Is this a joke? Those computers had/have malware installed that was never detected even after that major OPM hack that forced the mainframes to communicate with Russia…..yes RUSSIA. So, here comes that Inspector General audit report. We are bleeding data, even classified data….So we have tech companies and social media operations that are not protecting or safeguarding our data, now for sure we have government that cant do it either…..
There was a hearing though…..ahem
In part from the audit report: This memorandum transmits the findings of our evaluation of the U.S . Departmentof the Interior’ s incident response program. We found that the Office of the ChiefInformation Officer had not fully implemented the capabilities recommended byNational Institute for Standards and Technology (NIST) in its incident detectionand response program.We make 23 recommendations to help the Department improve its incident responseprogram , so it can promptly detect and full y contain cyber threats to maintain theavailability, confidentiality, and integrity of Department and bureau computersystems and data.In response to our draft report, the Department concurred with all recommendationsand provided target dates and officials responsible for implementation.We consider all 23 recommendations resolved but not implemented.We will forward the recommendations to the Office of Policy, Management andBudget for tracking and implementation. We understand that some of these recommendations may require significant investment in cyber security infrastructureas well as the recruitment of additional staff, but the intended timeframe to implementthese recommendations remains a concern.Five recommendations will not be addressed for more than 5 years, and four recommendations will not be addressed for more than 3 years.In the interim, the Department should consider additional temporary or partial solutions.
Three years after Chinese hackers stole security clearance files and other sensitive personal information of some 22 million U.S. federal employees, cyber-defenses at the Department of Interior, which hosted White House Office of Personnel Management (OPM) servers targeted in the theft, were still unable to detect “some of the most basic threats” inside Interior’s computer networks — including malware actively trying to make contact with Russia.
In a 16-month examination of Interior’s ability to detect and respond to cyber-threats, evaluators from the department’s Office of Inspector General (OIG) also discovered that Interior’s technicians simply did not implement a sweeping array of mandatory, government-wide defensive measures ordered up after the disastrous OPM hack, didn’t investigate blocked intrusion attempts, and left “multiple” compromised computers on their network “for months at a time,” according to a redacted OIG report issued in March.
Ultra-sensitive security clearance files have since been moved to the Defense Department, but, among other things, the OIG report noted that:
● sensitive data at Interior could be taken out of the department’s networks “without detection.”
● network logs showed that a computer at the U.S. Geological Survey, an Interior bureau, was regularly trying to communicate with computers in Russia. The messages were blocked, but “the USGS facilities staff did not analyze the alerts.”
● dangerous or inappropriate behavior by network users — including the downloading of pornography and watching pirated videos on Russian and Ukrainian websites — was not investigated.
● computers discovered to be infected with malware were scrubbed as soon as possible and put back into use—meaning little or no effort went into examining the scope and nature of any such threats to the broader network. This happened, the OIG team noted, with one intruder they discovered themselves.
● simulated intrusions or ransomware attacks created by the examiners were carried out with increasing blatancy without a response—in the case of ransomware, for nearly a month
● After the devastating OPM hack, which was discovered in April 2015, the department didn’t even publish a lessons-learned plan for its staffers based on the disaster. The OIG inspectors reported that Interior started to draft an “incident response plan” that month to deal with future intrusions, but “did not publish it until August 2017”— two months after the OIG team had finished their lengthy fieldwork.
● Distressingly, the report also notes that the department’s cybersecurity operations team was not privy to a list of Interior’s so-called “high-value IT assets” prepared by the Chief Information Officer, “due to its sensitive nature.” More here.







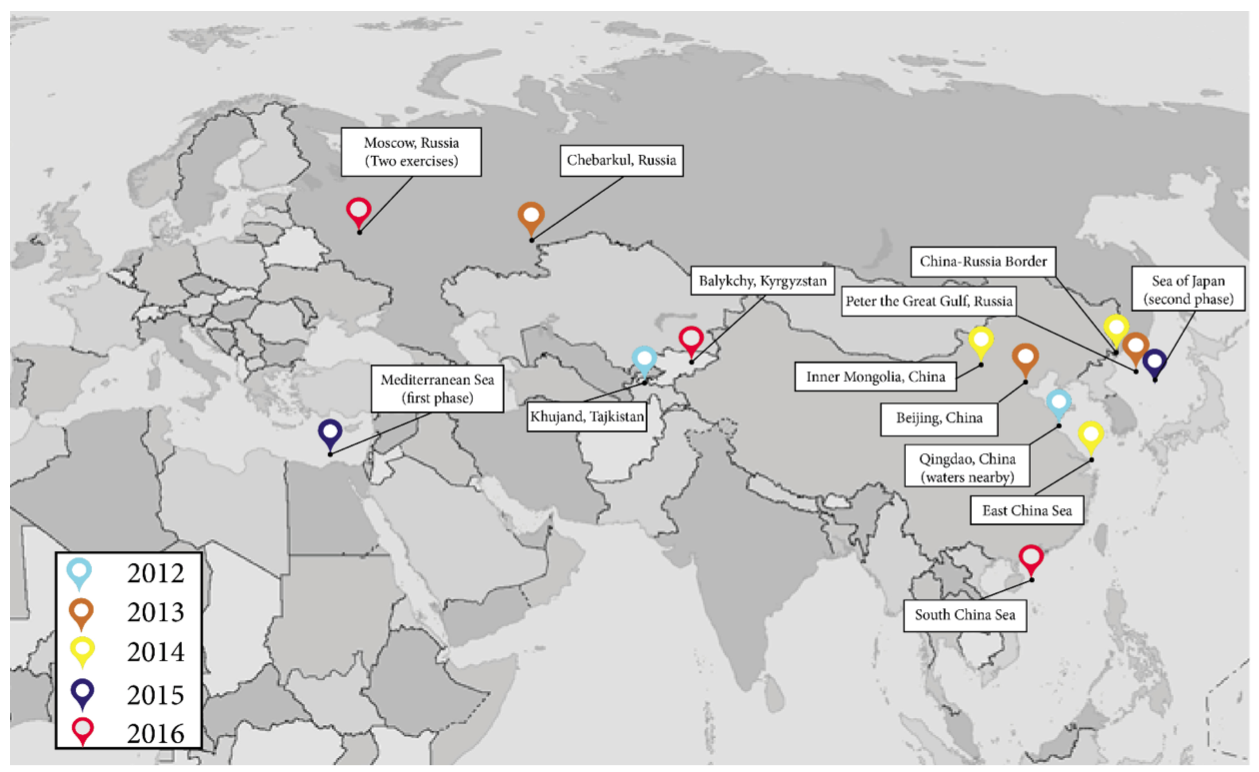 Before Russia and China began their recent series of bilateral exercises, the key tie between Moscow and Beijing was arms sales and military technology cooperation — totaling about $26 billion from 1992 to 2006 — according to estimates cited in the report.
Before Russia and China began their recent series of bilateral exercises, the key tie between Moscow and Beijing was arms sales and military technology cooperation — totaling about $26 billion from 1992 to 2006 — according to estimates cited in the report.