A hacking group has compromised at least nine global organizations in the fields of technology, defense, energy and other key sectors as part of an apparent espionage campaign. Attribution is still ongoing, specific tools and methods used in the apparent hacking efforts are in line with those used by Chinese cyber-espionage group Emissary Panda, also known as TG-3390, APT 27 and Bronze Union.
While China has indeed surpassed the United States in the size of their Navy, the other concern is the build up of Chinese nuclear weapons. Meanwhile, the United States has deployed at least 30 U.S.military forces to Taiwan for training.For years, U.S.-Taiwan military exchanges have been thought of as an open secret—also known by the People’s Republic of China (PRC) leadership in Beijing. However, Tsai became the first Taiwanese leader in decades to publicly acknowledge the existence of a training program.
The United States has deployed the Iron Dome missile-defense system for testing in Guam by U.S. military planners concerned about possible Chinese attacks.
WAR GAMES:
The Chinese military – the People’s Liberation Army – is waging so-called gray-zone warfare against Taiwan. This consists of an almost daily campaign of intimidating military exercises, patrols and surveillance that falls just short of armed conflict. Since that report, the campaign has intensified, with Beijing stepping up the number of warplanes it is sending into the airspace around Taiwan. China has also used sand dredgers to swarm Taiwan’s outlying islands.
