A few members of congress did ask Mark Zuckerberg about bundled permissions and Zuckerberg played dumb on the question. Remember that thing when your phone asks for permission to post to Facebook? Well it goes across all your synchronized devices. What? uh huh…read on.
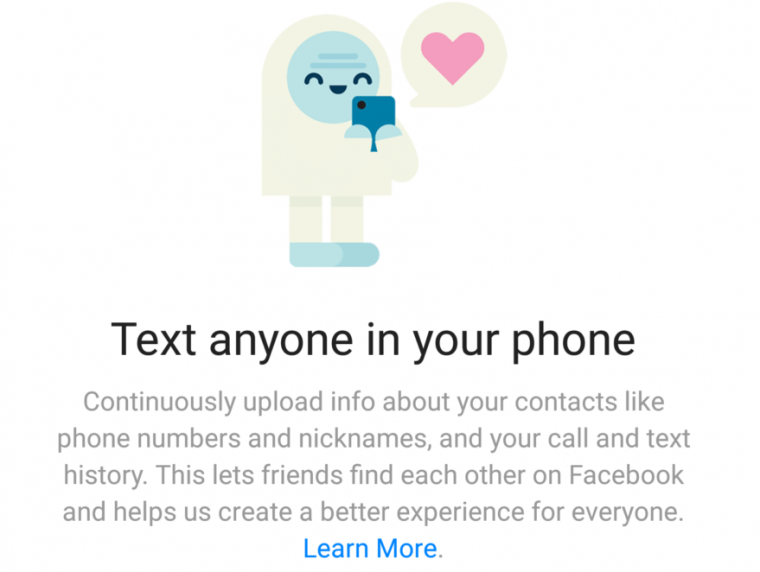 This screen in the Messenger application offers to conveniently track all your calls and messages. But Facebook was already doing this surreptitiously on some Android devices until October 2017, exploiting the way an older Android API handled permissions.
This screen in the Messenger application offers to conveniently track all your calls and messages. But Facebook was already doing this surreptitiously on some Android devices until October 2017, exploiting the way an older Android API handled permissions.
Better check and ask some harder questions…..
[Update, March 25, 2018, 20:24 Eastern Time]: Facebook has responded to this and other reports regarding the collection of call and SMS data with a blog post that denies Facebook collected call data surreptitiously. The company also writes that it never sells the data and that users are in control of the data uploaded to Facebook. This “fact check” contradicts several details Ars found in analysis of Facebook data downloads and testimony from users who provided the data. More on the Facebook response is appended to the end of the original article below.
This past week, a New Zealand man was looking through the data Facebook had collected from him in an archive he had pulled down from the social networking site. While scanning the information Facebook had stored about his contacts, Dylan McKay discovered something distressing: Facebook also had about two years’ worth of phone call metadata from his Android phone, including names, phone numbers, and the length of each call made or received.
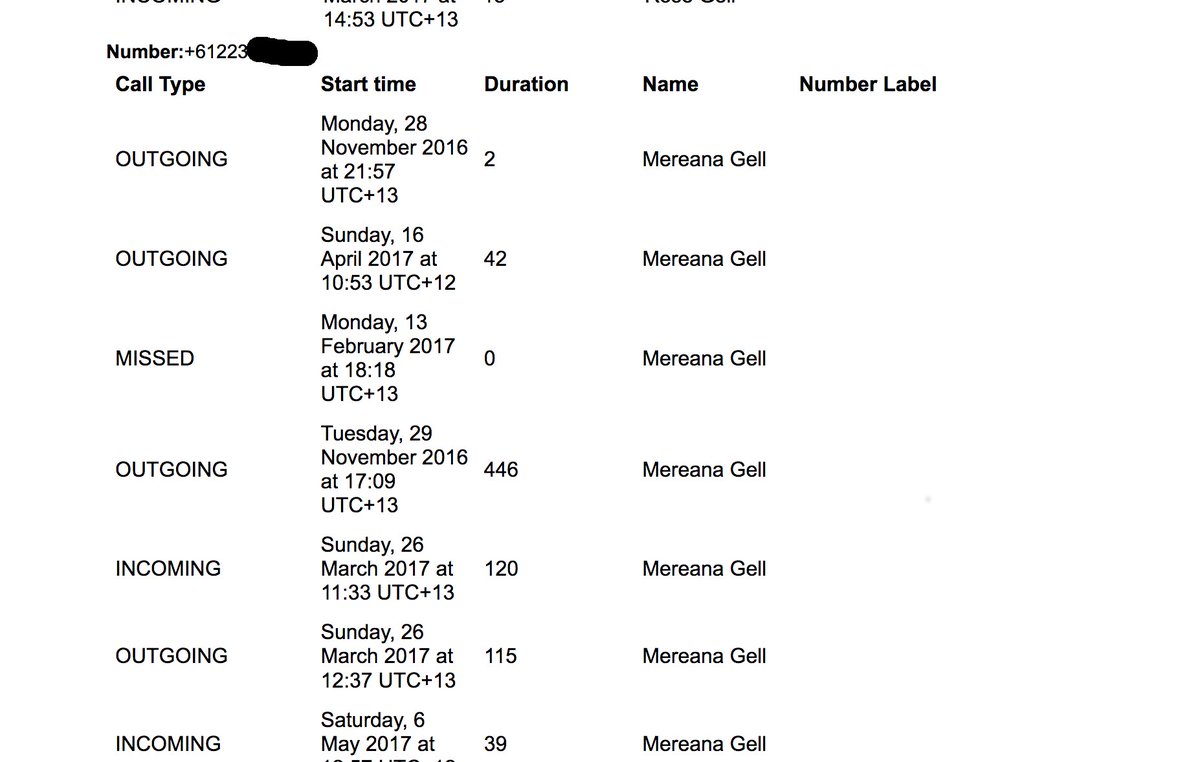
This experience has been shared by a number of other Facebook users who spoke with Ars, as well as independently by us—my own Facebook data archive, I found, contained call-log data for a certain Android device I used in 2015 and 2016, along with SMS and MMS message metadata.
