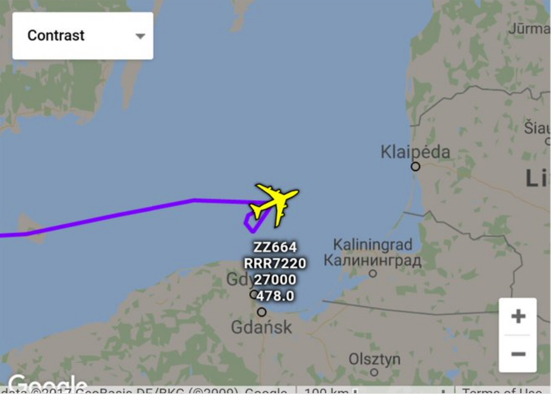
The Chinese leadership headed by President Xi Jinping made the request, through its ambassador in the United States, to dismiss Adm. Harry Harris, known as a hard-liner on China, including with respect to the South China Sea issue, the source said.
 Adm. Harry Harris, head of the U.S. Pacific Command, addresses the Lowy Institute think tank in Sydney last December. | AFP-JIJI
Adm. Harry Harris, head of the U.S. Pacific Command, addresses the Lowy Institute think tank in Sydney last December. | AFP-JIJI
China’s envoy to the United States, Cui Tiankai, conveyed the request to the U.S. side, to coincide with the first face-to-face, two-day meeting between President Donald Trump and Xi in Florida from April 6, but the Trump administration likely rejected it, the source said.
China is a longtime economic and diplomatic benefactor of North Korea.
As the head of Pacific Command, Harris, who was born in Japan and raised in the United States, plays a vital role in the security of the region.
He was responsible in ordering last month the dispatch of the USS Carl Vinson aircraft carrier to waters near off the Korean Peninsula in a show of force amid signs the North was preparing to test-fire another ballistic missile or conduct a sixth nuclear test.
The Trump administration has called for exerting “maximum pressure” on North Korea to prod it to give up its nuclear and missile programs. The administration has said all options — including a military strikes — remain on the table.
Harris has pushed for the U.S. deployment of the advanced Terminal High Altitude Area Defense (THAAD) anti-missile system to South Korea. China has opposed the deployment, saying it could undermine its security interests and the strategic balance of the region.
He has also called for continuing U.S. “freedom of navigation” operations in the contested South China Sea. Overlapping territorial claims, as well as land construction and militarization of outposts in disputed areas in the sea, remain a source of tension in the region.
According to the source, Cui also asked the Trump administration not to label China as a currency manipulator. As per the request, the United States did not label China as such, in light of Beijing’s role in helping Washington deal with the North Korean issue.
*** Related reading: 2013 Study Finds North Korea Has Indigenous Capabilities to Produce Nuclear Weapons

An example of the open-source evidence used for Kemp’s study: A 2011 image from a television broadcast in North Korea showing Kim-Jong Il inspecting a flow-forming machine located in an underground tunnel. This type of machine is able to produce centrifuge rotors for North Korea’s uranium-enrichment program.
***
Is the United States partners in the Asia Pacific region ready to deal with 5000 tunnels and an underground operation?
 The entrance of an ‘intrusion tunnel’ under the DMZ between South and North Korea, Telegraph
The entrance of an ‘intrusion tunnel’ under the DMZ between South and North Korea, Telegraph
North Korea’s Secret Strategy in a War with America: Go Underground
North Korea, one of the most secretive countries in the world, is no stranger to building underground military facilities. Whether a tunnel dug under the demilitarized zone designed to pass thousands of troops an hour, or bunkers to accommodate the regime’s leadership, North Korea has built extensive underground facilities designed to give it an edge in wartime.
