Really, at issue for smoother government operations is upgrading computer software across all agencies. Some parts of government is operating on Microsoft products no longer supported while others in fact still use DOS. It was never a lack of appropriations by Congress but rather using those funds for other expenditures and in some cases paying bonuses or for travel to classes, seminars or training.
Rather than have the White House launch this initiative, an outside advisory group should be mobilized to introduce and demonstrate innovation as the private sector is the cutting edge. Each agency lead or cabinet secretary should submit a ‘wants and needs’ wish list such that outside agencies can address those potential solutions, otherwise we end up with the fraud and collusion endured with the launch of the front-end, back-end and website for Obamacare. Anyone remember that disaster?
Anyway, the Obama administration did an innovation summit and solutions showcase at the White House. Has the Trump administration been through those files? Google visited the Obama White House at least once a week. This may be a good mission for government in the end, as Google is in fact offering some assistance to some issues the Trump White House is considering.
***
Trump Pledges New Office to Bring Business Innovation to Government Operations
The Trump administration is launching a new office to spur innovation in government operations, the White House announced Monday, promising to give business acumen a more prominent role in federal activities.
President Trump tapped Jared Kushner, his son-in-law and senior adviser, to lead the new White House Office of American Innovation. The administration is billing the initiative — first reported by The Washington Post — as a SWAT team of former business executives. The goal, the White House said, is to shake up the status quo of the federal bureaucracy by infusing new ideas that allow private enterprises to succeed.
The administration billed the office as non-partisan, looking for any new ideas from both inside and outside government. It will aim to make improvements at every federal agency, including through technology overhauls, projects stemming from Trump’s promised infrastructure investment and procurement reform. A particular area of focus will be improving the Veterans Affairs Department. The White House said the innovation office will function as a service organization offering its assistance to agencies.
Trump formally created the office through a presidential memorandum issued Monday, in which he vowed the office would “solve today’s most intractable problems.” It will consist of about a dozen existing White House staff and consult with the directors of the Office of Management and Budget and the Office of Science and Technology Policy. After hearing from private sector leaders and government officials, the office will make policy recommendations to the president and “coordinate implementation of any resulting plans.”
When an agency is struggling with certain projects, the office and its team of White House advisers and business leaders will come in to offer creative and cost-efficient solutions. The team will look to ensure agencies keep pace with the latest innovations in the private sector.
The office will “apply the president’s ahead-of-schedule and under budget mentality to a variety of government operations and services, enhancing the quality of life for all Americans,” White House Press Secretary Sean Spicer said Monday. He conceded that “government is not business,” as there are certain things that “business would never do” and government must pick up the slack. Business leaders, he explained, can “help us deliver a better product, a better service to the American people.”
The business leaders participating in the project are “looking to give back in some way, shape or form,” Spicer said.
The new office is the latest in a series of moves from Trump aiming to streamline government operations. Earlier this month, he issued an order calling for a “comprehensive plan for reorganizing the executive branch,” which will require a “thorough examination” of every agency to identify “where money can be saved and services improved.” Another order has sent task forces to every agency to identify regulations for elimination or modification.
It also follows initiatives by several recent presidential administrations to modernize and streamline the way agencies do their work. On the technology side, a key focus of the new innovation office, President Obama launched the U.S. Digital Service in 2014 as a White House office to offer a “SWAT team” in troubleshooting high-priority information technology projects, as well as the General Services Administration’s 18F to provide consultant services to agencies looking to build up new technology-based offerings. Still, Spicer said some functions of government are so “outdated and unmodernized” that agencies are no longer serving their constituencies.
Through his Grace Commission, President Reagan tapped business executives to help identify waste and inefficiencies in government.
“What we need from you and your expertise and your associates is to literally come in to the various departments and agencies of government and look at them as if you were considering a merger or a takeover, and to see how modern business practices could be put to work to make government more efficient and more effective,” Reagan told his group in 1982. The commission eventually identified $424 billion in cuts. “There are a million things that you think of and take for granted every day in your business that you’ll find they don’t take it for granted in Washington, and it isn’t done that way, and that’s what it’s all about,” Reagan said.
President Clinton’s National Partnership for Reinventing Government promised to remake the federal government. Its National Performance Review proposed 1,200 changes to “serve customers better,” similar to Kushner’s promise to “achieve successes and efficiencies for our customers, who are the citizens.”




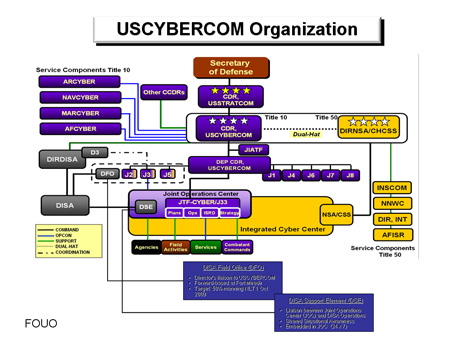

 Techviral
Techviral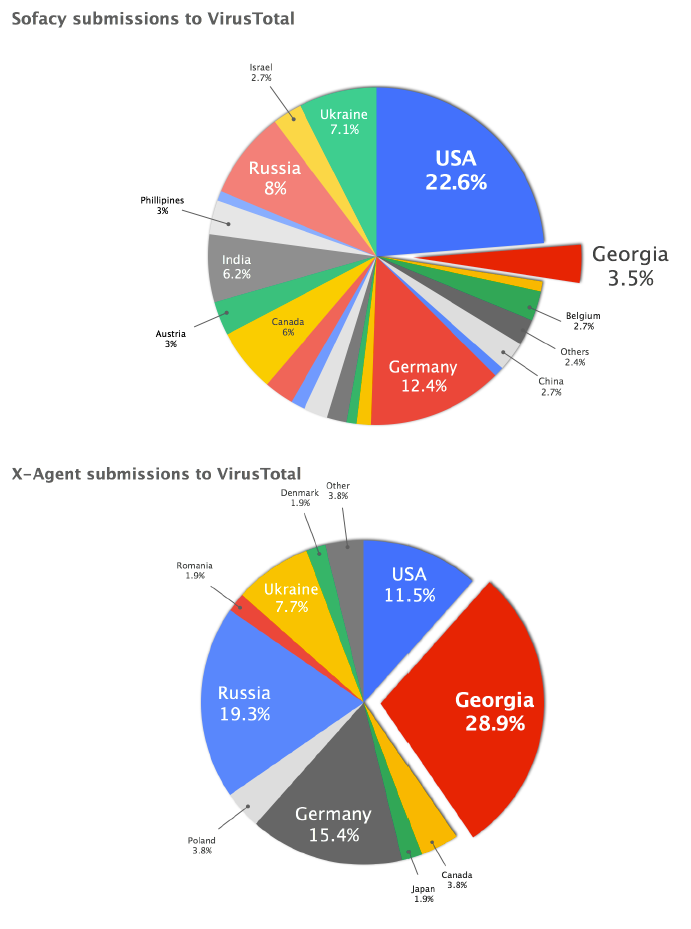
 Russian embassy Washington DC
Russian embassy Washington DC
