The Guardian more than a year ago, validates the summary posted below.
Tablet: The accusation that the Obama administration used information gleaned from classified foreign surveillance to smear and blackmail its political opponents at home has gained new traction in recent days, after reports that former National Security Adviser Susan Rice may have been rifling through classified transcripts for over a year that could have included information about Donald Trump and his associates. While using resources that are supposed to keep Americans safe from terrorism for other purposes may be a dereliction of duty, it is no more of a crime than spending all day on Twitter instead of doing your job. The crime here would be if she leaked the names of U.S. citizens to reporters. In the end, the seriousness of the accusation against Rice and other former administration officials who will be caught up in the “unmasking” scandal will rise or fall based on whether or not Donald Trump was actively engaged in a conspiracy to turn over the keys of the White House to the Kremlin. For true believers in the Trump-Kremlin conspiracy theories, the Obama “spying and lying” scandal isn’t a scandal at all; just public officials taking prudent steps to guard against an imminent threat to the republic.
But what if Donald Trump wasn’t the first or only target of an Obama White House campaign of spying and illegal leaks directed at domestic political opponents?
In a December 29, 2015 article, The Wall Street Journal described how the Obama administration had conducted surveillance by US Gov on Israeli officials to understand how Prime Minister Benjamin Netanyahu and other Israeli officials, like Ambassador Ron Dermer, intended to fight the Iran Deal. The Journal reported that the targeting “also swept up the contents of some of their private conversations with U.S. lawmakers and American-Jewish groups.”
Despite this reporting, it seemed inconceivable at the time that—given myriad legal, ethical, political, and historical concerns, as well as strict National Security Agency protocols that protect the identity of American names caught in intercepts—the Obama White House would have actually spied on American citizens. In a December 31, 2016, Tablet article on the controversy, “Why the White House Wanted Congress to Think It Was Being Spied on By the NSA,” I argued that the Obama administration had merely used the appearance of spying on American lawmakers to corner opponents of the Iran Deal. Spying on U.S. citizens would be a clear abuse of the foreign-intelligence surveillance system. It would be a felony offense to leak the names of U.S. citizens to the press.
Increasingly, I believe that my conclusion in that piece was wrong. I believe the spying was real and that it was done not in an effort to keep the country safe from threats—but in order to help the White House fight their domestic political opponents.
“At some point, the administration weaponized the NSA’s legitimate monitoring of communications of foreign officials to stay one step ahead of domestic political opponents,” says a pro-Israel political operative who was deeply involved in the day-to-day fight over the Iran Deal. “The NSA’s collections of foreigners became a means of gathering real-time intelligence on Americans engaged in perfectly legitimate political activism—activism, due to the nature of the issue, that naturally involved conversations with foreigners. We began to notice the White House was responding immediately, sometimes within 24 hours, to specific conversations we were having. At first, we thought it was a coincidence being amplified by our own paranoia. After a while, it simply became our working assumption that we were being spied on.”
This is what systematic abuse of foreign-intelligence collection for domestic political purposes looks like: Intelligence collected on Americans, lawmakers, and figures in the pro-Israel community was fed back to the Obama White House as part of its political operations. The administration got the drop on its opponents by using classified information, which it then used to draw up its own game plan to block and freeze those on the other side. And—with the help of certain journalists whose stories (and thus careers) depend on high-level access—terrorize them.
Once you understand how this may have worked, it becomes easier to comprehend why and how we keep being fed daily treats of Trump’s nefarious Russia ties. The issue this time isn’t Israel, but Russia, yet the basic contours may very well be the same.
***
Two inquiries now underway on Capitol Hill, conducted by the Senate intelligence committee and the House intelligence committee, may discover the extent to which Obama administration officials unmasked the identities of Trump team members caught in foreign-intelligence intercepts. What we know so far is that Obama administration officials unmasked the identity of one Trump team member, Michael Flynn, and leaked his name to the Washington Post’s David Ignatius.
“According to a senior U.S. government official,” Ignatius wrote in his Jan. 12 column, “Flynn phoned Russian Ambassador Sergey Kislyak several times on Dec. 29, the day the Obama administration announced the expulsion of 35 Russian officials as well as other measures in retaliation for the hacking. What did Flynn say, and did it undercut the U.S. sanctions?”
Nothing, the Times and the Post later reported. But exposing Flynn’s name in the intercept for political purposes was an abuse of the national-security apparatus, and leaking it to the press is a crime.
This is familiar territory. In spying on the representatives of the American people and members of the pro-Israel community, the Obama administration learned how far it could go in manipulating the foreign-intelligence surveillance apparatus for its own domestic political advantage. In both instances, the ostensible targets—Israel and Russia—were simply instruments used to go after the real targets at home.
