Primer: Capping off months of controversy, espionage claims and international intrigue, the U.S. government ban on Kaspersky Lab software has been signed into law. The ban, wedged into the Fiscal Year 2018 National Defense Authorization Act (NDAA), would preclude all federal computers and connected networks from using antivirus software made by the Russian cybersecurity firm.
The Kaspersky ban, which appears in Section 1634 of the 2018 NDAA, reads as follows:
“No department, agency, organization, or other element of the Federal Government may use, whether directly or through work with or on behalf of another department, agency, organization, or element of the Federal Government, any hardware, software, or services developed or provided, in whole or in part, by—
(1) Kaspersky Lab (or any successor entity);
(2) any entity that controls, is controlled by, or is under common control with Kaspersky Lab; or
(3) any entity of which Kaspersky Lab has majority ownership.”
Last week, Kaspersky Lab announced that it would close its Washington, D.C. offices, which it stated were “no longer viable.”
***
Since the founding of the Shanghai Cooperation Organization in 2009, Russian and Chinese officials have frequently discussed joint cybersecurity initiatives. A relatively substantial degree of collaboration was formalized in the context of heightened Russo-Chinese cooperation in 2014 and 2015, with both countries signing an agreement that included cybersecurity cooperation provisions in May of last year. In the words of the agreement’s signatories, its purpose was to limit the use of informational technology designed “to interfere in the internal affairs of states; undermine sovereignty, political, economic and social stability; [and] disturb public order.”
Digital Sovereignty
This emphasis on digital sovereignty remains a central tenet of both countries’ cyber policies, even as cooperation on the issue has ebbed and flowed. The non-aggression elements of the 2015 agreement floundered in the implementation stage, in part due to ambiguous language but largely as a result of continued Chinese cyberespionage. This activity rose to unprecedented levels in 2016, with Russian cybersecurity company Kaspersky Labs reporting 194 Chinese cyberattacks in the first seven months of the year alone—compared to just 72 in 2015. These attacks targeted Russian government agencies, the defense and aerospace industries, and nuclear technology companies. And they’re probably underreported: A Kaspersky Labs spokesperson told Bloomberg that only around 10% of their corporate clients exchange data related to hacks with their security network. More here.
Russia Seeks to Build Alternative Internet
TJF: Numerous Russian sources report that efforts are underway to produce a new and independent internet that would align Russia more closely with the BRICS countries (Brazil, Russia, India China and South Africa) while giving Russian political authorities greater control over what they refer to as “digital sovereignty.” In late November, the RBK news agency reported on the proceedings of a recent meeting of the Security Council of the Russian Federation (SCRF), which underscored the national security threats posed by the increasing vulnerability of the global Internet (RBK, November 28). The publicly available SCRF website confirms that a high-level meeting on cyber security did take place, but it does not expand upon it in detail (Scrf.gov.ru, October 25). Russia’s state-managed propaganda mouthpiece RT, however, cited “members of the Security Council” as stating that “the increased capabilities of Western nations to conduct offensive operations in the informational space as well as the increased readiness to exercise these capabilities pose a serious threat to Russia’s security” (RT, November 28). RT also noted that President Vladimir Putin set August 1, 2018, as the deadline for creating an alternative to the Internet.
The creation of an alternative internet—which would allow the governments of Russia and the BRICS countries to control the addressing and routing of electronic communications within their territory—raises many complex questions. For one thing, the establishment of a disjointed and competitive sphere of cyberspace threatens to disrupt and potentially fragment the existing conventions of global Internet practice. Moreover, the creation a “counter-net” would necessitate the establishment of an alternative system of identification, addressing and routing information through a new information network operating in a new “domain name system,” a new DNS. The existing DNS is based on a unique number associated with each originating and terminating point for every Internet transmission, coded in the form of a packet of digital information. The idea of the “RU NET” has long been discussed in post-Communist countries. But until now, this idea has only referred to the Russian-language-speaking Internet activities originating from servers in Russia or in other post-Soviet countries where Russian is recognized as an official language—not to a separate internet architecture (APN, December 14, 2016).
The global Internet is already a network of networks, consisting of a broad common space but with some segmented spheres of activity. Gaining complete control over a specific domain in the cyber-sphere, however, would require gaining autonomy. Full control over the Internet (or any segment therein) could only be achieved by creating “the ability to set policies for naming, addressing and routing” transmissions (Milton Mueller, Will the Internet Fragment?, 2017, p. 22). That, in turn, would require establishing control over the domain name system.
