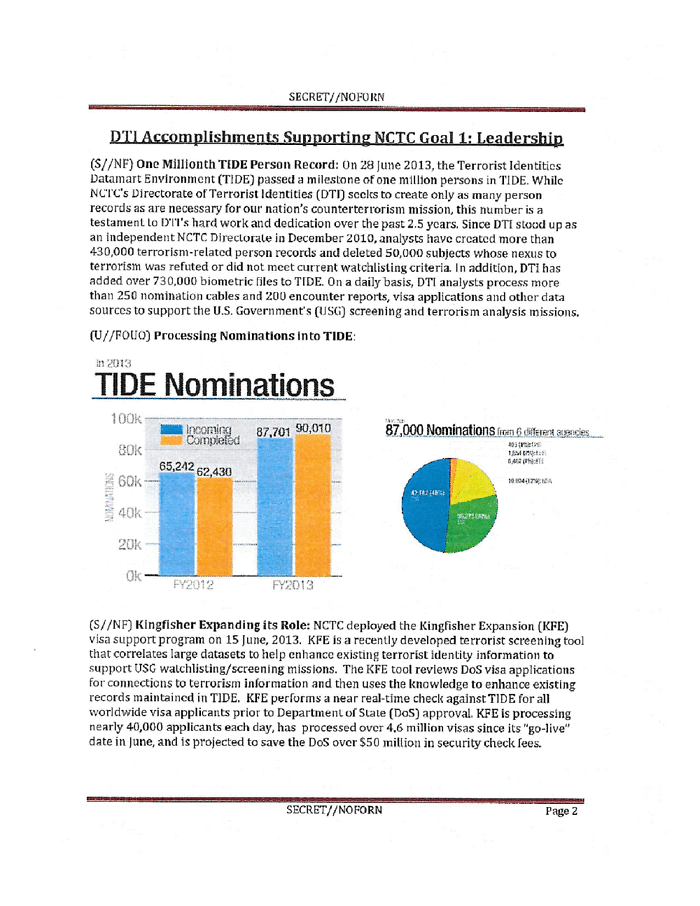
The Isis papers: a masterplan for consolidating power

Islamic State
Caliphate on the prophetic methodology
In the name of God, the compassionate, the merciful:
“No, by your Lord, they will not believe until they have you rule over them in what they have disagreed and find in themselves from what you have judged and willingly submit.”
Principles in the administration of the Islamic State – 1435AH [2103-2014]
Introduction
In the name of God, the compassionate, the merciful
As for what follows:
After 50 years of jihad whose sides have fallen prostrate in the totality of the land, and the states gathered against the centres of the Sunni jihad in the world, God ennobled his true soldiers whom he selected to establish the caliphate state whose fortresses had fallen at the hands of global Zionism in al-Astana [Istanbul] 100 years ago. [Note: This is a reference to the end of the Ottoman caliphate in 1924].
Indeed the establishment of the Islamic State, its concept does not stand on the basis of a mujahid soldier fighting and bearing his arms, nor does it rest on da’wa [evangelising] in a mosque or a street, but rather it is a comprehensive system requiring the leaders of the ummah [Muslim nation] to realise its concepts.
So on the expansion of the Islamic State, the state requires an Islamic system of life, a Qur’anic constitution and a system to implement it, and there must not be suppression of the role of qualifications, skills of expertise and the training of the current generation on administering the state.
From the start of the uprising of blessed Syria against the Nusayris [derogatory for Alawites], the mujahideen came in great numbers out of zeal for their religion. But some of them harboured Arab nationalist and tribalist arrogance, and others a zeal and will without shari’a aims.
But it was inevitable that there would be an organisation of these numbers and their principles as a shari’i [Islamically legitimate] organisation accepting the current reality that the world marshalled against it from its soldiers and intelligence services.
And from then there would be the confrontation of altering the principles and selling out to which the first mujahideen [fighters] did not show deference in Afghanistan, Iraq, Chechnya and elsewhere.
And from then there would be the cultivation of educational and societal change with which the muhajireen [immigrants] co-existed and organisation of their ranks with the ansar [natives] – the people of the land.
And there were many challenges and difficulties that one would have to deal with according to its establishment and according to its special ideological programme, and one must deal with each one of them on an individual basis.
