This is what global intelligence agencies are searching for answers. It was determined that the roads around the Wuhan Laboratory in question were closed determined by the lack of cell phone activity. How is that possible? There are in fact several telecom/research firms around the globe that monitor traffic and for two weeks in October there was almost no activity. Deeper investigations are underway.
In part from an NBC News article published May 8, 2020: WASHINGTON — A private analysis of cellphone location data purports to show that a high-security Wuhan laboratory studying coronaviruses shut down in October, three sources briefed on the matter told NBC News. U.S. spy agencies are reviewing the document, but intelligence analysts examined and couldn’t confirm a similar theory previously, two senior officials say.
The report — obtained by the London-based NBC News Verification Unit — says there was no cellphone activity in a high-security portion of the Wuhan Institute of Virology from Oct. 7 through Oct. 24, 2019, and that there may have been a “hazardous event” sometime between Oct. 6 and Oct. 11. Because the Wuhan lab is a high-security facility in an adversary nation studying dangerous pathogens, it is a collection target for several U.S. intelligence agencies, multiple officials told NBC News. Data gathered would include mobile phone signals, communications intercepts and overhead satellite imagery, the officials said.
Analysts are now examining what was collected in October and November for clues suggesting any anomalies at the lab, officials said. Congressional intelligence committees have also been given the document, and Sen. Marco Rubio, R.-Fla., appeared to be alluding to it or a similar report in a tweet on Wednesday.
“Would be interesting if someone analyzed commercial telemetry data at & near Wuhan lab from Oct-Dec 2019,” Rubio tweeted. “If it shows dramatic drop off in activity compared to previous 18 months it would be a strong indication of an incident at lab & of when it happened.”
As noted also within the article, nothing yet is conclusive.
***
Interesting to note however, it seems that another shutdown in Wuhan happened in January if those reports are found accurate regarding the empty roads and void of cell phone traffic.
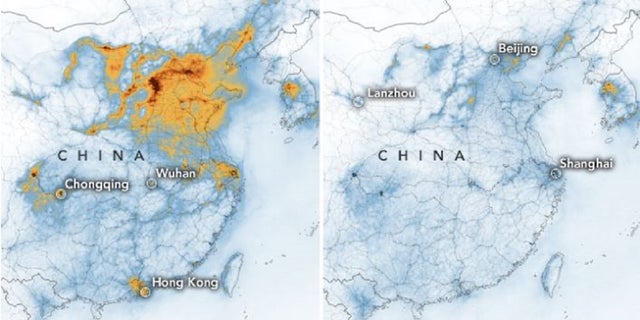
From MIT Technology in part: On January 22, China took the extraordinary step of shutting down all transportation in the city of Wuhan, where the coronavirus outbreak first began. The measure effectively put 11 million people under quarantine, which is still ongoing as public health officials work to treat individuals who have fallen ill and stop the spread of the virus. As satellite images shared with MIT Technology Review by Planet Labs and Maxar Technologies show, the metropolis has ground to a halt. Bridges and roads are empty. The city’s train stations are deserted. Wuhan’s normally busy airport has completely ceased operations.

 Photo Credits: Top photo Before The Wuhan Train Station surrounded by an enormous amount of traffic on the roads. Bottom photo After Traffic around the station evaporated following the quarantine. Trains have not been running since its implementation on January 22. PLANET LABS
Photo Credits: Top photo Before The Wuhan Train Station surrounded by an enormous amount of traffic on the roads. Bottom photo After Traffic around the station evaporated following the quarantine. Trains have not been running since its implementation on January 22. PLANET LABS
Also in January of 2020:
The World Health Organisation has denied a media report that claimed that Chinese President Xi Jinping personally asked WHO Director-General Tedros Adhanom to ‘delay a global warning’ regarding the coronavirus outbreak during a phone call in January.
The German news outlet, Der Spiegel, published a report citing intelligence from the country’s Federal Intelligence Service, known as the ‘Bundesnachrichtendienst’ (BND), that China “urged” the WHO to “delay a global warning” about the coronavirus outbreak. As per the report, the intelligence found that Xi and Tedros spoke by phone on January 21 during which the Chinese President “urged” the WHO chief to “hold back information about a human-to-human transmission and to delay a pandemic warning.” “The BND estimates that China’s information policy lost four to six weeks to fight the virus worldwide,” the report further added.
