Since 2020 up to now, we in America have suffered through supply chain shortages adding in the matter of ransomware of the Colonial pipeline and now the largest meat processor.
A cyberattack on JBS, the largest meat producer in the world, forced the shutdown of American slaughterhouses, and the closures may be spreading. JBS’s five biggest beef plants in the U.S. halted processing following the weekend attack, equal to one-fifth of all of America’s meat production. Slaughter operations across Australia were also down and one of Canada’s largest beef plants was idled. The prospect of more extensive shutdowns is upending agricultural markets and raising concern about food security as hackers increasingly target critical infrastructure. Livestock futures slumped while pork prices rose. JBS told the White House that the cyberattack, like several previous ransomware assaults, probably originated in Russia.
There are shortages of chicken, chlorine, flour, lumber, computer chips, rare earth minerals like cobalt, rental cars, palm oil, truck drivers, diapers and appliances to list a few. Just imagine the impact of pharmaceuticals via China.
Consider the supply chain dangers if sea shipping was slowed or stopped. Consider the Panama Canal. Why worry?
China is the short answer. And China hates the United States.
In part:
Beijing is currently the second or third largest trading partner with the countries of Central America. Chinese investment in Central America is present in infrastructure projects in Honduras, Nicaragua, Costa Rica, and Panama, and there are plans for further investment in El Salvador and Guatemala. Excluding a contemplated US $50 billion dollars in a canal project in Nicaragua, Chinese investment in Central American infrastructure has totaled approximately US $2 billion thus far.
In a further demonstration of growing ties between the PRC and the countries of Central America, Costa Rica, Panama, and El Salvador have each broken relations with Taiwan to establish diplomatic ties with China. Other countries in the region could soon follow suit.
Panamanian “Panda Bonds”
Sino-Central American investment is being actively pursued in Panama. The country is one of the nations in Latin America that is part of an ambitious program that Beijing has undertaken in the region.
The PRC’s “Silk Road” initiative is a trading and infrastructure plan that aims to connect Asia, Europe, Africa, and Latin America in the same way that the trade route existed during ancient times. In addition to this initiative, further Chinese investment in Central America will result from the Panamanian government’s issuance of US $500 million of “Panda Bonds” in 2018. Panda Bonds are Chinese renminbi-denominated bonds from a non-Chinese issuer that are sold into the Chinese market. Panama issued them in order to take advantage of China’s lower borrowing costs.
***
China’s advancement in Central America dates back to 2007, when Costa Rica became the first Central American country to establish diplomatic relations with Beijing. Since then, economic relations between both countries have developed, helping to promote China’s regional brand. Economically, China has presented itself as an attractive partner. In 2008, China purchased Costa Rican bonds in excess of $300m, offered the country aid worth $130m, and funded the $105m construction of the Estadio Nacional. Meanwhile, on March 2 Chinese state media claimed that China will finance the expansion of a highway connecting Costa Rica and the Caribbean.
Chinese activity in Costa Rica is not limited to finance. In terms of culture, students at the University of Costa Rica can study Chinese and enrol in Chinese cultural programmes. The Chinese government has also promoted the development of Chinatown in San José, Costa Rica’s capital.
What is the solution?
America First should consider mobilizing a real infrastructure operation that would build a new shipping canal that would be technologically more advances and handle larger ships. Where to put it? Nicaragua.
Really? Yes, beat China at their own game and do it fast. The Nicaragua Canal was proposed and backed by Chinese investors and was to be completed in 2020 at an estimated cost of $50 billion.
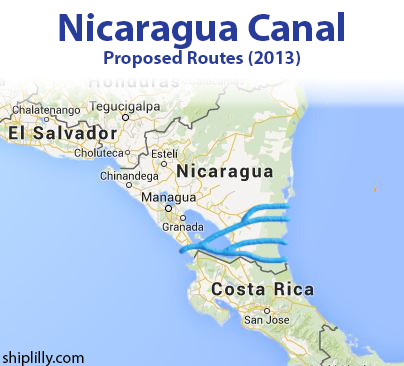
Can you see the natural location for such a shipping canal?
This would also stabilized Latin American countries with economic space and stem the immigration chaos. This time, don’t give the canal away either. The cost? Perhaps a mere $15 billion and these days that is much less than the Biden administration budget has proposed to spend…that pesky $6 trillion.
Has China placed some military operatives in Latin America to protect Chinese investments otherwise known as debt trapping? Seems a legit question especially when the left-leaning think tank Foreign Policy Magazine explains the context just as recently in June of 2020.
Furthermore, Iranian warships are headed to Venezuela with 7 high speed missile boats on board. Additionally, China continues to make plays in the energy sector in Cuba. More debt trapping? Yes.
The America First Policy Institute needs to do some immediate forecasts for national security reasons. The AFPI, which holds a stellar staff list has one particular section called ‘Center for New Frontiers’.
America was not founded to restore an imagined past, but to move its people into a bright and brilliant future. In this first half of the twenty-first century, the United States stands on the precipice of an array of extraordinary possibilities. Dreams from our yesterdays — interplanetary travel, autonomous vehicles, subterranean transit systems, artificial intelligence, 3D printing, organ regeneration, extraordinary new power sources, and beyond — are poised to enter our tomorrows. The America First Policy Institute (AFPI) will research and develop policies that nurture America’s experimental spirit.
A new infrastructure plan such as a shipping canal is just the cure for future supply chain protections and stabilizing countries in our own hemisphere when other key industries and manufacturing must relocate to either or both Central America and back to the United States.






