And he ran in 2019-20 for President….
Axios: A suspected Chinese intelligence operative developed extensive ties with local and national politicians, including a U.S. congressman, in what U.S. officials believe was a political intelligence operation run by China’s main civilian spy agency between 2011 and 2015, Axios found in a yearlong investigation.
Why it matters: The alleged operation offers a rare window into how Beijing has tried to gain access to and influence U.S. political circles.
- While this suspected operative’s activities appear to have ended during the Obama administration, concerns about Beijing’s influence operations have spanned President Trump’s time in office and will continue to be a core focus for U.S. counterintelligence during the Biden administration.
 Clockwise from top left: Fang with then-Dublin City Councilmember Eric Swalwell at an October 2012 student event; undated photo of Fang, now former Fremont Mayor Bill Harrison and Rep. Judy Chu; Fang with then-Rep. Mike Honda and then-San Jose city Councilmember Ash Kalra at a March 2014 event at the Chinese Embassy in D.C. Sources: Renren, Facebook, Facebook
Clockwise from top left: Fang with then-Dublin City Councilmember Eric Swalwell at an October 2012 student event; undated photo of Fang, now former Fremont Mayor Bill Harrison and Rep. Judy Chu; Fang with then-Rep. Mike Honda and then-San Jose city Councilmember Ash Kalra at a March 2014 event at the Chinese Embassy in D.C. Sources: Renren, Facebook, Facebook
The woman at the center of the operation, a Chinese national named Fang Fang or Christine Fang, targeted up-and-coming local politicians in the Bay Area and across the country who had the potential to make it big on the national stage.
- Through campaign fundraising, extensive networking, personal charisma, and romantic or sexual relationships with at least two Midwestern mayors, Fang was able to gain proximity to political power, according to current and former U.S. intelligence officials and one former elected official.
- Even though U.S. officials do not believe Fang received or passed on classified information, the case “was a big deal, because there were some really, really sensitive people that were caught up” in the intelligence network, a current senior U.S. intelligence official said.
- Private but unclassified information about government officials — such as their habits, preferences, schedules, social networks, and even rumors about them — is a form of political intelligence. Collecting such information is a key part of what foreign intelligence agencies do.
Among the most significant targets of Fang’s efforts was Rep. Eric Swalwell (D-Calif.).
- Fang took part in fundraising activity for Swalwell’s 2014 re-election campaign, according to a Bay Area political operative and a current U.S. intelligence official. Swalwell’s office was directly aware of these activities on its behalf, the political operative said. That same political operative, who witnessed Fang fundraising on Swalwell’s behalf, found no evidence of illegal contributions.
- Federal Election Commission records don’t indicate Fang herself made donations, which are prohibited from foreign nationals.
- Fang helped place at least one intern in Swalwell’s office, according to those same two people, and interacted with Swalwell at multiple events over the course of several years.
A statement from Swalwell’s office provided to Axios said: “Rep. Swalwell, long ago, provided information about this person — whom he met more than eight years ago, and whom he hasn’t seen in nearly six years — to the FBI. To protect information that might be classified, he will not participate in your story.”
What happened: Amid a widening counterintelligence probe, federal investigators became so alarmed by Fang’s behavior and activities that around 2015 they alerted Swalwell to their concerns — giving him what is known as a defensive briefing.
- Swalwell immediately cut off all ties to Fang, according to a current U.S. intelligence official, and he has not been accused of any wrongdoing.
- Fang left the country unexpectedly in mid-2015 amid the investigation. She did not respond to multiple attempts by Axios to reach her by email and Facebook.
Between the lines: The case demonstrates China’s strategy of cultivating relationships that may take years or even decades to bear fruit. The Chinese Communist Party knows that today’s mayors and city council members are tomorrow’s governors and members of Congress.
- In the years since the Fang probe, the FBI has prioritized investigations into Chinese influence operations, creating a unit in May 2019 within the bureau solely dedicated to countering Beijing’s activities at the state and local levels. U.S. national security officials believe the threat posed by China has only grown with time.