Earlier attempts by Russian authorities to gain control over the digital sphere focused on taking charge of the physical hardware of the Internet, such as transmission facilities, and asserting authority over the places where data resides, particularly web servers. In 2014, Russia’s Ministry of Communications and Mass Media specified data localization requirements in the federal communications legislation (Federal Law No. 242) (Minsvyaz.ru, accessed December 13). The law requires data operators in Russia to store all personal data of citizens of the Russian Federation in databases located inside Russia. This legislation was further extended in December 2016 by a set of measures by President Putin to establish a “digital economy” in Russia (Kremlin.ru, December 1, 2016). The most recent Law on “Security of Critical Infrastructure” was passed in July 2017, and is scheduled to go into effect January 1, 2018 (Pravo.gov.ru, July 27).
In order to control the flow of information not in compliance with the legislation, the idea of blocking transmission through physical facilities located on the territory of the Russian Federation led to the establishment of a single register of websites, maintained by the Federal Service for Supervision of Communications, Information Technology and Mass Media (Roskomnadzor). In an effort to conduct this “filtering,” Roskomnadzor developed and implemented a so-called “blacklist” (Rkn.gov.ru, accessed December 13). But while the blacklist succeeded in blocking some websites it identified as unwanted, it also had the effect of blocking websites linked to those, effectively creating a self-censoring network. Roskomnadzor has now stepped back from this practice, correcting many of those problems of excessive blockage but has nonetheless reasserted the intention to more vigorously pursue the policing of websites (Rkn.gov.ru, December 8). Creating the establishment of a separate domain naming system goes considerably further than efforts to “filter” websites, even though Igor Shchyogolev, the staff member of the President’s Office assigned to mass communications, has insisted the idea is not to fragment the Internet (TASS, March 27, 2017)
The robustness of the current Internet naming conventions probably can be attributed to the fact that the Internet emerged in its early days more as a computer science experiment than as an effort to create a new format for global communication, commerce and governance. The identification of parties communicating on the Internet was established through naming protocols established for convenience and by convention, not for control. But the Internet grew so quickly that management responsibility was turned over to a new body, the Internet Corporation for Assigned Names and Numbers (ICANN), in September 1998, which, on October 1, 2016, was re-chartered as a fully independent, non-governmental organization.
The functions of ICANN quickly attracted international competition. Some governments sought to promote a government-centric framework for addressing and naming conventions, while other parties sought to maintain a multiple-stakeholders approach. The failure of the Russian government and others to prevail in winning greater control for states is what has led to Moscow’s intention to create a “counter-net.” The question of whether an autonomous and detachable “segment” of cyberspace could be fashioned by the Kremlin without resulting in self-imposed isolation is an issue with far-reaching implications.
–Gregory Gleason
Category Archives: China
Deport Those Chinese Operatives Now
Have you read the newly released book titled ‘Bully of Asia’ by Steven W. Mosher? China is the single largest threat to global stability and Russia and Iran in second and third place.
Have you heard of the Thucydides Trap? China is an ascending power and just who is paying attention? Have you studied the fact that China is a major enabler of North Korea’s aggression behavior including the most recent launch of the intercontinental ballistic missile?
China is a thief. China has dispatched operatives throughout the West under the guise of cultural exchanges, students, temporary workers and journalists. It is all about espionage and cyberwar.
Hey State Department and DHS, get these operatives outta here. By the way, are there any sanctions on China with regard to PLA Unit 61398?
Have you wondered what happened to that Obama Asia Pivot that he announced in 2011? The United States needs to pivot again and now.
Why?
This Beijing-Linked Billionaire Is Funding Policy Research at Washington’s Most Influential Institutions
The Chinese Communist Party is quietly reshaping public opinion and policy abroad.
FP: The Johns Hopkins University’s School of Advanced International Studies (SAIS), located just a short walk from Dupont Circle in Washington, D.C., is one of the top international relations schools in the United States. Its graduates feed into a variety of government agencies, from the State Department to the CIA, and the military. Its China studies program is especially well known; many graduates come away with expert knowledge of the language, culture, and politics of the United States’ most important strategic competitor.
In August, SAIS announced a new endowed professorship in the China Studies department as well as a new research project called the Pacific Community Initiative, which aims to examine “what China’s broader role in Asia and the world means for its neighbors and partners.”
