Primer: For all you pro Russian and pro Putin types out there:
What you Need to Know About the Gerasimov Doctrine’
and
Russian Hybrid Warfare: How to Confront a New Challenge to the West
***
Military: The U.S. Army‘s chief of staff on Tuesday issued a stern warning to potential threats such as Russia and vowed the service will defeat any foe in ground combat.
“The strategic resolve of our nation, the United States, is being challenged and our alliances tested in ways that we haven’t faced in many, many decades,” Army Chief of Staff Gen. Mark Milley told an audience at the Association of the United States Army’s annual meeting in Washington, D.C.
“I want to be clear to those who wish to do us harm … the United States military — despite all of our challenges, despite our [operational] tempo, despite everything we have been doing — we will stop you and we will beat you harder than you have ever been beaten before. Make no mistake about that.”
Milley’s comments come during an election year in which voters will decide a new president and commander in chief — and a period of increased military activity of near-peer competitors, including Russia and China.
The Army has struggled to rebuild its readiness after more than a decade of extended combat operations in Iraq and Afghanistan. The service has significantly cut the size of its force since the Cold War and decreased its modernization budget in the last decade, Milley said.
“While we focused on the counter-terrorist fight, other countries — Russia, Iran, China, North Korea — went to school on us,” he said. “They studied our doctrine, our tactics, our equipment, our organization, our training, our leadership. And, in turn, they revised their own doctrines, and they are rapidly modernizing their military today to avoid our strengths in hopes of defeating us at some point in the future.”
Milley also quoted a senior Russian official as saying publicly, “The established world order is undergoing a foundational shake-up” and that “Russia can now fight a conventional war in Europe and win.”
The general warned that future warfare with a near-peer adversary will “be highly lethal, unlike anything our Army has experienced at least since World War II.”
“Our formations will likely have to be small; we will have to move constantly,” he said. “On the future battlefield, if you stay in one place for longer than two or three hours, you will be dead.”
Despite the challenges, Milley said the Army will adapt to survive such a dangerous battlefield.
“It’s a tall order for sure — to project power into contested theaters, fight in highly populated urban areas, to survive and win on intensely lethal and distributed battlefields and to create leaders and soldiers who can prevail. Tough? Yes. But impossible? Absolutely not,” Milley said.
“Make no mistake about it, we can now and we will … retain the capability to rapidly deploy,” he said, “and we will destroy any enemy anywhere, any time.”
**** So what is percolating globally and against the United States that has the Pentagon concerned?
Using the same provocations that Iran has used against the United States, Russia is doing the same thing.
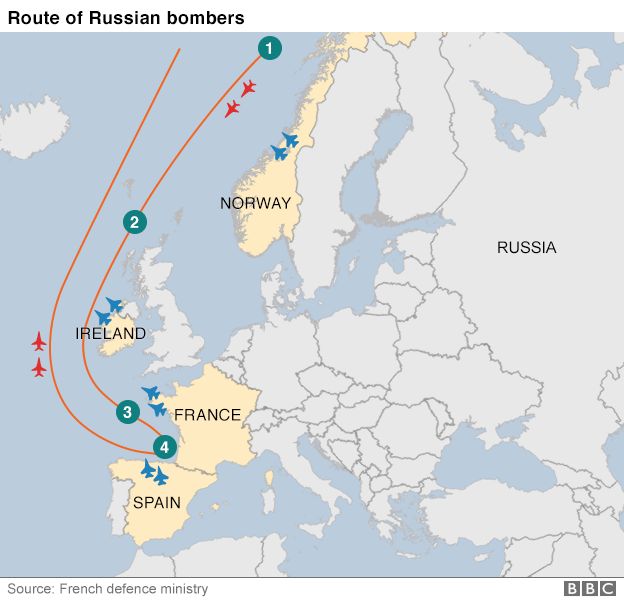
Nato jets scrambled as Russian bombers fly south
Two Russian Blackjack bombers were intercepted by fighter jets from four European countries as they flew from the direction of Norway to northern Spain and back, it has emerged. Norway, the UK, France and Spain all scrambled jets as the TU-160 planes skirted the airspace of each country. It comes at a time of heightened tension between the West and Russia. Correspondents say the frequency of Russian bombers being intercepted by Nato planes has increased markedly. Spanish media say it is the furthest south such an operation has had to take place. More here from the BBC.