In response to an email inquiry by Ars about this data gathering, a Facebook spokesperson replied, “The most important part of apps and services that help you make connections is to make it easy to find the people you want to connect with. So, the first time you sign in on your phone to a messaging or social app, it’s a widely used practice to begin by uploading your phone contacts.”
The spokesperson pointed out that contact uploading is optional and installation of the application explicitly requests permission to access contacts. And users can delete contact data from their profiles using a tool accessible via Web browser.
Facebook uses phone-contact data as part of its friend recommendation algorithm. And in recent versions of the Messenger application for Android and Facebook Lite devices, a more explicit request is made to users for access to call logs and SMS logs on Android and Facebook Lite devices. But even if users didn’t give that permission to Messenger, they may have given it inadvertently for years through Facebook’s mobile apps—because of the way Android has handled permissions for accessing call logs in the past. (For Facebook’s instructions on turning off continuous contact uploading, go here. )
If you granted permission to read contacts during Facebook’s installation on Android a few versions ago—specifically before Android 4.1 (Jelly Bean)—that permission also granted Facebook access to call and message logs by default. The permission structure was changed in the Android API in version 16. From Android 4.1 on, a single request from those applications would trigger two separate permission requests.
But until the “Marshmallow” version of Android, even with split permissions, all permissions could still be presented all at once, without users getting the option to decline them individually. So Facebook and other applications could continue to gain access to call and SMS data with a single request by specifying an earlier Android SDK version. Starting with Marshmallow, users could toggle these permissions separately themselves. But as many as half of Android users worldwide remain on older versions of the operating system because of carrier restrictions on updates or other issues.
Apple iOS has never allowed access to call log data by third-party apps, overt or silently, so this sort of data acquisition was never possible.
Facebook provides a way for users to purge collected contact data from their accounts, but it’s not clear if this deletes just contacts or if it also purges call and SMS metadata. After purging my contact data, my contacts and calls were still in the archive I downloaded the next day—likely because the archive was not regenerated for my new request. (Update: The cached archive was generated once and not updated on the second request. However, two days after a request to delete all contact data, the contacts were still listed by the contact management tool.)
As always, if you’re really concerned about privacy, you should not share address book and call-log data with any mobile application. And you may want to examine the rest of what can be found in the downloadable Facebook archive, as it includes all the advertisers that Facebook has shared your contact information with, among other things.
Update, March 25, 2018, continued:
Facebook responded to reports that it collected phone and SMS data without users’ knowledge in a “fact check” blog post on Sunday. In the response, a Facebook spokesperson stated:
Call and text history logging is part of an opt-in feature for people using Messenger or Facebook Lite on Android. This helps you find and stay connected with the people you care about, and provide you with a better experience across Facebook. People have to expressly agree to use this feature. If, at any time, they no longer wish to use this feature they can turn it off in settings, or here for Facebook Lite users, and all previously shared call and text history shared via that app is deleted. While we receive certain permissions from Android, uploading this information has always been opt-in only.
This contradicts the experience of several users who shared their data with Ars. Dylan McKay told Ars that he installed Messenger in 2015, but only allowed the app the permissions in the Android manifest that were required for installation. He says he removed and reinistalled the app several times over the course of the next few years, but never explicitly gave the app permission to read his SMS records and call history. McKay’s call and SMS data runs through July of 2017.
In my case, a review of my Google Play data confirms that Messenger was never installed on the Android devices I used. Facebook was installed on a Nexus tablet I used and on the Blackphone 2 in 2015, and there was never an explicit message requesting access to phone call and SMS data. Yet there is call data from the end of 2015 until late 2016, when I reinstalled the operating system on the Blackphone 2 and wiped all applications.
While data collection was technically “opt-in,” in both these cases the opt-in was the default installation mode for Facebook’s application, not a separate notification of data collection. Facebook never explicitly revealed that the data was being collected, and it was only discovered as part of a review of the data associated with the accounts. The users we talked to only performed such reviews after the recent revelations about Cambridge Analytica’s use of Facebook data.
Facebook began explicitly asking permission from users of Messenger and Facebook Lite to access SMS and call data to “help friends find each other” after being publicly shamed in 2016 over the way it handled the “opt-in” for SMS services. That message mentioned nothing about retaining SMS and call data, but instead it offered an “OK” button to approve “keeping all of your SMS messages in one place.”
Facebook says that the company keeps the data secure and does not sell it to third parties. But the post doesn’t address why it would be necessary to retain not just the numbers of contacts from phone calls and SMS messages, but the date, time, and length of those calls for years. Sean Gallagher Sean is Ars Technica’s IT and National Security Editor. A former Navy officer, systems administrator, and network systems integrator with 20 years of IT journalism experience, he lives and works in Baltimore, Maryland.







