. military is thinking too defensively. He believes the Pentagon should work toward a more disciplined, consistent response, and shift from a “broadly reactive” posture “to something we are doing something as a result of our own campaign and planning efforts.”
“They’re on the field and we are figuring out how to get on that field,” White said. “What nations are doing in this space, it’s more coordinated. It’s more interoperable from their perspective. It’s more structured and it’s more integrated.”
Industrial espionage from China appears to have waned since Barack Obama and Xi signed an agreement in September 2015. But attacks have not vanished entirely. Between March and May of last year, Chinese hackers deployed a backdoor into a government services company, stole important credentials, and attempted to gain access to U.S. military secrets, according to the FireEye cyber security group.
Without speaking specifically about that incident, Vice Adm. Jan Tighe, deputy chief of naval operations for information warfare and the director of naval intelligence, said that many of the attacks, pings, intrusion attempts and probe “appear to be part of deliberate campaigns” of adversarial nation-state activities against Western targets.
How to fight them off? The head of U.S. Cyber Command, Adm. Michael Rogers, has suggested giving more authority to lower-ranking service personnel. The Navy anticipates that all 40 of the Navy’s cyber mission force teams will reach full operational capability by 2018.
Navy leaders at Sea-Air-Space also said artificial intelligence would play a bigger role in attacking and defending networks.