Given the failed truce or cease fire agreement regarding Syria, it was announced by John Kerry and approved by the White House and National Security Council to walk away fully from Russia and seek other avenues with regard to the deadly civil war in Syria. As noted, last week before the Senate, it was admitted there was no Plan B.
In recent months, Russia has been quite aggressive and militant towards Americans in Moscow and other cities in Russia. Some diplomats have been beaten up, robbed and their homes broken into. The most recent incident involved some Americans being drugged.
“We are outraged,” Russian Deputy Foreign Minister Sergey Ryabkov said in a statement posted on the Russian Foreign Ministry website, adding the claim may have been the work of the US State Department seeking “revenge” for the collapse of talks between the two counties to address the situation in Syria.Russia’s denial came after a report two days ago by Radio Free Europe/Radio Liberty that the diplomats — a man and a woman who were not senior officials — allegedly had their drinks spiked with a date-rape drug while attending a United Nations convention on corruption last November. The report, attributed to anonymous sources, said the State Department quietly protested the incident to Russian officials.The story also said one of the diplomats had been treated at a “Western medical clinic” – which Russia said was not true. More here from CNN.
Russia had agreed to a cease-fire last month, but that fell apart quickly. Russia argues that the United States has failed in its commitment to separate the moderate rebel groups it supports from more radical factions such as the Syrian branch of Al Qaeda.
Kirby said the United States will withdraw a team that had been dispatched to open a so-called joint implementation center, in which Russian and American armed forces were going to join efforts to fight Islamic State and other jihadi groups.
Also Monday, Russian President Vladimir Putin signed a decree suspending his country’s participation in a treaty with the U.S. designed to eliminate nuclear weapons.
Putin cited “a threat to strategic stability as a result of USA’s unfriendly acts toward Russia.” This was a reference to a deepening diplomatic spat between the Kremlin and the White House over Syria, as well as tensions and sanctions that followed Russia’s 2014 takeover of Crimea and its support to separatists in eastern Ukraine.
It is the latest action by Russia that serves to unwind the nuclear-cooperation and weapons treaties that have governed the relationship between the U.S. and Russia in the years after the Soviet dissolution.
The U.S. said it would continue to participate in multilateral talks over Syria, aimed at achieving a cessation of hostilities and the delivery of aid, and would communicate with Russia regarding airstrikes to avoid collisions.
Last week, when it first threatened to suspend Syria talks with Russia, Washington said it would consider other options, including additional financial sanctions or even military operations. More here from the LATimes.
Then it appears the National Security Council and the State Department pinged the United Nations for some action….well kinda sorta.
The United States virtually blocked the United Nations Security Council’s statement that condemned the mortaring of Russia’s embassy in Damascus, Russia’s Permanent Mission to the global organization said.
“It was actually blocked by the U.S. delegation, which tried to bring outside elements into a standard text. Brits and Ukrainians clumsily helped Americans,” the mission said.
It said that the behavior of the three countries “testifies to their blatant disrespect for the Vienna Convention on Diplomatic Relations”, which demands to protect diplomatic and consular facilities and personnel.
The Russian mission said that “when such crimes were committed earlier, including against the diplomatic missions of Western countries, Russia has always unconditionally supported their condemnation by the Security Council.”
“We have to state that the moral principles of some of our colleagues in the Security Council have seriously teetered,” it said. More here from TASS.
Russia is taking all precautions forecasting future aggressions in Syria as they installed the S-300 anti-aircraft missile defense system at the Russia base of Tartus which is near Latakia, Syria on the Mediterranean Sea.
Further there is the matter of the Baltics and Ukraine. Control and management of the Mediterranean and the Black Sea is at risk.
