Primer: Steve Bannon works for President Trump in the White House.
Steve Bannon is a star – for Al-Qaeda, that featured him on the cover of their newspaper
Then this headline….
The new scandal headlines for today is WikiLeaks, telling us they published the largest cache of secret CIA documents relating to the CIA’s ability to hack, break encryption and install malware. This is a problem? The problem is not the tools the CIA has, the problem is that someone inside the agency stole them and delivered them to WikiLeaks.
It is a good thing that the agency has these resources, why you ask?
Well….try this…The threat is real from Russians, Chinese, North Korea, Iran, Syria, Ukraine, al Qaeda and Islamic State…
Remember Stuxnet? This was a successful joint program under the Bush presidency with Israel to infect the Iranian nuclear program and it was to forces the centrifuges to spin out of control, which they did. Ultimately, it caused the progress of the Iranian infrastructure to be delayed substantially. It was in fact later uncovered by cyber scientists working for Siemens, the hardware and software platform used as the operating system. Good right? Yes.
Well, there is more…
In recent years, Iran and North Korea have been sharing nuclear scientists and engineers, parts, testing and missile collaboration. So far, the missiles launched by North Korea for the most part have been unsuccessful, or at least did not achieve the ultimate objective and that is an official target strike. Why? Because of the United States. How so you ask?
Over the weekend, North Korea fired off 4 missiles in succession toward Japan. They did not reach the mainland but did reach the waterway that is part of the Japanese economic zone for maritime operations. We have American cyberwarriors that are doing effective work causing the missiles to fly off course or to technically fail. The objective is to use non-explosive weaponry to foul the North Korea and hence Iran’s missile program and while North Korea is not especially connected to the internet, some related systems are connected and then there is electronic warfare.
We know that Islamic State is a terror operation that has militant cells in an estimated 30 countries. While they have depraved methods of murder, rape and terror, they too have a cyber operation.
The Will to Act
One question is whether ISIS will be consumed with the protection and continued expansion of its immediate fighting fronts, i.e., the “near enemy,” or whether its scope of vision includes America’s homeland. The Economist advances a strong case that desire for such expansion not only exists but will be exercised: “With its ideological ferocity, platoons of Western passport holders, hatred of America and determination to become the leader of global jihadism, ISIS will surely turn, sooner or later, to the ‘far enemy’ of America and Europe.”
And perhaps any doubt the militant’s sights are on America was removed by ISIS leader Abu Bakr al-Baghdadi’s Sept. 22 call for jihadists to not wait for the order but to rise, take up arms, and “kill Americans and other infidels” wherever they are. Clearly the group is showing no hesitancy in its desire to strike the U.S. heartland on a personal scale.
Cyber Operations Capability?
As to whether ISIS will have the capability to mount cyber operations against the U.S., David DeWalt, head of cybersecurity firm FireEye, believes that ISIS will follow in the footsteps of the Syrian Electronic Army and the Iran-based Ajax Security Team to target the United States and other Western nations.
“We’ve begun to see signs that rebel terrorist organizations are attempting to gain access to cyber weaponry,” DeWalt stated recently. He added that booming underground markets dealing in malicious software make offensive cyber weapons just an “Internet transaction” away for groups such as ISIS. More here.
Is there more to this that we should know? Yes…
There is the Middle East and we have a major vested interest in the region.
***
Cybersecurity in the Gulf: The Middle East’s Virtual Frontline
Cybersecurity is often discussed in relation to the major global powers: China’s economic espionage, Russian influence operations, and U.S. dragnet global surveillance to thwart terrorism.
However, as other countries move to digitize their economies, cybercriminals are zeroing in on these new and lucrative targets while regional players are quickly incorporating cyber capabilities into their own arsenals for achieving strategic ends.
The Middle East, particularly the Gulf states, are quickly recognizing the urgent need for better cybersecurity, while regional adversaries such as Iran have begun weaponizing code as an extension of broader strategic goals within the region. What, though, is the Gulf’s current cybersecurity atmosphere, and how does Iran’s emerging use of offensive cyber capabilities fit into its broader strategy in the Middle East?
Wajdi Al Quliti, the Director of Information Technology at the Organization of Islamic Cooperation, notes that “the region’s dramatic strides towards digitization—expected to add over $800 billion to GDP and over 4 million jobs by 2020—is making the Gulf a major target for fast evolving cyber threats.” Much like other regions, the Gulf is finding it difficult to sufficiently create criminal deterrence due to segmented laws and difficulties in attribution. Al Quliti argues “cross-border cooperation and common cybersecurity structures could prove to be a game-changing advantage in the fight against cybercrime.” However, “the elephant in the room,” according to Al Quliti, “is the issue of state-sponsored hacking, in which case harmonized laws are unlikely to make a difference.”
A critical point in nation-state hacking in the Middle East begins with the Stuxnet worm. Discovered in 2010 burrowed deep in Iranian networks, the worm had slowly been sabotaging Iran’s nuclear ambitions. Then in 2011 CrySyS Lab discovered Duqu, a cyber espionage tool tailored to gather information from industrial control systems, and in 2012, Kaspersky Labs identified Flame, another espionage tool, targeting various organizations in the Middle East. Both Duqu and Flame are associated with Stuxnet and attributed back to the Equation Group, widely considered an arm of the National Security Agency.
