Primer: The Mann Act (also known as the White-Slave Traffic Act of 1910) is a federal law that criminalizes the transportation of “any woman or girl for the purpose of prostitution or debauchery, or for any other immoral purpose.” More here.
Hunter also used the prostitution expenses as deductions on his income tax filings…when EVER they got filed, if they did in the first place.
Primer #2: Chateau Marmont is a members only hotel
 Chateau Marmont says 70% of its clientele are repeat guests. Photo Credit: 4kclips/Shutterstock source
Chateau Marmont says 70% of its clientele are repeat guests. Photo Credit: 4kclips/Shutterstock source
Hunter Biden once denied putting “a [expletive] hole in any wall” at the Chateau Marmont, a swanky California hotel where he was alleged to have been banned for drug-fueled antics.
An IRS agent said investigators retrieved the photos showing “the destruction” Mr. Biden wrought on the rooms.
Agents said they also obtained, through a search warrant, WhatsApp messages from Mr. Biden’s iCloud account. Among them is a striking instance in which he uses his father as a threat to a Chinese Communist Party member and business associate.
Agents said they interviewed prostitutes whom the younger Mr. Biden hired and flew out, sometimes paying for first-class tickets, to meet him and engage in sex — and then wrote off the payments as business expenses. Agents talked with the owner of a sex club to which Mr. Biden paid $10,000, which he then wrote off on his taxes as a golf club membership.
For a Washington that is often burned by too-good-to-be-true stories such as the Steele dossier, the revelations about Hunter Biden by two IRS criminal investigators may seem, well, too good to be true.
IRS Special Agent Gary Shapley and another agent, known in congressional committee documents as “Mr. X,” testified for hours, under oath, that they had the goods to back up what they were saying.
In some cases, they have already provided it to Congress, either in documents or by reading messages into the transcript of the testimony they delivered.
They spent years building a case against Hunter Biden on tax law violations. They said they interviewed 60 witnesses, issued subpoenas and followed the trail of his income, businesses and expenses, particularly those he tried to write off on his taxes.
That was why they were interested in the Chateau Marmont in the first place.
“So he deducted a lot for the Chateau Marmont, and he actually was blacklisted and thrown out of the Chateau Marmont. We actually have videos — or we have photos of the rooms and the destruction that was done to the rooms,” Mr. X told the House Ways and Means Committee on June 1.
Mr. Shapley said they were investigating Mr. Biden’s 2018 tax return, which he didn’t file until 2020, in which he was writing off business expenses such as $25,000 to a girlfriend and $10,000 for a “golf membership.”
“We’ve talked to the person that owned that sex club, and they confirmed that he was there,” said Mr. X. “And the guy has to pay $10,000, and the girl — whoever is referring him there doesn’t have to pay anything. So that was deducted on the tax return.”
One woman whom Mr. Biden labeled as his West Coast assistant was part of the sex club situation, the agent said.
“Some ended up being his girlfriends. So they all kind of morphed and changed. So I want to be accurate in how I represent them. But there were a lot of females that I believe he was having sexual relationships with that I ended up interviewing,” said Mr. X, adding that the women were being paid for sex.
He said the Justice Department had been compiling data on cases in which Mr. Biden had prostitutes cross state lines in violation of a federal law known as the Mann Act.
“I know there was an effort at some point to compile them, but I don’t know what ultimately happened with them,” Mr. X said.
The write-offs weren’t mistakes, the agents said. They saw Mr. Biden’s highlighting of his bank statements where he was picking what exactly he wanted to deduct and what he wouldn’t deduct.
It was so bad that his accountants, as if to distance themselves from the factual claims on the forms, made him sign a representation letter, in which he tells his tax preparers that all the income and deductions he is reporting are accurate.
“I’ve never seen that in my career,” Mr. X told Congress.
The IRS agents, in addition to the iCloud account, also gained access to QuickBooks accounts and a Dropbox account and retrieved data from the laptop that Mr. Biden left at a Delaware repair shop.
