Charges Announced in Malware Conspiracy
The case appears to have begun in 2011. The DOJ has connected Yakubets and Turashev to cyberattacks as recently as March of this year, according to the indictment. As a part of its investigation, the U.S. in 2010 transmitted a mutual legal assistance treaty request to Russia, and according to Bowdich, the Russian government was “helpful to a point.” Once the hackers were in possession of the bank credentials, they would use “money mules” to funnel the funds into foreign bank accounts. In one case, an employee of a Pennsylvania school district clicked on a graphic in a phishing email sent by Yakubets and Turashev, and the two later attempted to transfer nearly $1 million from the district’s bank account to a bank in Ukraine. The malware was deployed by Yakubets and Turashev infected tens of thousands of computers across North America and Europe, including two banks, a school district, four Pennsylvania companies and a North Carolina firearm manufacturer.
Two Russian Nationals Engaged in Cybercrime Scheme That Infected Tens of Thousands of Computers
The U.S. Department of Justice today joined with the U.S. Department of State and the United Kingdom’s National Crime Agency in charging two Russian nationals with a vast and long-running cybercrime spree that stole from thousands of individuals and organizations in the United States and abroad.
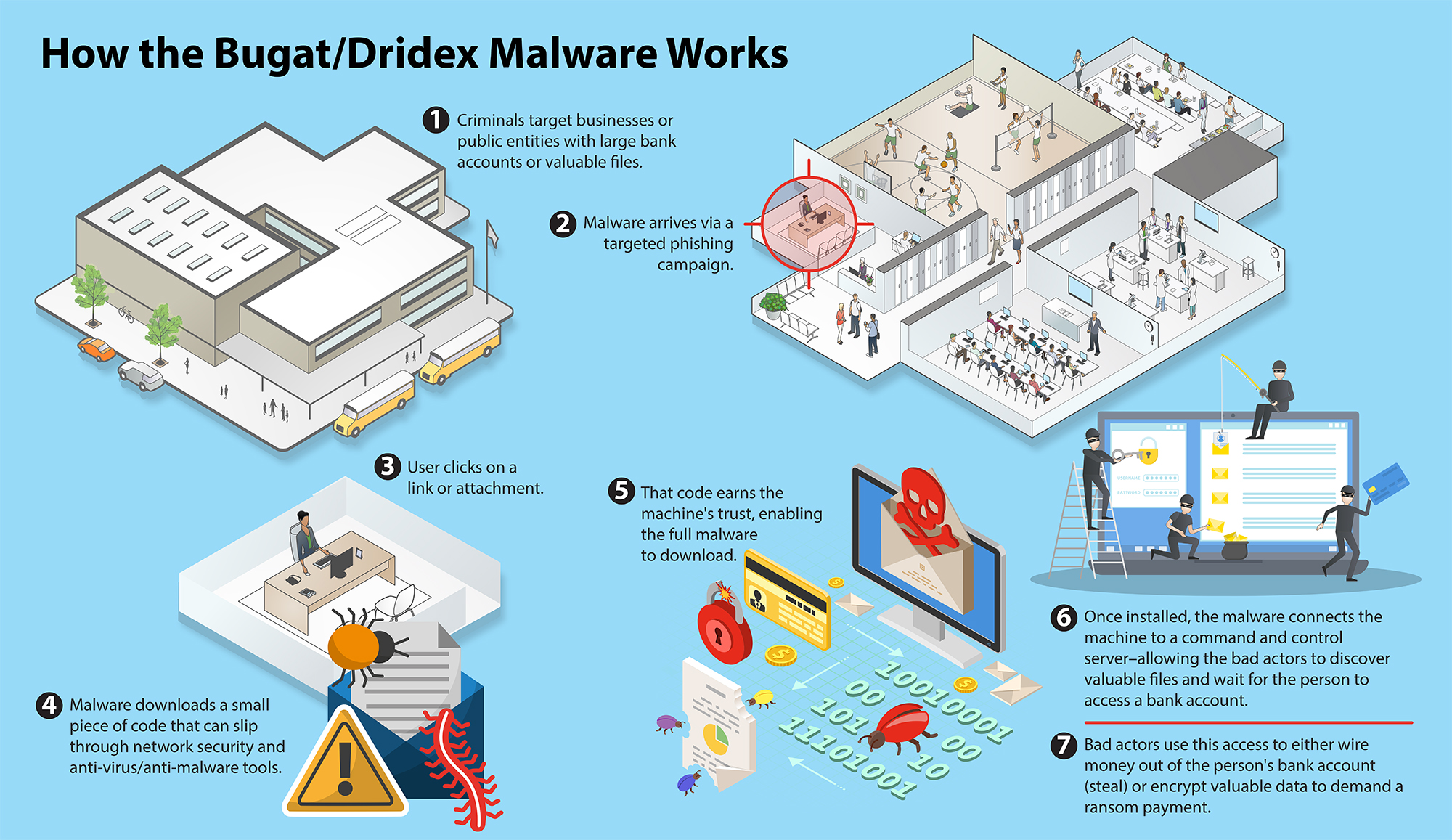
Along with several co-conspirators, Maksim V. Yakubets and Igor Turashev are charged with an effort that infected tens of thousands of computers with a malicious code called Bugat. Once installed, the computer code, also known as Dridex or Cridex, allowed the criminals to steal banking credentials and funnel money directly out of victims’ accounts. The long-running scheme involved a number of different code variants, and later version also installed ransomware on victim computers. The criminals then demanded payment in cryptocurrency for returning vital data or restoring access to critical systems.
“Although their realm is a digital one, this is one of the world’s largest organized crime groups,” said FBI Supervisory Special Agent Adam Lawson of the Major Cyber Crimes Unit. “They are personally getting rich, and new organizations and individuals are being victimized every day.”
Turashev and Yakubets were both indicted in the Western District of Pennsylvania on conspiracy to commit fraud, wire fraud, and bank fraud, among other charges. Yakubets was also tied to charges of conspiracy to commit bank fraud issued in the District of Nebraska after investigators were able to connect him to the indicted moniker “aqua” from that case, which involved another malware variant known as Zeus.
