Sidley Austin Reps Clinton Confidante in Benghazi Probe
Former DAG James Cole appears with Sidney Blumenthal for depo in House investigation.
Sidney Blumenthal, a longtime Clinton family friend, on Tuesday sat for a closed-door deposition in the House over his communications with former Secretary of State Hillary Clinton around the time of the 2012 attack on the U.S. diplomatic compound in Benghazi, Libya. James Cole, a former deputy attorney general under Eric Holder Jr. who is now a partner in Sidley Austin’s Washington office, represents Blumenthal.
*** Then this in a snippet:
The complaint, filed in October, names Sidley Austin and partner Edward McNicholas, alleging that they assisted one Joseph Garcia in securing millions in investments from a woman named Carrie Birkel. Birkel is looking to recover $1.5 million from the lawyers. Birkel claims that she had millions to invest after she got her $10 million divorce settlement — a divorce precipitated by Garcia providing her, unsolicited, with compromising photos of her husband, before introducing her to McNicholas, who vetted divorce lawyers for her on a $25,000 retainer.
As the complaint states:
Birkel’s claims arise out of a truly bizarre set of circumstances that would seem more appropriate for an episode of “Law and Order” than in reality.
Indeed.
Garcia, who is serving a 37-month sentence for similar activity, is a curious character by all accounts:
Garcia and his wife used multiple aliases to go along with numerous Social Security numbers. While peddling phony investments, Garcia would only reference his time as a Navy SEAL; the details were confidential. And he instructed his family to always have “go bags” packed should they need to flee one of the many lavish homes they rented across the country. More here.
***
For the confirmation hearing for Loretta Lynch, Statement of David B. Barlow ,Partner, Sidley Austin LLP made an endorsing and glowing recommendation for her.
Okay, so Sidley Austin is a very big and weird law firm with clear power in Washington DC, so what?
Well, let’s bring in the Russian lobby operation shall we? Sidley is the law firm of record to influence Congress and the White House against sanctions and political cover. The lobby agreement was generated by VTB Bank with Sidley Austin.
 You can read the full document/agreement here.
You can read the full document/agreement here.
The International Consortium of Investigative Journalists (ICIJ) reported in April that suspicious payments made by “Putin’s cronies may have, in some cases, been intended as payoffs, possibly in exchange for Russian government aid or contracts.”
The secret documents suggested that much of the money originally came from a bank in Cyprus, the ICIJ said, “that, at the time, was majority-owned by the Russian state-controlled VTB Bank.”
The documents also showed dozens of transactions, over more than a decade, involving people or companies linked to Putin, who has been in power at the Kremlin since 2000. Among those identified in the document were Putin’s longtime friend, cellist Sergei Roldugin, and the wife of Putin’s spokesman, Dmitry Peskov.
Putin has admitted there were transactions between him and Roldugin, but said there was no evidence of illegal activity.
Roldugin has dismissed any suggestion that he was either a custodian or a conduit for Putin’s money or assets.
*** Back in 2014:
VTB Bank and Bank of China today signed an Agreement on Cooperation in the presence of Russian President Vladimir Putin and Chinese President Xi Jinping.
The agreement was signed by First Deputy President and Chairman of VTB Bank Management Board Vasily Titov and Bank of China President Chen Siqing.
Under the agreement, the banks plan to develop their partnership in a number of areas, including cooperation on ruble and renminbi settlements, investment banking, inter-bank lending, trade finance and capital-markets transactions.
Vasily Titov said :”The signing of the agreement underscores VTB Group’s ongoing drive to grow its business in Asia, and will help facilitate the development of bilateral trade and economic relations between Russia and China, which have always been reliable partners.”
***
The Russian state-controlled bank VTB confirmed that its websites had been targeted by a cyber attack. The VTB is the second largest bank in the country. In December of 2016, Security Affairs reported:
Last week the Russian intelligence service FSB revealed that an unnamed foreign power is planning to undermine Russian Banks with cyber attacks and PSYOPS via social media.
According to the Russian intelligence, a group of servers in the Netherlands and leased to the Ukrainian web hosting firm BlazingFast were ready to launch an assault next Monday.
“Russia’s domestic intelligence agency, the Federal Security Service (FSB), said that the servers to be used in the alleged cyber attack were located in the Netherlands and registered to a Ukrainian web hosting company called BlazingFast.” reported the Reuters.
“The attack, which was to target major national and provincial banks in several Russian cities, was meant to start on Dec. 5, the FSB said in a statement.”
A few hours after the announcement made by the FSB, the Russian Central Bank confirmed that hackers have stolen 2 billion rubles, roughly 31 million US dollars, from accounts at the Russian central bank.
