Primer: President Trump called on the U.S. attorney in Minnesota to investigate a report of alleged illegal ballot harvesting by supporters of Rep. Ilhan Omar in Minnesota.
Project Veritas, an investigative reporting project that uses undercover journalists, released a report on Sunday night that claimed Omar’s supporters in Minneapolis were illegally collecting blank ballots and bragging about it on social media. Trump condemned the actions depicted in the video in a tweet posted on Sunday night.
“This is totally illegal. Hope that the U.S. Attorney in Minnesota has this, and other of her many misdeeds, under serious review??? If not, why not??? We will win Minnesota because of her, and law enforcement. Saved Minneapolis & Iron O Range!” Trump wrote.
The report focuses on ballot harvesting, a practice Trump and other Republicans have condemned for years. Ballot harvesting is when a third party, often volunteers or campaign staff, collects ballots directly from the homes of voters to deliver them to polling stations. The third-party harvesters can be paid hourly for their work.
Most states that allow voters to have a third party deliver their ballots have a limit on the number of ballots that can be collected by an individual. California is the exception, which allows unlimited ballot collection so long as the harvesters are paid hourly and not per ballot. Full article here.
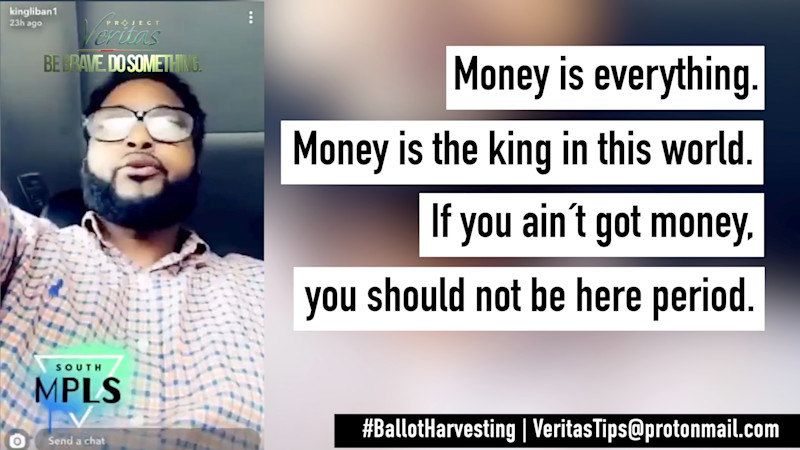
- Ballot Harvester Liban Mohamed: “Money is Everything. Money is the King in this World. If You Got No Money, You Should Not Be Here, Period. You Know What I am Saying? Money is Everything and a Campaign is Managed By Money.”
- Mohamed: “Numbers Do Not Lie. Numbers Do Not Lie. You Can See My Car is Full. All These Here Are Absentee Ballots. Can’t You See? Look at All These, My Car is Full.”
- Paid Voter: “When We Sign The Voting Document and They Fill It Out Is When They Give Us The Money,”… “The Minute We Signed The Thing [Ballot] For The Election. That’s When We Get paid.”
- Ballot Harvesting Triangle: River Plaza Apartments, Horn Towers seniors Community and 980 Hennepin Polling Site All Subject to Fraud
- Minneapolis Somali Community Insider: “It’s an Open Secret” … “She [Ilhan Omar] Will Do Anything That She Can Do To Get Elected and She [Omar] Has Hundreds of People on The Streets Doing That.”
- Seniors at Horn Towers Ballots Compromised; Harvester: We “Request” Ballots For The Seniors and Then Take Them Away.
[Minneapolis–Sept. 27, 2020] Project Veritas investigators revealed a ballot harvesting scheme here involving clan and political allies and associates of Rep. Ilhan Omar (D.-Minn.) in the first of a series of reports.
***
“Numbers don’t lie. Numbers don’t lie. You can see my car is full. All these here are absentees’ ballots. Can’t you see? Look at all these, my car is full. All these are for Jamal Osman… We got 300 today for Jamal Osman only,” said Liban Mohamed in a series of Snapchat videos posted July 1 and July 2 on his own Snapchat profile.
Mohamed said he was collecting the ballots to help his brother win the city’s Aug. 11 special election for a vacant Ward 6 city council race—which was held the same day as the primary for Omar’s MN-05 congressional seat. Ward 6 is the heart of the city’s Somali community and the Omar’s political base.
James O’Keefe, the founder and CEO of Project Veritas, said: “Ballot harvesting is real and it has become a big business. Our investigation into this ballot harvesting ring demonstrates clearly how these unscrupulous operators exploit the elderly and immigrant communities—and have turned the sacred ballot box into a commodities trading desk.”
O’Keefe said, “We are showing Americans what is really going on in one of our great cities—but, it’s not me saying—we have the operators on tape saying it all themselves.”
Our investigation found that among three locations inside Ward 6, a ballot harvesting triangle, where the scheme operates: the Riverside Plaza apartments, the senior citizen community at Horn Towers and the Minneapolis Elections and Voter Services office at 980 E. Hennepin Ave., which also functions as a voting location and ballot drop-off site.