Chapter one
Announcement of the Islamic Caliphate
The announcement of the renewal of the caliphate in Iraq in the year 1427AH [2006] was the arbiter between division and separation as well as the glory of the Muslims. That year was tantamount to the hemiplegia for the idolatrous west that began preparing equipment and projects to strike any project of the Islamic State, and the announcement of the caliphate.
And the announcement of the caliphate was the result of the mujahideen’s realising the lack of advantage in fighting against the idolaters without the existence of a leader and caliph who could gather the Muslims under his banner and be a figure of strength for them.
America and its allies were able to destroy the caliphate project [ie the Islamic State of Iraq] to a great extent in Iraq after they established the Sunni Iraqi Sahwa forces [Sunni Awakening tribal forces that fought the Islamic State of Iraq] and struck the Sunni nursemaid [ie basis of Sunni support for the Islamic State of Iraq], by portraying it as a treacherous terrorist state of hypocritical political projects, with great marshalling of the media to accomplish that. The deeds of the soldiers of the state thus became limited to security operations to strike American targets and their allies.
After the arising of the blessed uprising of Syria, the Islamic State had a great role in striking the Nusayris in it and destroying the pillars of the rule of Assad in the heart of the command centres.
And it has therefore been the case that the lesson to be learned from the prior leaders of the state is the way to benefit from prior mistakes, and the means to preserve the revolutionaries of Syria on the jihadi trend while not moulding them in a western framework which that western support brings.
And in the second chapter is a statement on the administration of the muhajir (foreign) mujahid in particular and developing the creed of the Islamic State among the ansar in Syria.
The announcement of the caliphate in Syria was a powerful blow that the agents of the west who were set on the direction of the Sahwat of Iraq by whom the west thought that it could put an end to the Islamic caliphate project as it had weakened it in Iraq did not expect.
There were new modified problems that the leadership of the state was able to deal with, among them [Abu Muhammad] al-Joulani, [Note: the leader of al-Qaida in Syria formerly of Islamic State] announcement of his rejection of joining the Islamic State despite his allegiance to the caliph in Iraq, and in that he was trying to split the ranks and sabotage the project in subordination to his personal agendas bound with regional states, and his rejection was a confrontation for the Islamic project that God gave victory to despite the multitude of those discouraged and the callers to humiliation and servitude.
And the one who witnesses the events of Syria sees how God has given might to the Islamic State and lowered Joulani and those with him.
Chapter two
Organisation of the individual and group
With the entry of the second year of the uprising of Syria, the Shia militias of various nationalities entered Syria to fight at the side of the Nusayri-Rafidite [Assad] regime which flaunted its crimes with regards to the Sunnis, which led to a global Islamic uprising represented in the hijra [migration] of thousands of Muslim youths to fight in the rank of the Sunnis from the various regions of the land.
Thousands migrated to Syria to fight alongside the mujahideen, without their knowing the direction of any faction, its affiliation or private agendas.
It was necessary to prepare a sound programme in which the muhajireen might take refuge as their jihad is the result of the glory to Islam and the monotheists.
So the announcement of the caliphate was the obligation that gathers those arriving in the land of jihad, strengthens their hearts – and through it their minds are set – and gathers them over the difference of their colours under one banner, one word and one caliph
The majority of the first muhajireen came from the Gulf states and the Arabic Maghreb whose zeal for their religion urged them on, and among them were those with zeal for their Arab Sunni brothers without religious jihadist inhibition, and without there being for them prior expertise in global jihadi organisations.
After them was hijra [migration] from the states of the world after the announcement of the caliphate, as no disbelieving state has remained which hasn’t also suffered from the hijra [migration] of its youth to support the Islamic State which the soldiers of Joulani and the apostate Sahwa forces from the Free [Syrian] Army and others besides them rejected.
And after that, Sheikh Abu Bakr al-Baghdadi ordered to establish a first camp which included the new muhajireen [immigrants] who had no deeply ingrained expertise and creed, near the prior borders for the Sykes-Picot “Iraq-Syria” lines.
And the camp included the organisation of the muhajir [immigrant] individual in the Islamic State and laying aside local tribalism and ignorance before him, and making his affiliation to the religion alone and under one banner.
And the camp included nurturing the spirit of the brothers between the muhajireen and the ansar through laying aside the prior identity for the muhajir, and making him a resident in the Islamic State with his family without feelings of estrangement or distinguishing between him and his brothers from the muhajireen and the ansar.