The Russian authorities haven’t disclosed the identity of the alleged threat actor behind the attack.
The Russian bank industry was recently hit by a string of cyber attacks, a few day ago experts from Kaspersky Lab revealed that at least five of Russia’s largest banks were targeted by massive DDoS attacks.
The attacks were powered by devices located in 30 countries across the world, including the United States.
The Russian Government was accused by Washington of interference in the recent US Presidential Election.
The Office of the Director of National Intelligence and the Department of Homeland Security have issued a joint security statement to accuse the Russian government of a series of intrusions into the networks of US organizations and state election boards involved in the Presidential Election.
“The U.S. Intelligence Community (USIC) is confident that the Russian Government directed the recent compromises of e-mails from US persons and institutions, including from US political organizations. The recent disclosures of alleged hacked e-mails on sites like DCLeaks.com and WikiLeaks and by the Guccifer 2.0 online persona are consistent with the methods and motivations of Russian-directed efforts. These thefts and disclosures are intended to interfere with the US election process” reads the statement.
There is more to the Obama administration and decisions than we know. This matter of cyber intrusions, sanctions, lawyers, Russian interference will not go away any time soon.




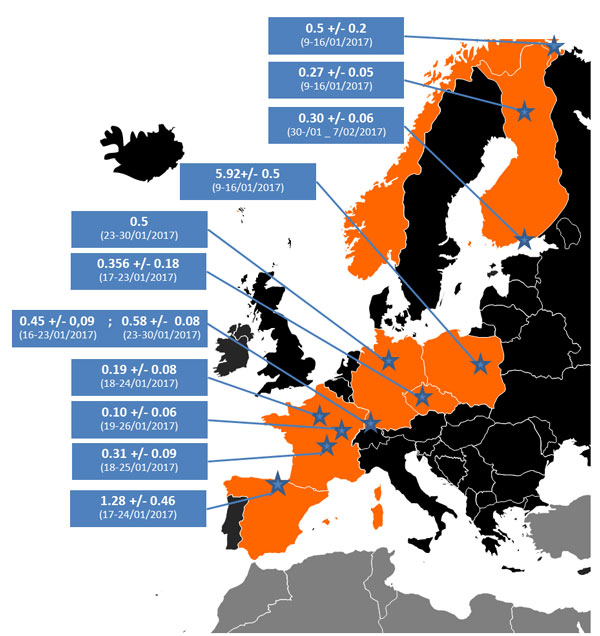
 Techviral
Techviral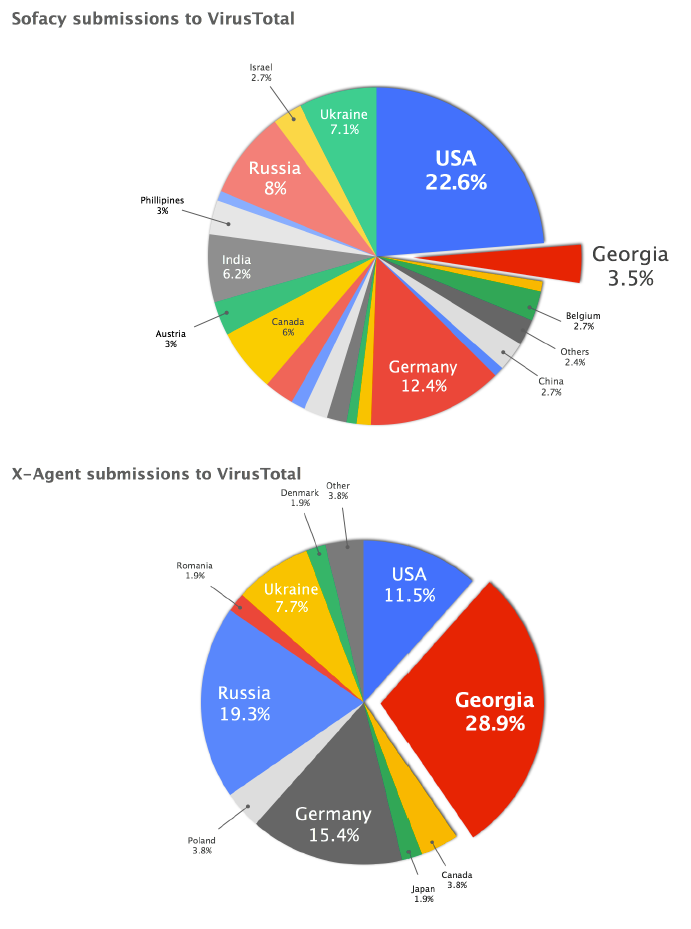
 Russian embassy Washington DC
Russian embassy Washington DC

