“I would not say we see new and exquisite DARPA-like capabilities yet,” emerging out of China in terms of artificial intelligence specifically for information warfare, according to White. “But I do think it will be inevitable because you’re not constrained by physics.”
Meanwhile, the U.S. military is exploring the use of cognitive computing and deep learning to better understand network vulnerabilities and predict attacker behavior, according to Vice Adm. Michael Gilday, who leads the Navy’s 10th Fleet and Cyber Command, in accordance with phase II of the Command’s strategic plan to 2020, first laid out in 2015.
Marine Maj. Gen. Lori Reynolds, the commander of Marine Forces Cyber Command also maid a plea to industry. “Anything we can do to automate the intelligence cycle … that’s the right investment,”
But Military cyber leaders say that the United States and China will likely put artificial intelligence to different uses in information warfare. Automation can and probably should take over much defensive work to better keep up with the speed of attacks. But the use of offensive cyber weapons will still involve human decision making for the United States military. They could not guarantee the same of China.
“AI can absolutely tighten your ability to make a decision inside your enemy’s ability to make a decision,” said Gilday.
Defense One asked Gilday and Tighe if they were seeing adversarial nations attempt to automate the use of offensive cyber weapons. They declined to respond.





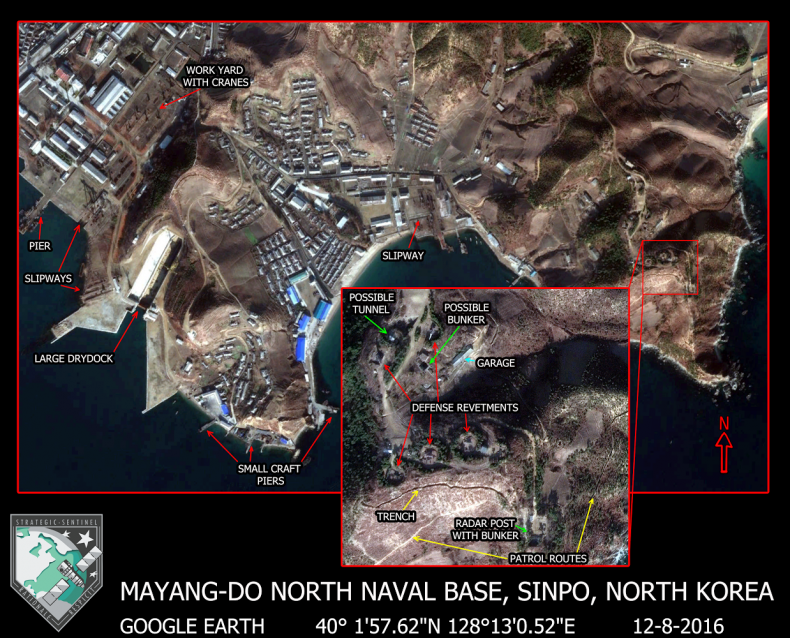
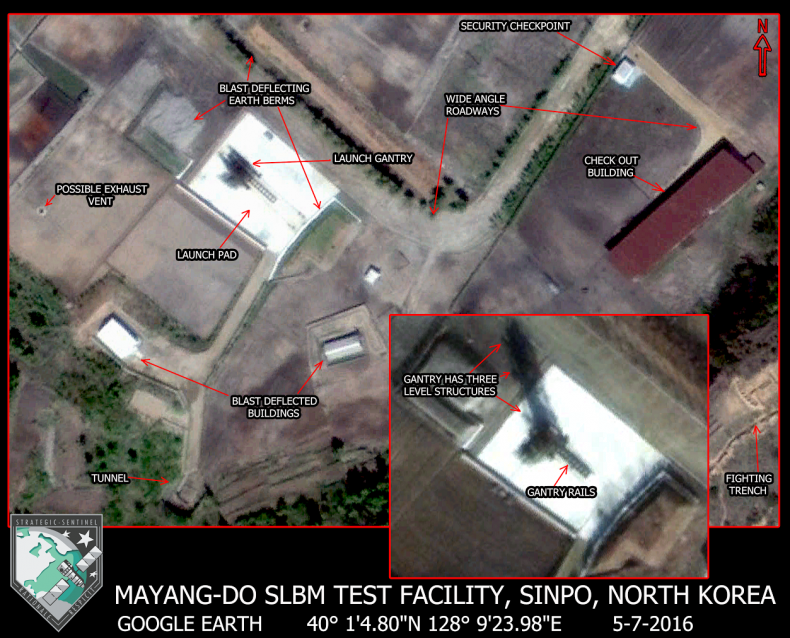
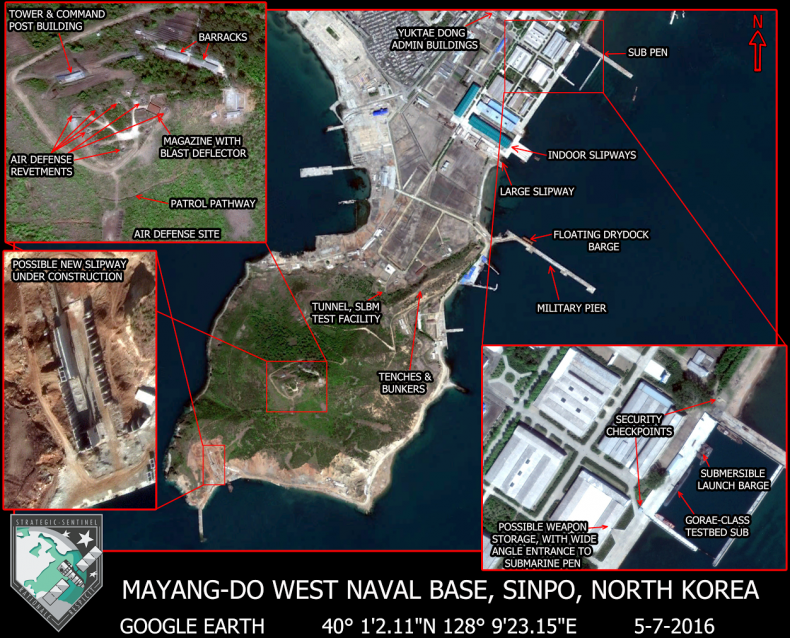



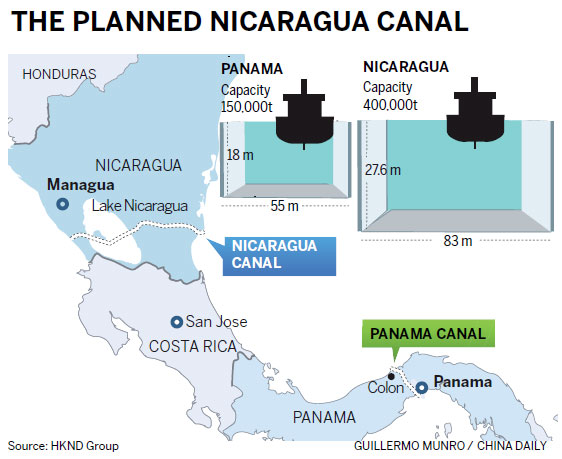
 PBS
PBS BBC
BBC