And without Islam it is not possible for this change to be included which encountered difficulty in the beginning on account of place affiliation that the mujahideen felt on the day of their fight with the Free Army Sahwa and inclinations of nationalism and ethnic division which was making the muhajir lose his zeal to fight alongside them.
And there resulted from the camp the formation of joint fighting groups between the muhajireen and the ansar established on the basis of the leadership of the individual most capable of bearing responsibility, having prior expertise and the military and sharia [law] tests of the camp.
And there also resulted from the camp the formation of groups composed of the muhajireen from the western states in particular in view of the difficulty of linguistic communication in the beginning and launch stage and in view of the mutual understanding and precedence of coordination between some of the muhajireen from Chechnya and France to fight in single cells without the existence of any distinction for members from those besides them [ie there was no differential treatment on the basis of ethnic identity].
And it was inevitable that Arabic character should precede over the character of the muhajireen, for the language of the Qur’an is Arabic, and the prophetic hadiths [sayings] are in Arabic and the customs of Islamic society were Arabic in great part, and in view of the nature of the local society of the peoples of Syria it was inevitable that Arabic character should be cultivated in the language and religious culture in the muhajireen and laying aside the foreign identity that bears in its hidden nature hostility to Islam, its culture and its roots.
For unifying the life of the mujahid and his language and culture is the guarantor for unifying the rank of the mujahideen and realising their total belonging in the Islamic State that includes muhajireen from every corner of the earth.
Chapter three
Administration of the camps
The preparatory camp is the first home and school of the mujahid in which his military and jihadi training sessions take place and he undergoes sufficient education in matters of his religion, life and jihad.
And according to the plans of the Islamic State to nurture the caliphate generation, the camps are divided into three types:
1. Continuation camps
And these are special camps for the mujahideen who lead in the jihad and those who are masters of expertise in managing and planning the battle in beginning and end. And the camp includes physical preparation for 15 days. And that is in a training session every year, and the mujahid through that camp comes upon the latest arts of using weapons, military planning and military technologies currently put forth in battles and weapons whose use by the enemy are anticipated, along with detailed commentary on the technologies of enemy use of the weapons, areas of their use, their strength and how the soldiers of the state can take advantage of them.
2. First preparation camps
For the mujahid on the day he joins the Islamic State, whether as a muhajir or from the ansar: and the camp includes sharia sessions through which the mujahid studies the fiqh [jurisprudence] of the rulings, Islamic doctrine, al-wala’ and al-bara’ [loyalty and disavowal], in addition to the arts of fighting and the arts of using weapons, with screening of every mujahid in a specialty in which he excels and completing his camp according to his skill in specific weapons.
3. Preparation camp for children
The camp includes sharia sessions in fiqh of doctrine and rulings, with special sessions in Islamic society and manners, and training on bearing light arms and the principles of use.
Outstanding individuals are selected from them for security portfolio assignments, including checkpoints, patrols and the various Amniyat units [internal security units].
And the camps administration is responsible for planning, aims and results, and as the results of the camp should be in alignment with the aims and principles of the Islamic State, it has been necessary to establish a centre for the administration of the camps whose tasks are as follows:
1. Preparing special sharia sessions in the camps in coordination with the al-Buhuth and al-Eftaa [fatwa – legal opinion] committee.
2. Preparing educational programmes to teach the Arabic language and recitation of the Qur’an in coordination with the Diwan al-Ta’aleem [department of education] for every province.
3. Preparing military programmes teaching the types of weapons and military tactics with the supervision of the military commander in every province.
4. Studying expenditures and allowances for every camp whose study and analysis are to be completed by the military leader or wali [governor] of every area according to the needs connected with every wilaya [province] and submitting the study to the wali.
5. Overseeing the selection of the educational and training staff in the camp.
6. Putting in place detailed planning and programmes on the course of the battle.
7. Tracking the supervision of the camp according to the defined programmes.
8. Assessing the camp session and raising a report to the officials concerning the readiness of the session after the camp.
Chapter four
Direction administration
The mujahid [soldier] remains in need of direction and tracking after his completion of the special training session for him, for spiritual direction is the foundation of his success in every matter he undertakes and the mujahid’s direction in every stage will consist of reminding him of the aims of the Islamic State and hadiths [prophetic sayings] on the virtue of the mujahid and persevering and continuing despite the difficulty of the path of jihad.
