US sending nuclear-capable B-52 bombers to ISIS fight
FNC: The United States is sending nuclear-capable B-52 aircraft to drop bombs on the Islamic State terror group, defense officials confirmed to Fox News Friday.
The B-52 Stratofortress will start its first bombing campaign against ISIS in April, the Air Force Times reports. It’s not clear how many B-52s or airmen will be involved.
Officials say the aircraft will replace nuclear-capable B-1 Lancers hitting ISIS targets in Iraq and Syria.
The Lancers returned to home bases in the U.S. in January. They flew only 3% of all strike missions against ISIS, but had dropped 40% of the bombs and other munitions. B-1s could loiter over the battlefield for 10 hours, much longer than jet fighters, and also could fly supersonic, reaching targets across Iraq and Syria within minutes.
“The B-1s are rotated out, so they’re not here right now, they’ve gone back to do some upgrades,” Lieutenant General Charles Q. Brown Jr., commander at U.S. Air Forces Central Command, told reporters. More here.
The U.S. just sent a carrier strike group to confront China
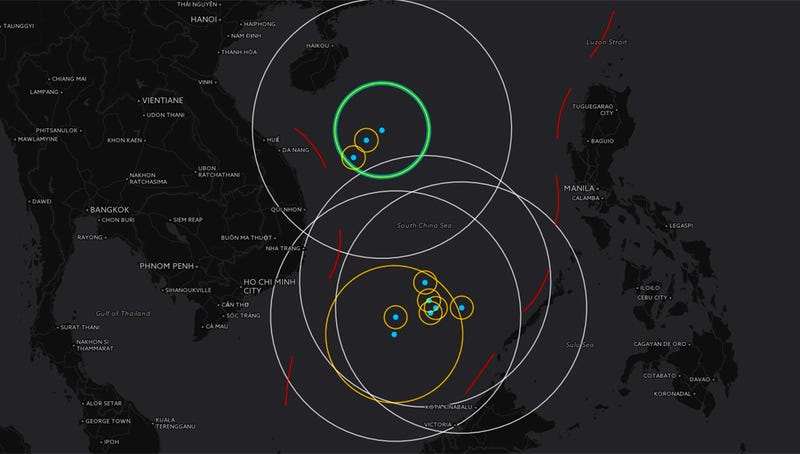
The U.S. Navy has dispatched a small armada to the South China Sea.
NavyTimes: The carrier John C. Stennis, two destroyers, two cruisers and the 7th Fleet flagship have sailed into the disputed waters in recent days, according to military officials. The carrier strike group is the latest show of force in the tense region, with the U.S. asserting that China is militarizing the region to guard its excessive territorial claims.
Stennis is joined in the region by the cruisers Antietam and Mobile Bay, and the destroyers Chung-Hoon and Stockdale. The command ship Blue Ridge, the floating headquarters of the Japan-based 7th Fleet, is also in the area, en route to a port visit in the Philippines. Stennis deployed from Washington state on Jan. 15.
The Japan-based Antietam, officials said, was conducting a “routine patrol” separate from the Stennis, following up patrols conducted by the destroyer McCambell and the dock landing ship Ashland in late February.
The stand-off has been heating up on both sides. After news in February that the Chinese deployed an advanced surface-to-air missile battery to the Paracel Islands, U.S. Pacific Command head Adm. Harry Harris told lawmakers that China was militarizing the South China Sea.
“In my opinion China is clearly militarizing the South China Sea,” Harris testified on Feb. 24. “You’d have to believe in a flat Earth to believe otherwise.”
Overnight, Chinese officials dismissed claims that China was militarizing the region, pointing to the Stennis’s patrol as evidence that the U.S. was to blame for the increased military tensions.
“The accusation [that China is militarizing the region] can lead to a miscalculation of the situation,” said Fu Ying, a spokeswoman for China’s National People’s Congress. “If you take a look at the matter closely, it’s the US sending the most advanced aircraft and military vessels to the South China Sea.”
A Pacific Fleet spokesman downplayed the heavy U.S. presence in the region.
“Our ships and aircraft operate routinely throughout the Western Pacific — including the South China Sea — and have for decades,” Cmdr. Clay Doss said in a statement. “In 2015 alone, Pacific Fleet ships sailed about 700 combined days in the South China Sea.”
However, experts say sending Stennis and its air wing to the South China Sea is a clear signal to China and the region.
“Clearly the Navy and DoD is demonstrating its full commitment to presence and freedom of navigation in the region,” said Jerry Hendrix, a retired Navy captain and analyst with the Center for a New American Security in Washington, D.C. “With the full carrier strike group and the command ship, the Navy is showing the scope of its interests and ability to project presence and power around world.”
The destroyer Lassen’s vaunted October patrol within the 12-mile limit of China’s man-made South China Sea islands was the first challenge of China’s sovereignty over the Spratly Islands since Chinese land-reclamation projects began there.
On Jan. 30, the destroyer Curtis Wilbur patrolled near Triton Island, part of the Paracel Islands chain China also claims. More here.