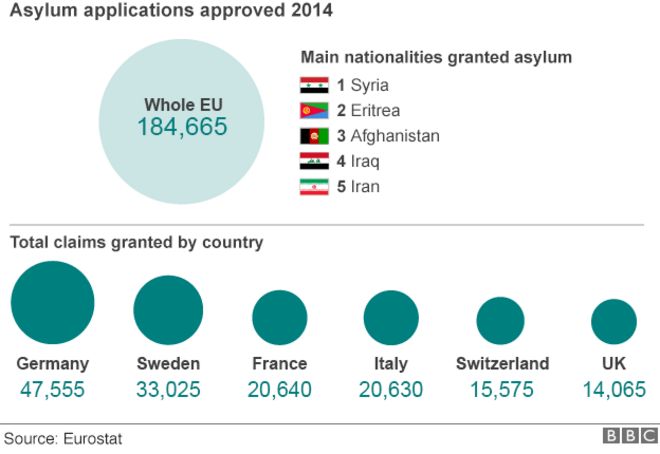
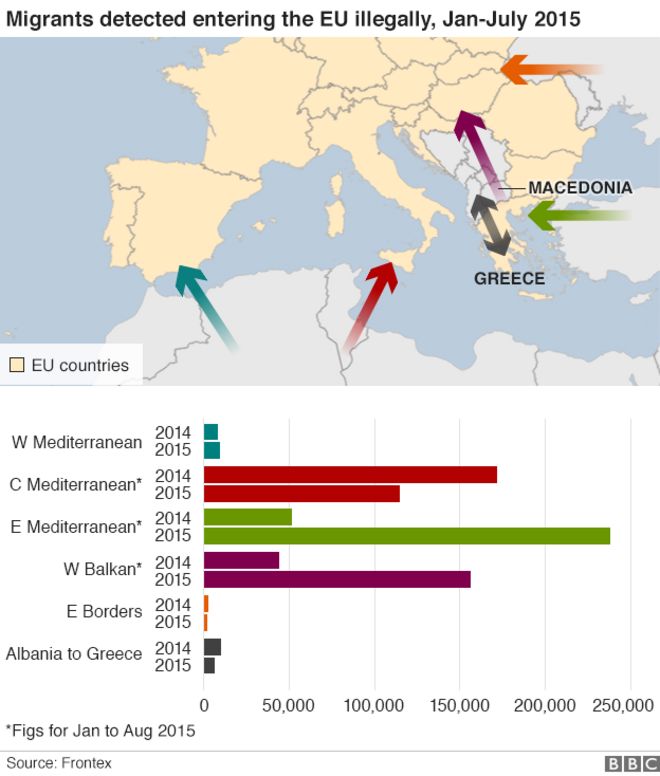
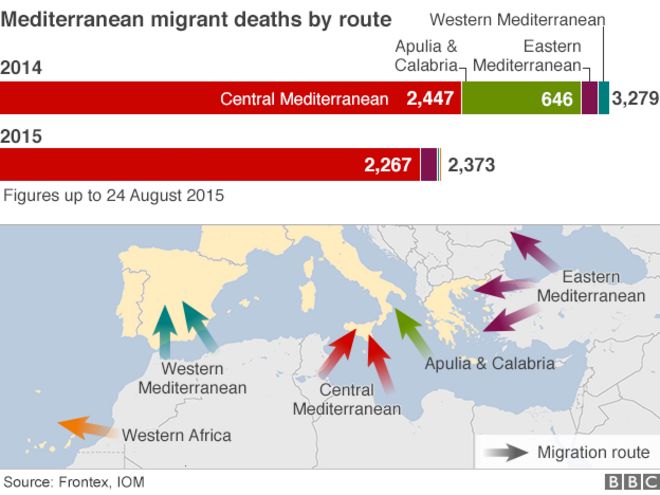
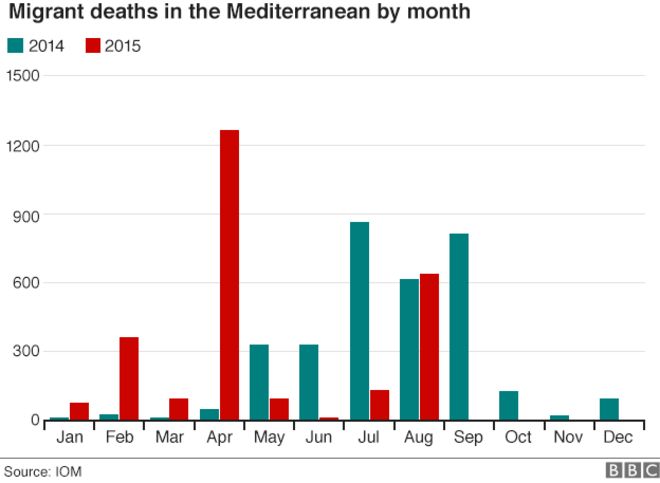
A new unit of the People’s Liberation Army was identified last week by cyber security researchers as Unit 78020 based in Kunming, in Yunnan Province.
The unit’s operations have been tracked for five years and have included targeted attacks on states in the region that are challenging Beijing’s strategic program of seeking to control the sea through building up small islands and reefs and then deploying military forces on them.