- “She was just one of lots of agents,” said a current senior U.S. intelligence official.
- Beijing “is engaged in a highly sophisticated malign foreign influence campaign,” FBI director Chris Wray said in a July 2020 speech. These efforts involve “subversive, undeclared, criminal, or coercive attempts to sway our government’s policies, distort our country’s public discourse, and undermine confidence in our democratic processes and values,” Wray said.
The FBI declined to comment. The Chinese Embassy in Washington did not respond to a request for comment.
Details: Axios spoke with four current and former U.S. intelligence officials about the case over a period of more than a year. They requested anonymity because they were not authorized to speak to the media about the case.
- Axios also spoke with 22 current and former elected officials, political operatives, and former students who knew Fang personally when she was based in the United States.
The cover: How Fang worked
Fang’s friends and acquaintances said she was in her late 20s or early 30s when she was based in the U.S. and was enrolled as a student at a Bay Area university.
She used political gatherings, civic society conferences, campaign rallies, and campus events to connect with elected officials and other prominent figures, according to U.S. intelligence officials, Bay Area political operatives, former students, and current and former elected officials who knew her.
- U.S. intelligence officials believed she was overseeing likely unwitting subagents whom she helped place in local political and congressional offices.
- Fang attended regional conferences for U.S. mayors, which allowed her to grow her network of politicians across the country.
