Here it comes again, a major hack that took place earlier this month and the documents are in a pipeline to be published. Some are out there now.
From www.securityaffairs.co who I just interviewed for radio last week:
“We have gained access to the Saudi Ministry of Foreign Affairs (MOFA) network and have full control over more than 3000 computers and servers, and thousands of users. We also have access to the emails, personal and secret information of hundreds of thousands of their diplomats in different missions around the world.” states the group.
The following image was left on the PC of the employees at the Saudi foreign ministry on Thursday morning
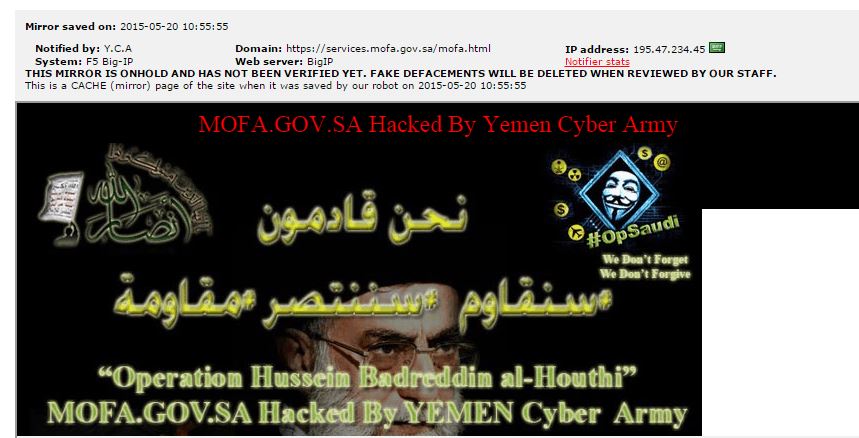
More details here on the Yemen Cyber Army and the Saudi hack. The Yemen Cyber Army left behind these messages for file access as well:
OPERATION Name : “Syed Hussein Badreddin al-Houthi”
OPERATION Key : b919117da9954bd82e65677cb240bbb3e4ddbd9ac93e10f0a399257ad54d851a
Saudi Arabia Ministry of Foreign Affairs Hacked By Yemen Cyber Army
All MOFA.GOV.SA Subdomains And Servers Hacked and HDD Encrypted
Allah is the enemy of those who oppress people
This is to convey a message to Saudi Dictators, if they’ve got a listening ear!
It’s us again, Yemen Cyber Army!
We are an Islamic Group who fights against you oppressors.
What you and your puppets commit in Yemen, Syria, Bahrain, Iraq and Lebanon, remind us of crimes your forefather Yazid-ibn-Muawiya committed in Karbala. And indeed you are good successors to him. You are ISIS and ISIS is you.
Never assume our calmness is due to weakness. We are oppressed! God will judge between you and us. As we never seek help from other than him.
You are pagan oppressors as you always fawn for US and Israel, that’s what you deserve.
So congratulations to those who achieve martyrdom in fight against pagan oppressors.
“And never think of those who have been killed in the cause of Allah as dead. Rather, they are alive with their Lord, receiving provision ”
Our cyber operation is just started and by the grace of God we are expecting the Saudi regime’s collapse by the “Labbaik Ya-Hossain” slogan.
This second operation is blessed by the name of martyred “Syed Hussein Badreddin al-Houthi” and is going to be a beginning to Saudi’s overthrow, Inshallah.
We have gained access to the Saudi Ministry of Foreign Affairs (MOFA) network and have full control over more than 3000 computers and servers, and thousands of users. We also have access to the emails, personal and secret information of hundreds of thousands of their diplomats in different missions around the world.
We publish only few portions of vital information we have, just to let them know that “truly the flimsiest of houses is the spider´s house”
Some portions of visa secret information, thousands of documents from the MOFA’s automation system and secret emails will be published gradually so as to keep Saudi puppets always in fear of their identity disclosure.
This way they might slightly come to know how it feels when our innocent women and children rush into havens crying and looking for their beloved once in dark.
And that’s not all! All your computers will be automatically wiped on Wednesday – 2015 20 May and at 12:00 to become a lesson for oppressors.
We have the same access to the Interior Ministry (MOI) and Defense Ministry (MOD) of which the details will be published in near future. Wish such shocking news make Saudi dictators to come to their senses and recapture those young wild dogs’ leash to avoid Muslims exploiting hate against Saudi family.
