Much has been written about Trump’s now former National Security Counsel advisor H.R. McMaster who at one time was General Petraeus’ ‘go-to’ tank operations expert in Iraq. The 3-star general from the outset never really gelled in a cohesive policy relationship with President Trump and the chatter for months in DC was that his time at the White House was going to be short.
Question is who recommended McMaster to Trump in the first place and who did the background investigation such that Trump accepted and confirmed him to lead the National Security Council?
- Outgoing National Security Advisor H.R. McMaster worked for a foreign-based think tank for 11 years before assuming his post
- The think tank has ties to Russia, China, the Uranium One deal and Bahrain
- Career armed forces officers spoke out against the arrangement
Outgoing National Security Advisor Lt. Gen. H.R. McMaster served for more than a decade as a consultant to the London-based International Institute for Strategic Studies, a foreign-based think-tank that has received funding from hostile foreign governments to include Russia and China, according to a Daily Caller News Foundation investigation.
The career soldier ended his employment at the International Institute for Strategic Studies (IISS) in February 2017 after President Donald Trump tapped him to serve as his national security adviser following the resignation of former National Security Adviser Michael Flynn.
McMaster is planning to leave the NSC in April, to be replaced by former U.N. Ambassador John Bolton, according to The Wall Street Journal.
The outgoing NSC official said in a statement, he was “requesting retirement from the U.S. Army effective this summer after which I will leave public service.”
The general, who did not leave the Army to assume his NSC post, was one of only two White House national security chiefs who retained active duty status while working at the White House. The other general was Gen. Colin Powell.
McMaster never publicized his decade-long outside consultant work with the foreign-based think tank that often supported a globalist agenda opposed by Trump. IISS often espoused foreign and military policies that served as the centerpiece of the Obama presidency, including support for the former president’s Iran nuclear deal.
While his 11 years at the institute were never part of his official military biography, former military officers who learned of it were harshly critical of his unusual moonlighting.
Veteran military officers expressed disbelief at McMaster’s consulting work at a foreign-based think tank that receives funding from hostile governments. They called the arrangement “unethical” and “unprecedented.”
IISS operates offices in the Bahrain, Singapore and Washington, D.C. It generally reflects a globalist “realist” Eurocentric view of foreign and military postures that’s at odds with Trump’s foreign policy. The think-tank was a major advocate of former President Barack Obama’s nuclear deal with Iran.
IISS receives funding from friendly Western sources such as aerospace firms and even the British army, but is also has received funding from the Russian Federation, China’s Ministry of Foreign Affairs, as well as the governments of Azerbaijan, Turkey, Qatar, Pakistan, Saudi Arabia and Bahrain, according to the IISS website.
During McMaster’s time at IISS, the think tank also received $700,000 from George Soros’s Open Society and $140,000 from Ploughshares, the pacifist organization that aggressively pushed for Obama’s Iran nuclear deal.
The organization’s council — its board of directors — also is filled with people who have ties to the Kremlin, to the Qatari emir who has been accused of supporting terrorists, to people associated with the Uranium One scandal, and with a Russian investment bank that paid former President Bill Clinton $500,000 for a single speech.
“This is bizarre,” retired Army Lt. Gen. William “Jerry” Boykin said in an interview with TheDCNF. “If that kind of information was available to The Trump administration before they selected him, the question is: Would they have selected him for this very job?”
The Army told TheDCNF that from 2006 when he first joined IISS as a “senior research associate” until he left in 2017, he did file annual financial disclosure forms notifying the Army of payments he received from the institute.
McMaster’s office did not respond to a DCNF request for his current financial disclosure form, which he was required to submit in 2017 as a White House employee.
Retired Rear Adm. James “Ace” Lyons, who served 35 years in the Navy, including a stint as commander of the Pacific Fleet, told TheDCNF McMaster’s consulting role at the think tank was “absurd.”
“It is really absurd that an active duty military officer, particularly one of flag rank, is a consultant to a foreign organization that is taking money and contributions from questionable countries that are known enemies of the United States,” Lyons told TheDCNF in an interview. “This to me seems to be outside the bounds of what we’re committed to. This is atrocious.”
“I’ve never seen this kind of thing before,” said Boykin, a 36-year veteran who served as under secretary for defense intelligence for President George W. Bush.
Boykin said he was convinced any commanding officer would have rejected McMaster’s proposed consulting work at IISS. “I cannot believe that the ethics people of the U.S. Army would approve of him doing that, and I can’t believe that any responsible person he worked for in the Army would have agreed to that.”
William J. Sharp, a public affairs civilian attached to U.S. Army Headquarters, told TheDCNF the Army accepted McMaster’s proposed consulting work at IISS without any prior approval because they regarded the think tank as not falling under the category of a “prohibited source.”
The term “prohibited source” relates to a company that seeks a business or other formal contractual relationship from the Department of Defense. Using that limited standard, the Army concluded IISS was not a prohibited source and McMaster did not need to obtain prior approval from military superiors.