1. Direction before the battle
And here the military commander for the mission or the sharia official accompanying him should undertake it, and the direction should be a little before the launching of the mujahid to battle through mentioning hadiths on the virtue of jihad and endurance on encountering the enemy as well as following the decisions and instructions of the field commander during the battle, along with the virtue of martyrdom in the path of God to raise the banner of Islam and the caliphate and the virtue of the one struck with wounds in the land of the battle. All this should be done during the readying and preparation for the battle. And the director oversees the mujahideen in all their moments until their absence from him in the battle.
And the director should not be discouraged, having doubts, hesitating or cowardly because he is the example that the mujahid summons whenever the furnace of the battle flares up.
2. Direction after the battle:
In the event of victory, the director summons what came from the Prophet from sayings on the virtue of the mujahid and their feelings that what they have accomplished aspires to be in the service of their religion and creed, with their being reminded to embrace the instructions coming from the battle leadership from the rulings of spoils and not adopting any decision to plunder the wealth of the people except by its rights and by explicit order from the commander responsible.
In the event of being broken, the direction should be on patience, reckoning and steadfastness on meeting the enemy while not heeding those having doubts and those who spread rumour and terror in the ranks of the soldiers.
3. Lasting direction:
Remaining on activity and steadfastness with the mujahid in all his states and lessons in al-wala and al-bara [loyalty and disavowal] as well as fiqh, Islamic creed and listening to and obeying the amir [leader].
The staff of direction in every province should be from the cream of the crop of free sharia and military officials who have the ability to argue, convince and encourage as well as from the soldiers around whom the group have congregated and should be possessors of confidence among them.
Chapter five
Organisation of the provinces
The Sykes-Picot agreement and after them the indirect rule of the west over the states of Islam tried to place administrative borders drawing social, madhhabist and ethnic differences in every region, and deepening the roots of the differences between the Sunni Muslims.
Thus the distinction of the Sunnis from the Shia in the provinces of Iraq and oversight of the centres of administration in every Sunni region, and even the appointment of officials in the Sunnis’ regions from the filth of the Rafidites have been clear, while the regions have been entrusted under the rule of [their own] Kurdish and Shia sects independent in decision-making from the ruling presidency as we have seen in Kirkuk and Irbil and in even smaller regions including from them in the cursed Najaf and Karbala and that have enjoyed “religious” administrative independence, unannounced.
All those divisions have also forbidden the Sunnis from the simplest of their rights while making the Nusayris masters of the sea, and the Shia in Iraq the kings of oil and the merchant pathways, and the Yazidi Kurds the sheikhs of the mountains while the Druze have become masters over the mountains overseeing Israel.
All that has not merely been a coincidence, but it was a dirty political decision in order to implement a tightening stranglehold on the Sunnis and make them the most remote people and strip them of all assets for advancement or thinking of a rightly-guided Islamic State.
If we were to see today the borders of the Islamic State and the borders of the Sunnis regions, we would see them torn apart, besieged and persecuted, for there are the Shia from the south of Iraq, the Nusayris from the west of Syria and the communist Kurdish parties to their north, and the Druze to their south.
So it is no surprise that today we see the bloodshed flowing in the land of Syria and Iraq.
So it has been from the law and sound mind to redraw the borders of the provinces and give lengthy consideration to every development that occurs in the region. Thus we protect the power of the Sunnis and strengthen its expansion and focal points, and then special teams can be deployed for fundamental change in the structuring of the regions that are subject to the rule of the Islamic State.
And that was what the companions [of the Prophet Muhammad] and after them the caliphs pursued against every heretic community: that is, dispersing their groupings so there no longer remained any impeding opinion, strength or ability, and the Muslim alone remains the master of the state and decision-making and no one is in conflict with him.
And in what there is no doubt is the fact that among the assets of the ummah [Islamic nation] are: its wealth, the nature of its land, its inhabitants and its water. And in everything is distinction:
1. Wealth of the state
It is the principal component and source of financing for all internal and external operations, and the existence of secure financial resources whose value does not change in every time and place is a must – and the need of the people for them should be clear with the nations unable to do without them despite the existence of the impediments that prevent their use and purchase from the land of the state.
This includes oil and gas and what the land possesses including gold as currency that does not deteriorate or decline, as well as trade routes from which they have no wealth and all of it should be the intervention of the Islamic State as a powerful side in all their plans and such that they cannot pretend that it has no existence and might.