Military strategists tell Reuters that the gray-zone strategy has the potential to grind down Taipei’s resistance – but also that it may fall short, or even backfire by strengthening the island’s resolve. They are also envisioning starker futures. While they can’t predict the future, military planners in China, Taiwan, the United States, Japan and Australia are nonetheless actively gaming out scenarios for how Beijing might try to seize the prized island, and how Taiwan and America, along with its allies, might move to stop it.Xi’s options include seizing Taiwan’s outlying islands, blockades or all-out invasion. Some Taiwanese military experts say Beijing’s next step might be to seize the lightly defended and remote Pratas Islands in the north of the South China Sea. Any of these moves could spin out of control into war between China and America over Taiwan.
Reuters has published a comprehensive report and possible scenarios.
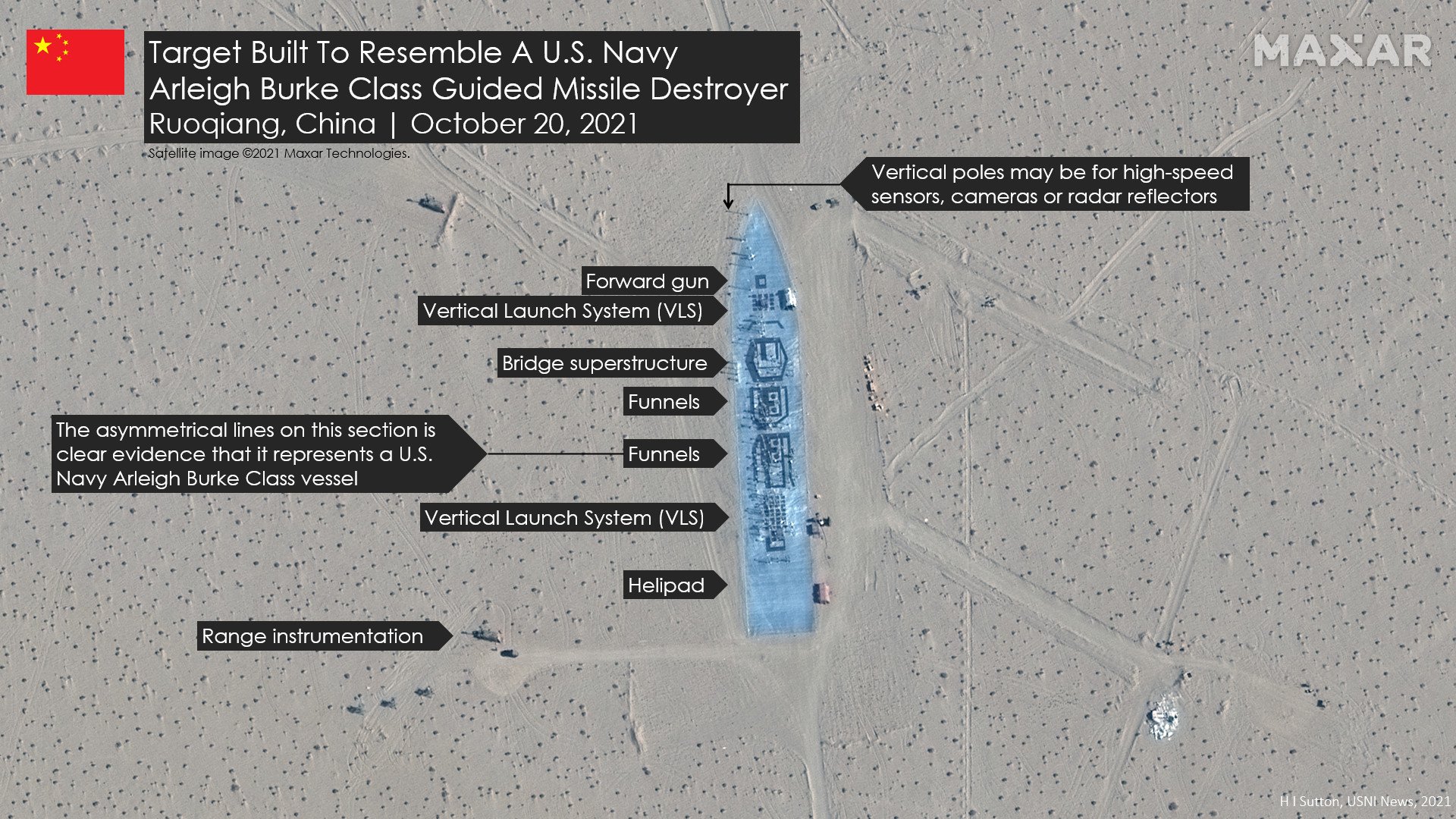
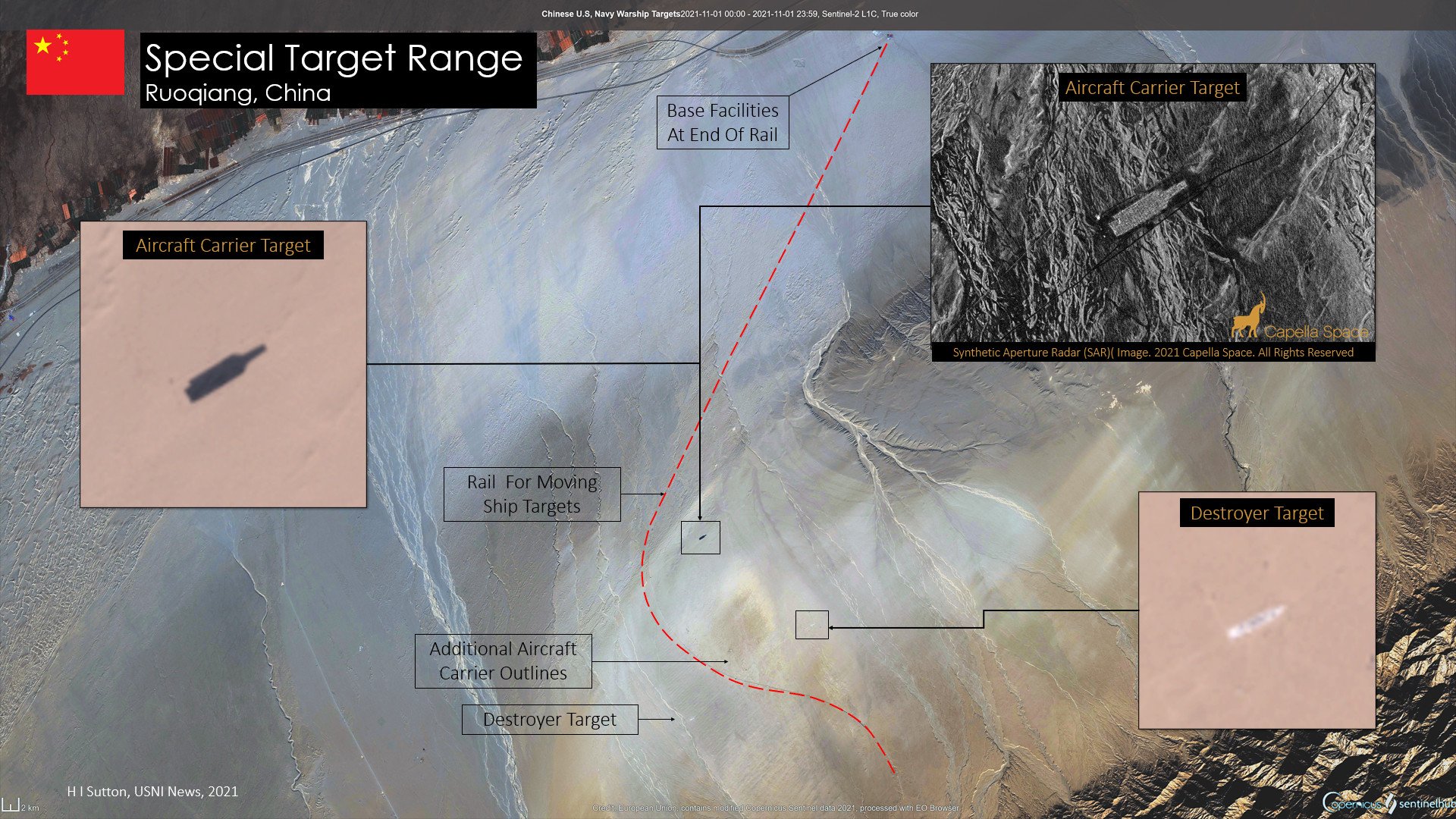
The Chinese military has built targets in the shape of an American aircraft carrier and other U.S. warships in the Taklamakan desert as part of a new target range complex, according to photos provided to USNI News by satellite imagery company Maxar.
