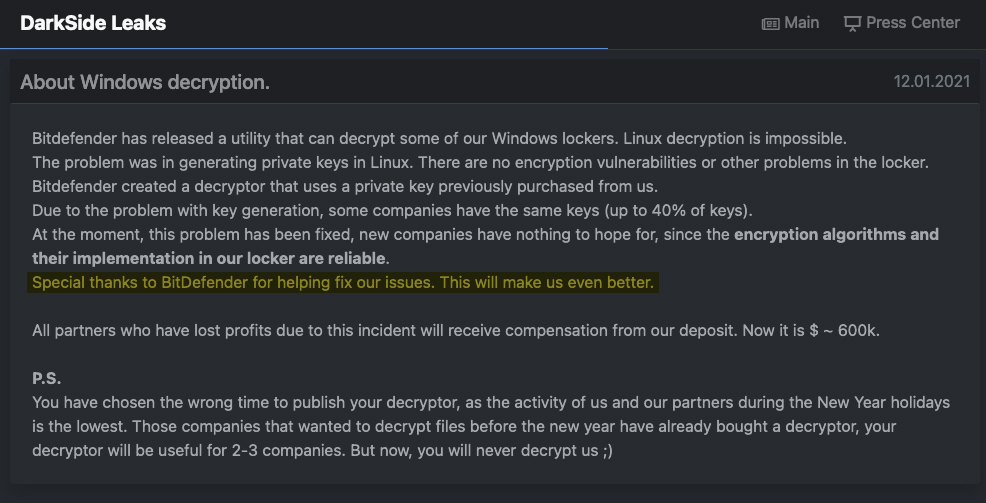
It is additional definition of the cyber war…
Operatives at the behest of Moscow have never passed up the opportunity to exploit a crisis in the Western world. It has gone on for years, back to the days of the KGB, now know as the SVR.
 Yet, does media keep making the same mistakes?
Yet, does media keep making the same mistakes?
Readers and researchers must validate the sources, all of them and check them often. Big media has fallen victim as well and some make corrections while others don’t bother.
Even CNN has admitted as much –>
Washington (CNN)Online platforms directed by Russian intelligence are spreading disinformation about two of the coronavirus vaccines being used in the US, a State Department spokesperson confirmed to CNN on Sunday.
The agency’s Global Engagement Center identified three Russian outlets — News Front, New Eastern Outlook and Oriental Review — that are spreading not only misinformation about the virus, but also regarding “international organizations, military conflicts, protests; and any divisive issue that they can exploit,” according to the spokesperson.“These sites all vary in their reach, tone, and audience — but they all are spreading Russian propaganda and disinformation. The State Department’s finding of a link between these sites and Russian Intelligence is a result of a joint interagency conclusion,” the spokesperson said.
French and German YouTubers, bloggers and influencers have been offered money by a supposedly UK-based PR agency with apparent Russian connections to falsely tell their followers the Pfizer/BioNTech vaccine is responsible for hundreds of deaths.
Fazze, an “influencer marketing platform … connecting bloggers and advertisers”, claimed to be based at 5 Percy Street in London but is not registered there. On Tuesday, it temporarily closed its website and made its Instagram account private.
The agency contacted several French health and science YouTubers last week and asked them, in poor English, to “explain … the death rate among the vaccinated with Pfizer is almost 3x higher than the vaccinated by AstraZeneca”.
The influencers were told to publish links on YouTube, Instagram or TikTok to reports in Le Monde, on Reddit and on the Ethical Hacker website about a leaked report containing data that supposedly substantiates the claim.
The article in Le Monde is about data reportedly stolen by Russian hackers from the European Medicines Agency and later published on the Dark Web. It contains no information on mortality rates. The pages on the other two sites have been deleted.
The influencers were asked to tell their subscribers that “the mainstream media ignores this theme”, and to ask: “Why some governments actively purchasing Pfizer vaccine, which is dangerous to the health of the people?”
The brief also included requests to “act like you have the passion and interest in this topic”, and to avoid using the words “advertising” or “sponsored” in posts or videos because “the material should be presented as your own independent view”.
Screen shots of the emails were posted on Twitter by Léo Grasset, a popular French science YouTuber with nearly 1.2m subscribers. Grasset said the campaign had a “colossal budget” but that the agency refused to identify its client.
The French investigative news site Numerama also published extracts from the exchanges, including Fazze’s exhortation to “encourage viewers to draw their own conclusions, take care of themselves and their loved ones”.
Mirko Drotschman, a German YouTuber and podcaster with 1.5 million subscribers, also posted a screenshot of an email asking him to take part in an “information campaign” about “a significant number of deaths” after the Pfizer shot.
“Please send us statistics on the age of your subscribers … and how much it would cost,” the mail concluded. The French investigative website Fact&Furious posted a mail describing Fazze’s budget as “considerable” and the fee as “the rate you wish”.
According to LinkedIn, Fazze’s management come from Moscow and have worked for an agency reportedly founded by a Russian entrepreneur.
French media have pointed to the similarities between Fazze’s message and the official Twitter account of Russia’s Sputnik V – a viral vector vaccine like AstraZeneca – which has repeatedly claimed “real world data” shows they are “safer and more efficient” than mRNA vaccines.
An EU study last month accused Russian and Chinese media of “state-sponsored disinformation” aimed at sowing mistrust in western vaccines by sensationalising safety concerns, making “unfounded links between shots and deaths in Europe”, and promoting Russian and Chinese vaccines as superior.