2. The nature of its land
The state cannot remain without the existence of the land that allows for its continuation and expansion, for the assets of the land are – the mountains, the agricultural lands, the sea and the river – for these natural assets are what makes the Islamic State acquire its importance and the importance of location, and the agreement of the west in Sykes-Picot were established on the basis of depriving the Sunnis from those assets, as the mountains were granted to the Kurds, Druze and Alawites, while the sea was granted to the Rafidites and Nusayris, while the river and what surrounds it in investment for the Jews and the agricultural lands under their administration.
And that was a new setback that was added to all the ambitions in establishing the Islamic State and freeing it from servitude of the filthy Nusayris and the disbelieving Rafidites [Alawites and Shia]. When there is no asset for them the enemy have been shut on their openings from every side.
3. The traitorous governments have tried to mislead the Sunni peoples in every Arab land, as corrupt programmes were introduced for them and there spread among them the love of vice, bonds, bribery, usury and abandoning worship and forgetting the rulings of jihad. So the Sunnis in Syria have lived in a new ignorance after ignorance during the French occupation of their land as there was the Alawite government that planted its vices in every house, permitted the forbidden and made forbidden development and civilisation.
But after the uprising undertaken by the Sunnis in Iraq and Syria and their getting rid of the servitude to the tyrants began the second plan that requires implementing the “demographic” change in their regions and expelling the Sunnis from their areas, for it has been what we saw in Fallujah, Aleppo, Homs, Tikrit and other areas besides them from the regions of the Sunnis many of whose people have suffered during their presence in their land.
Indeed they realise that the Islamic State cannot renew the ummah’s blood without a human member capable of always producing, and there was the alluring of the best of its youth and plundering the land with hijra outside their areas and liquidating many of them.
And today it is necessary to have a studied plan that responds in kind and brings about like change in the profane abode of disbelief, expelling its people and killing its people until there is no base for them and the land is for God and his servants.
And in turn implementing the plans that include the return of the Muslim youth to their land and bringing together the skills from the land of the Muslims, and the going out of the state for specialised staff in their fields if they are not of those of the pact in Islam [ie Jews and Christians].
Chapter six
Administration of wealth
Indeed the might of the Islamic State can only be through its being free entirely from all bonds of tyranny that the west possesses as means of leverage against it, and it moves them according to its need and whim based on knowing from it the need of the mujahideen for support, wealth and weapons.
Jihadi groups in Iraq and Syria have lived through long bonds of humiliation pledged on conditional western support, until they seized wide areas of the land and possessed all assets of advancement.
And all of that is on account of the ignorant administration that controls them and keeps them under western guardianship for all their activities, wars and expansion.
Indeed the Islamic State’s seizure of vast areas includes all assets of advancement that does not suffice without the existence of an administration managing the interests and managing the crises. So it is necessary for a plan to be put in place including the might of the state and its independence as we specify in the following points:
– Preserving the capabilities [personnel and infrastructure] that managed the production projects under the prior governments, whilst taking into account the need to place strict oversights and an administration affiliated with the Islamic State.
– Placing specialists in accounting and oversight over all production directorates in the Islamic State including establishments of oil, gas, archaeological areas and factories for manufacturing and production.
– Preserving additional reserves that ensure the continuation of operation in one successive arrangement in all circumstances.
– Regulating expenses through a comprehensive administration including collective expenses and collective production without singling out a province or group by provision of estimates exceeding their needs in normal circumstances.
– Establishing factories for local military and food production and independence from the monopoly of arms dealers for materials of necessity and cutting them off in the event of contravening the interests.
– Realising local needs and providing for them within the borders of the state in isolated safe zones and connecting trade routes inside the state through principal centres and beneficiary wings.
– Reducing excess expenditure through the administration of the province; it must operate independently and be able to take its own decisions in matters concerning the province.
– Relying on external business as a principal source of income through the openings of the state to the other side without an intermediary. Direct exchange has better guarantees than the monopoly of the intermediary for business transactions and means of connection.
Chapter seven
Administration of the projects
In parallel with military preparation in the lines of fighting and the camps, a committee is to be put in place to administer production projects and put in place plans to implement new investment projects.
The one who invests in the lands of the state is to be given comprehensive protection according to the agreement that arises with the observance of the interests of the Islamic State in production, exporting and prices.