One of the earliest examples of North Korean underground engineering was the discovery of several tunnels leading from North Korea under the demilitarized zone to South Korea. The first tunnel was located in 1974, extending one kilometer south of the DMZ. The tunnel was large enough to move up to two thousand troops per hour under the DMZ. A U.S. Navy officer and South Korean Marine corporal were killed by a booby trap while investigating the tunnel. Thanks to a tip from a North Korean defector, an even larger tunnel was discovered in 1978, a mile long and nearly seven feet wide.
Since then at least four tunnels have been discovered, with reinforced concrete slabs, electricity for lighting and fresh air generation, and narrow railway gauges to shuttle dirt and rock back to the tunnel entrance. Collectively, the four tunnels would have likely been able to move a brigade’s worth of troops an hour under South Korea’s defenses.
It’s difficult to determine how many tunnels exist. One report says that Kim Il-sung, the founder of the North Korean state and Kim Jong-un’s grandfather, ordered each of the ten frontline combat divisions to dig two tunnels. If completed, that would theoretically mean another dozen or so tunnels remain undiscovered. A former South Korean general, Han Sung-chu, claims there are at least eighty-four tunnels—some reaching as far as downtown Seoul. The South Korean government does not believe Han’s numbers—nor the claimed ability to reach Seoul—are credible. A forty-mile tunnel would reportedly generate a seven-hundred-thousand-ton debris pile, which has not been picked up by satellite. Despite the warnings, the last major tunnel was discovered in 1990 and South Korea seems to believe that the tunneling danger has passed.
If it has passed, it may be because North Korea has decided to tunnel in different ways. The North Korean People’s Liberation Army Air Force is believed to have three different underground air bases at Wonsan, Jangjin and Onchun. The underground base at Wonsan reportedly includes a runway 5,900 feet long and ninety feet wide that passes through a mountain. According to a defector, during wartime NK PLAAF aircraft, including MiG-29 fighters and Su-25 Frogfoot ground-attack aircraft, would take off from conventional air bases but return to underground air bases. This is plausible, as one would expect North Korean air bases to be quickly destroyed during wartime.
Another underground development is a series of troop bunkers near the DMZ. A North Korean defector disclosed that, starting in 2004, North Korea began building bunkers capable of concealing between 1,500 and two thousand fully armed combat troops near the border. At least eight hundred bunkers were built, not including decoys, meant to conceal units such as light-infantry brigades and keep them rested until the start of an invasion.
Other underground facilities are believed to have been constructed to shelter the North’s leadership. According to a South Korean military journal, the United States believes there are between six thousand and eight thousand such shelters scattered across the country. This information was reportedly gathered from defectors in order to hunt down regime members in the event of war or government collapse.
North Korea is believed to have hundreds of artillery-concealing caves just north of the DMZ. Known as Hardened Artillery Sites, or HARTS, these are usually tunneled into the sides of mountains. An artillery piece, such as a 170-millimeter Koksan gun or 240-millimeter multiple-launch rocket system, can fire from the mouth of the cave and then withdraw into the safety of the mountain to reload. These sites are used to provide artillery support for an invasion of South Korea or direct fire against Seoul itself. As of 1986, and estimated two hundred to five hundred HARTS were thought to exist.
According to a report by the Nautilus Institute, North Korea is also thought to have “radar sites in elevator shafts that can be raised up like a submarine periscope; submarine and missile patrol boat bases in tunnels hewn in rock; tunnels a kilometer or more in length for storing vehicles and supplies, or to hide the population of a nearby city.”
How would the United States and South Korea deal with these underground facilities in wartime? First, it would have to locate the facilities. These facilities are hard to spot via satellite, and gleaning information from defectors is perhaps the best way to learn about them in peacetime. Once war commences, signal intelligence will pick up radio transmissions from previously unknown underground locations, enemy troops will from concealed positions or tunnel entrances, and artillery counter-battery radars will fix the positions of HARTS. It is likely that, despite advance preparations, many of these positions will be a surprise to Washington and Seoul.
