Dell has reached out to this site with updated/corrected links for the item below:
Please refer to https://www.quest.com and https://www.quest.com/solutions/network-security/
What is SCADA? A computerized system that controls all national infrastructure. This includes water, power grids, transportation and supply chains.
In 2012:
The last “INTERNET SECURITY THREAT REPORT” published by Symantec reports that in 2012, there were eighty-five public SCADA vulnerabilities, a massive decrease over the 129 vulnerabilities in 2011. Since the emergence of the Stuxnet worm in 2010, SCADA systems have attracted more attention from security researchers.
Today, 2015 there is a significantly more chilling condition.
A recent report published by Dell revealed a 100 percent increase in the number of attacks on industrial control (SCADA) systems.
The new Dell Annual Threat Report revealed that the number of attacks against supervisory control and data acquisition (SCADA) systems doubled in 2014 respect the previous year. Unfortunately, the majority of incidents occurred in SCADA systems is not reported. The experts confirmed that in the majority of cases the APT are politically motivated.
“Attacks against SCADA systems are on the rise, and tend to be political in nature as they target operational capabilities within power plants, factories, and refineries,” the researchers explained. “We saw worldwide SCADA attacks increase from 91,676 in January 2012 to 163,228 in January 2013, and 675,186 in January 2014.”
The countries with the greatest number of attacks are the Finland, the United Kingdom, and the United States, where online SCADA systems are widespread.
“In 2014, Dell saw 202,322 SCADA attacks in Finland, 69,656 in the UK, and 51,258 in the US” continues the report.
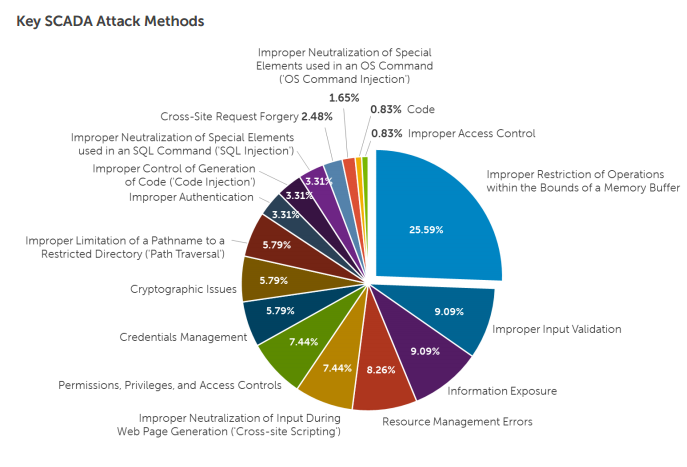
The experts noticed that buffer overflow is the vulnerability in SCADA system most exploited by hackers (25%), among other key attack methods there are the lack of input validation (9%) and Information Exposure (9%).
Security experts speculate that the number of the attacks will continue to increase in the next years.
“This lack of information sharing combined with the vulnerability of industrial machinery due to its advanced age means that we can likely expect more SCADA attacks to occur in the coming months and years.” states the report.
The data published by Dell are aligned with the findings included in a report recently published by the ICS-CERT. The CERT responded to 245 incidents in Fiscal Year 2014, more than half of the incidents reported by asset owners and industry partners involved sophisticated APT.
Let’s closed with the suggestions provided by Dell experts to protect SCADA systems from attacks:
- Make sure all software and systems are up to date. Too often with industrial companies, systems that are not used every day remain installed and untouched as long as they are not actively causing problems. However, should an employee one day connect that system to the Internet, it could become a threat vector for SCADA attacks.
- Make sure your network only allows connections with approved IPs.
- Follow operational best practices for limiting exposure, such as restricting USB ports if they aren’t necessary and ensuring Bluetooth is disabled.
- In addition, reporting and sharing information about SCADA attacks can help ensure the industrial community as a whole is appropriately aware of emerging threats.