“IISS is not a prohibited source for Army personnel,” Sharp told TheDCNF in an email. “Therefore, LTG McMaster was not required to obtain approval prior to consulting for IISS.”
“I’m surprised at this,” Boykin said. “I find this in my view and in my experience of 36 years to be unprecedented, and I would love to see an authorization. And if it’s an open-ended authorization — if there’s one at all — then I would be willing to bet you it was an error on the part of whoever provided that authorization. You just can’t do this on your own,” he told TheDCNF.
Retired Special Forces Col. James Williamson told TheDCNF he considered it “very unusual” for an active duty officer to serve for a decade at any educational institution. “It’s very unusual for a general officer on active duty to have that type of affiliation over that timespan,” he said. “I’ve had friends that have gone to Harvard or the Fletcher School at Tufts, but they’re U.S.-based.” He said most terms were for a short duration — usually six months to a year.
In fact, the military approves and even encourages active duty officers to seek temporary assignments with American educational institutions and think tanks. But those assignments are very short and rarely extend for more than a year.
Williamson said active duty military officers have plenty of private sector and think tank opportunities after they leave military service. “We have other people who served in London, but they’re not on active duty. They’re retired officers and there’s no problem with that,” he said.
Williamson, a counter terrorism specialist who served with NATO and U.S. Southern Command, said he regarded McMaster’s work as posing a basic “conflict of interest” in light of funding from hostile governments. That funding “would almost make it a de facto conflict of interest in my eyes.”
Retired U.S. Air Force Col. James Waurishuk, who also worked at the NSC, agreed. “I would be concerned about the work he’s doing and how it applies in relation to a think-tank that’s taking money from perhaps adversarial foreign governments. That would be of concern to me,” he said.
Williamson also shared the same view and added that even working at a London think tank poses problems. “Even our closest allies don’t have the same agendas and priorities that we do,” he said.
During his 11 years with IISS, the group promoted McMaster’s activities. A review of previous IISS websites by TheDCNF shows he was highlighted between six and 10 times each year.
IISS praised McMaster when he joined the Trump White House. Jonathan Stevenson, an Obama NSC official who also is a senior fellow at IISS, wrote a fawning opinion piece about McMaster in The New York Times. He called him a “compelling choice: a scholar-warrior” and “both a proven cavalry officer and a formidable defense intellectual.” Stevenson wrote McMaster could save Trump, and the general’s appointment, “should augur at least a fleeting period of stability at the dysfunctional National Security Council.”
Igor Yurgen has been on the IISS Council since 2010. He is chairman of Rennaissance Capital Group, which awarded Bill Clinton $500,00 in speaking fees.
Russia Today, a pro-Kremlin news organization, once described Yurgen as “one of Russia’s most influential experts close to [former] President Dmitry Medvedev.”
“He is remarkably skilled at combining public, business and political careers,” according to RT.
Another council member is Michael Rich, an executive vice president of the RAND Corp. But significantly, he is co-chair of the board of overseers of a project called the RAND Qatar Policy Institute.
The Qatar Policy Institute is also part of the Qatar Foundation, started by Qatar’s former emir, Sheikh Hamad Bin Khalifa Al Thani, and his wife, Sheikha Moza bint Nasser.
Saudi Arabia and the Persian Gulf states accuse Qatar of supporting Islamic terrorism. Al Thani has supported the Taliban in Afghanistan, Hamas in the Gaza Strip, militias in Libya, and the Muslim Brotherhood, The New York Times reported in 2014. The Emir personally traveled in 2012 to the Gaza Strip, where he received a hero’s welcome as he pledged to work with the terrorist group Hamas. Al Thani also founded Al Jazeera, the pro-Muslim Brotherhood television news channel.
Badr Jafar, another current council member, is the son of Hamid Jafar, who founded the biggest private equity firm in the Middle East, North Africa and South Asia. Badr is the CEO of Crescent Enterprises who, with his father Hamid Jafar, engineered an oil exploration partnership between their Emirates-based company, Crescent Petroleum with the Boris Kovalchuk, CEO of the Russian company of Inter Rao UES.
News agencies in the United Arab Emirates hailed the 2010 financial deal between Crescent and Moscow. “Russian state news agencies began their coverage of the recent high-level meeting in Moscow between Crescent officials, the Russian prime minister, Vladimir Putin, and the Iraqi former prime minister Dr Ayad Allawi by linking the names of Hamid Jafar and Mr Putin,” according to the National Business report.
Russian President Vladimir Putin decreed that all shares of Inter Rao UES be transferred to the Russian state-owned atomic energy agency called Rosatom. Kovalchuk is a Kremlin confidant who served as a vice president of Rosatom. Americans know about Rosatom because of its purchase of Uranium One, which was made possible by then Secretary of State Hillary Clinton’s support for the Russian acquisition.
While McMaster was a consultant at IISS the organization was a strong, unwavering supporter of President Obama’s nuclear deal with Iran.
Mark Fitzpatrick, its director for non-proliferation and disarmament was the most outspoken IISS director for the nuclear deal calling it in 2015 a “a potential game changer in many ways, opening a path to better relations with Iran that has been closed for more than 35 years.” Fitzpatrick said the deal “makes it demonstrably less likely Iran will become nuclear-armed now and in the future.”