In 2012, Iranian officials found a wiper virus erasing files in the network of the Oil Ministry headquarters in Tehran, leading the ministry to disconnect all oil terminals from the Internet to prevent the virus from spreading. It is uncertain who was behind the attacks, but a mere four months later, Saudi Arabia’s largest oil company, Saudi Aramco, was hit with a similar wiper virus known as Disttrack—possibly coopted from the previous attack on Iran’s oil industry.
The data-erasing malware sabotaged three-quarters, some 35,000 of the company’s computers while branding screens with an image of a burning American flag. A few months later, another wiper virus attacked Qatar’s RasGas.
Al Quliti identifies “the region’s heavy dependence on oil and gas—as well as the oil and gas-powered desalination plants that provide much of the region’s fresh water”—as “a source of cyber vulnerability,” adding that “any cyber attack on these installations could prove catastrophic and might result in a humanitarian disaster.”
The sabotage operations against the Gulf’s oil industry have been attributed by various cybersecurity firms—but not officially by any government—to a group called Shamoon, thought to be an arm of the Iranian government.
Michael Eisenstadt, the Director of the Military and Security Studies Program at the Washington Institute for Near East Policy, notes that “cyber allows Iran to strike at adversaries globally, instantaneously, and on a sustained basis, and to potentially achieve strategic effects in ways it cannot in the physical domain.” For example, in March 2016, the Justice Department indicted seven Iranian Revolutionary Guard members for distributed denial of service attacks against U.S. banks in 2012 in retaliation for Iran sanctions imposed the previous year, as well as for infiltrating the systems of a small New York dam in 2013—a possible testing ground for penetrating larger pieces of U.S. critical infrastructure. In 2014, the same year North Korea set its sights on Sony Pictures, Iran’s cyber capabilities again reached into the United States, using another wiper virus to sabotage the operations of the Las Vegas Sands casino, whose chief executive, a staunch supporter of Israel, had suggested detonating a nuclear bomb in the heart of Tehran.
Last November, right before a major OPEC meeting, a variation of the Disttrack wiper used against Saudi Aramco struck again, now fitted with a picture of Alan Kurdi, the drowned Syrian toddler who washed up in Turkey in 2015. The virus targeted six Saudi organizations, most notably the Saudi General Authority of Civil Aviation, delivering its payload at the close of business on a Thursday, the start of the Islamic weekend, for maximum impact. Some experts speculate the November attack could have also been a false-flag operation to derail the Iranian nuclear deal.
Interestingly, for both the 2012 and 2016 Shamoon attacks, the wiper came fitted with stolen login credentials that Symantec now believes could have been gleaned from a cyber espionage tool, known as Greenbug, found on one of the administrator computers of a Saudi organization targeted in November. The potential link between Greenbug and the Shamoon group opens up possible investigations into the group’s involvement in a host of other Greenbug attacks throughout the Middle East, including breaches in Saudi Arabia, Bahrain, Iraq, Qatar, Kuwait, Turkey, and even Iran—though likely for domestic surveillance on dissidents. Just last week, another wiper virus hit 15 Saudi organizations, including the Ministry of Labor, prompting the government to issue an urgent warning of pending Shamoon attacks.
Eisenstadt points out that “Iran’s cyber activities show that a third-tier cyber power can carry out significant nuisance and cost-imposing attacks,” and “its network reconnaissance activities seem to indicate that it is developing contingency plans to attack its enemies’ critical infrastructure.” According to Eisentadt, is now seems that “in the past decade, Iran’s cyber toolkit has evolved from a low-tech means of lashing out at its enemies by defacing websites and conducting DDoS attacks, to a central pillar of its national security concept.”
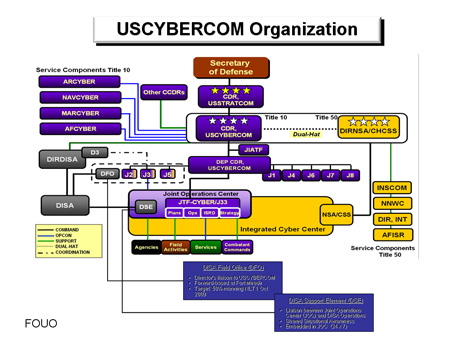
Beginning to understand why the CIA and the other agencies are building cyber command war-rooms?






 The Asahi Shimbun
The Asahi Shimbun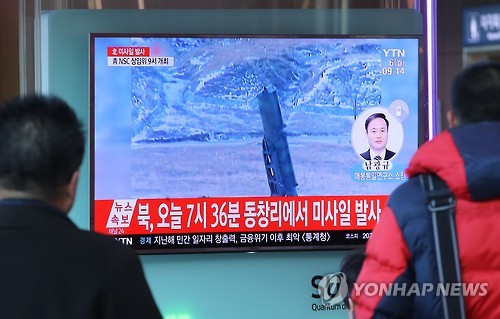







 Then we have the gullible Prime Minister of Canada, Justin Trudeau who has invited Middle Eastern migrants, asylees and refugees in a welcome to Canada. Yet the intelligence and security authorities in Canada have a different position.
Then we have the gullible Prime Minister of Canada, Justin Trudeau who has invited Middle Eastern migrants, asylees and refugees in a welcome to Canada. Yet the intelligence and security authorities in Canada have a different position.