What the SAIS press release did not say is that the money for the new initiatives came in part from the China-United States Exchange Foundation (CUSEF), a Hong Kong-based nonprofit. CUSEF is a registered foreign agent bankrolled by a high-ranking Chinese government official with close ties to a sprawling Chinese Communist Party apparatus that handles influence operations abroad, known as the “united front.”
The China-U.S. Exchange Foundation’s partnership with a premier U.S. academic institution comes amid a Chinese Communist Party push to strengthen its influence over policy debate around the globe. The Chinese government has sought to repress ideas it doesn’t like and to amplify those it does, and its efforts have met with growing success.
Even as Washington is embroiled in a debate over Russian influence in U.S. elections, it’s China that has proved adept at inserting itself in American politics.
“The Chinese approach to influence operation is a bit different than the Russian one,” said Peter Mattis, a fellow at the Jamestown Foundation. “The Russian one is much more about an operational objective and they work backward from that objective, saying, ‘How do we achieve that?’” But on the Chinese side, Mattis said, “they focus on relationships — and not on the relationships having specific takeaway value, but that someday, some way, those relationships might become valuable.”
The Chinese seek a kind of “ecological change,” he explained. “If they cultivate enough people in the right places, they start to change the debate without having to directly inject their own voice.”
The China-U.S. Exchange Foundation was founded in 2008 by Tung Chee-hwa, a Hong Kong shipping magnate who later served as the chief executive of the former British colony, where he championed the benefits of close ties to Beijing. Tung’s Hong Kong-based nonprofit conducts academic and professional exchanges, bringing U.S. journalists, scholars, and political and military leaders to mainland China. It also has funded research projects at numerous U.S. institutions, including the Brookings Institution, the Center for Strategic and International Studies, the Atlantic Council, the Center for American Progress, the East-West Institute, the Carter Center, and the Carnegie Endowment for Peace.
Tung’s foundation’s ties to the united front are indirect, but important. Tung currently serves as the vice chairman of one of the united front’s most important entities — the so-called Chinese People’s Political Consultative Conference, which is one of China’s two rubber-stamp assemblies.
The body is one of Beijing’s most crucial tentacles for extending influence.
In its newest project with SAIS, the foundation describes the Pacific Community Initiative as a “joint research project.” David Lampton, director of the university’s China Studies Program, said in an August press release that the new professor “will also be responsible for running our Pacific Community Initiative and work closely with the China-U.S. Exchange Foundation in Hong Kong.”
Lampton also confirmed that CUSEF funded the new programs. “Both the Initiative and the Professorship were made possible through the support of the China-U.S. Exchange Foundation,” he said in an emailed statement to Foreign Policy.
But he denied that CUSEF had attached any intellectual strings to its funding.
“There are absolutely no conditions or limitations imposed upon the Pacific Community Initiative or our faculty members by reason of a gift or otherwise,” Lampton told FP. “We have full confidence in the academic integrity and independence of these endeavors.”
CUSEF denies it acts as a vehicle for Beijing’s ideological agenda or has “any connections” to the united front. “We do not aim to promote or support the policies of any one government,” wrote a spokesperson for the foundation in an email.
This isn’t the first time SAIS and the foundation have worked together; they co-sponsored a conference on China’s economy in Hong Kong in March 2016, according to the school’s website. But a professorship and a major research project offer an opportunity for broader reach — the kind of global influence that Chinese President Xi Jinping has made a centerpiece of his policies. In October, at the meeting of the Communist Party that sets the national agenda for the next five years, Xi called for an expansion of the party’s overseas influence work, referring to the united front as a “magic weapon” of party power.
That quest to shape the global view of China isn’t the same thing as soft power, said James Leibold, a professor at La Trobe University in Melbourne who researches Chinese influence in Australia, where Beijing’s recent influence operations have sparked a national controversy.
China is an authoritarian state where the Communist Party rules with an iron fist, Leibold said — and that is what Beijing is trying to export.
“What we’re talking about here is not Chinese influence per se, but the influence of the Chinese Communist Party.”
In a joint project like the one at SAIS, that influence can be subtle rather than being heavy-handed, said Jamestown’s Mattis. “It’s the ability to privilege certain views over others, to create a platform for someone to speak,” he said. “When you have a role in selecting the platform and generating what I presume they hope are some of the bigger reports on U.S.-China relations in the next few years, that’s important.”