- She also engaged in sexual or romantic relationships with at least two mayors of Midwestern cities over a period of about three years, according to one U.S. intelligence official and one former elected official.
- At least two separate sexual interactions with elected officials, including one of these Midwestern mayors, were caught on FBI electronic surveillance of Fang, according to two intelligence officials. Axios was unable to identify or speak to the elected officials.
Between 2011 and 2015, Fang’s activities brought her into contact with many of the Bay Area’s most prominent politicos.
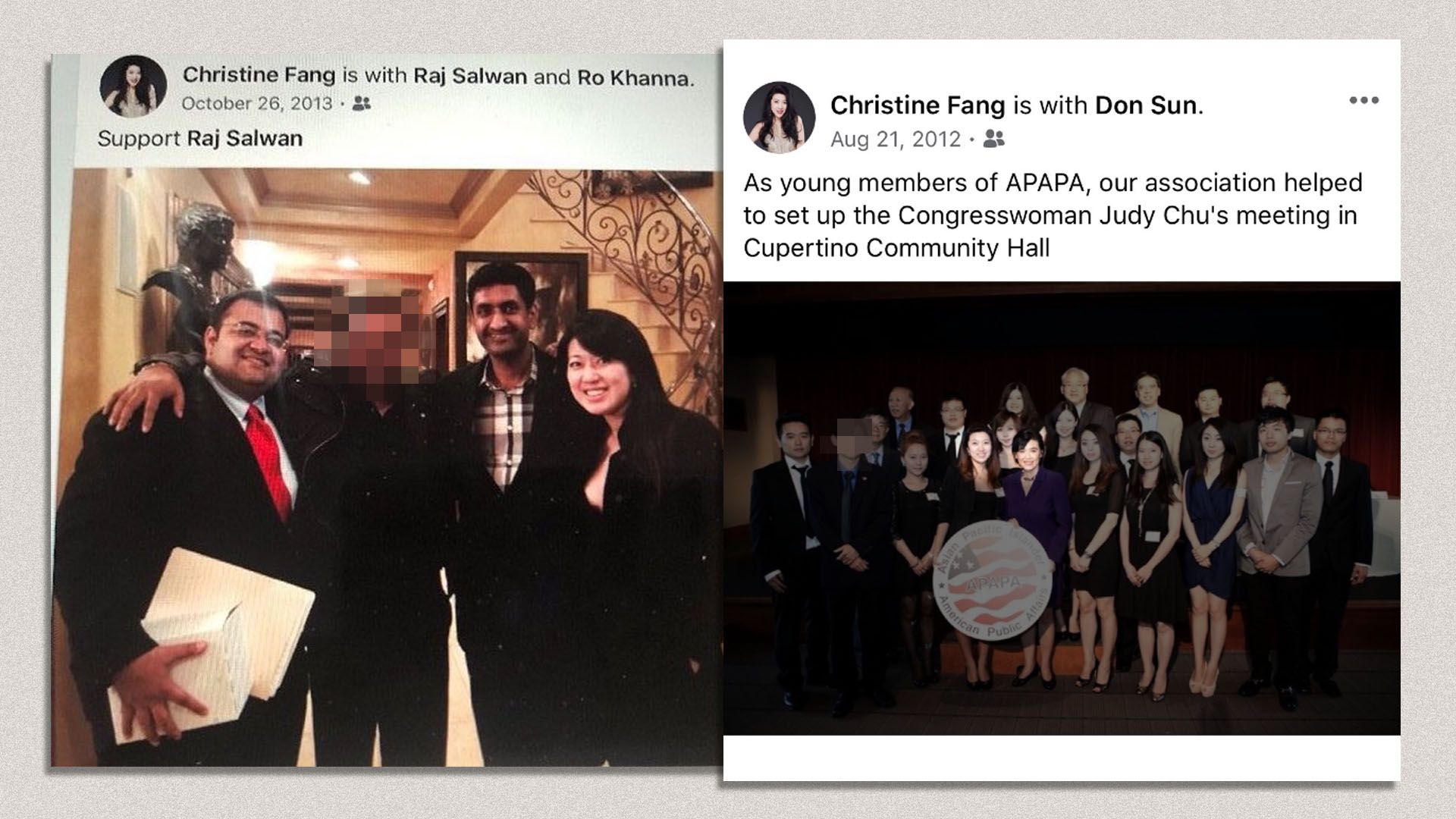
- She volunteered for Ro Khanna’s unsuccessful 2014 House bid, according to a former campus organizer and social media posts. (Khanna, a Democrat, was elected to the House in 2016.) Khanna’s office said he remembers seeing Fang at several Indian American political gatherings but did not have further contact with her. Khanna’s office said the FBI did not brief him on her activities. Khanna’s 2014 campaign staff said that Fang’s name does not appear in their staff records, though they said that their records do not include all volunteers.
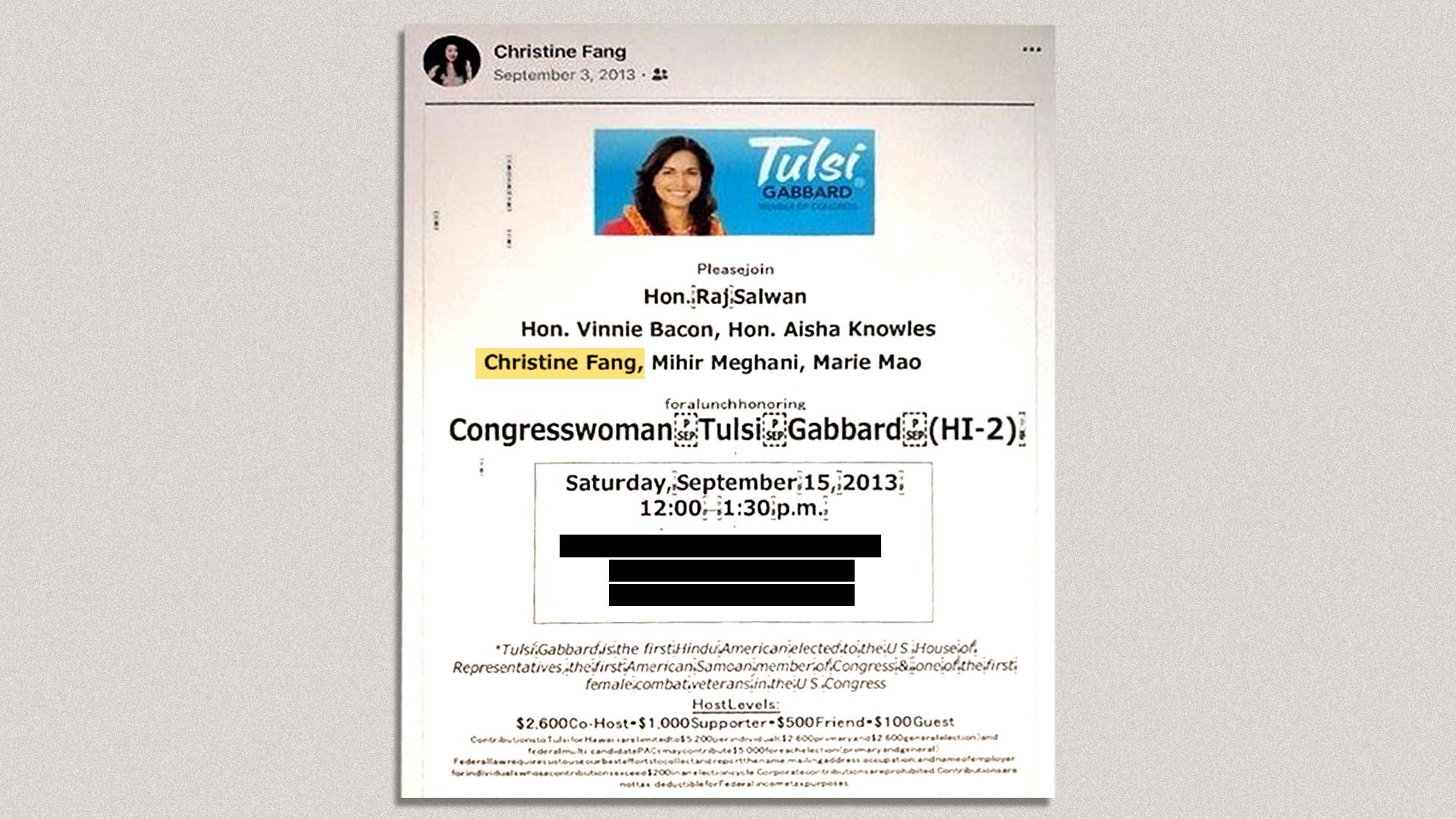
- Fang helped with a fundraiser for Rep. Tulsi Gabbard (D-Hawaii) in 2013, according to a flyer from the event Fang shared on Facebook. She appeared in photos over multiple years with a host of California politicians, including Khanna, Swalwell, Rep. Judy Chu (D-Calif.) and then-Rep. Mike Honda (D-Calif.).
