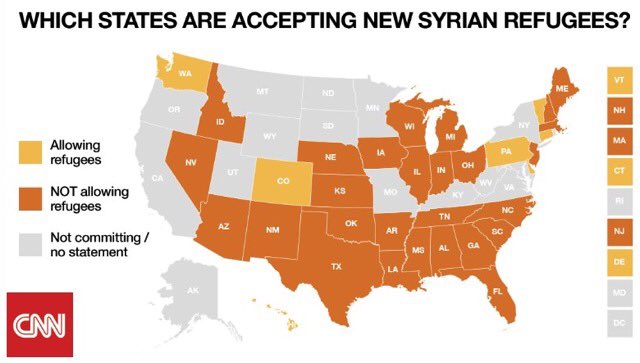
WallStreetJournal: This week dozens of state governors said they would refuse Syrian refugees, citing national security concerns after the Paris attacks. The Obama administration pushed back on those announcements and stressed that the governors had little power to do so. But they also pledged to explain the program to those doubting it could screen out potential terrorists. Here’s a breakdown of how the program works.
* * *
Q: What kind of screenings do Syrian refugees go through?
A: Refugees from all countries receive “the most rigorous screening and security vetting of any category of traveler to the United States,” a senior administration official told reporters Tuesday. That process includes biographic and biometric security checks – i.e. checking records and doing fingerprinting. Law enforcement, the Pentagon and the intelligence community all vet information provided by and obtained about refugees to help make a determination about whether they will ultimately be allowed to come to the U.S. Syrian refugees go through an enhanced review process on top of that with extra national security checks. All Syrian refugees considered for resettlement in the U.S. are interviewed in person by specially trained staff, mostly in Amman and Istanbul, but also in Cairo and elsewhere. Refugees must also undergo health screenings and a cultural orientation before they arrive in the U.S.
Q: How long does it take?
A: The process usually takes between 18 to 24 months and generally begins with a referral from the U.N. refugee agency. Those referrals include biographic and other information that the Department of Homeland Security uses to determine if the cases meet the criteria for refugee status. If DHS decides a refugee qualifies on one of five protected grounds – race, religion, nationalist, political views or belonging to a certain social group, the extensive screening processes described earlier begin. For comparison, an international student seeking to study in the U.S., for example, usually schedules a consular interview three to five months in advance of beginning schooling.
Q: Who are the Syrian refugees coming to the U.S.?
A: Half of the Syrian refugees resettled in the U.S. so far are children, according to a senior administration official. Of the rest, 2.5% are adults over 60 and 2% are single men. The refugees are roughly half men and half women, with slightly more men.
Q: How many are here now?
A: Since the Syrian crisis began in 2011, the U.S. has admitted about 2,200 Syrian refugees. That’s a very small chunk of the more than 332,000 refugees who have come to the U.S. during the same period. The Obama administration has pledged to take in at least 10,000 in fiscal year 2016, which began in October. Over 4 million people have fled Syria since the crisis began in March 2011. Most are located in countries in the region.
Q: Where are Syrian refugees living in the U.S.?
A: The top resettlement states for Syrian refugees are California, Texas, Michigan, Illinois and Arizona. Overall 36 states have taken in Syrians since 2011.
Q: What happens once a refugee arrives to the U.S.?
A: Refugees are required to adjust their status to become legal permanent residents within one year of arriving to the U.S. Each week the nine networks of nonprofits that work with the State Department to resettle refugees meet to decide where to send refugees arriving here. Those decisions are based on where their family members might be located, which states have low unemployment rates and what cities might be able to provide specialized medical treatment, for example. Officials usually try to resettle refugees in medium-size cities like Nashville, Tenn., and Buffalo, N.Y. that aren’t too expensive. But once refugees get here, they are free to live wherever they wish, officials said.
*** Then there is the Office of Refugee Resettlement, a division of Health and Human Resources.
The Office of Refugee Resettlement (ORR) gives new populations the opportunity to maximize their potential in the United States. ORR’s programs provide people in need with critical resources to assist them in becoming integrated members of American society, such as cash, social services, and medical assistance.