One goal of the joint research project is, in fact, to “yield a white paper to be submitted for endorsement by both the U.S. and Chinese governments,” a CUSEF spokesperson wrote in an emailed statement to FP.
While CUSEF representatives stress that it is not an agent of the Chinese Communist Party, the foundation has cooperated on projects with the the People’s Liberation Army and uses the same Washington public relations firm that the Chinese Embassy does.
One of those PLA projects is the Sanya Initiative, an exchange program that brings together U.S. and Chinese former high-ranking military leaders. On the Chinese side, the Sanya Initiative is led by a bureau of the PLA that engages in political warfare and influence operations, according to Mark Stokes, executive director of the Project 2049 Institute.
Sometimes the results of such high-level exchanges aren’t subtle. In February 2008, PLA participants in the Sanya Initiative asked their U.S. counterparts to persuade the Pentagon to delay publishing a forthcoming report about China’s military buildup, according to a segment excised from the 2011 annual report of the congressional U.S.-China Economic and Security Review Commission.
The U.S. members complied, though their request was not successful.
Exchanges and partnerships are not CUSEF’s only initiatives. As a registered foreign agent, in 2016 it spent just under $668,000 on lobbying, hiring the Podesta Group and other firms to lobby Congress on the topic of “China-U.S. relations.” The foundation has spent $510,000 on lobbying to date in 2017.
CUSEF also keeps on retainer the consulting and public relations firm BLJ Worldwide LTD, the same firm the Chinese Embassy in the United States uses. According to FARA filings, CUSEF currently pays the firm $29,700 a month to promote the foundation’s work and run a pro-Beijing website called China US Focus.
Whether through websites, partnerships, or endowments, China has learned to wrap its message in a palatable wrapper of U.S. academics and intellectuals, according to Mattis.
“Who better to influence Americans than other Americans?” he said.
Due to N Korea, Hawaii Goes to Nuclear Warning Systems
TOKYO/WASHINGTON (Reuters) – Japan has detected radio signals suggesting North Korea may be preparing for another ballistic missile launch, although such signals are not unusual and satellite images did not show fresh activity, a Japanese government source said on Tuesday.
After firing missiles at a pace of about two or three a month since April, North Korean missile launches paused in September, after Pyongyang fired a rocket that passed over Japan’s northern Hokkaido island.
“This is not enough to determine (if a launch is likely soon),” the source told Reuters.
Japan’s Kyodo news agency reported late on Monday that the Japanese government was on alert after catching such radio signals, suggesting a launch could come in a few days. The report also said the signals might be related to winter military training by the North Korean military.
South Korea’s Yonhap news agency, citing a South Korean government source, also reported that intelligence officials of the United States, South Korea and Japan had recently detected signs of a possible missile launch and have been on higher alert.
Hawaii reinstates Cold War-era nuclear attack warning signal amid North Korea tension
Hawaii is reinstating a statewide nuclear attack warning signal in December to prepare for a potential attack from North Korea.
The alarm, which has not been used since the Cold War, will be reinstated on Dec. 1 as part of a ballistic missile preparedness program, according to the Hawaii Emergency Management Agency (HI-EMA).
The agency instructed residents to immediately “Get inside, stay inside and stay tuned” if they hear the siren. Alerts will be sent to resident’s phones and broadcast on television and radio. “When [HI-EMA] started this campaign, there were concerns we would scare the public. What we are putting out is information based on the best science that we have on what would happen if that weapon hit Honolulu or the assumed targets,” said HI-EMA Administrator Vern Miyagi during an emergency preparedness presentation.
Since officials would have only 15 minutes or less of warning time before a North Korean missile’s impact, Hawaii residents are advised to have a designated place to go for shelter. “There will be no time to call our loved ones, pick up our kids and find a designated shelter. We should all prepare and exercise a plan ahead of time so we can take some comfort in knowing what our loved ones are doing,” said Miyagi in an interview with The Honolulu Star Advertiser.
Although the U.S. has conducted successful missile interception tests, there is no guarantee that the Navy would detect and intercept a target, the HI-EMA warns.
An HI-EMA fact sheet explains that, based on the estimated yield of North Korean missiles, there could be anywhere from 50,000 to 120,000 burn casualties and nearly 18,000 fatalities if an attack occurs.
After an attack, residents would have to stay sheltered in place until the HI-EMA has fully assessed the radiation and fallout, which could take a few hours or as long as 14 days, the agency says on its website.
State officials have been holding town halls to answer questions from residents.