In order to spy on U.S. congressmen before the Iran Deal vote, the Obama administration exploited a loophole, which is described in the original Journal article. The U.S. intelligence community is supposed to keep tabs on foreign officials, even those representing allies. Hence, everyone in Washington knows that Israeli Ambassador Ron Dermer is under surveillance. But it’s different for his American interlocutors, especially U.S. lawmakers, whose identities are, according to NSA protocol, supposed to be, at the very least, redacted. But the standard for collecting and disseminating “intercepted communications involving U.S. lawmakers” is much less strict if it is swept up through “foreign-foreign” intercepts, for instance between a foreign ambassador and his capital. Washington, i.e. the seat of the American government, is where foreign ambassadors are supposed to meet with American officials. The Obama administration turned an ancient diplomatic convention inside out—foreign ambassadors were so dangerous that meeting them signaled betrayal of your own country.
During the long and contentious lead-up to the Iran Deal the Israeli ambassador was regularly briefing senior officials in Jerusalem, including the prime minister, about the situation, including his meetings with American lawmakers and Jewish community leaders. The Obama administration would be less interested in what the Israelis were doing than in the actions of those who actually had the ability to block the deal—namely, Senate and House members. The administration then fed this information to members of the press, who were happy to relay thinly veiled anti-Semitic conceits by accusing deal opponents of dual loyalty and being in the pay of foreign interests.
It didn’t take much imagination for members of Congress to imagine their names being inserted in the Iran deal echo chamber’s boilerplate—that they were beholden to “donors” and “foreign lobbies.” What would happen if the White House leaked your phone call with the Israeli ambassador to a friendly reporter, and you were then profiled as betraying the interests of your constituents and the security of your nation to a foreign power? What if the fact of your phone call appeared under the byline of a famous columnist friendly to the Obama administration, say, in a major national publication?
To make its case for the Iran Deal, the Obama administration redefined America’s pro-Israel community as agents of Israel. They did something similar with Trump and the Russians—whereby every Russian with money was defined as an agent of the state. Where the Israeli ambassador once was poison, now the Russian ambassador is the kiss of death—a phone call with him led to Flynn’s departure from the White House and a meeting with him landed Attorney General Jeff Sessions in hot water.
Did Trump really have dealings with FSB officers? Thanks to the administration’s whisper campaigns, the facts don’t matter; that kind of contact is no longer needed to justify surveillance, whose spoils could then be weaponized and leaked. There are oligarchs who live in Trump Tower, and they all know Putin—ergo, talking to them is tantamount to dealing with the Russian state.
Yet there is one key difference between the two information operations that abused the foreign-intelligence surveillance apparatus for political purposes. The campaign to sell the Iran deal was waged while the Obama administration was in office. The campaign to tie down Trump with the false Russia narrative was put together as the Obama team was on its way out.
The intelligence gathered from Iran Deal surveillance was shared with the fewest people possible inside the administration. It was leaked to only a few top-shelf reporters, like the authors of The Wall Street Journal article, who showed how the administration exploited a loophole to spy on Congress. Congressmen and their staffs certainly noticed, as did the Jewish organizations that were being spied on. But the campaign was mostly conducted sotto voce, through whispers and leaks that made it clear what the price of opposition might be.
The reason the prior abuse of the foreign-intelligence surveillance apparatus is clear only now is because the Russia campaign has illuminated it. As The New York Times reported last month, the administration distributed the intelligence gathered on the Trump transition team widely throughout government agencies, after it had changed the rules on distributing intercepted communications. The point of distributing the information so widely was to “preserve it,” the administration and its friends in the press explained—“preserve” being a euphemism for “leak.” The Obama team seems not to have understood that in proliferating that material they have exposed themselves to risk, by creating a potential criminal trail that may expose systematic abuse of foreign-intelligence collection.
Lee Smith is a senior editor at the Weekly Standard and a senior fellow at the Hudson Institute. He is also the author of the recently published The Consequences of Syria.
 Back to the half a trillion dollars….
Back to the half a trillion dollars….