- Gabbard “has no recollection of ever meeting or talking with her, nor any recollection of her playing a major role at the fundraiser,” a spokesperson said in an email to Axios.
- Fremont City Councilmember Raj Salwan, whose name appears on the flyer, told Axios he was unaware of Fang’s role in the event and her name was added to the flyer by other Asian American leaders.
- Chu’s office said they have no records of Christine Fang. Honda said he had no memory of meeting Fang.
The bottom line: U.S. officials believe Fang’s real reason for being in the U.S was to gather political intelligence and to influence rising U.S. officials on China-related issues.
- Close relationships between a U.S. elected official and a covert Chinese intelligence operative can provide the Chinese government with opportunities to sway the opinion of key decision-makers.
- Beijing may aim to influence foreign policy issues directly related to China, or issues closer to home, such as partnering with Chinese companies for local investment — an issue particularly salient among local-level officials such as mayors and city council members.
Sounding the alarm: The U.S. response

U.S. counterintelligence officials said they believe Fang acted at the direction of China’s Ministry of State Security (MSS), the country’s main civilian spy agency.
- U.S. officials first noticed Fang through surveillance they were conducting on a different person — a suspected MSS officer working undercover as a diplomat in the San Francisco consulate, a current U.S. counterintelligence official said.
- The suspected officer used the consulate as a base to do outreach to state and local-level U.S. politicians, including inviting them on trips to China, the official said.