If you did not stop attacks on Muslims in Yemen, do not blame anyone but yourself and expect greater harms.
Files PASSWORD : [email protected]
Your Network Hacked By Yemen Cyber Army
We Are Cutting Sword of Justice
All Your Data is Encrypted and You Can’t Access Them without Key
Find Out the Decryption Key This Way :
Number of Yemeni Children Killed in Saudi Air Attacks +
Number of Yemeni Homes Destroyed By Saudi-USA Bombs –
Number of Saudis Killed By Yemenis –
Number of Israeli Soldiers Killed by Saudi and Arab Union in 1984!!!!
#OPSAUDI
#YEMEN_UNDER_ATTACK
#OPKSA
We Are Anonymous
We Are Everywhere
We Are Legion
We do Not Forgive
We do Not Forget
Stop Attacking To Our Country!
****
Now enter the documents and Wikileaks.
WikiLeaks says it’s leaking over 500,000 Saudi documents
ISTANBUL (AP) — WikiLeaks is in the process of publishing more than 500,000 Saudi diplomatic documents to the Internet, the transparency website said Friday, a move that echoes its famous release of U.S. State Department cables in 2010.
WikiLeaks said in a statement that it has already posted roughly 60,000 files. Most of them appear to be in Arabic.
There was no immediate way to verify the authenticity of the documents, although WikiLeaks has a long track record of hosting large-scale leaks of government material. Many of the documents carried green letterhead marked “Kingdom of Saudi Arabia” or “Ministry of Foreign Affairs.” Some were marked “urgent” or “classified.” At least one appeared to be from the Saudi Embassy in Washington.
If genuine, the documents would offer a rare glimpse into the inner workings of the notoriously opaque kingdom. They might also shed light on Riyadh’s longstanding regional rivalry with Iran, its support for Syrian rebels and Egypt’s military-backed government, and its opposition to an emerging international agreement on Tehran’s nuclear program.
One of the documents, dated to 2012, appears to highlight Saudi Arabia’s well-known skepticism about the Iranian nuclear talks. A message from the Saudi Arabian Embassy in Tehran to the Foreign Ministry in Riyadh describes “flirting American messages” being carried to Iran via an unnamed Turkish mediator.
Another 2012 missive, this time sent from the Saudi Embassy in Abu Dhabi, said the United Arab Emirates was putting “heavy pressure” on the Egyptian government not to try former president Hosni Mubarak, who had been overthrown in a popular uprising the year before.
Some of the concerns appear specific to Saudi Arabia.
In an Aug. 14, 2008 message marked “classified and very urgent,” the Foreign Ministry wrote to the Saudi Embassy in Washington to warn that dozens of students from Saudi Arabia and other Gulf countries had visited the Israeli Embassy in the U.S. capital as part of an international leadership program.
“They listened to diplomats’ briefings from the embassy employees, they asked questions and then they took pictures,” the message said, asking the embassy for a speedy update on the situation.
Another eye-catching item was a document addressed to the interior and justice ministers notifying them that a son of Osama bin Laden had obtained a certificate from the American Embassy in Riyadh “showing (the) death of his father.”
Many more of the dozens of documents examined by The Associated Press appeared to be the product of mundane administrative work, such as emails about setting up a website or operating an office fax machine.
The AP was able to partially verify a handful of documents’ authenticity by calling the telephone numbers included in many of them. WikiLeaks spokesman Kristinn Hrafnsson told AP he was confident that the material was genuine.
It is not clear how WikiLeaks got the documents, although in its statement the website referred to a recent electronic attack on the Saudi Foreign Ministry by a group calling itself the Yemen Cyber Army. Hrafnsson declined to elaborate on the statement or say whether the hackers subsequently passed documents on to WikiLeaks.
“As a matter of policy we’re not going to discuss the source of the material,” he said.
The Saudi Embassy in Washington did not immediately return repeated messages seeking comment.
In its statement, WikiLeaks said the release coincided with the three-year anniversary of its founder, Julian Assange, seeking asylum in the Ecuadorian Embassy in London.
Assange took refuge in the embassy to avoid extradition to Sweden, where he is wanted for questioning about alleged sex crimes. Assange has denied any wrongdoing. To access: WikiLeaks’ Saudi Cables site: https://wikileaks.org/saudi-cables/