 VOA
VOA


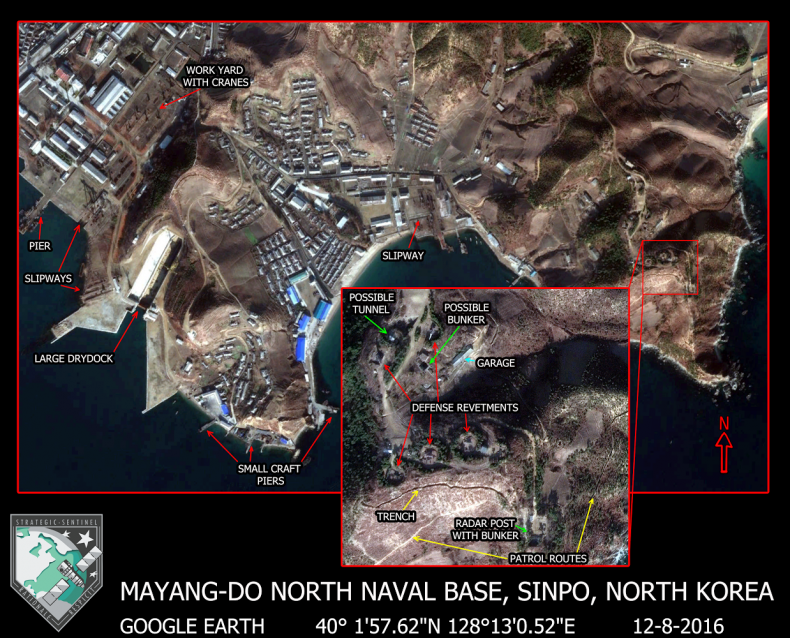
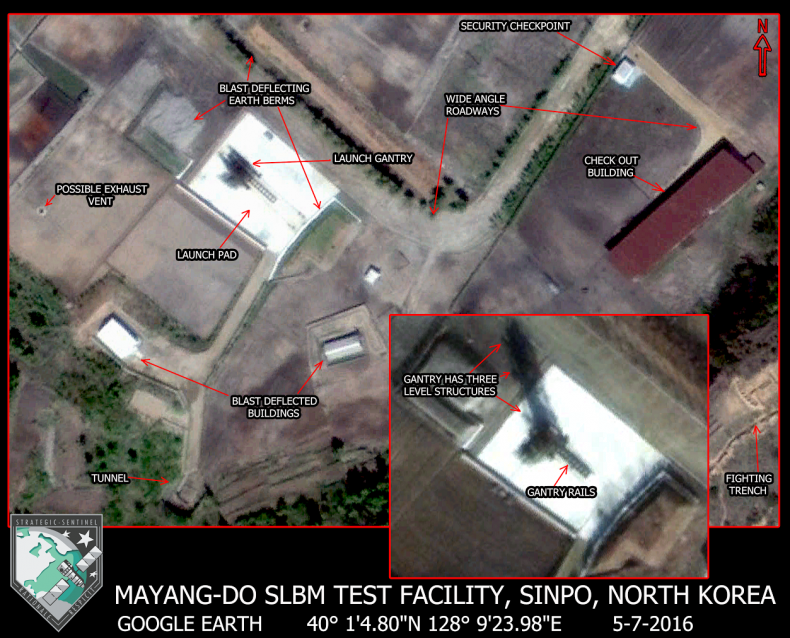
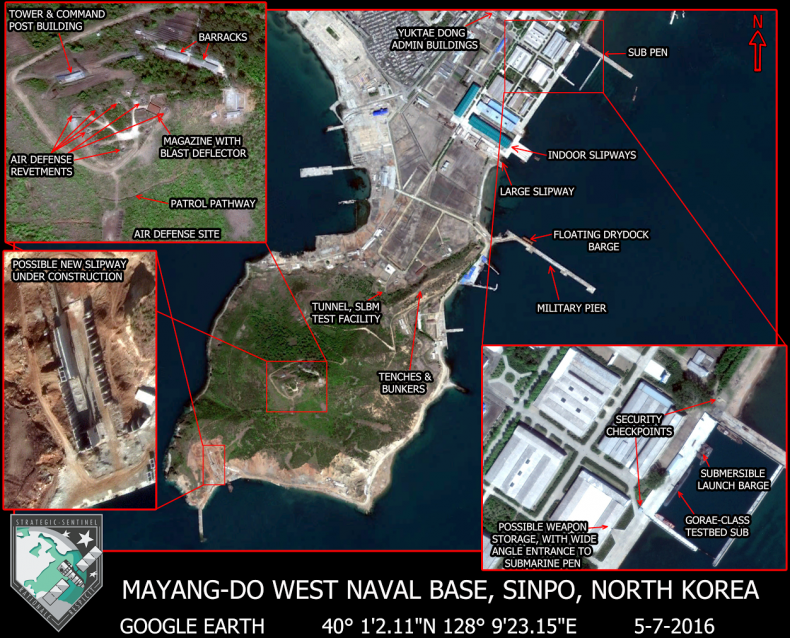
 She wrote a book, it is chilling and a must read,
She wrote a book, it is chilling and a must read, 