- The official added that both Fang and the suspected officer were focused on gathering political intelligence and conducting influence operations in the Bay Area. (Axios corroborated through U.S. State Department records that a Chinese diplomat with the same name as the suspected MSS officer was stationed in San Francisco during the period Fang was there.)
- Fang and the suspected officer met or spoke on numerous occasions, leading U.S. officials to look into Fang’s own background and activities, the official said.
- However, Fang’s main intelligence handlers were believed to be based in China, according to two U.S. officials.
Fang was put under FBI surveillance, four current and former U.S. officials said. The FBI’s San Francisco Division led a counterintelligence investigation into Fang’s activities, according to one current and one former U.S. intelligence official.
- “The fact that she was traveling around the country” getting close to U.S. politicians “was a big red flag,” said one of the officials. “She was on a mission.”
What happened next: Senior U.S. intelligence officials provided multiple defensive briefings around 2015 to warn targeted local and national politicians about Fang’s connections to Chinese intelligence and potential Chinese assets in their offices, one of these officials said.
- U.S. intelligence officials also provided multiple briefings to White House officials and members of Congress on the case, a current senior official said.
- Bill Harrison, the mayor of Fremont, California, at that time, said he knew Fang because she volunteered in his office and participated in numerous local political and community events. Harrison told Axios that in August 2015 he was contacted by FBI officials who warned him about Fang’s suspected activities in the Bay Area.
- Bureau officials said Fang’s activities were part of a “long game play” targeting local politicians, Harrison recalled. The FBI told him the Chinese government’s strategy is “to strike up a relationship with you and see if you move up the line,” Harrison said.
How it ended: Fang left the U.S. suddenly

U.S. officials said China’s intelligence operation broke up in mid-2015 when Fang left the U.S. amid the FBI-led probe.
- Fang had planned to travel to Washington, D.C., to attend a June 2015 event.
- But shortly beforehand, she said she could no longer attend because she unexpectedly needed to return to China, according to an acquaintance from California on the same trip, who spoke with Axios.
Many of Fang’s political contacts in the Bay Area were surprised and confused about her sudden departure from the country.
- “When she left kind of abruptly, we all kind of scratched our heads,” recalled Harrison, the former Fremont mayor. (The FBI reached out to Harrison after Fang’s departure.)
- “She disappeared off the face of everything,” remembered Gilbert Wong, the former mayor of Cupertino, California, who had seen Fang frequently at political events.
- But in the months surrounding her departure, rumors swirled in Bay Area political circles that the FBI was investigating her, according to four local organizers, political operatives, and elected officials who knew her.
Fang has not returned to the U.S., said intelligence officials and her former political acquaintances. She appears to have largely cut off contact with her U.S.-based friends and the networks she spent years building in California.
The Justice Department has filed no public charges against Fang.
Why Beijing targets California’s Bay Area

The Bay Area offers ideal conditions for a foreign intelligence operative aiming to identify and target ambitious local politicians with national aspirations.
The big picture: Some of America’s most powerful politicians got their start in Bay Area politics, and China recognizes California’s importance. The MSS has a unit dedicated solely to political intelligence and influence operations in California.
- Silicon Valley is also the world’s most important center for the technology industry, making it a hotbed for Chinese economic espionage. Russian intelligence has also long targeted the Bay Area.
- California’s economy is the largest of all the U.S. states, giving California state lawmakers significant influence over national trends.
Democrats dominate the Bay Area, from mayors to its numerous U.S. congressional districts, and anyone seeking proximity to power needs to be in their political circles.
Context: The FBI’s extensive surveillance of left-wing political groups in the 1960s and 1970s has created a lingering distrust of the bureau that still exists today in Bay Area politics.
The Bay Area has one of the largest and oldest Chinese American communities in the country. Keeping tabs on Chinese diaspora communities is a top priority of China’s intelligence services, U.S. officials said.
- China’s spy services want to influence these communities to become more predisposed to the regime, as well as surveil and stamp out potential organized opposition to the Communist Party.
- Access to local political offices can give Beijing’s intelligence operatives opportunities to collect information on communities of Chinese descent in the United States.