Mohamed continued: “Money is everything. Money is the king in this world. If you got no money, you should not be here period. You know what I am saying.”
*** 
Mohamed said that his political methods are interwoven with money. “Money is everything and a campaign is managed by money. You cannot campaign with $200 or $100 you got from your grandmother or grandfather. You cannot campaign with that. You gotta have an investment to campaign. You gotta have fundraisers.”
Hennepin County Attorney Jeff Wojciechowski told a Project Veritas journalist on a recorded line the ballot harvesting conduct described to him was: “Illegal, and we will be investigating.”
Somali insider stepped forward to expose election corruption in Minneapolis
Central to the Project Veritas investigation was Omar Jamal, political insider active in the city’s Somali community. Jamal works with the Ramsey County Sheriff Department and is the chairman of the Somali Watchdog Group. “I have been involved in the community for the last 20 years.”
*** 
“Omar Jamal is the latest brave Project Veritas Insider to come forward and expose a voter fraud scheme in Minnesota that will shock you,” said O’Keefe. “When we spoke with Omar Jamal, he actually repeated part of our PV Insider motto: ‘Do Something.’”
Jamal said he was motivated to reach out to Project Veritas, because he wants to eliminate the corruption that weakens his community, such as the ballot harvesting practiced by Minnesota’s Democratic-Farmer-Labor Party, in which Ilhan Omar has emerged as a rising power broker.
“It’s an open secret,” he said. “she [Omar] will do anything that she can do to get elected and she has hundreds of people on the streets doing that.”
The political insider said he hopes there is still time to clean up elections in the country.
“If American people don’t pay attention to what’s happening, the country will collapse,” he said.
“The regulations, if you ignore that and you let corruption and fraud become a daily business and then tough luck, the country will not exist as they [Americans] know it,” Jamal said.
“I’m afraid it’s already too big to stop, you know, maybe it’s too late. Maybe it’s already too big to stop,” he said. “There’s a lot of people invested in this, you know, and they don’t care how they did it: ‘We win,’ and that’s it.”
Ballot Harvester described how his own ballot was harvested by Omar operatives
Jamal, as part of his participation in the investigation, interviewed a Somali-American who functions as a ballot harvester his community. In the interview, the harvester described how he was paid to vote in the Aug. 11 special election and primary, along with a Project Veritas undercover journalist.
The harvester said Somali-American vote-buying operatives from the Omar machine came to his apartment building to oversee the voter filling out the paperwork.
Omar operatives request the ballots and fill them out for the voters, he said.
“They come to us. They came to our homes. They said: ‘This year, you will vote for Ilhan,’” he said. “They said: ‘We will make the absentee ballots. We will fill out the forms for you and when you get them back, we will again fill it out and send it.”
There was no need to go to the voting site, because the Omar operatives told him: “You stay home and you will not go to the place.”
After the ballots are signed and documented the harvester said he got paid.
“When we sign the voting document and they fill it out is when they give us the money,” he said. “The minute we signed the thing [ballot] for the election. That’s when we get paid.”
Ballot harvester describes how he targets elderly voters
Omar Jamal: So they [ballot harvesters] will request it [the ballot] for the elderly?
Ballot harvester: Yes. They [ballot harvesters] request [the ballot] for them [the elderly].
Omar Jamal: And it [the ballot] is taken away from them [elderly]?
Ballot Harvester: Yes. It [the ballot] is taken away from them [elderly].
DFL operative describes why he did not speak up about the election corruption
A political operative, known as Jamal, for Minnesota’s Democratic-Farmer-Labor Party, which functions as the state’s official chapter of the national Democratic Party, told a Project Veritas undercover journalist he was afraid to speak up when he saw abuses of the voting system.
“They fight you if you speak up,” Jamal said. “Like what? Like what can I do? Like get jumped? Hell no. They ain’t got—no, no, I’m good.”
The DFL operative said he also saw Mohamed’s Snapchat videos. “I was looking at them and they were not filled. They were blank.”
*** 
“Liban didn’t get it in a unique way,” he said. “He just gets them the way that everybody before him, or even, maybe even after him will do, which is go to the elders, maybe bait them and collect and help to them and he’s helping them–so, I think that’s the process of collecting from the seniors, from their buildings.”
The Insider said another corrupting effect is the miseducation of the city’s new immigrants.
“We have to understand that the immigrants mostly, here now, are first generation immigrants,” he said.
“Through no fault of their own the new immigrants are learning about democracy from the ballot harvesters,” he said. “When they get here, because of that ignorance, not knowing how this, all things work. Sometimes they even think it’s legal.” – he said.
Documented ballot harvesting, vote buying violates federal and state law
Jered Ede, the chief legal officer for Project Veritas, said Mohamed and his confederates may have violated both state and federal election laws, some carrying a maximum penalty of five years imprisonment.
“The federal laws, 18 USC §597 and 52 U.S.C. §10307(c), are quite clear,” he said. “In the case of 18 USC §597, it is punishable by up to two years in prison and in the case of 52 USC §10307 it’s punishable by up to $10,000 in fines and up to five years in prison.”