Statement on False Allegations in @derspiegel: Reports of a 21 Jan phone call between @DrTedros & ?? President Xi are unfounded & untrue. They didn’t speak on 21 Jan & have never spoken by ?
Such inaccurate reports distract & detract from WHO’s & the ?’s efforts to end #COVID19— World Health Organization (WHO) (@WHO) May 9, 2020
The WHO noted on Saturday that “China confirmed human-to-human transmission of the novel coronavirus on Jan. 20.” The WHO publicly declared on Jan. 22 that “data collected … suggests that human-to-human transmission is taking place in Wuhan.” The organisation declared coronavirus a pandemic in March.
If a country is not part of the China Silk Road Initiative then cooperation of any sort is limited as noted from their own website –>
China and International Community Work
Together to Build Health Silk Road
As the COVID-19 pandemic spreads rapidly across the globe, China has made tremendous contributions to the international cooperation on combating the virus. China has actively conducted cooperation with the participating countries for the Belt and Road Initiative and international organizations, through mutual support and assistance as well as solidarity, to tide over the difficulties, in joint efforts to build the Health Silk Road and promote the global community of shared future for mankind.
As of March 31st, Chinese government has provided 120 countries and 4 international organizations with aid supplies including medical masks, N95 respirators, protective gowns, NAT kits and ventilators. Chinese local authorities have donated medical supplies to 50 countries through international sister-city channel. Chinese enterprises have donated medical supplies to over 100 countries and international organizations. Up to April 7th, China has sent 11 batches of medical specialist teams to 9 countries comprised of Italy, Serbia, Cambodia, Pakistan, Iran, Iraq, Laos, Venezuela, and the Philippines. China has unreservedly shared the anti-contagion information with the international community, shared the pandemic prevention and control, treatment and other technology documents with over 100 countries and 10 international and regional organizations, established the online knowledge center for the pandemic and the expert tank for international cooperation, and held more than 40 conferences on technology exchanges via remote video with over 100 countries and regions. China has donated 20 million USD to WHO in support of anti-pandemic international cooperation organized by WHO.
***
According to China’s “One Belt, One Road” initiative, the chance that exotic pathogens could be brought into the country has dramatically increased (7). Our new BSL-4 facility will play an integral role in preventing and controlling highly pathogenic microbes. To safely operate this facility, we designed a training program that ensures all personnel meet the institutional, national, and international standards for working in maximum-containment laboratories.
In preparation for the opening of the Wuhan BSL-4, we engaged in short- and long-term personnel exchanges focused on biosafety training through international cooperation (8). Four staff members visited the P4 Jean Mérieux-Inserm Laboratory in Lyon, France; 2 visited Galveston National Laboratory, The University of Texas Medical Branch at Galveston, Texas, USA; and 1 visited the Australian Animal Health Laboratory, Geelong, Victoria, Australia for training and certification on BSL-4 laboratory operations, maintenance, and scientific or support work. These members are now the main instructors for our BSL-4 laboratory user training program.
Rather than being standardized, our training is specialized to fundamentally cover different BSL-4 users, including administrators and management, biosafety professionals, operations and maintenance staff, and researchers and technicians who currently work in the laboratory. The theoretical coursework is designed to help trainees understand the features of the BSL-4 laboratory and prepares them to enter the laboratory environment. We constructed the first BSL-4 training laboratory in China with the sole purpose of providing hands-on practicum for staff. This laboratory gives staff a safe environment in which they can learn all routine and emergency procedures of high-containment laboratories without the risk of exposure to dangerous pathogens. In addition, we developed an online training management software tool to support the training program and track participants’ progress towards certification.
We plan to incorporate additional user training, such as training for temporary or visiting workers from outside the institution who currently do not have access to our laboratory. In addition, we are planning specific training designed for emergency first responders, such as security staff at the institute and the city’s police and fire departments. Because these groups are tasked with responding to incidents, such as terrorism or fires, they need to be familiar with the complex design and mechanical and engineering features of the BSL-4 facility. Our expanded training will orient them to the laboratory and its operating systems so they can respond as safely as possible to any emergency at our facility.