Once located, there are three ways of dealing with the sites. The first and safest way to deal with them is to bomb them from above. This presents the least risk to allied forces, but it will also prove difficult to determine whether air or artillery strikes have had good effect. The use of bombs or artillery shells may cause cave-ins that prevent allied forces from entering an underground complex and exploiting any intelligence found inside.
Another option is to simply station troops outside tunnels and shoot anyone who ventures outside. While also a safer option, an underground complex will always have multiple exits—the tunnels Kim Il-sung ordered his divisions to dig were to each have four or five exit points. The most thorough way to deal with the tunnels would be to enter them. This would be by far the most effective way to deal with regime holdouts, but also the most dangerous.
Pyongyang’s eventual defeat in any wartime scenario is a given, but its underground headquarters, fortifications and troop depots have the potential to not only enhance the Korean People’s Army’s ability to mount a surprise attack, but also to prolong the war, confounding the high-tech armed forces of its adversaries. Such underground shelters, wherever they are, will likely be the site of the endgame phase of the war, as the regime is driven underground by rapidly advancing allied forces. Only then will we discover the true extent of North Korea’s extensive underground empire.

 The RegisterUK
The RegisterUK


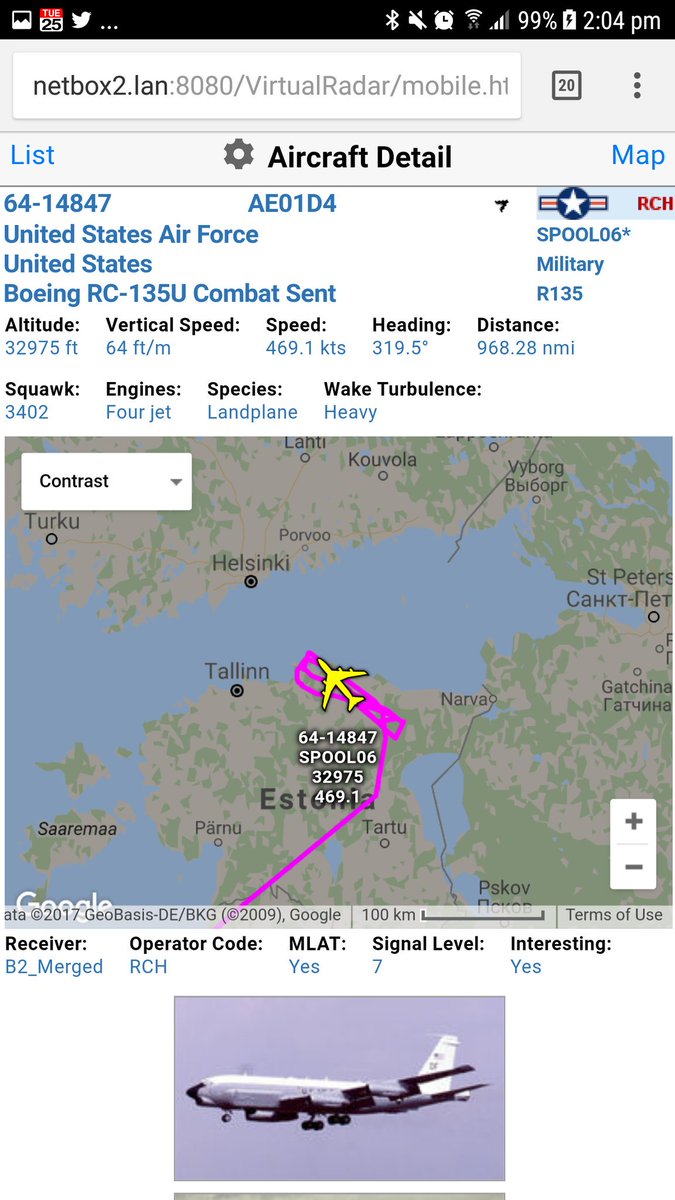 Shortly thereafter, even a
Shortly thereafter, even a