ORR benefits and services are available to eligible persons from the following groups:
- Refugees
- Asylees
- Cuban/Haitian entrants
- Amerasians
- Victims of human trafficking
- Unaccompanied alien children
- Survivors of torture
ORR has five divisions and one major program area:
- Refugee Assistance
- Refugee Health
- Resettlement Services
- Children’s Services
- Anti-Trafficking in Persons
- Office of the Director
Division of Refugee Assistance:
The Division of Refugee Assistance (DRA) supports, oversees and provides guidance to State-Administered, Public Private Partnership and Wilson/Fish programs that provide assistance and services to refugees, asylees, certain Amerasian immigrants, Cuban and Haitian entrants, and Certified Victims of Human Trafficking (henceforth referred to collectively as refugees). DRA reviews and monitors state plans, budget submissions, service plans, and reports, while providing technical assistance to ensure that federal regulations are followed and adequate services and performance are maintained. The ultimate goal is to provide the types of assistance that will allow refugees to become economically self-sufficient as soon as possible after their arrival in the United States.
Program structures:
- State Administered: Cash, medical, and social services are primarily managed by states as part of their social service or labor force programs. The program goal is to enable refugees become self-sufficient as soon as possible.
- Public Private Partnership: This partnership provides States the option to enter into a partnership with local voluntary resettlement agencies to provide cash assistance to refugees. The objective is to create more effective resettlement, while maintaining state responsibility for policy and administrative oversight.
- Wilson-Fish: The program is an alternative to the traditional state administered refugee resettlement program. This program provides cash, medical assistance, and social services to refugees. The purpose of the Wilson-Fish program is to increase refugee prospects for early employment and self-sufficiency, promote coordination among voluntary resettlement agencies and service providers, and ensure that refugee assistance programs exist in every state where refugees are resettled.
DRA is responsible for the following programs:
- Cash and Medical Assistance: This program provides reimbursement to states and other programs for cash and medical assistance. Refugees who are ineligible for TANF and Medicaid may be eligible for cash and medical assistance for up to eight months from their date of arrival, grant of asylum, or date of certification for trafficking victims.
- Refugee Social Services: This program allocates formula funds to states to serve refugees who have been in the United States less than 60 months (five years). Services are focused on addressing employability and include interpretation and translation, day care, citizenship, and naturalization. Services are designed to help refugees obtain jobs within one year of enrollment.
- Targeted Assistance Formula: This program allocates formula funds to states that qualify for additional funds due to an influx of refugee arrivals that need public assistance. TAG service prioritize (a) cash assistance recipients, particularly long-term recipients; (b) unemployed refugees not receiving cash assistance; and (c) employed refugees in need of services to retain employment or to attain economic independence.
- Cuban Haitian: This program provides discretionary grants to states and other programs to fund assistance and services in localities with a heavy influx of Cuban and Haitian entrants and refugees. This program supports employment services, hospitals, and other health and mental health care programs, adult and vocational education services, refugee crime or victimization programs, and citizenship and naturalization services.
- Refugee School Impact: This program provides discretionary grants to state and other programs. Funds go to school districts to pay for activities that will lead to the effective integration and education of refugee children between the ages of 5 and 18. Activities include English as a second language; after-school tutorials; programs that encourage high school completion and full participation in school activities; after-school and/or summer clubs and activities; parental involvement programs; bilingual/bicultural counselors; interpreter services, etc.
- Services to Older Refugees: This program provides discretionary grants to states to ensure that refugees aged 60 and above are linked to mainstream aging services in their community. ORR cooperates with the Administration for Community Living to reach this goal.
- Targeted Assistance Discretionary: This program provides discretionary grants to states and other programs to address the employment needs of refugees that cannot be met with the Formula Social Services or Formula Targeted Assistance Grant Programs. Activities under this program are for the purpose of supplementing and/or complementing existing employment services to help refugees achieve economic self-sufficiency.
- Technical Assistance Program: This program provides technical assistance grants to organizations with expertise in specific areas, such as employment, cultural orientation, economic development, and English language training.
Division of Refugee Health
ORR recently created the refugee heath program to address issues of health and well-being that are vital to refugees and other ORR-eligible populations. The refugee health program works on various projects including: collaborating with federal partners in the implementation of the Affordable Care Act (ACA); administering the Survivors of Torture and Preventive Health programs; and providing technical assistance on medical screening guidelines, assessment and follow-up for contagious or communicable diseases, mental health awareness and linkages, suicide prevention, emergency preparedness and other health and mental health initiatives. It also coordinates with state and federal partners to advance ORR’s overall health initiatives.DRH is responsible for the following programs:
- Refugee Preventive Health: This program provides discretionary grants to states or their designated health agencies or other programs that facilitate medical screenings and support health services. The program aims to reduce the spread of infectious disease, treat any current ailments, and promote preventive health practices.