IISS also entered domestic American politics by defending the Democratic Party during the 2016 presidential campaign. It flatly stated following the release of emails from the Democratic National Committee it “revealed no evidence of significant wrongdoing within the Democratic Party.”
IISS also has been criticized for the secrecy of its activities and its routine denial of visas for reporters seeking to attend its overseas events, particularly its annual event in Bahrain where human right groups accuse the government of silencing critics and keeping journalists away.
BahrainWatch, a human rights group published an investigation in December 2016 claiming that even well known American journalists have been barred from its Bahrain conferences called the “Manama Dialogue.”
“New York Times journalist Nicholas Kristof has openly called for an invitation since 2011, though his media visa was once again rejected last year. Wall Street Journal journalist Yaroslav Trofimov was also denied a visa.
Waurishuk concluded that McMaster’s relationship with IISS raises too many alarms.
“There’s too many red flags that kind of go up,” he said.
Neither IISS Washington nor IISS London returned repeated queries about McMaster.



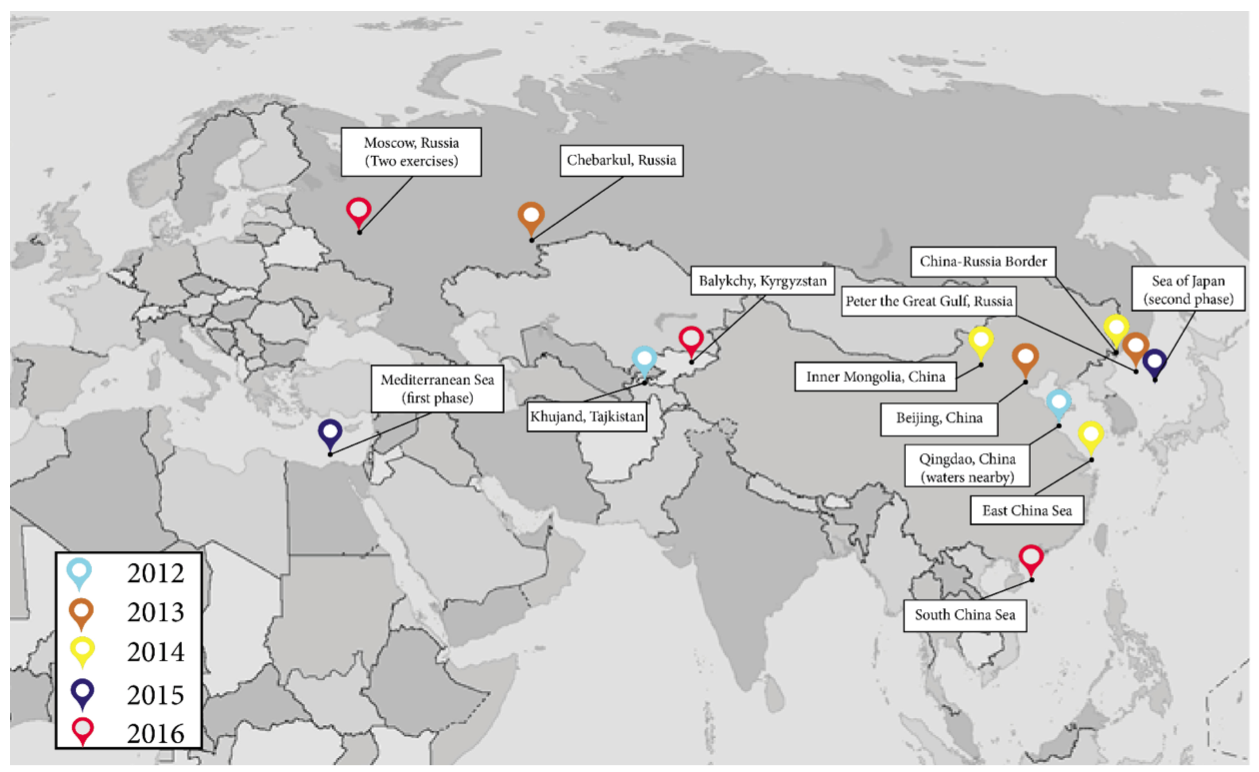 Before Russia and China began their recent series of bilateral exercises, the key tie between Moscow and Beijing was arms sales and military technology cooperation — totaling about $26 billion from 1992 to 2006 — according to estimates cited in the report.
Before Russia and China began their recent series of bilateral exercises, the key tie between Moscow and Beijing was arms sales and military technology cooperation — totaling about $26 billion from 1992 to 2006 — according to estimates cited in the report.

/arc-anglerfish-arc2-prod-mco.s3.amazonaws.com/public/UFFFHH5KSJAQJCIMYLQG5GYC2I.jpg)
%2Farc-anglerfish-arc2-prod-mco.s3.amazonaws.com%2Fpublic%2FPZC237S56BFODEX3RNDZOIOAEM.jpg&f=1)