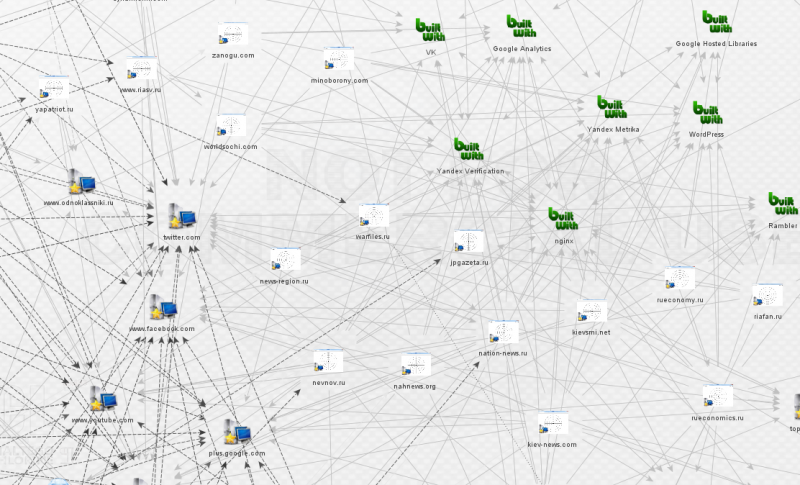
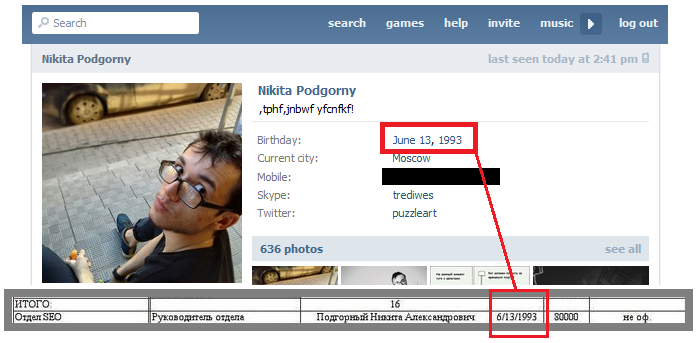
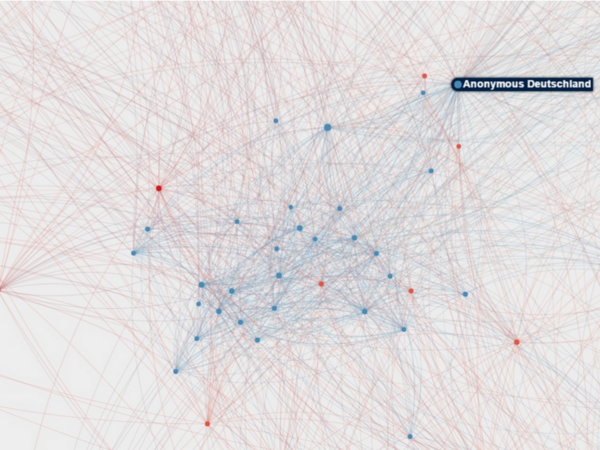
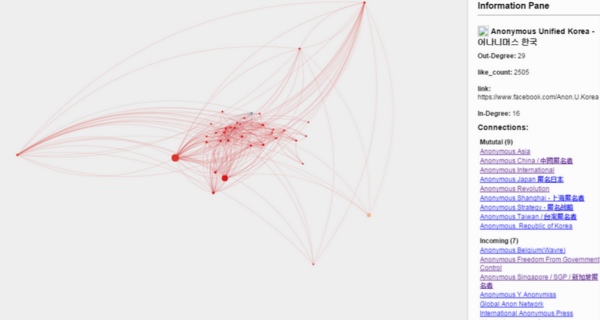
Anyone read the book ‘Disinformation’ by Ronald Rychlak and LtG. Ion Pacepa?

General Joseph Dunford is next in line to replace General Dempsey as the Chairman of the Joint Chiefs of Staff. His assessment today about who represented the topic threat to America’s National Security shocked the lawmakers when his response was Russia.
Peeling back some layers, we will come to understand why the General’s alarming conclusions are exactly right. Russia is operating a stealth KGB operation and it has been effective.
Wikileaks Release Indicates Hacking Team Sold To FSB, Russia’s Secret Police

From Forbes:
Now that Wikileaks has released the emails included in the 415GB leaked by the hackers who breached Italian “lawful intercept” provider Hacking Team TISI NaN%, the world has easy access to a trove of information blowing open the inner workings of the private surveillance industry. Amongst the files seen by FORBES so far, emails detailing Hacking Team’s sales to Russia’s secret police, the FSB.
Previous analysis of the leaks had sold its Galileo Remote Control System (RCS) to KVANT, a Russian state-owned military technology company. This inspired questions from Dutch politician and European Member of Parliament Marietje Shaake about the potential breach of European Union sanctions about the sale of such goods to Russia, which has been put on blacklists for its operations in war-torn Ukraine. Selling to the FSB would likely concern onlookers more, given the agency’s widespread access to communications in Russia. Many more details here.
Going beyond the next layer
State Department warns IS online threat ‘unmatched’
The hacker group Cyber Caliphate that was thought to be an online arm of the Islamic State has no ties to the terror group despite its cyber attacks in support of the ultra-violent al-Qaeda offshoot, according to a State Department security report.