- A high-profile example of this occurred in the 2000s, when China’s Ministry of State Security allegedly recruited a San Francisco-based staffer in Sen. Dianne Feinstein’s office. This person, who was fired when the FBI alerted Feinstein to his activities, was responsible for liaising with the local Chinese community.
What’s at stake: Chinese Americans find themselves in a difficult position in 2020, being squeezed both by influence campaigns from the Chinese government and a rise in anti-Chinese racism in the United States.
- “We want to fight against racism, we want to call it out,” Wong, the former mayor of Cupertino, told Axios. “But if there’s a spy, we definitely support full prosecution and we don’t support China penetrating the Chinese community.”
- “How do we address this issue without infringing on Chinese American rights?” he added.
- Khanna said in a statement: “I respect the need for law enforcement to protect our nation from espionage. [But] we need strict guardrails to make sure the FBI’s investigations do not have collateral damage to the privacy of American citizens or to the legitimacy of Asian Americans in this country.” He underscored his concern about “the chilling effect” of overbroad surveillance on Chinese American political participation.
How Fang rose to prominence among Bay Area politicos
In 2011, Fang enrolled as a student at California State University East Bay, where she served as the president of the school’s Chinese Student Association and president of the campus chapter of Asian Pacific Islander American Public Affairs (APAPA), a national organization that encourages Asian Americans to get involved in civic affairs.
- She used those positions as her initial platform to gain access to political circles. She frequently invited political figures, business executives, and Chinese consular officials to attend the flurry of high-profile events she organized over a period of several years, according to current and former local officials, former students, Bay Area politicos, and social media activity.
- Fang’s first known contact with numerous politicians, including Swalwell, Harrison, Chu, and then-candidate Khanna was through her role as president of these organizations.
- Fang received a campus pride award for the work she did on behalf of the Chinese Student Association during the 2012–2013 academic year.
During this time, Fang maintained unusually close ties to the Chinese consulate in San Francisco.
- It’s common for Chinese student association presidents to communicate frequently with Chinese consular officials.
- But Fang’s relationship to the San Francisco consulate was especially close, according to social media posts, event flyers, photographs, and one current U.S. intelligence official.

As Fang branched out into off-campus politics, she relied heavily on her APAPA affiliation. Many of Fang’s activities were “under the auspices of APAPA,” said one Bay Area political operative, an observation echoed by five other Bay Area political figures and activists.
- Henry Yin, who is president of the APAPA Bay Area region chapter, told Axios in a phone call that he had seen Fang at numerous events and remembered her as being “very active.”
- APAPA is “not involved with foreign countries,” said Yin, adding that the organization tries “to make connections with concerned citizens for the betterment of Asian and Pacific Islanders, and also benefit all citizens at large.”
Fang soon became a mainstay at Bay Area political events, fundraising for candidates and bringing along donors.
- “She was everywhere,” said Raj Salwan, a current Fremont City councilmember, expressing a sentiment echoed by several other current and former local officials who spoke to Axios. “She was an active student. I was surprised at how active she was and how she knew so many politicos.”
Fang’s Facebook friends list is a virtual who’s who of local Bay Area politicos, and includes city council members, current and former mayors, Khanna, and Swalwell’s father and brother.
- She positioned herself “to be the connector between the Asian American community and members of Congress,” recalled a Bay Area political operative who knew her.
- One photo, taken at a March 2014 event at the Chinese Embassy in D.C., shows Fang together with Honda and Ash Kalra — at the time a San Jose city councilmember, later elected to the California State Assembly in 2016. A representative of Kalra’s office said he does not remember meeting Fang.
- Fang attended events in support of former San Francisco Mayor Ed Lee, according to an acquaintance present at the gatherings. (Lee, who began serving as mayor in 2011, passed away in 2017 while in office.)
What they’re saying: Several acquaintances in political circles told Axios that Fang was “charismatic” and “well liked” — though others described her behavior as “secretive” and even “suspicious.”
