WASHINGTON (AP) — Federal authorities expressed increased alarm Thursday about an intrusion into U.S. and other computer systems around the globe that officials suspect was carried out by Russian hackers. The nation’s cybersecurity agency warned of a “grave” risk to government and private networks.
The Cybersecurity and Infrastructure Security Agency said in its most detailed comments yet that the intrusion had compromised federal agencies as well as “critical infrastructure” in a sophisticated attack that was hard to detect and will be difficult to undo.
CISA did not say which agencies or infrastructure had been breached or what information taken in an attack that it previously said appeared to have begun in March.
“This threat actor has demonstrated sophistication and complex tradecraft in these intrusions,” the agency said in its unusual alert. “CISA expects that removing the threat actor from compromised environments will be highly complex and challenging.”
President Donald Trump, whose administration has been criticized for eliminating a White House cybersecurity adviser and downplaying Russian interference in the 2016 presidential election, has made no public statements about the breach.
President-elect Joe Biden said he would make cybersecurity a top priority of his administration, but that stronger defenses are not enough.
“We need to disrupt and deter our adversaries from undertaking significant cyberattacks in the first place,” he said. “We will do that by, among other things, imposing substantial costs on those responsible for such malicious attacks, including in coordination with our allies and partners.”
The cybersecurity agency previously said the perpetrators had used network management software from Texas-based SolarWinds t o infiltrate computer networks. Its new alert said the attackers may have used other methods, as well.
Over the weekend, amid reports that the Treasury and Commerce departments were breached, CISA directed all civilian agencies of the federal government to remove SolarWinds from their servers. The cybersecurity agencies of Britain and Ireland issued similar alerts.
A U.S. official previously told The Associated Press that Russia-based hackers were suspected, but neither CISA nor the FBI has publicly said who is believed be responsible. Asked whether Russia was behind the attack, the official said: “We believe so. We haven’t said that publicly yet because it isn’t 100% confirmed.”
Another U.S. official, speaking Thursday on condition of anonymity to discuss a matter that is under investigation, said the hack was severe and extremely damaging although the administration was not yet ready to publicly blame anyone for it.
“This is looking like it’s the worst hacking case in the history of America,” the official said. “They got into everything.”
The official said the administration is working on the assumption that most, if not all, government agencies were compromised but the extent of the damage was not yet known.
This hack had nothing to do with President Trump firing Director Krebs at CISA even though Associated Press keeps suggesting. But things just took a turn for the bad bad side –>
Sandia
/https://static.texastribune.org/media/files/174cf0beea0e357d19c00fe69593f659/Los_Alamos_TT.jpg) Los Alamos
Los Alamos
The Energy Department and National Nuclear Security Administration, which maintains the U.S. nuclear weapons stockpile, have evidence that hackers accessed their networks as part of an extensive espionage operation that has affected at least half a dozen federal agencies, officials directly familiar with the matter said.
On Thursday, DOE and NNSA officials began coordinating notifications about the breach to their congressional oversight bodies after being briefed by Rocky Campione, the chief information officer at DOE.
They found suspicious activity in networks belonging to the Federal Energy Regulatory Commission (FERC), Sandia and Los Alamos national laboratories in New Mexico and Washington, the Office of Secure Transportation and the Richland Field Office of the DOE. The hackers have been able to do more damage at FERC than the other agencies, the officials said, but did not elaborate.
Federal investigators have been combing through networks in recent days to determine what hackers had been able to access and/or steal, and officials at DOE still don’t know whether the attackers were able to access anything, the people said, noting that the investigation is ongoing and they may not know the full extent of the damage “for weeks.”
Spokespeople for DOE did not immediately respond to requests for comment.
The attack on DOE is the clearest sign yet that the hackers were able to access the networks belonging to a core part of the U.S. national security enterprise. The hackers are believed to have gained access to the federal agencies’ networks by compromising the software company SolarWinds, which sells IT management products to hundreds of government and private-sector clients.
DOE officials were planning on Thursday to notify the House and Senate Energy committees, House and Senate Energy and Water Development subcommittees, House and Senate Armed Services committees, and the New Mexico and Washington State delegations of the breach, the officials said.
The FBI, Cybersecurity and Infrastructure Security Agency, and Office of the Director of National Intelligence acknowledged the “ongoing” cybersecurity campaign in a joint statement released on Wednesday, saying that they had only become aware of the incident in recent days.
“This is a developing situation, and while we continue to work to understand the full extent of this campaign, we know this compromise has affected networks within the federal government,” the statement read.
NNSA is responsible for managing the nation’s nuclear weapons, and while it gets the least attention, it takes up the vast majority of DOE’s budget. Similarly, the Sandia and Los Alamos National Labs conduct atomic research related to both civil nuclear power and nuclear weapons. The Office of Secure Transportation is tasked with moving enriched uranium and other materials critical for maintaining the nuclear stockpile.
Hackers may have been casting too wide a net when they targeted DOE’s Richland Field Office, whose primary responsibility is overseeing the cleanup of the Hanford nuclear waste site in Washington state. During World War II and the Cold War, the U.S. produced two- thirds of its plutonium there, but the site hasn’t been active since 1971.
The attack on the Federal Energy Regulatory Commission may have been an effort to disrupt the nation’s bulk electric grid. FERC doesn’t directly manage any power flows, but it does store sensitive data on the grid that could be used to identify the most disruptive locations for future attacks.


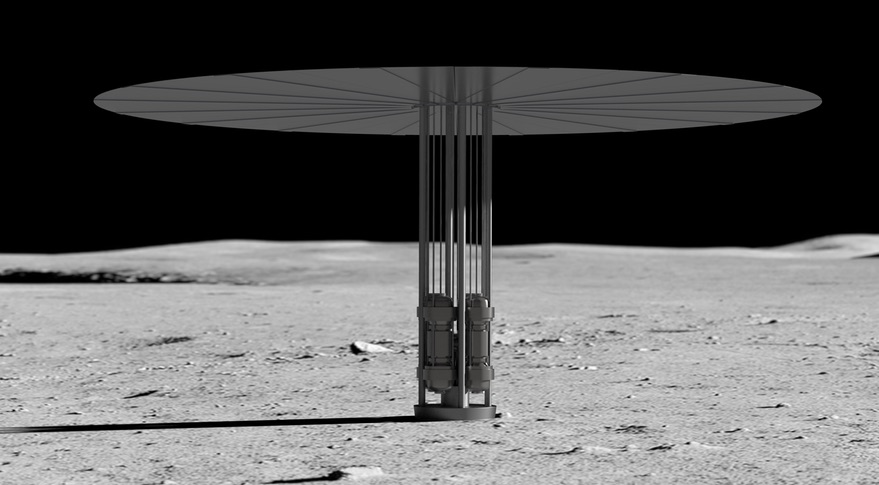 An illustration of a Kilopower nuclear reactor on the moon. Development of surface nuclear power technologies is a key element of the roadmap included in Space Policy Directive 6. Credit: NASA
An illustration of a Kilopower nuclear reactor on the moon. Development of surface nuclear power technologies is a key element of the roadmap included in Space Policy Directive 6. Credit: NASA