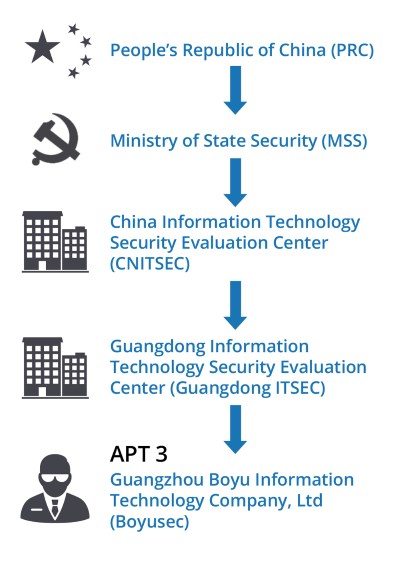
3 Chinese Nationals Charged with Hacking, Stealing Intellectual Property
Wonder if President Trump has called President Xi….The U.S. Treasury should at least sanction Guangzhou Bo Yu Information Technology Company Limited….
The Justice Department on Monday unsealed an indictment against three Chinese nationals in connection with cyberhacks and the alleged theft of intellectual property of three companies, according to US officials briefed on the investigation.
Acting U.S. Attorney for Western Pennsylvania Soo C. Song charged Wu Yingzhuo, Dong Hao and Xia Lei with conspiracy to commit computer fraud and abuse, conspiracy to steal trade secrets, wire fraud and identity theft.
The most serious charge, wire fraud, carries a sentence of up 20 years in federal prison. Each conspiracy charge has a possible sentence of up to 10 years and the identity theft carries a sentence of up to two years.
The indictment alleged that Wu, Dong and Xia worked with Guangzhou Bo Yu Information Technology Company Limited, a Chinese cybersecurity firm in Guangzhou, but used their skills to launch attacks on corporations in the U.S.
Between 2011 and May 2017, the trio stole files containing documents and data pertaining to a new technology under development by Trimble, along with employee usernames and passwords and 407 gigabytes of proprietary data concerning Siemens’ energy, technology and transportation efforts, according to the indictment. The trio gained access to the internal email server at Moody’s Analytics and forwarded all emails sent to an “influential economist” working for the firm, the indictment stated. Those emails contained proprietary and confidential economic analyses, findings and opinions. The economist was not named in the indictment.
A Siemens spokesperson said that the company “rigorously” monitors and protects its infrastructure and continually detects and hunts for breaches. The company did not comment on the alleged breach by the Chinese hackers and declined to comment on internal security measures.
Michael Adler, a spokesman for Moody’s Analytics, said that to the company’s knowledge no confidential consumer data or other personal employee information was exposed in the alleged hack.
“We take information security very seriously and continuously review and enhance our cybersecurity defenses to safeguard the integrity of our data and systems,” Adler wrote in an email to the Tribune-Review.
Trimble, in a statement sent to the Trib, wrote that no client data was breached. The company concluded that the attack had no meaningful impact on its business.
Song, however, said the loss to the companies targeted was considerable.
“The fruit of these cyber intrusions and exfiltration of data represent a staggering amount of dollars and hours lost to the companies,” Song said.
Wu, Dong and Xia used “spearphish” emails to gain access to computers, spread malware to infect networks and covered their tracks by exploiting other computers known as “hop points.”
Hop points allow users to hide their identities and locations by routing themselves through third-party computer networks.
“But there were missteps that led our investigators right to them,” said FBI Special Agent in Charge Bob Johnson of the Pittsburgh office.
Johnson would not elaborate on the missteps the accused hackers took, claiming doing so could jeopardize future investigations.
The U.S. Attorney’s Office led the investigation and was assisted by the FBI’s Pittsburgh Division, the Navy Criminal Investigative Service Cyber Operations Field Office and the Air Force Office of Special Investigations.
Counterfeit Operations, Iran and North Korea
It is a globally business and a nasty one.
U.S. officials have long accused Iran of supplying arms to rebel Houthi forces battling for control of Yemen. But Monday’s sanctions help highlight the scope of what Western officials commonly describe as the IRGC’s far-reaching and malign activities.
“Iran itself, together with its proxy, Lebanese Hezbollah, is knee-deep and has been knee-deep in the counterfeit business for quite some time,” said Matthew Levitt with the Washington Institute for Near East Policy. “Exposing this is kind of a two-for one, both exposing the organization’s terrorist activity and also exposing the nature of the criminal activity that it engages in.” More here.
