The Russia-linked hackers behind last year’s compromise of a wide swath of the U.S. government and scores of private companies, including SolarWinds Corp. , have stepped up their attacks in recent months, breaking into technology companies in an effort to steal sensitive information, cybersecurity experts said.
In a campaign that dates back to May of this year, the hackers have targeted more than 140 technology companies including those that manage or resell cloud-computing services, according to new research from Microsoft Corp. The attack, which was successful with as many as 14 of these technology companies, involved unsophisticated techniques like phishing or simply guessing user passwords in hopes of gaining access to systems, Microsoft said.
***
Source: In a recent blog post to the company’s website, Microsoft’s corporate vice president of customer security and trust, Tom Burt, wrote that “state actor Nobelium has been attempting to replicate the approach it has used in past attacks by targeting organizations integral to the global IT supply chain.”
Nobelium is “attacking a different part of the supply chain: resellers and other technology service providers that customize, deploy and manage cloud services and other technologies on behalf of their customers,” according to the company.
Burt wrote that 609 Microsoft customers had been informed that they’d been attacked between July and October of this year close to 23,000 times “with a success rate in the low single digits.”
The attacks, according to the executive, were not aimed at a specific flaw in any of the systems, rather, they were “password spray and phishing” attacks, which are aimed at stealing credentials that grant the attackers access to privileged information.
The Russian state-backed hacking group is, according to Burt, “trying to gain long-term, systematic access to a variety of points in the technology supply chain, and establish a mechanism for surveilling – now or in the future – targets of interest to the Russian government.”
***
Over 600 Microsoft customers targeted since July
“Since May, we have notified more than 140 resellers and technology service providers that have been targeted by Nobelium,” said Tom Burt, Corporate Vice President at Microsoft.
“We continue to investigate, but to date we believe as many as 14 of these resellers and service providers have been compromised.”
As Burt added, in all, more than 600 Microsoft customers were attacked thousands of times, although with a very low rate of success between July and October.
“These attacks have been a part of a larger wave of Nobelium activities this summer. In fact, between July 1 and October 19 this year, we informed 609 customers that they had been attacked 22,868 times by Nobelium, with a success rate in the low single digits,” Burt said.
“By comparison, prior to July 1, 2021, we had notified customers about attacks from all nation-state actors 20,500 times over the past three years.”
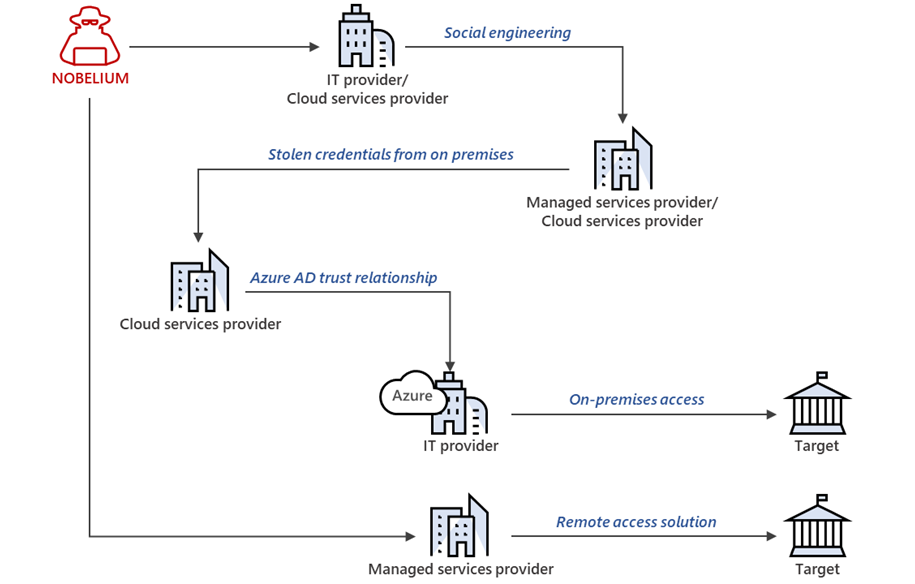
This shows that Nobelium is still attempting to launch attacks similar to the one they pulled off after breaching SolarWinds’ systems to gain long-term access to the systems of targets of interest and establish espionage and exfiltration channels.
Microsoft also shared measures MSPs, cloud service providers, and other tech orgs can take to protect their networks and customers from these ongoing Nobelium attacks.
Nobelium’s high profile targets
Nobelium is the hacking division of the Russian Foreign Intelligence Service (SVR), also tracked as APT29, Cozy Bear, and The Dukes.
In April 2021, the U.S. government formally blamed the SVR division for coordinating the SolarWinds “broad-scope cyber espionage campaign” that led to the compromise of multiple U.S. government agencies.
At the end of July, the US Department of Justice was the last US govt entity to disclose that 27 US Attorneys’ offices were breached during the SolarWinds global hacking spree.
In May, the Microsoft Threat Intelligence Center (MSTIC) also reported a phishing campaign targeting government agencies from 24 countries.
Earlier this year, Microsoft detailed three Nobelium malware strains used for maintaining persistence on compromised networks: a command-and-control backdoor dubbed ‘GoldMax,’ an HTTP tracer tool tracked as ‘GoldFinder,’ a persistence tool and malware dropper named ‘Sibot.’
Two months later, they revealed four more malware families Nobelium used in their attacks: a malware downloader known as ‘BoomBox,’ a shellcode downloader and launcher known as ‘VaporRage,’ a malicious HTML attachment dubbed ‘EnvyScout,’ and a loader named ‘NativeZone.’