“Although Cyber Caliphate declares to support ISIL, there are no indications—technical or otherwise—that the groups are tied,” the two-page report from the Overseas Security Advisory Council states. The Islamic State (IS) is also known by the acronyms ISIL or ISIS.
Instead, Russian hackers now appear to be linked to the Cyber Caliphate, a fact discovered by French government authorities after a cyber attack on TV5Monde television in France last April.
In addition to the announcing the lack of a connection between IS and the Cyber Caliphate, the State Department warned that the terrorist group nevertheless continues to have unprecedented online recruitment and propaganda capabilities.
“ISIL’s online presence for propaganda and recruitment purposes continues to be unmatched by other terrorist organizations,” the report said.
The Islamic State uses Internet sites and social media strategies to disseminate and control its Islamist message.
“ISIL’s use of Twitter has been deemed particularly effective; a Brookings study reported at least 46,000 Twitter accounts in use by ISIL supporters during the timeframe of September through December 2014,” the report said.
IS also deftly exploits modern technology and has mastered online propaganda in appealing to young and computer-savvy foreigners, including known hackers who support its ends.
“Although ISIL continues to demonstrate success in using online tools for propaganda, recruitment, and fundraising purposes, the suspected link of Russian hackers to the TV5Monde attack reinforces the assessment that ISIL still lacks the ability to carry out a technically sophisticated cyberattack,” the report concludes.
President Obama on Monday defended the administration strategy against ISIL—despite the group’s expansion from Iraq and Syria to other parts of the world.
Obama said ISIL is “particularly effective” in recruiting foreigners, including Americans, and is using online methods to spread its ideology.
The president said that to defeat ISIL and al Qaeda, “it is going to also require us to discredit their ideology.”
However, the president and his administration continue to play down the Islamist nature of the threat, preferring the non-religious term “violent extremism.”
“Ideologies are not defeated with guns. They’re defeated by better ideas, [a] more attractive and more compelling vision,” Obama said.
“So the United States will continue to do our part by working with partners to counter ISIL’s hateful propaganda, especially online.”

The State Department report, “Who Is Cyber Caliphate? Re-examining the Online ISIL Threat,” was produced by a unit of the Department’s Office of Diplomatic Security, which supports American businesses overseas. It describes Cyber Caliphate as a relatively unsophisticated group that has conducted cyber attacks against perceived enemies of the Islamic State.
“This included targeting various media outlets, issuing threats against U.S. military spouses, and the highly publicized hacking of U.S. Central Command’s Twitter account and YouTube channel,” the report said.
Most of the group’s technical activities involved website defacements and hacking of Twitter accounts. The cyber vandalism seems to have beeen intended to spread IS propaganda and to build notoriety for the group.
However, the TV5Monde cyber attack that disrupted live broadcasts, staff email accounts, and the station’s web page for some 20 hours demonstrated new capabilities, the report said.
“The methodology employed in the attack was atypical of previous Cyber Caliphate activity, and further investigation by French authorities and U.S. private cyber security companies instead pointed to nation-state actors,” the report said.
Among the information said to have been compromised during the TV5Monde attack were personal information about relatives of French soldiers fighting IS. France is among the coalition of nations engaged in military operations against IS.
According to the report, IP addresses traced to the TV5Monde attack were traced to the Russian hacker group known as APT28.
“The [APT28] hacking group was formerly observed targeting the North Atlantic Treaty Organization, entities in Eastern Europe, security companies, and journalists,” the report said.
“APT28 is assessed to conduct operations to benefit the Russian government, and was not previously seen using hacktivists or terrorist organizations as cover.”
The origin of Cyber Caliphate and its members remains unclear. Initially, it was believed by security authorities that the group started by a British hacker, 20-year-old Junaid Hussain, who was linked to a hack against former British Prime Minister Tony Blair.
Hussain then was said to have moved from Britain to Syria where he sought to recruit hackers.
The Cyber Caliphate has not been officially endorsed by IS but it has gained from the free publicity its hacker attacks have generated.
The group’s attack on TV5Monde was described in the report as an anomaly for the hackers. Several theories are under consideration by experts regarding the nature of the group’s actions.
Some analysts believe the group was testing its cyber capabilities in preparation for expanded strikes on new targets.
Other analysts said the television station cyber attack was retaliation based on strained ties between Moscow and Paris.
Russia was angered by France’s recent decision to cancel a $1.3 billion deal for two Mistral-class helicopter carriers for the Russian Navy after Russia’s military aggression against Ukraine.
According to the report, the cyber security firm iSight Partners has assessed the Cyber Caliphate as a “false front for anti-western Russian actors.”
Another theory is that Cyber Caliphate is part of a Russian disinformation operation used by Moscow’s hackers as cover for their cyber attacks. The report noted “Russia’s long history of disinformation campaigns.”