- Services to Survivors of Torture Program: This program provides funding for a comprehensive program of support for survivors of torture. The Torture Victims Relief Act of 1998 recognizes that a significant number of refugees, asylees, and asylum seekers entering the United States have suffered torture. The program provides rehabilitative services which enable survivors to become productive members of our communities.
Division of Resettlement Services
The Division of Resettlement Services (DRS) provides assistance through public and private non-profit agencies to support the economic and social integration of refugees. DRS is responsible for the following programs:
- Matching Grant Program: This is an alternative program to public assistance designed to enable refugees to become self-sufficient within four to six months from the date of arrival into the United States. Eligible grantees are voluntary agencies able to coordinate comprehensive multilingual, multicultural services for refugees at local sites; the same agencies are under cooperative agreements with the Department of State/Bureau of Population, Refugees and Migration (PRM).
- Refugee Agriculture Partnership Program: The Refugee Agriculture Partnership Program (RAPP) involves refugees in the effort to improve the supply and quality of food in urban and rural areas. Refugees are potential farmers or producers of more healthful foods, as well as consumers whose health and well-being are affected by diet. RAPP has evolved into a program with multiple objectives that include: creating sustainable income; producing supplemental income; having an adequate supply of healthy foods in a community; achieving better physical and mental health; promoting community integration, and developing the capacity of organizations to access USDA and other services and resources. In cooperation with the USDA, ORR helps develop community gardens and farmers’ markets.
- Preferred Communities Program: This program supports the resettlement agencies of newly arriving refugees by providing them additional resources to help refugees to become self-sufficient and to integrate into their new communities. The program also assists service providers that assist refugees with special needs that require more intensive case management.
- Ethnic Community Self-Help Program: This program provides assistance to refugee ethnic community-based organizations (ECBOs) that address community building and facilitate cultural adjustment and integration of refugees. The program’s purpose is to promote community organizing that builds bridges between newcomer refugee communities and community resources.
- Microenterprise Development Program: This program enables refugees to become financially independent by helping them develop capital resources and business expertise to start, expand, or strengthen their own business. The program provides training and technical assistance in business plan development, management, bookkeeping, and marketing to equip refugees with the skills they need to become successful entrepreneurs.
- Microenterprise Development – Home-Based Child Care Program: This program is designed to enable refugee women to become entrepreneurs while simultaneously caring for their own children.
- Individual Development Accounts Program: Individual development accounts are matched savings accounts available for the purchase of specific assets. Under the IDA program, the matching funds, together with the refugee’s own savings from his or her employment, are available for one (or more) of the following: home purchase; microenterprise capitalization; post secondary education or training; and in some cases, purchase of an automobile if necessary to maintain or upgrade employment. Upon enrolling in an IDA program, a refugee signs a savings plan agreement, which specifies the savings goal, the match rate, and the amount the refugee will save each month. Refugees also receiving training in navigating the financial system, budgeting, saving, and credit.
Division of Children’s Services
The Division of Children’s Services (DCS) recognizes the importance of providing a safe and appropriate environment for unaccompanied alien children during the interim period between the minor’s transfer into ORR care and reunification with family or other sponsors or removal from the United States by the U.S. Department of Homeland Security. DCS strives to provide the best care and placement for unaccompanied alien children (UAC), who are in federal custody by reason of their immigration status, while taking into account the unique nature of each child’s situation in making placement, case management, and release decisions. DCS also oversees the Unaccompanied Refugee Minors (URM) program, which connects refugee minors with appropriate foster care services and benefits when they do not have a parent or a relative available and committed to providing for their long-term care.
- Unaccompanied Children’s Services: This program makes and implements placement decisions in the best interests of UAC to ensure that they are in the least restrictive setting possible while in federal custody. The majority of UAC are cared for through a network of state licensed ORR-funded care providers, which provide classroom education, mental and medical health services, case management, and socialization/recreation. ORR/DCS funds programs to provide a continuum of care for children, including foster care, group homes, and residential treatment centers. The division also coordinates a legal access project assuring that these children have information about their legal rights and receive an individual legal screening to assess their chances of legal relief. Finally, ORR/DCS provides family reunification services to facilitate safe and timely placement with family members or other qualified sponsors.