NATO members must increase the alliance’s military capabilities, position additional forces in the Baltics and Eastern Europe, establish a maritime force in the Black Sea and bolster its presence in the Arctic, all to counter Russia’s growing military strength and increasingly belligerent behavior toward its neighbors, the Atlantic Council said in a new report.
The report, “Restoring the Power and Purpose of the NATO Alliance,” also urges America’s leaders to strengthen U.S. leadership of NATO, work to restore public support for the trans-Atlantic alliance and “counter those who threaten to withdraw U.S. support for NATO.” And it calls on alliance members to maintain their commitment to securing Afghanistan and to increase military assistance and intelligence-sharing with “its Arab partners” in response to the spreading terrorist threat.
The policy paper was crafted by a team led by former veteran diplomatic Nicholas Burns, who was the U.S. ambassador to NATO, and retired Gen. James Jones, a former Marine Corps commandant and Supreme Allied Commander in Europe. The report was prepared ahead of next month’s NATO summit in Warsaw. More here.
What about the Arctic?
Russia: Militarizing the Arctic
While the Arctic region remains peaceful, Russia’s recent steps to militarize the Arctic, coupled with its bellicose behavior toward its neighbors, makes the Arctic a security concern. Russia’s Maritime Doctrine of Russian Federation 2020, adopted in July 2015, lists the Arctic as one of two focal points, the other being the Atlantic.[1]
Russia’s Northern Fleet, which is based in the Arctic, now counts for two-thirds of the Russian Navy. A new Arctic command was established in 2015 to coordinate all Russian military activities in the Arctic region.[2] Underwater, Russian submarines are operating at a rate not seen since the end of the Cold War. Indeed, Admiral Viktor Chirkov, commander-in-chief of the Russian navy, stated in 2015 that the navy had ramped up submarine patrols by 50 percent from just 2013.[3]
Over the next few years, two new so-called Arctic brigades will be permanently based in the Arctic region, and Russian special forces have been training in the region. Soviet-era facilities have been re-opened; Russia is expected to have nine operative airfields in the Arctic by 2018.[4] Russia has reportedly also placed radar and S-300 missiles on the Arctic bases at Franz Joseph Land, New Siberian Islands, Novaya Zemlya, and Severnaya Zemlya.[5] Russia’s ultimate goal is to deploy a combined arms force in the Arctic by 2020, and this plan appears to be on track.[6] In early June, the Russian Navy showed off its first new icebreaker in 45 years.[7]
As an Arctic power, Russia’s military presence in the region is to be expected. However, it should be viewed with some caution in light of recent Russian aggression in its neighborhood. The former Supreme Allied Commander of Europe, General Philip Breedlove, described Russian activity in the Arctic as “increasingly troubling,” stating: “Their increase in stationing military forces, building and reopening bases, and creating an Arctic military district—all to counter an imagined threat to their internationally undisputed territories—stands in stark contrast to the conduct of the seven other Arctic nations.”[8]. More here from Heritage.
****
ABC: The Russians are already there in force. Last year, they staged a military exercise in the Arctic as seen in this Russian Ministry of Defense footage.
It involved about 40,000 troops, 15 submarines, 41 warships and multiple aircraft. No one disputes their right to do that on their own territory. It’s just that it wasn’t announced.
Philip Breedlove: We pre-announce ours. No one is surprised by them whereas the exercise that Russia did was a snap exercise which is a bit destabilizing.
Until May of this year, retired four-star General Philip Breedlove was the supreme Allied commander of NATO with responsibility for the Arctic.
What else is destabilizing, he says, is Russia’s military build up along something called the Northern Sea Route skirting the Russian Arctic coastline. The route could become an alternative to the Suez Canal, saving huge amounts of time and money for the commercial shipping industry.
Philip Breedlove: I have heard as much as 28 days decrease in some of the transit from the northern European markets to the Asian markets. That is an incredible economic opportunity. And it could be a very boon— big boon to business around the world.
Lesley Stahl: What would it mean if the Russians did gain control over the Northern Sea route?
Philip Breedlove: If the Russians had the ability to militarily hold that at ransom, that is a big lever over the world economy.
Related reading: Russia’s Military Sophistication in the Arctic Sends Echoes of the Cold War