The full-scale outline of a U.S. carrier and at least two Arleigh Burke-class destroyers are part of the target range that has been built in the Ruoqiang region in central China. The site is near a former target range China used to test early versions of its so-called carrier killer DF-21D anti-ship ballistic missiles, according to press reports in 2013.
This new range shows that China continues to focus on anti-carrier capabilities, with an emphasis on U.S. Navy warships. Unlike the Iranian Navy’s aircraft carrier-shaped target in the Persian Gulf, the new facility shows signs of a sophisticated instrumented target range.
A target in the shape of a U.S. Destroyer in the Taklamakan Desert in Central China. H I Sutton Illustration for USNI News Satellite image ©2021 Maxar Technologies Used with Permission
The carrier target itself appears to be a flat surface without the carrier’s island, aircraft lifts, weapons sponsons or other details, the imagery from Maxar shows. On radar, the outline of the carrier stands out from the surrounding desert – not unlike a target picture, according to imagery provided to USNI News by Capella Space.
There are two more target areas representing an aircraft carrier that do not have the metaling, but are distinguishable as carriers due to their outline. But other warship targets appear to be more elaborate. There are numerous upright poles positioned on them, possibly for instrumentation, according to the imagery. Alternatively these may be used for radar reflectors to simulate the superstructure of the vessel.
The facility also has an extensive rail system. An Oct. 9 image from Maxar showed a 75 meter-long target with extensive instrumentation on a 6 meter-wide rail.
The area has been traditionally used for ballistic missile testing, according to a summary of the Maxar images by geospatial intelligence company AllSource Analysis that identified the site from satellite imagery.
“The mockups of several probable U.S. warships, along with other warships (mounted on rails and mobile), could simulate targets related to seeking/target acquisition testing,” according to the AllSource Analysis summary, which said there are no indications of weapon impact areas in the immediate vicinity of the mockups. “This, and the extensive detail of the mockups, including the placement of multiple sensors on and around the vessel targets, it is probable that this area is intended for multiple uses over time.“
Analysis of historical satellite images shows that the carrier target structure was first built between March and April of 2019. It underwent several rebuilds and was then substantially dismantled in December 2019. The site came back to life in late September of this year and the structure was substantially complete by early October.