- Unaccompanied Refugee Minors Program: This program ensures that eligible unaccompanied minor populations receive the full range of assistance, care, and services available to all foster children in the state by establishing a legal authority to act in place of the child’s unavailable parent(s). Our programs encourage reunification of children with their parents or other appropriate adult relatives through family tracing and coordination with local refugee resettlement agencies. However, if reunification is not possible, each program works to design a case specific permanency plan for each minor or youth in care. Additional services ORR provides include: indirect financial support for housing, food, clothing, medical care, and other necessities; intensive case management by social workers; independent living skills training; educational supports including educational training vouchers; English language training; career/college counseling and training; mental health services; assistance adjusting immigration status; cultural activities; recreational opportunities; support for social integration; cultural and religious preservation.
Anti-Trafficking in Persons Division
The Division of Anti-Trafficking in Persons (ATIP) helps certify victims of a severe form of trafficking in persons, as defined by the Trafficking Victims Protection Act of 2000. These individuals are eligible to receive federally funded benefits and services to the same extent as refugees, and can begin to rebuild their lives in the United States. ATIP is committed to promoting public awareness and assisting in the identification of trafficking victims by educating the public and persons likely to encounter victims. These organizations or persons may include: social services providers; public health officials; legal organizations; as well as ethnic, faith-based, and community organizations.ATIP is responsible for the following programs:
Victim Identification and Public Awareness
• Rescue and Restore Campaign: This program is a public awareness campaign that established Rescue and Restore coalitions in 24 cities, regions, and states. These community action groups are comprised of non-governmental organization leaders, academics, students, law enforcement officials, and other key stakeholders who are committed to addressing the problem of human trafficking in their own communities.
• Rescue and Restore Regional Program: This program serves as the focal point for regional public awareness campaign activities and intensification of local outreach to identify victims of human trafficking. Each Rescue and Restore Regional partner oversees and builds the capacity of a local anti-trafficking network, and sub-awards 60 percent of grant funds to local organizations that identify and work with victims. By acting as a focal point for regional anti-trafficking efforts, Rescue and Restore Regional partners encourage a cohesive and collaborative approach in the fight against modern-day slavery.
Assistance for Victims of Human Trafficking
- Certifications and Eligibility Letters: HHS is the sole federal agency authorized to certify foreign adult victims of human trafficking. Similarly, it is the sole federal agency authorized to make foreign child victims of human trafficking eligible for assistance. ORR issues all certifications and eligibility letters. Certification grants adult foreign victims of human trafficking access to federal benefits and services to the same extent as refugees. Likewise, eligibility letters grant minor foreign victims of trafficking access to federal benefits and services to the same extent as refugees, including placement in the Unaccompanied Refugee Minors program.
- National Human Trafficking Victim Assistance Program: This program provides funding for comprehensive case management services to foreign victims of trafficking and potential victims seeking HHS certification in any location in the United States. The grantees provide case management to assist a victim of trafficking to become certified, and other necessary services after certification, through a network of sub-awardees in locations throughout the country. These grants ensure the provision of case management, referrals, and emergency assistance (such as food, clothing, and shelter) to victims of human trafficking and certain family members. Grantees help victims gain access to housing, employability services, mental health screening and therapy, medical care, and some legal services, enabling victims to live free of violence and exploitation.
- National Human Trafficking Resource Center: This program is a national, toll-free hotline for the human trafficking field in the United States. It is reached by calling 1-888-3737-888 or e-mailing [email protected]. The NHTRC operates around the clock to protect victims of human trafficking. It provides callers with a range of comprehensive services including: crisis intervention; urgent and non-urgent referrals; tip reporting; anti-trafficking resources; and technical assistance for the anti-trafficking field and those who wish to get involved. To perform these functions, the NHTRC maintains a national database of organizations and individuals, as well as a library of anti-trafficking resources and materials.
Office of the Director
The Office of the Director responds to overall ORR operations and special projects, including communications and outreach, media relations, and the federal government’s U.S. Repatriation Program. The Budget, Policy, and Data Analysis (BPDA) team is also located within the Office of the Director, and is responsible for the allocation and tracking of funds for refugee cash and medical assistance, as well as state administrative costs; forecasting and executing ORR’s annual budget; developing regulations and legislative proposals; and routinely interpreting policy. BPDA also coordinates preparation of the ORR Annual Report to Congress.