The independence of the investor from the administration of the province is a more preferred means for the administration of the wealth, increasing local production and improving the capability of the producing material, and regulating the time and expenditure. And it will [also] be a better guarantee against losses resulting from any sizeable investment project.
For the independent foundation is outside the limits of liability that arise for those projects that are affiliated with a province of the Islamic State.
And it is not right for the investor according to the law, to hand over the production to those who have no right to it and they [those who have the right to it] are the ones determined in an agreement by the administration that is entrusted over the project and overseeing its organisation by the province in which the project is established.
And such an agreement is stipulated on determining the beneficiaries and the means of profit with the guarantee of the [Islamic] State to convey the products internally to the borders of the Islamic State without exposing them to any risk.
And it is not allowed to invest in the following projects:
1. Oil products
It is not allowed for a person who has no pledge of allegiance on his neck to the caliph to invest in an oil or gas field or what has arisen from their trajectory, but it is allowed besides that to produce derivatives after buying the crude products from the fields of the Islamic State, just as it is allowed to sell and deal in them inside and outside the state.
2. Gold and antiquities
It is not allowed to excavate for gold and antiquities except by expressed agreement from the resources department, and all transferred and stored materials will be confiscated for the interest of the treasury.
And it is allowed to deal in gold not excavated from the ground according to the well-known aharia frameworks with immediate effect.
3. Weapons
It is forbidden to establish factories to produce weapons and materials particular to them without granting of any explicit permits for the situation, just as it is forbidden to establish shops to sell public weapons besides personal weapons and deal in them without prior knowledge and agreement from the responsible military amir in the wilaya.
As for the other principal goods that also come under the crux of people’s lives, the officials must know about all means of operation and production like dealing in water, flour and livestock.
Chapter eight
Administration of education
Education is the foundation upon which Islamic society is built, and it is the division that makes the Muslims differ in their lives from the rest of the paths of disbelief.
The previous Ba’athist and Shia governments tried to deviate the Muslim generation from their path through their educational programmes that concord with their governments and political whims.
The programmes focused on glorifying the ruling authorities and discarding differences between sects, stripping Sunnis of their identity.
And among the most important of their goals were:
1. Focusing on glorifying and eternalising the leaders and taking refuge in God and inserting them into hidden shirk [idolatry] through immortalising ephemeral, temporary personalities.
2. Spreading the aims of their parties and their ideas whilst distancing the nurtured from Islamic thought, because the ruling party considers itself the pulse of society and the symbol of its endurance, while Islamic principles are for the mosque only and between man and his Lord with severe proceedings against all those who tried to do away with party thinking or modify it.
3. Discarding the difference with the disbelieving sects, and considering co-existence with them as the true societal bond that the ummah must operate in accordance with in order to preserve its goals, while in reality protection is implemented for the rights of all the communities of disbelief while oppressing the Sunnis and their principles.
4. Spreading the culture of moral dissolution by promoting it through expressions of civilisation and exchanges of cultures with the west.
And thus it was that the ummah entered into labyrinths of confusion that made it forget its glory, its strength and its past, while the prior Islamic caliphates were portrayed as being a foreign occupation that arose on the basis of ignorance and the decline of the ummah and nationalism.
– And among the aims of the Islamic programme in the Islamic State:
1. Implanting Islamic values in society as well as sound, sharia-based societal manners and customs.
2. Correcting the erroneous narrations that the prior programmes had implanted about the prior caliphs and imams.
3. Developing Islamic society on the basis of manners and on sharia.
4. Raising a knowledgeable Islamic generation capable of bearing the ummah and its future without needing the expertises of the west.
So it is also that the Islamic school is one of the houses of worship, whose aims are confined to acquiring knowledge also, but also it is an educational nurturing ground that raises the individual with comprehensive development of mind and body.
And in it there should be training facilities for mind, body and vocation, as successful programmes cannot rely on what is written between the lines, without practical training on all given subjects.
Also it is the case that the interest in the Arabic language and its use in daily life for the individual is an important matter in the Islamic State as is distancing from vulgar expressions that were put forward in society in a well-considered plan to guarantee the forgetting of the Islamic identity for society.
Chapter nine
Administration of relations
External relations are the first foundation for building every nascent state, and they are among the foundations that show the strength and might of the state. They should constitute for it a general stance in everything that happens in the world with the people of Islam and be for it an external hand protecting its dealings.