Detailed Photos of the mobile target at the Ruoqiang facility. H I Sutton Illustration for USNI News Satellite image ©2021 Maxar Technologies Used with Permission
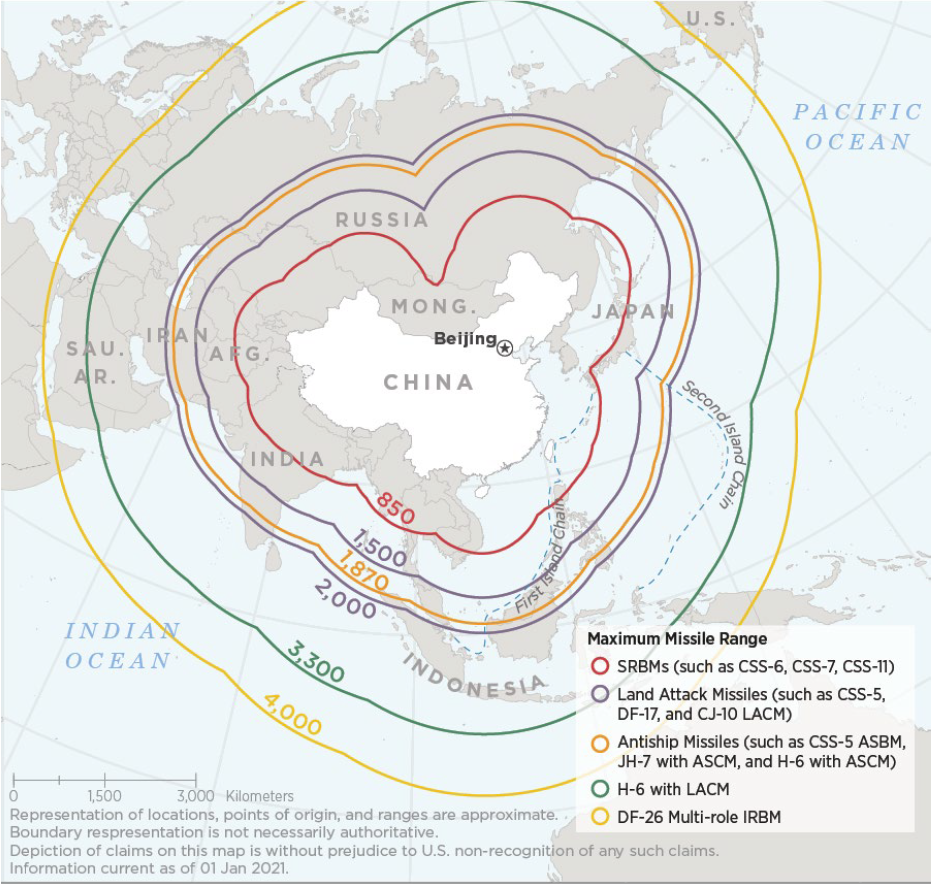
China has several anti-ship ballistic missile programs overseen by the People’s Liberation Army Rocket Force. The land-based CSS-5 Mod 5 (DF-21D) missile has a range of over 800 nautical miles. It has a maneuverable reentry vehicle (MaRV) to target ships. The larger CSS-18 (DF-26) has a range of around 2,000 nautical miles.
“In July 2019, the PLARF conducted its first-ever confirmed live-fire launch into the South China Sea, firing six DF-21D anti-ship ballistic missiles into the waters north of the Spratly Islands,” according to the Pentagon’s latest annual report on China’s military. The Chinese are also fielding a longer range anti-ship ballistic missile that initially emerged in 2016.
“The multi-role DF-26 is designed to rapidly swap conventional and nuclear warheads and is capable of conducting precision land-attack and anti-ship strikes in the Western Pacific, the Indian Ocean, and the South China Sea from mainland China. In 2020, the PRC fired anti-ship ballistic missiles against a moving target in the South China Sea, but has not acknowledged doing so,” reads the report.
A Nov. 5, 2021 Capella Space synthetic aperture radar image of the target in the shape of a U.S. aircraft carrier in the Taklamakan Desert H I Sutton Illustration for USNI News
In addition to the land-based anti-ship ballistic missiles, China has a program to equip the People’s Liberation Army Navy H-6 bombers with a massive anti-ship ballistic missile. First revealed in 2018, the CH-AS-X-13 will likely be the largest air-launched missile in existence, and would be large enough to accommodate a hypersonic warhead.
Another possible launch platform for anti-ship ballistic missiles is the new Type-055 Renhai Class large destroyer. Described as a guided-missile cruiser, it will be capable of carrying anti-ship ballistic missiles, according to the Pentagon report.
It’s not the first time China has built an aircraft carrier target in the desert. Since 2003, a large concrete pad, roughly the size of a carrier, has been used as a target. The slab, which is part of the Shuangchengzi missile test range, has been hit many times and is frequently repaired. The new site in the Taklamakan desert is 600 miles away and is much more evolved. The newer ship targets are closer approximations of the vessels that they are supposed to represent.
While questions remain on the extent of weapons that will be tested at the new facility, the level of sophistication of what can now be seen at the site show the PLA is continuing to invest in deterrents to limit the efficacy of U.S. naval forces close to China – in particular targeting the U.S. carrier fleet.
According to the Pentagon report released last week, a primary objective of the PLARF will be to keep U.S. carriers at risk from anti-ship ballistic missiles throughout the Western Pacific.