Natalia Veselnitskaya had clients to defend in New York. Those clients were Denis Katsyv, Alexander Litvak, and Timofey Krit. Natalia had expensive choices in accommodations in New York where the U.S taxpayer paid the bill.
Prevezon Holdings was part of a money laundering prosecution case in Southern District of New York that for the most part was settled in May of 2017. Prevezon is/was owned by Denis Katsyv and has a principal by the name of Timofey Krit. The Prevezon office was located in Brooklyn, New York. The registered agent for Prevezon is Gabriella Volshteyn.
Gabriella Volshteyn is a founder and a managing attorney of Volshteyn & Associates. The lawfirm boasts the following on the website:
In our Real Estate practice, we have participated in over $1 billion of transactions in commercial and residential real estate involving both the US-based and international corporate entities and individuals.
In our Business and Contract Law practice, we have represented a full range of clients from individuals and small business owners to large multinational holding companies. We have drafted contracts ranging from simple corporate agreements to complex contractual agreements related to large-scale international events, such as Sochi Olympic Games.
In our Global Corporate and Tax practice, we have considerable expertise in structuring complex corporate, banking and investment accounts for foreign investors and the establishment of offshore trusts in tax-favored jurisdictions, such as the British Virgin Islands, the Cayman Islands, the Bahamas, the Netherlands, Antilles, the Channel Islands, Panama, Switzerland, Liechtenstein and Madeira.
Our Surrogacy Law practice is an area of passion for this firm as we have been fortunate to help many families from all over the world with bringing a child in their lives. With the help of our firm, surrogacy has made the dream of having children possible for those who are infertile, unable to become pregnant, or unable to carry a child to term.
(of note, the countries listed above are those that are known to be quite common in use by front companies to hide money, evade taxes and park laundered funds)
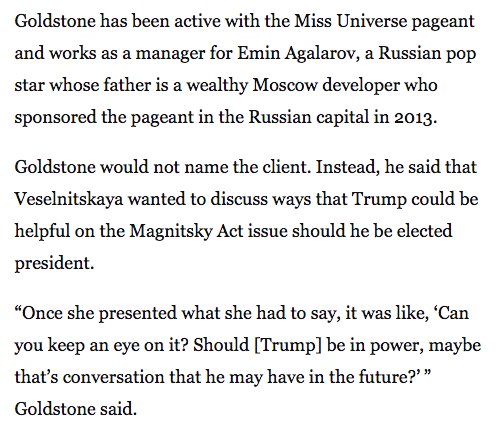
*** While Donald Trump Jr. had a meeting on June 6, 2016 with Natalia Veselnitskaya, the meeting allegedly had several objectives including opposition intelligence on Hillary Clinton, getting waivers or removal of sanctions from the Magnitsky Act and later Russian adoption. Donald Jr. included Jared Kuschner and Paul Manafort in the meeting without vetting Natalia or on background the sanctions. Natalia also does have ties to former top members of GRU and FSB. As a normal practice, the Kremlin always dispatches operatives that are at least one layer removed from listed official positions of the Russian government.
A particular group of note for which Veselnitskaya was involved and is a large lobby operation in Washington DC is HRAGI, a front operation on human rights known as Human Rights Accountability Global Initiative Foundation. Those involved in the lobby operation on behalf of HRAGI and Prevezon include:
A. Rinat Akhmetshin – Russian national living in Washington D.C.
B. Robert Arakelian
C. Chris Cooper – CEO Potomac Square Group
D. Glenn Simpson – SNS Global and Fusion GPS
E. Mark Cymrot – Partner, Baker Hostetler
F. Ron Dellums – Former Republican Congressman (correction, Dellums is Democrat of operative status)
G. Howard Schweitzer – Managing Partner of Cozen O’Connor Public
StrategiesIn more detail as published by Senator Grassley’s office:
The Russian Government also has a vested interested in ensuring that Prevezon
Holdings Limited and its affiliated companies successfully defend asset forfeiture
proceedings brought against them by the United States Government in New
York, in which Prevezon is accused of laundering proceeds of the $230 million
fraud.
Prevezon is owned by Denis Katsyv, the son of a Russian government official,
Piotr Katsyv. Denis Katsyv currently has $7million frozen by the Swiss General
Prosecutor, pursuant to a criminal investigation by the Swiss authorities into the
laundering of proceeds from the $230 million fraud. More here.***
Another issue is Jared Kushner.
HRAGI’s other clients include Vladimir Lelyukh, a top executive at Sberbank Capital, a subsidiary of the state-owned Russian bank involved in the real estate, energy, transportation, and automotive sectors. Sberbank Capital’s CEO, Ashot Khachaturyants, is a former senior official in Russia’s Federal Security Service (FSB) and its Ministry of Economic Development and Trade.
State-owned Russian financial institutions are common conduits for surreptitious intelligence work in the country. Jared Kushner, the president’s son-in-law and senior adviser, has faced scrutiny over a January meeting a top executive at another bank with ties to Russian intelligence, Moscow-based Vnesheconombank. For context and validation, go here.Vnesheconombank was sanctioned by the U.S. Treasury in 2014 due to Russian annexation of Crimea and Ukraine.
Vnesheconombank also known as VEB bank has the following officers:









 ABC
ABC
 Facebook check-ins can be damming.
Facebook check-ins can be damming.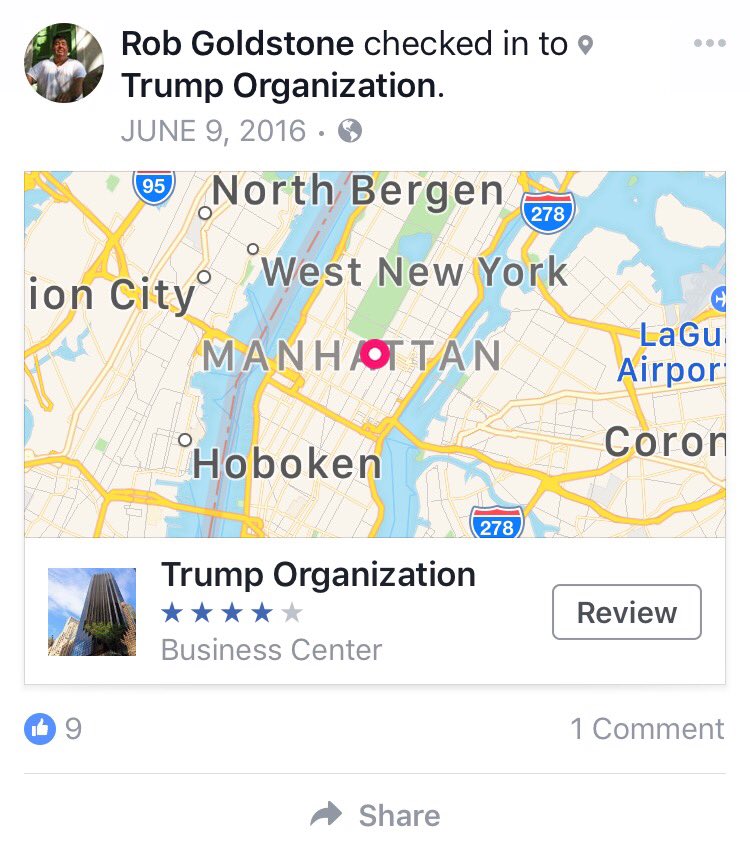 Rob Goldstone, the man
Rob Goldstone, the man