And the Prophet (peace be upon him) was considered the master of the global Islamic message; it was necessary for him to be acquainted with what was happening around him in the neighbouring states, and knowing their latest affairs and thus inviting them to Islam. And indeed the messenger (God’s peace and blessings be upon him and his family) established his proficiency and skill in external movements through viewing at a distance and personifying the just of the just, and appropriate evaluation of matters as well as outstanding ability in the operation of recruiting to Islam.
Indeed external relations are key to knowing the international politics surrounding the Islamic State, and alliances should be as a guarantee of force and leverage that the Islamic leadership can use in all its matters with the external world.
According to sharia politics, the leadership is not allowed to adopt decisions to ally with a state or implement an agreement with it if that violates sharia politics, as agreed on by the majority of ulama [religious scholars] and symbols of jihad. So indeed every agreement must include the following:
1. The internal sovereignty of the Islamic State and not allowing for other states to intervene in matters of Islamic rule or the general politics of the Islamic State.
2. Protecting the borders of the Islamic State from every mushrik [idolater], disbeliever, aggressor and even friend, for no army or other force is allowed to enter the borders of the Islamic State whatever the pretext.
3. A provision that the [Islamic] State should be witness to good treatment of Muslims in its lands and mutual affection with Muslims in other areas of the world, and that it is not allowed to deal with another state that has a history of hostility to Islam’s spread, the building of mosques and oppression of Muslims in its lands.
4. A provision that the agreement should first be in the interest of the Muslims, not in the interest of the disbelievers.
5. That the agreement should not include any future provisions touching on the freedom and sovereignty of the Muslim state, and no bonds of debt or conditions of harmful exploitation even if in the future with regards to the matters of the state.
6. That there should be for the Muslims their rights and freedoms within the state that is to enter into an agreement with us.
7. That all points of the agreement should be clear to the imam [the caliph] and those with him.
And in the event of the nullification of any one of the conditions or lack of their provision, it is not allowed for the imam to enter the ummah and the Muslims into dubious bonds that oppress the ummah and the fate of its development.
Chapter ten
Administration of media
Indeed everything that I have previously mentioned constitutes practical steps on the ground and [so] there must be a principal means to promote them that should be comprehensive. All of its ideas and activities should be advertised in the interest of the aforementioned practical steps. That will not be realised without media foundations that are branched out and comprehensive in operation within one administration and background.
So there should be one media foundation branched out within multiple pockets according to the following outline:
1. The Base Foundation:
To be directly affiliated with the Diwan al-Khilafa [office of the caliph] or Majlis al-Shura [advisory council] of whoever so represents them, and the official for it should be connected by his relations with the military commander, [chief] security official and the caliph himself. The office will put implement the main media principles and tasks and it should be supervising the distribution of the media offices in the provinces and the media foundations that take a name and are independent from the administration of the provinces [ie so-called auxiliary agencies and foundations mentioned below].
And the Base Foundation defines the priorities of publication and broadcasting as well as the media campaigns, just as it directly supervises through a committee the activities of the offices and undertakes inspection campaigns in the provinces and activist places.
The foundation also sets the preparation of media staff, their expenses and requirements and receives monthly reports on the activities of every office.
2. The provincial media
And in every province there should be a media office affiliated with the governor himself and in coordination with the military and security official in its region, and its director should be in direct contact with the media official in the Base Foundation.
And among the offices’ tasks are covering the military operations and their results, with issues concluding the end of every great military operation or distinguished operations for the soldiers of the state, as well as services’ facilities, implementing sharia rulings and the course of life in the province.
Also the office should be interested in implementing tasks of printing and distribution or supervising them within the province.
3. Auxiliary agencies and foundations:
It is suggested that production foundations or auxiliary agencies are established according to the mother office’s needs and interests.
The auxiliary office specialises in tracking military and services coverage in a province or number of provinces without there being in the name of the foundation or its symbol something to directly link it with the Islamic State.
The auxiliary foundations are not to be allowed to cover security operations or implementations of [judicial] rulings.
These are general suggestions placed for you by the poor slave of God, the servant of the Islamic State, in order to be a lighthouse by which there is guidance, as well as general and prompt systems of organisation.
And the administrative cadres will receive training sessions on operating according to the following programme.
Abu Abdullah al-Masri.

 The
The