Our rigorous training program will reduce the risk of harm or exposure to laboratory staff working with highly pathogenic agents. We encouraged all laboratory users to provide feedback and thoughts regarding how to improve and further advance our training program. China intends to build 5–7 high-containment laboratories by 2025 (9). Our BSL-4 laboratory worker training system is the starting point for developing national norms for high-containment laboratory training and preparing qualified, maximum biocontainment laboratory scientists and facility operations specialists. More detail here.
Before you go…here is an interesting item on China tracking cell phone users and how that data is used. Welcome to the Chinese Communist Party….check yourself at the door.
BEIJING/HONG KONG (Reuters) – When the man from Hangzhou returned home from a business trip, the local police got in touch. They had tracked his car by his license plate in nearby Wenzhou, which has had a spate of coronavirus cases despite being far from the epicenter of the outbreak. Stay indoors for two weeks, they requested.
After around 12 days, he was bored and went out early. This time, not only did the police contact him, so did his boss. He had been spotted near Hangzhou’s West Lake by a camera with facial recognition technology, and the authorities had alerted his company as a warning.
“I was a bit shocked by the ability and efficiency of the mass surveillance network. They can basically trace our movements with the AI technology and big data at any time and any place,” said the man, who asked not to be identified for fear of repercussions.
Chinese have long been aware that they are tracked by the world’s most sophisticated system of electronic surveillance. The coronavirus emergency has brought some of that technology out of the shadows, providing the authorities with a justification for sweeping methods of high tech social control.
Artificial intelligence and security camera companies boast that their systems can scan the streets for people with even low-grade fevers, recognize their faces even if they are wearing masks and report them to the authorities.
If a coronavirus patient boards a train, the railway’s “real name” system can provide a list of people sitting nearby.
Mobile phone apps can tell users if they have been on a flight or a train with a known coronavirus carrier, and maps can show them locations of buildings where infected patients live.
Although there has been some anonymous grumbling on social media, for now Chinese citizens seem to be accepting the extra intrusion, or even embracing it, as a means to combat the health emergency.
“In the circumstances, individuals are likely to consider this to be reasonable even if they are not specifically informed about it,” said Carolyn Bigg, partner at law firm DLA Piper in Hong Kong.
NEW TECHNOLOGIES
Telecoms companies have long quietly tracked the movements of their users. China Mobile promoted this as a service this week, sending text messages to Beijing residents telling them they can check where they have been over the past 30 days. It did not explain why users might need this, but it could be useful if they are questioned by the authorities or their employers about their travel.
“In the era of big data and internet, the flow of each person can be clearly seen. So we are different from the SARS time now,” epidemiologist Li Lanjuan said in an interview with China’s state broadcaster CCTV last week, comparing the outbreak to a virus that killed 800 people in 2003.
“With such new technologies, we should make full use of them to find the source of infection and contain the source of infection.”
The industry ministry sent a notice to China’s AI companies and research institutes this week calling on them to help fight the outbreak. Companies have responded with a flurry of announcements touting the capabilities of their technology.
Facial recognition firm Megvii said on Tuesday it had developed a new way to spot and identify people with fevers, with support from the industry and science ministries. Its new “AI temperature measurement system”, which detects temperature with thermal cameras and uses body and facial data to identify individuals, is already being tested in a Beijing district.
SenseTime, another leading AI firm, said it has built a similar system to be used at building entrances, which can identify people wearing masks, overcoming a weakness of earlier technology. Surveillance camera firm Zhejiang Dahua says it can detect fevers with infrared cameras to an accuracy within 0.3ºC.
In an interview with state news agency Xinhua, Zhu Jiansheng of the China Academy of Railway Sciences explained how technology can help the authorities find people who might be exposed to a confirmed or suspected coronavirus case on a train.
“We will retrieve relevant information about the passenger, including the train number, carriage number and information on passengers who were close to the person, such as people sitting three rows of seats before and after the person,” he said.
“We will extract the information and then provide it to relevant epidemic prevention departments.”