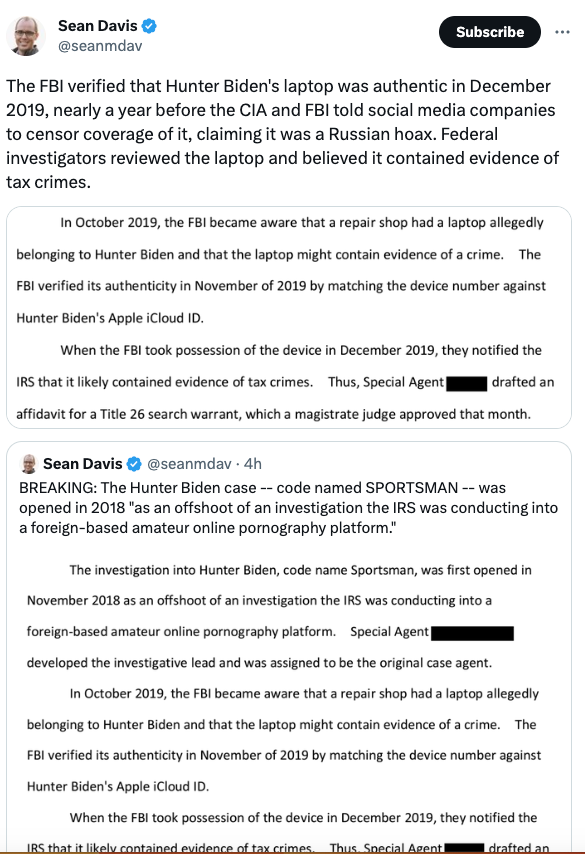
The agents revealed that the laptop was actually three pieces — a laptop, a hard drive and another external hard drive. They were in the FBI’s hands in 2019, and the bureau had verified that the data was Mr. Biden’s by November that year.
That was nearly a year before high-level former intelligence officials, some from the FBI, along with Hunter’s father during a presidential debate, dismissed the laptop as Russian misinformation amid the heat of the 2020 campaign.
iPhone messages were on the hard drive, but they were encrypted. It wasn’t until agents found a business card with the password that they were able to gain access, Mr. Shapley said in a set of Oct. 22, 2020, notes detailing the timeline of the laptop.
The notes were entered into the committee’s transcript of his testimony.
After the testimony was taken by the committee but before its public release, Mr. Biden agreed to plead guilty to two misdemeanors and the prosecution agreed not to ask for prison time. Another charge, a gun felony, will be resolved with a diversion, which means that if Mr. Biden keeps his nose clean while on probation, the charge will be dropped.
The agents’ work can’t definitively answer whether Hunter Biden should be facing more serious criminal charges, but it does give the public an unparalleled look at some of the evidence prosecutors had in hand when they cut the deal.
Hunter Biden has a court date scheduled for late next month, when a federal judge will decide whether to bless the deal.
Dean Zerbe, a leading IRS whistleblower lawyer who is serving as Mr. X’s attorney and who used to serve as tax counsel for the top Republican on the Senate Finance Committee, said it was striking to have two career agents with years of experience testify to essentially the same pattern of facts.
“We never had anyone of this stature coming forward from the IRS to speak to us about problems,” he said, citing his years on Capitol Hill. “That alone sets these guys apart.”
The testimony was released Thursday and set social media afire. President Biden’s defenders blasted the two agents for delivering a “fairy tale” or a fabrication. Some questioned the existence of the emails that the agents, under oath, had read to the committee.
Former MSNBC host turned podcaster Keith Olbermann opined that the agents had “no evidence” to back up their claim that Attorney General Merrick Garland hamstrung the investigation.
Christopher Clark, Mr. Biden’s attorney, issued a statement saying there were “serious questions” about the WhatsApp message where Hunter Biden used his father’s goodwill as a bargaining chip with a Chinese business associate.
The WhatsApp message may be the most explosive part of the testimony the Ways and Means Committee released last week. It suggests that Hunter Biden made a practice of using his father, at the time the former vice president was pondering his own presidential bid, as a threat.
Mr. Shapley said agents obtained it through a search warrant against Hunter Biden’s iCloud account.
The White House didn’t address whether President Biden was present when Hunter Biden sent the message but insisted he was not involved in his son’s transaction with Henry Zhang, the Chinese business associate.
“The president was not in business with his son,” press secretary Karine Jean-Pierre said.
Mr. Biden, asked Monday by reporters whether he had lied about any business dealings with his son, replied “No.”
Mr. X said Hunter Biden had tax issues dating to the early part of the century, including filing late and owing massive bills.
He said his investigation, which began in 2018, covered 2014 through 2019. He said charges should have been brought for each year. Those included failure to timely file or to pay taxes in 2016, 2017 and 2019; failure to timely pay in 2015; filing a false return and evasion of tax assessment in 2014; and failure to timely file and pay tax, filing a false return and evasion of tax assessment in 2018.
The 2014 and 2018 charges rose to the level of felonies, Mr. X said.
Hunter Biden did begin making $10,000 monthly payments on his delinquent taxes in 2017, in what the IRS investigators called an arrangement with his tax team. He stopped making the payments on March 5, 2018.
“There’s an actual email where he asked how long he can go without paying his taxes,” said Mr. X said, pointing out that Hunter Biden earned $2.4 million from Hudson West III, a firm with connections to Chinese money, but he “can’t make the $10,000 payment he was making on his taxes.”