“Unit 78020 conducts cyber espionage against Southeast Asian military, diplomatic, and economic targets,” according to a security report on the unit that included a satellite photo of the unit’s Kunming compound.
“The targets include government entities in Cambodia, Indonesia, Laos, Malaysia, Myanmar, Nepal, the Philippines, Singapore, Thailand, and Vietnam as well as international bodies such as United Nations Development Program (UNDP) and the Association of Southeast Asian Nations (ASEAN).” More details here.
Chinese president Xi Jinping is supposed to have dinner this evening with U.S. president Barack Obama. Wonder if the name Ge Xing will come up?Ge Xing is the subject of a joint report published this morning by ThreatConnect and Defense Group Inc., computer and national security service providers respectively. Ge is alleged to be a member of the People’s Liberation Army unit 78020, a state-sponsored hacking team whose mission is to collect intelligence from political and military sources to advance China’s interests in the South China Sea, a key strategic and economic region in Asia with plenty of ties to the U.S.
The report connects PLA 78020 to the Naikon advanced persistent threat group, a state-sponsored outfit that has followed the APT playbook to the letter to infiltrate and steal sensitive data and intellectual property from military, diplomatic and enterprise targets in a number of Asian countries, as well as the United Nations Development Programme and the Association of Southeast Asian Nations (ASEAN).
Control over the South China Sea is a focal point for China; through this region flows trillions of dollars of commerce and China has not been shy about claiming its share of the territory. The report states that China uses its offensive hacking capabilities to gather intelligence on adversaries’ military and diplomatic intentions in the regions, and has leveraged the information to strengthen its position.“The South China Sea is seen as a key geopolitical area for China,” said Dan Alderman, deputy director of DGI. “With Naikon, we see their activity as a big element of a larger emphasis on the region and the Technical Reconnaissance Bureau fitting into a multisector effort to influence that region.”The report is just the latest chess piece hovering over Jinping’s U.S. visit this week, which began in earnest yesterday with a visit to Seattle and meetings with giant technology firms such as Microsoft, Apple and Google, among others.
Those companies want to tap into the growing Chinese technology market and the government there is using its leverage to get them to support stringent Internet controls imposed by the Chinese government. A letter sent to American technology companies this summer, a New York Times report last week, said that China would ask American firms to store Chinese user data in China. China also reportedly asked U.S.-built software and devices sold in China to be “secure and controllable,” which likely means the Chinese would want backdoor access to these products, or access to private encryption keys.Jinping, meanwhile, tried to distance himself from the fray when he said in a Wall Street Journal interview: “Cyber theft of commercial secrets and hacking attacks against government networks are both illegal; such acts are criminal offences and should be punished according to law and relevant international conventions.”Journal reporter Josh Chin connected with Ge Xing over the phone and Ge confirmed a number of the dots connected in the report before hanging up on the reporter and threatening to report him to the police.
While that never happened, the infrastructure connected to Ge and this slice of the Naikon APT group, was quickly shut down and taken offline. In May, researchers at Kaspersky Lab published a report on Naikon and documented five years of activity attributed to the APT group. It describes a high volume of geo-politically motivated attacks with a high rate of success infiltrating influential organizations in the region. The group uses advanced hacking tools, most of which were developed externally and include a full-featured backdoor and exploit builder.Like most APT groups, they craft tailored spear phishing messages to infiltrate organizations, in this case a Word or Office document carrying an exploit for CVE-2012-0158, a favorite target for APT groups. The vulnerability is a buffer overflow in the ActiveX controls of a Windows library, MSCOMCTL.OCX. The exploit installs a remote administration tool, or RAT, on the compromised machine that opens a backdoor through which stolen data is moved out and additional malware and instructions can be moved in.Chin’s article describes a similar attack initiated by Ge, who is portrayed not only as a soldier, but as an academic.
The researchers determined through a variety of avenues that Ge is an active member of the military, having published research as a member of the military, in addition to numerous postings to social media as an officer and via his access to secure locations believed to be headquarters to the PLA unit’s technical reconnaissance bureau.“Doing this kind of biopsy, if you will, of this threat through direct analysis of the technical and non-technical evidence allows us to paint a picture of the rest of this group’s activity,” said Rich Barger, CIO and cofounder of ThreatConnect. “We’ve had hundreds of hashes, hundreds of domains, and thousands of IPs [related to PLA unit 78020].
Only looking at this from a technical lens only gives you so much. When you bring in a regional, cultural and even language aspect to it, you can derive more context that gets folded over and over into the technical findings and continues to refine additional meaning that we can apply to the broader group itself.”The report also highlights a number of operational security mistakes Ge made to inadvertently give himself away, such as using the same handle within the group’s infrastructure, even embedding certain names in families of malware attributed to them. All of this combined with similar mistakes made across the command and control infrastructure and evidence pulled from posts on social media proved to be enough to tie Ge to the Naikon group and elite PLA unit that is making gains in the region.“If you look at where China is and how assertive they are in region, it might be a reflection of some of the gains and wins this group has made,” Barger said. “You don’t influence what they’re influencing in the region if you don’t have the intel support capabilities fueling that operational machine.”