Last week, Defense Secretary Mattis said:
Defense Secretary Jim Mattis this week voiced new U.S. opposition to China’s continued militarization of islands in the South China Sea.
“We remain highly concerned with continued militarization of features in the South China Sea,” Mattis told reporters on Monday as he traveled to Vietnam.
Mattis also said China is using predatory economics to seek control over other nations.
The Chinese are engaged in a global infrastructure development plan called the Belt and Road Initiative that U.S. officials have said is being used by Beijing to expand influence and control abroad, and expand Chinese military bases around the world.
Mattis said the predatory economic policies include loans “where massive debt is piled on countries that fiscal analysis would say they are going to have difficulty, at best, repaying in the smaller countries.”
The defense secretary, echoing the new U.S. hardline policy toward China, said the United States is not seeking to “contain” China but wants more reciprocal relations.
In part from Newsweek:
“Beijing can now deploy military assets, including combat aircraft and mobile missile launchers to the Spratly Islands at any time,” said the Asia Maritime Transparency Initiative (AMTI) on Monday in a report that included images of the three man-made islands—Fiery Cross reef, Subi, and Mischief. Its director Greg Poling told Voice of America that new antennas had been spotted on Subi and Fiery Cross, so he expected deployments there soon.
The Spratly Islands are around 500 miles from the coast of China, and Fiery Cross Reef about 740 miles from mainland China. It is approximately 170 miles off the coast of Vietnam. Why did China build these islands and how did they manage to make land out of sea?
***
But media is not paying attention.
It gets worse.
Researchers have mapped out a series of internet traffic hijacks and redirections that they say are part of large espionage and intellectual property theft effort by China.
The researchers, Chris Demchak of the United States Naval War College and Yuval Shavitt of the Tel Aviv University in Israel, say in their paper that state-owned China Telecom hijacked and diverted internet traffic going to or passing through the US and Canada to China on a regular basis.
Tel Aviv University researchers built a route tracing system that monitors BGP announcements and which picks up on patterns suggesting accidental or deliberate hijacks and discovered multiple attacks by China Telecom over the past few years.
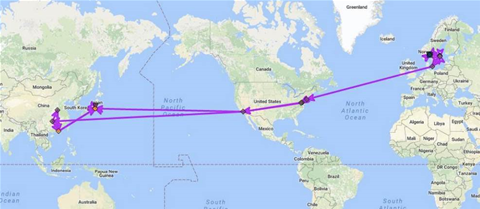
In 2016, China Telecom diverted traffic between Canada and Korean government networks to its PoP in Toronto. From there, traffic was forwarded to the China Telecom PoP on the US West Coast and sent to China, and finally delivered to Korea.
Normally, the traffic would take a shorter route, going between Canada, the US and directly to Korea. The traffic hijack lasted for six months, suggesting it was a deliberate attack, Demchak and Shavitt said.
Demchak and Shavitt detailed other traffic hijacks, including one that saw traffic from US locations to a large Anglo-American bank’s Milan headquarters being terminated in China, and never delivered to Italy, in 2016.
During 2017, traffic between Scandinavia and Japan, transiting the United States, was also captured by China Telecom, ditto data headed to a mail server operated by a large Thai financial company.
China Telecom is able to divert the traffic by announcing bogus routes via the Border Gateway Protocol (BGP) that governs data flows between Autonomous Systems, the large networks operated by telcos, internet providers and corporations.
After the traffic was copied by China Telecom for encyption breaking and analysis, it was delivered to the intended networks with only small delays. Demchak and Shavitt said.
Such hijacking is difficult to detect as China Telecom has multiple points of presence (PoPs) in North America and Europe that are physically close to the attacked networks, causing almost unnoticeable traffic delivery delays despite the lengthened routes.
China in comparison does not allow overseas telcos to establish PoPs in the country, and has only three gateways into the country, in Beijing, Shanghai and Hong Kong. This isolation protects the country’s domestic and transit traffic from foreign hijacking.
BGP hijacking of internet traffic is a common phenomenon, one which requires the support of large network operators to exploit at scale.
While the US and China agreed in 2015 to not hack one another’s computer networks, the deal did not cover hijacking of internet backbones, Demchak and Shavitt pointed out.
The researchers suggest the allied democratic nations establish an “access reciprocity” policy for internet PoPs located in their countries, to address the traffic hijacking.
Under the access reciprocity policy US telcos and providers should be allowed to set up PoPs in China, Demchak and Shavitt said.
If access reciprocity is refused, “then an appropriate defence policy in response could state that no traffic to or from the US or ally is allowed to enter a China Telecom PoP in the US or in the ally’s networks,” the researchers suggested.
Such a policy could be inserted into BGP routing tables as required for automatic implementation.