Gotta look deep for information and there are two theories, one is Russia as the other is the medical industry. Humm….it goes something like this…. By the way, the dates could easily lineup.
Related reading: US sends specialist ‘nuke sniffer’ plane to the UK as ‘radiation spike’ sparks fears Putin has tested nuclear weapon in the Arctic
Primer:
The Washington Free Beacon quotes Pentagon officials saying the unmanned underwater vehicle, code named Kanyon by the Pentagon, was test-launched from the Sarov-class submarine on November 27th.
What Pentagon names Kanyon is what in Russia is known as the «Ocean Multipurpose System Status-6» – a top secret weapon system the world has never seen anything like before. A year ago, Russian state-TV Channel One showed a glimpse of a graphic slide of the Status-6, later on said to be an unauthorized leak of a secret weapon development plan.
The drawings on the slide could very well be a purpose leak aimed at telling the world what weapon-systems are under development. The TV news covered the meeting in Sochi where President Putin was told by high-ranking officers in the Strategic forces how Russia’s nuclear deterrence strategy is developing. Moscow are looking for ways to overcome the United States’ Anti-Ballistic Missile Defence system, and one answer is to go deep with the nukes. Highly suggested reading more here.

Mysterious Radiation Spike Across Europe
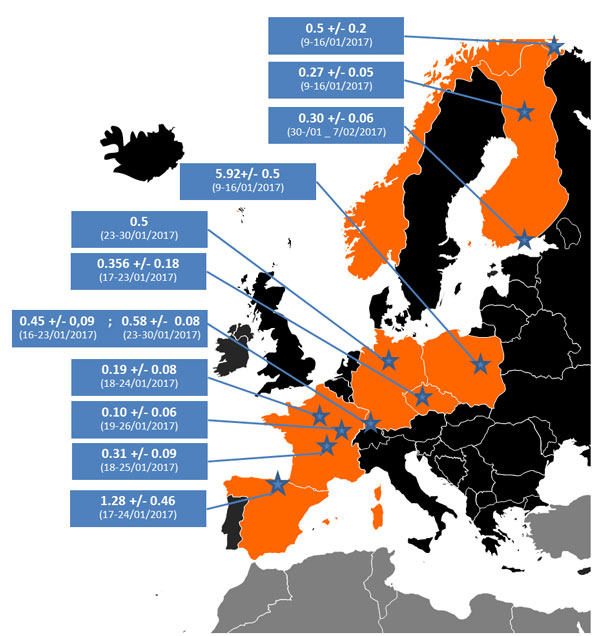
Nuclear scientists are struggling to determine the source of small amounts of nuclear radiation that bloomed over Europe throughout January.
France’s IRSN institute, the public body for radiological and nuclear risks, announced in a statement on February 13 that Iodine-131, a radionuclide of human origin, was detected in trace amounts at ground-level atmosphere in continental Europe. First detected in the second week of January over northern Norway, Iodine-131 presence was then detected over Finland, Poland, Germany, Czech Republic, France, and Spain. However, the levels have since returned to normal and scientists have yet to determine the source of the radiation.
Norway’s Radiation protection Authority (NRPA), which first detected the Iodine-131 over its northern Russian border, told Motherboard over the phone today that the levels present essentially no risk to human health. “I can assure you that the levels are low,” said a press a spokesperson.
But with a half-life of just eight days, the detection of Iodine-131 is proof of a recent release, said IRSN in its statement to the media.
Rumors are circulating, of course, that Russia has secretly tested a low-yield nuclear weapon in the Arctic, possibly in the Novaya Zemlya region—historically used for Russia’s nuclear tests. Iodine-131, discovered by two University of California researchers in 1938, is a radioisotope synonymous with the atomic bomb tests carried out by the US and Russia throughout the 1950s, and has recently presented threats from leaking during the Chernobyl nuclear power plant disaster and the 2011 Fukushima nuclear accident.
But Iodine-131 is also found in the medical industry, commonly used for treating thyroid-related illnesses and cancers. Astrid Liland, head of the section for emergency preparedness at the NRPA, told Motherboard in an email today, “Since only Iodine-131 was measured, and no other radioactive substances, we think it originates from a pharmaceutical company producing radioactive drugs.
Iodine-131 is used for treatment of cancer.”Britain’s Society for Radiological Protection (SRP) also told Motherboard that the exclusive presence of Iodine-131 suggests the source is not a nuclear incident, but rather a medical facility such as a hospital or a supplier of radio-pharmaceuticals. “The release was probably of recent origin. Further than this it is impossible to speculate,” the SRP’s Brian Gornall told Motherboard in an email.
Still, where exactly that pharma company could be located is unknown. “Due to rapidly changing winds, it is not possible to track exactly where it came from. It points to a release source somewhere in Eastern Europe,” Liland told Motherboard.
The Iodine cloud prompted the United States Air Force to send over a specialized particle-sniffing aircraft to investigate. As per reports on The Aviationist, a US Air Force WC-135 deployed to Royal Air Force base Mildenhall in the UK on February 17, equipped to test the atmosphere over Europe for radiation. The aircraft’s last intercontinental expedition was to analyse the atmosphere over the Korean Peninsula following an alleged North Korean nuclear test.
The deployment spurred on rumors of a nuclear test from Russia, but a spokesperson for the the Comprehensive Nuclear-Test-Ban Treaty Organization (CTBTO), an international body that monitors nuclear weapon tests, told Motherboard in an email today, “Although some readings of I-131 above minimal detection level have been observed since beginning of year in Europe nothing extraordinary has been measured.”
The IRSN said in its statement that the data has now been shared between the members of the informal European network called Ring of Five, a group of organizations that research radiation levels in the atmosphere.

 p
p


 p
p