Treasury Designates Large-Scale IRGC-QF Counterfeiting Ring
11/20/2017
Iranian Network Prints Counterfeit Yemeni Bank Notes for IRGC-Qods Force
WASHINGTON – Today, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) designated a network of individuals and entities involved in a large-scale scheme to help Iran’s Islamic Revolutionary Guard Corps-Qods Force (IRGC-QF) counterfeit currency to support its destabilizing activities. This network employed deceptive measures to circumvent European export control restrictions and procured advanced equipment and materials to print counterfeit Yemeni bank notes potentially worth hundreds of millions of dollars for the IRGC-QF. The IRGC-QF was designated pursuant to the global terrorism Executive Order (E.O.) 13224.
“This scheme exposes the deep levels of deception the IRGC-Qods Force is willing to employ against companies in Europe, governments in the Gulf, and the rest of the world to support its destabilizing activities. Counterfeiting strikes at the heart of the international financial system, and the fact that elements of the government of Iran are involved in this behavior is completely unacceptable,” said Treasury Secretary Steven Mnuchin. “This counterfeiting scheme exposes the serious risks faced by anyone doing business with Iran, as the IRGC continues to obscure its involvement in Iran’s economy and hide behind the façade of legitimate businesses to perpetrate its nefarious objectives.”
Reza Heidari and Pardazesh Tasvir Rayan Co.
Reza Heidari (Heidari) is being designated today for having acted for or on behalf of the IRGC-QF and having assisted in, sponsored, or provided financial, material, or technological support for, or financial or other services to or in support of, the IRGC-QF.
Pardavesh Tasvir Rayan Co. (Rayan Printing) is being designated today for being controlled by Heidari; for having acted for or on behalf of the IRGC-QF; having assisted, sponsored, or provided financial, material, or technological support for, or financial or other services to or in support of, the IRGC-QF; and being owned by Tejarat Almas Mobin Holding, another Iranian company also being designated today.
Heidari played a key role in procuring secure printing equipment and materials for the IRGC-QF in support of the group’s currency counterfeiting scheme. Heidari served as the managing director of Iran-based Rayan Printing, a company involved in printing counterfeit Yemeni rial bank notes potentially worth hundreds of millions of dollars for the IRGC-QF, as of late 2016. Heidari used front companies to obfuscate the actual end user and facilitate deceptive transactions when dealing with European suppliers of secure printing equipment and materials.
ForEnt Technik and Printing Trade Center
ForEnt Technik GmbH is being designated today for being owned or controlled by Heidari, while Printing Trade Center GmbH (PTC) is being designated for having acted for or on behalf of, and assisted in, sponsored, or provided financial, material, or technological support for, or financial or other services to or in support of, Heidari.
Heidari used German-based ForEnt Technik GmbH and PTC as front companies to deceive European suppliers, circumvent export restrictions, and acquire advanced printing machinery, security printing machinery, and raw materials in support of the IRGC-QF’s counterfeit currency capabilities. These raw materials included watermarked paper and specialty inks from European suppliers. Heidari is the Managing Director and sole shareholder of ForEnt Technik Gmbh.
Mahmoud Seif and Tejarat Almas Mobin
Mahmoud Seif is being designated today for having assisted, sponsored, or provided financial, material, or technological support for, or other services to or in support of, the IRGC-QF. Tejarat Almas Mobin Holding is being designated today for being controlled by Seif.
Seif is the managing director of Tejarat Almas Mobin, the parent company of Rayan Printing. Heidari and Seif coordinated on the procurement of raw supplies and equipment that enabled the IRGC-QF counterfeiting capabilities. Seif was involved with the logistics of importing materials for the counterfeiting project into Iran. Additionally, Seif has previously been involved in the procurement of weapons for the IRGC-QF.
For identifying information on the individuals and entities listed today, click here: https://www.treasury.gov/resource-center/sanctions/OFAC-Enforcement/Pages/20171120.aspx
*** So, did Iran teach North Korea to counterfeit or was it the other way around? North Korea has been counterfeiting and participating in illicit activities going back decades. North Korea is not especially fretful over the newly applied sanctions or being listed again as a terror state by President Trump. While it should be done, the regime has proven methods to finesse the system.
Ri Jong Ho had simply had enough. He’d seen too many executions.