- “Christine was a political player and she was someone who was good to know,” said a former campus political organizer who knew her.
- But others found her less substantive. “She never really, to me, was interested on the policy side,” recalled the Bay Area political operative.
Few seemed to know Fang on a personal level. Several acquaintances told Axios she seemed to come from wealth — she drove a white Mercedes, according to one official — but said she never spoke about her family or her hometown.
Fang’s connection to Swalwell

Fang’s ties to Rep. Eric Swalwell, which began when he was a councilmember for Dublin City, California, demonstrate China’s long game.
- Swalwell rose to prominence rapidly, and in late 2012 became one of the youngest members of the U.S. House.
- In January 2015, Swalwell was assigned a seat on the House Permanent Select Committee on Intelligence, serving as the lead Democrat on the subcommittee on CIA oversight.
Details: Fang’s earliest known engagement with Swalwell occurred through the Chinese Student Association. By 2014, she had risen in local political circles and developed close ties to Swalwell’s office.
- Fang “was a bundler” for Swalwell and other candidates, according to a Bay Area political operative with direct knowledge of her efforts. A current U.S. intelligence official confirmed her activity for Swalwell; a local elected official also said she brought in donors for other candidates. Bundlers persuade others to write checks for campaigns; they can bring in substantial sums of money as well as deepen the campaign’s engagement with target communities, making bundlers a valuable and thus potentially influential ally to a candidate.
- The Bay Area political operative who witnessed Fang fundraising on Swalwell’s behalf was concerned whether donors she brought in were legally permitted to donate. They found no evidence of illegal contributions.
- Fang facilitated the potential assignment of interns into Swalwell’s offices, the political operative said. In at least one case, an intern recommended by Fang was placed into Swalwell’s D.C. office, this person said. A current U.S. intelligence official confirmed the intern placement.
For Fang, targeting Swalwell made sense. His 2012 campaign — which was something of a longshot bid, pitting a young and relatively inexperienced city official against a longtime incumbent from the same party — relied heavily on Asian American support, said a former congressional staffer from the East Bay.
- That made Swalwell’s ties to the Chinese American community, and particularly APAPA, the Asian American civic organization, especially important.
Fang sought out mayors around the U.S.

Fang attended conferences for mayors around the U.S., according to three U.S. intelligence officials, as well as numerous current and former politicians who knew her.
Why it matters: By attending conferences for local officials, Fang went to extraordinary lengths to meet and befriend U.S. politicians, ostensibly as part of her activities as a Chinese agent, U.S. officials believe.
Details: Fang engaged in sexual or romantic relationships with at least two mayors of Midwestern cities, said one U.S. intelligence official and one former elected official.
- At a 2014 conference in Washington, an older Midwestern mayor “from an obscure city” referred to Fang as his “girlfriend” and insisted the relationship was genuine despite the clear age difference between Fang and himself, according to former Cupertino Mayor Gilbert Wong, who was directly present for the conversation.
- Fang also had a sexual encounter with an Ohio mayor in a car that was under electronic FBI surveillance, said one current U.S. official. When the mayor asked why Fang was interested in him, Fang told him she wanted to improve her English, the same official said.
What they’re saying: Wong told Axios he knew Fang from her political activities in California, where she would attend fundraisers and Chinese cultural events.
- But Wong said he was “shocked” to see her appear at an event for U.S. municipal officials hosted by the Chinese Embassy in D.C. in March 2014. Wong told Axios he had gone to D.C. twice that year to attend mayor-focused events, and that he saw Fang at both of those events.
- At the Chinese Embassy event, Fang introduced Wong to the mayor of Shenzhen, a city that, like Cupertino, is home to a major tech industry. She translated so that the two mayors could have a conversation.
The bottom line

U.S. intelligence officials believe China’s spy services have become more aggressive and emboldened, including in their U.S.-focused influence and political intelligence-gathering operations. Fang’s case shows how a single determined individual, allegedly working for Beijing, can gain access to sensitive U.S. political circles.




