The Drive: U.S. officials believe that a DJI Mavic 2, a small quadcopter-type drone, with a thick copper wire attached underneath it via nylon cords was likely at the center of an attempted attack on a power substation in Pennsylvania last year. An internal U.S. government report that was issued last month says that this is the first time such an incident has been officially assessed as a possible drone attack on energy infrastructure in the United States, but that this is likely to become more commonplace as time goes on. This is a reality The War Zone has sounded the alarm about in the past, including when we were first to report on a still unexplained series of drone flights near the Palo Verde nuclear powerplant in Arizona in 2019.
ABC News was first to report on the Joint Intelligence Bulletin (JIB) covering the incident in Pennsylvania last year, which the Department of Homeland Security (DHS), Federal Bureau of Investigation (FBI), and the National Counterterrorism Center (NCTC) published on Oct. 28, 2021. The document, which ABC obtained a copy of, but only released a small portion of, is marked unclassified, but parts also labeled Law Enforcement Sensitive (LES) and For Official Use Only (FOUO). Other outlets have since obtained copies of this document, which reportedly says that this likely attack took place on July 16, 2020, but does not identify where the substation in question was located.
DHS via ABC News
RELATED READING: FBI Strategic Intelligence/Assessment on Domestic Terrorism
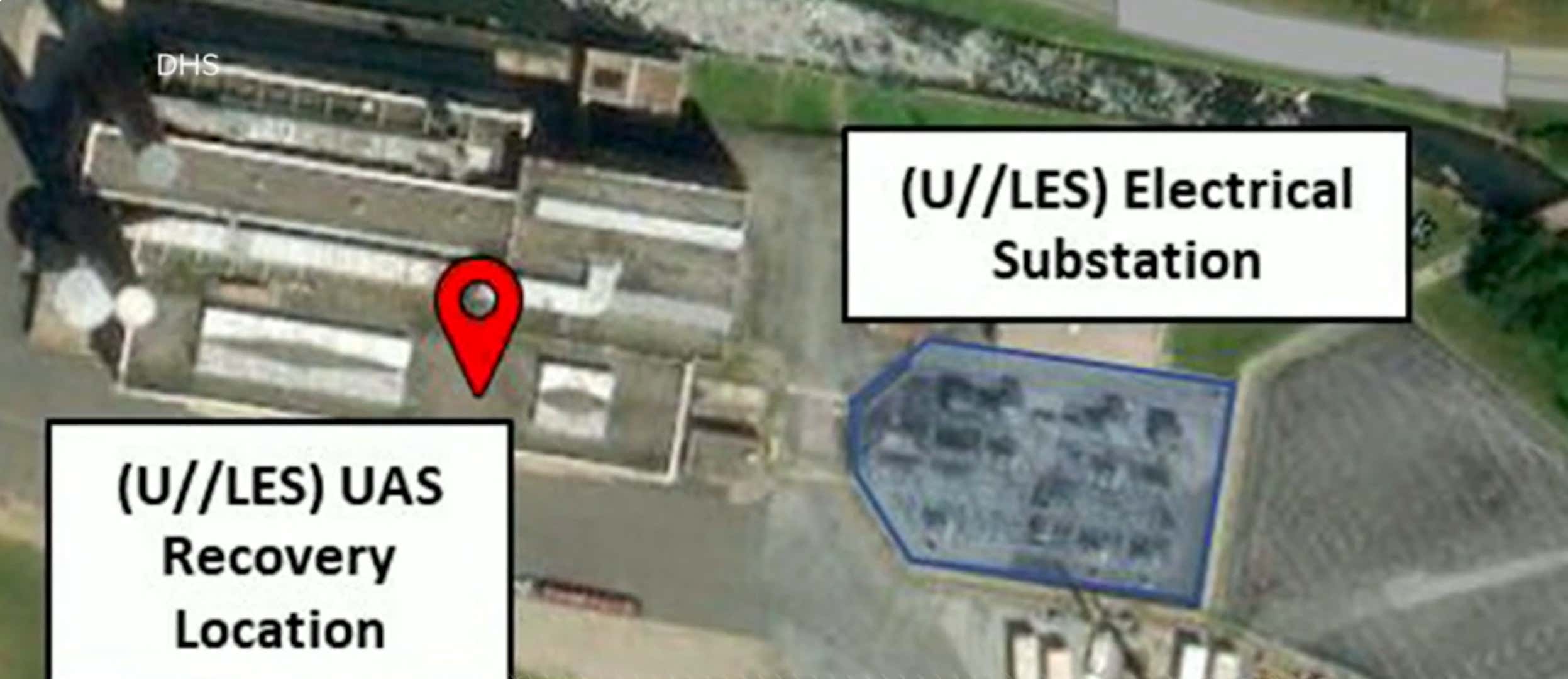
A portion of an annotated satellite image from a US Joint Intelligence Bulletin regarding a likely attempted drone attack on a power substation in Pennsylvania in 2020.
