So, a senior official in the Trump campaign was the victim of an email phishing trick and it worked….countless emails were hacked/stolen and began to be distributed. Microsoft has confirmed this and several Iranian cyber signatures from previous hack are providing some pretty good attributions to Iran as the hackers. But no worries, the FBI, likely the Pittsburgh office as agreed t investigate.
Just last night after some recent promoting the SPACES event hosted by Donald Trump and Elon Musk was delayed for an estimated 45 minutes due to a DDOS hit. Again, that too had the signature tactics of Iran.  source
source
The hackers allegedly obtained sensitive data as a result of a successful phishing campaign against Trump officials. Cheung cited the Microsoft report which said in June 2024, Mint Sandstorm, a group run by the Islamic Revolutionary Guards Corp (IRGC) intelligence unit, sent a spear-phishing email to a high-ranking official of a presidential campaign from a compromised email account of a former senior advisor.
“On Friday, a new report from Microsoft found that Iranian hackers broke into the account of a ‘high ranking official’ on the US presidential campaign in June 2024, which coincides with the close timing of President Trump’s selection of a vice-presidential nominee,” Cheung added. More here.
Threat actor Mint Sandstorm, believed to be linked to Iran, has been observed using bespoke phishing lures to attack high-profile targets while leveraging a new custom backdoor called MediaPI.
In a Jan. 17 blog post, Microsoft Threat Intelligence said the attacks were on individuals working at a high level on Middle Eastern affairs at universities and research organizations in Belgium, France, Gaza, Israel, the United Kingdom, and the United States.
The Microsoft researchers said Mint Sandstorm — also known as APT35 and APT42 — used legitimate, yet compromised accounts to send phishing lures. The researchers said Mint Sandstorm continues to improve and modify the tooling used in targets’ environments, activity that might help the group persist in a compromised environment and better evade detection.
“Based on the identities of the targets observed in this campaign and the use of lures related to the Israel-Hamas war, it’s possible this campaign is an attempt to gather perspectives on events related to the war from individuals across the ideological spectrum,” wrote the researchers.
Mint Sandstorm operates as a state-sponsored actor from Iran and, as a result, serves government agency and potential military objectives, explained Balazs Greksza, threat response lead at Ontinue. Greksza said the group employs tactics such as watering hole attacks and phishing emails, to target governments, NGOs, private entities, and academia for espionage. They often pose as journalists, government officials, or academics on social media and their primary objective is to get hold of sensitive information.
“Actors like APT35 have primary goals around geopolitics, national security, counter-intelligence,” said Greksza. “As openly shared by different intelligence agencies in the past, intelligence goals may shift rapidly based on the needs of national interests, current political and military leadership and their decision and intelligence needs.”
Ngoc Bui, cybersecurity expert at Menlo Security, added that the deployment of the custom backdoor MediaPI, along with the use of other tools like MischiefTut, indicates a shift in the operational tactics of Mint Sandstorm, marking an evolution in their cyber espionage capabilities.
***
This all begs the question, just exactly what is being done to not only protect a political campaign and election, but every website or American out there from Iran, Russia, China or North Korea and their team of hackers?
CSOOnline goes on to read –>
Iran, found extremely capable in the past of conducting cyberattacks against its foes in the Middle East, earlier in 2022 had threatened to avenge the killing of General Qassem Soleimani by the United States in a drone strike ordered by the Trump administration.
During this time, among many other efforts, Mandiant reported that the news site EvenPolitics, a Tehran-controlled disinformation site, had published articles covering the 2022 US midterm elections. An inauthentic amplification network promoting the site was taken down by the X platform that same year, yet EvenPolitics continues to operate, releasing approximately ten articles per week.
Microsoft, in its report, added that Iranian cyber-enabled influence operations “have been a consistent feature of at least the last three US election cycles”.
Iran’s mission to the United Nations, in response to inquiries about the Trump campaign’s allegations, denied any involvement. Speaking to The Associated Press, the mission stated, “We dismiss these reports entirely. The Iranian government has neither the capability nor the intention to interfere in the United States presidential election.”

 .Satellite imagery of Ream Naval Base from 5 February 2023, annotated to show the shape of the pier extension. Original image courtesy of BlackSky
.Satellite imagery of Ream Naval Base from 5 February 2023, annotated to show the shape of the pier extension. Original image courtesy of BlackSky



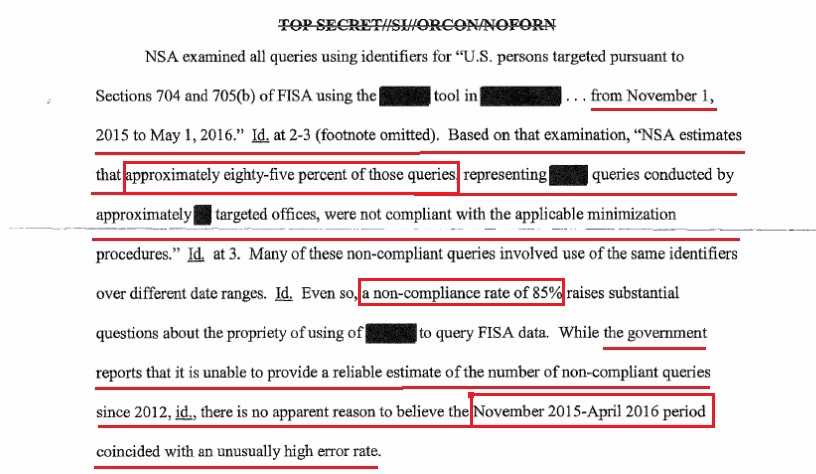
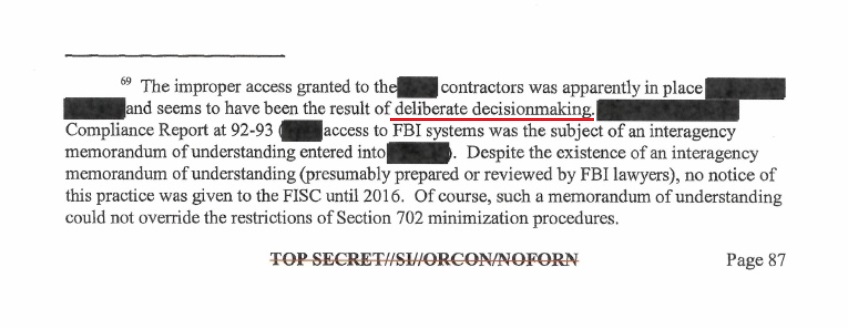 This specific footnote is a key. Note the phrase: “([redacted] access to FBI systems was the subject of an interagency memorandum of understanding entered into [redacted])”, this sentence has the potential to expose an internal decision; withheld from congress and the FISA court by the Obama administration; that outlines a process for access and distribution of surveillance data.
This specific footnote is a key. Note the phrase: “([redacted] access to FBI systems was the subject of an interagency memorandum of understanding entered into [redacted])”, this sentence has the potential to expose an internal decision; withheld from congress and the FISA court by the Obama administration; that outlines a process for access and distribution of surveillance data.