The Minnesota statute, 211B.13(1) prohibits paying a person or receiving money to register to vote or to vote, he said. “This is a state felony punishable by more than one-year imprisonment.”
Beyond paying voters, there are also state and federal laws regarding intimidation of voters, he said.
“The federal laws 52 USC §20511, 18 USC §594 and 52 USC §10307(b) and the Minnesota statue 211B.07 law prohibit anyone from using undue influence threats intimidation or fraud to influence a person’s vote or to influence them to vote at all,” he said.
It’s also a violation of federal law for anyone who votes for others illegally:
“The punishment under 52 USC §10307(e) also goes up to five years’ incarceration and a $10,000 fine,” he said.
“In addition to those statutes, Minnesota has another statute, 211B.11(3), which makes it a misdemeanor to induce or persuade a voter to vote for or against a candidate, while transporting the voter to the polls,” he said.
Former campaign worker comes forward
One Minneapolis-based source, who is a former political worker, told Project Veritas journalists on the night of the Aug. 11 special election and primary that Omar’s campaign manager Ali Isse Gainey is a key player in the ballot harvesting scheme.
*** 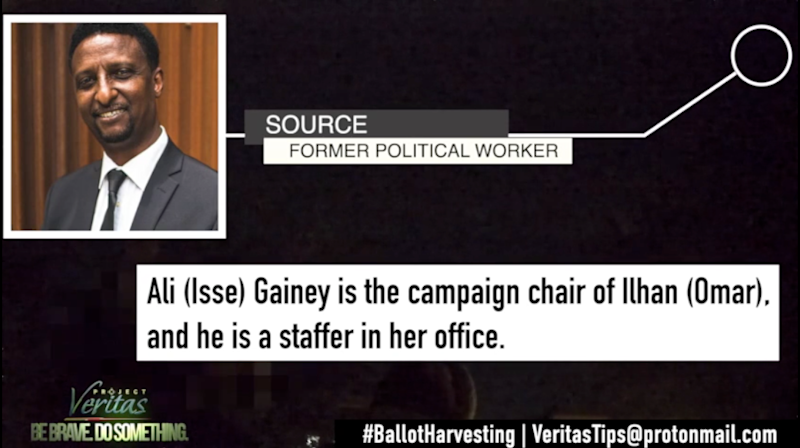
The source said, “[Gainey], who’s working in Ilhan’s campaign is the one who is managing the voting place. They bring them. They line them. They put the open ballots in there and then they take them in and say, ‘Here,’ and the people mark [the ballots].”
The practice is pervasive she said.
“They’re accepting temporary addresses; they’re accepting all kind of shenanigans,” she said.
“People that are showing their ID: ‘I moved 30 days ago, my ID’s not come back.’ ‘OK, just give us the last four of your social and tell us the address,’ and then somebody else will say ‘Yeah.’ They will send people who are helping them vote and saying: ‘Yeah, I can vouch for this madness,’” she said.
The former campaign worker said Isse and the Omar-connected political machine have turned voter fraud into an organized process for application, registering and tracking the harvested ballots from collection to delivering to polls.
“They have perfected this system,” she said. “This is what they do. They will tell you we are applying for your ballot. They take a picture of your social security and your driver’s license. They have a database. When the ballot comes, they track it, sometimes, they make fake emails. They track the ballot. Then, they come and pick up the ballot—unopened,” she said.
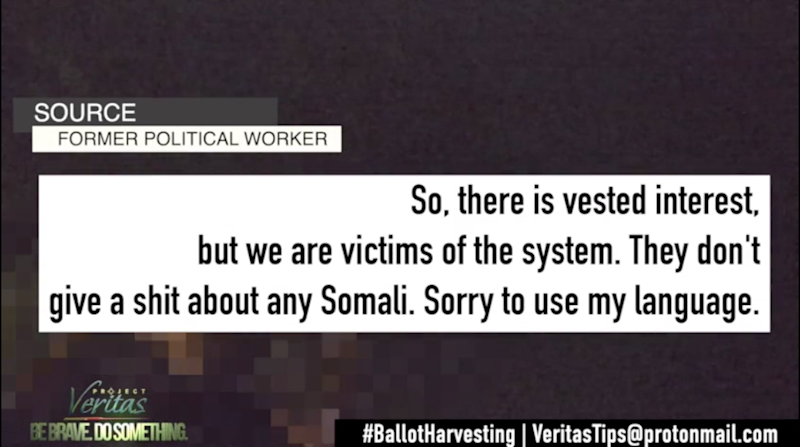
“So, there is vested interest, but we are victims of the system,” she said. “They [the Omar political machine] don’t give a shit about any Somali.”
*** 
Our source was disgusted by the exploitation of her vulnerable community.
“No, and the ones that didn’t vote on ballots, the young people, and the women and stuff, they were paying cash, cash, cash,” she said. “They were carrying bags of money. And when you vote and they mark you off, then you get in the van, they give you the cash.”