“This is the first known instance of a modified UAS [unmanned aerial system] likely being used in the United States to specifically target energy infrastructure,” the JIB states. “We assess that a UAS recovered near an electrical substation was likely intended to disrupt operations by creating a short circuit to cause damage to transformers or distribution lines, based on the design and recovery location.”
ABC and other outlets have reported that the JIB says that this assessment is based in part on other unspecified incidents involving drones dating back to 2017. As already noted, The War Zone previously reported on another worrisome set of incidents around Arizona’s Palo Verde Generating Station, the largest nuclear power plant in the United States in terms of its output of electricity, in 2019. In the process of reporting that story, we uncovered other reported drone flights that prompted security concerns near the Limerick Generating Station nuclear power plant in Pennsylvania earlier that year.
The Night A Mysterious Drone Swarm Descended On Palo Verde Nuclear Power Plant By Tyler Rogoway and Joseph Trevithick Posted in The War Zone
Here’s What’s In New Guidelines For Defending Infrastructure Against Drone Attacks By Brett Tingley Posted in The War Zone
The Y-12 Nuclear Development Site Has Deployed Its First Anti-Drone System By Brett Tingley Posted in The War Zone
Some Chinese-Made Drones Cleared By Pentagon For U.S. Government Use By Brett Tingley Posted in The War Zone
Is The United States Firing Off “Electricity Bombs” in Syria? By Joseph Trevithick Posted in The War Zone
“To date, no operator has been identified and we are producing this assessment now to expand awareness of this event to federal, state, local, tribal, and territorial law enforcement and security partners who may encounter similarly modified UAS,” the JIB adds.
Beyond the copper wire strung up underneath it, the drone reportedly had its camera and internal memory card removed. Efforts were taken to remove any identifying markings, indicating efforts by the operator or operators to conceal the identifies and otherwise make it difficult to trace the drone’s origins.

DHS via ABC News
A low-quality image showing the drone recovered after the likely attempted attack in Pennsylvania. The green lines are the nylon cables. A copper wire was attached to the bottom ends of both lines.
It’s unclear how much of a threat this particular drone posed in its modified configuration. The apparent intended method of attack would appear to be grounded, at least to some degree, in actual science. The U.S. military employed Tomahawk cruise missiles loaded with spools of highly-conductive carbon fiber wire against power infrastructure to create blackouts in Iraq during the first Gulf War in 1991. F-117 Nighthawk stealth combat jets dropped cluster bombs loaded with BLU-114/B submunitions packed with graphite filament over Serbia to the same effect in 1999.
Regardless, the incident only underscores the ever-growing risks that small drones pose to critical infrastructure, as well as other civilian and military targets, in the United States. If this modified drone did pose a real risk, it would also highlight the low barrier to entry to at least attempt to carry out such attacks. New DJI Mavic 2s can be purchased online right now for between $2,000 and $4,000.
The technology is so readily available that non-state actors around the world, from terrorists in the Middle East to drug cartels in Mexico, are already employing commercial quad and hexacopter-type drones armed with improvised explosive payloads on a variety of targets on and off more traditional battlefields. This includes attempted assassinations of high-profile individuals.
The U.S. government is finally coming to terms with these threats and there are certainly some steps being taken, at least at the federal level, to protect civilian and domestic military facilities against small drones. At the same time, it is equally clear that there is still much work to be done.
This particular incident in Pennsylvania last year highlights separate security concerns relating to Chinese-made small drones that are now widely available in the United States and are even in use within the U.S. government. DJI, or Da Jiang Innovations, is by far the largest Chinese drone maker selling products commercially in the United States today and has been at the center of these debates in recent years.
Whether or not the modified Mavic 2 posed a real danger in this instance or if this was truly the first-ever attempted drone attack on energy infrastructure in the United States, it definitely reflects threats are real now and will only become more dangerous as time goes on.



 . There are even beagle puppy farms….
. There are even beagle puppy farms….