Assisted in some cases by money mules who funneled the stolen funds through U.S. bank accounts before shipping the money overseas, the group stole or extorted tens of millions of dollars from victims. Among those affected was a Pennsylvania school district that saw $999,000 wired out of its accounts and an oil company that lost more than $2 million.
The FBI, in partnership with the State Department’s Transnational Organized Crime Rewards Program, also announced a reward of up to $5 million for information leading to the arrest of Yakubets, who is alleged to be the leader of the scheme. The reward is the largest ever offered for a cyber criminal.
“The actions highlighted today, which represent a continuing trend of cyber-criminal activity emanating from Russian actors, were particularly damaging as they targeted U.S. entities across all sectors and walks of life,” said FBI Deputy Director David Bowdich. “The FBI, with the assistance of private industry and our international and U.S. government partners, is sending a strong message that we will work together to investigate and hold all criminals accountable.”
According to the charges, the co-conspirators distributed the malware through email phishing campaigns. In the early years, these messages were sent in massive, widespread campaigns. More recent attacks have been more strategic—specifically targeting businesses and organizations that have valuable computer systems and access to significant financial resources.
Victims were tricked into opening a document or clicking on a graphic or link that appeared to be from a legitimate source. The link or attachment downloaded the malicious code onto the user’s machine, where it could also spread to any networked computers.
According to FBI Supervisory Special Agent Steven Lampo, this campaign deployed a stealth type of malware designed to avoid detection by antivirus software. “The full program does too much and is too big to avoid detection,” Lampo said. The smaller piece of code, however, can inject itself into the running processes of the machine—beginning a process that allows the full suite of malware to load onto the machine or network. The malware’s creators were constantly creating new variants of the code to avoid antivirus tools.



Pingback: Russian Nationals, Cyber Scheme Infected Thousands Of Computers – Trevor Loudon's New Zeal Blog
Pingback: Russian Nationals, Cyber Scheme Infected Thousands of Computers | NoisyRoom.net