Ri, a high-profile North Korean defector, spent years working for what is essentially a slush fund for one of the most notorious regimes on the planet, Kim Jong Un and his compatriots.Life was good. Ri helped bring in somewhere between $50 million and $100 million for North Korean elites, and was handsomely rewarded with luxuries most North Koreans couldn’t dream of in years past: a car, a color TV and some extra cash on the side, once rarities in the communist state but more commonplace now in the capital, Pyongyang.But he watched the regime kill his peers and their families, even children.“It was not just high level officers, officials, but their families, their children (and) their followers,” Ri told CNN in his first interview to a major US broadcast network. “It was not just once or twice a year — it was ongoing throughout the year, thousands of people being executed or purged.”Ri said the final straw came in late 2013, when Kim Jong Un executed his own uncle, Jang Song Thaek, with an anti-aircraft gun.“It was a cruel and crude method of execution,” he said. “After all these years living in the socialist system, I never witnessed anything like that.”Ri was living in China at the time, and in 2014 was able to safely defect with his family.And just like that, Kim lost one of his top money makers.Office 39
Ri said he worked for decades in what’s known as “Office 39.”The office is in charge of bringing in hard currency for the regime. Ri calls it a “slush fund for the leader and the leadership.”Ri told CNN “Office 39” is not engaged in illicit activities, but the US Treasury Department says otherwise.The US government accused the office of engaging in “illicit economic activities” to support the North Korean government. It has branches throughout the nation that raise and manage funds and is responsible for earning foreign currency for North Korea’s Korean Workers’ Party senior leadership through illicit activities such as narcotics trafficking.North Korea has been accused of crimes like hacking banks, counterfeiting currency, dealing drugs and even trafficking endangered species.Workers who help bring in cash for the regime are granted access to the outside world — especially China — in order to establish networks that are crucial to making money, analysts say. They often have diplomatic privileges that allow them to evade their host country’s domestic laws, experts say.Ri said he was not involved in illegal activities and that they were not under the purview of Office 39, but did not deny they occurred. He said much of North Korea’s hard cash is earned through exporting labor — the country sends workers across the globe and collects much of their pay, according to the UN — and exporting natural resources like coal, which China used to buy but has since stopped.Illicit activities make a lot of money, though. The Congressional Research Service estimated in 2008 that North Korea could earn anywhere from $500 million to $1 billion from these types of illicit activities.That money helps fund the lavish lifestyles of the North Korean elites while sanctions limit the country’s ability to make money. That keeps North Korea’s leadership happy and helps Kim prevent coup attempts, analysts say.“They (North Korean leaders) are focused on maintaining their ruling power, and they are working on making this dynasty-like system lasting for a long time,” Ri said. “So instead of focusing on their economic development or better life, they are more focused on maintaining their system.Some of Office 39’s profits also go to the country’s nuclear and missile programs, which crossed an important threshold this month with the testing of two intercontinental ballistic missiles, weapons that experts say likely put the United States homeland in North Korea’s range.CNN reached out to the North Korean mission at the United Nations for a response to the interview with Ri. An official at the mission said Ri was lying to “make money and save his own life.”‘Hundreds of fishing boats’
Analysts say Office 39 is likely now in the cross hairs of US President Donald Trump’s administration.The Trump team has made it clear that one of the ways it plans to deal with North Korea is to squeeze its revenue streams across the globe in order to pressure them into negotiations over their weapons programs.Ri is not sure if the tactic will work, as he says it’s easy to side-step sanctions and believes the international community has made strategic mistakes that could come back to bite them.North Korean companies can just change their names once sanctioned, he says. North Korean leaders don’t keep much money abroad, so the sanctions against them are pointless, according to Ri. Smugglers are difficult to catch.“Smuggling is conducted by any and every means you could imagine. Mostly larger items are done using ships, for example by filing a cargo list … where what’s written on the (list) is different from what is really being shipped,” he said. “On the open sea, the Yellow Sea, there are hundreds of fishing boats — both from China and North Korea — and all the smuggling is done by these so-called fishing boats.Going after China
Ri believes that secondary sanctions — targeting those who do business with North Korea, like the United States did to China’s Bank of Dandong in June — is the way to go, especially in China.Beijing accounts for about 85% of North Korean imports in 2015, according to UN data, though Ri revealed that Pyongyang does import some oil from Russia.North Korean economist Ri Gi Song told CNN in February that China accounts for 70% of trade and that trade with Russia is increasing. More here from CNN.