Maybe new keels are soon to be laid and a draft could be in the future of the military.
As for the Army, the numbers are noted below but do not include the other branches of service.
ArmyTimes: Endstrength for March was 479,172 soldiers, which is 154 fewer troopers than were on active duty when the Army halted the post-Cold War drawdown in 1999 with 479,424 soldiers, the smallest force since 1940, when the active component numbered 269,023 soldiers.
Barring unexpected delays, the Army is well-positioned to achieve, or exceed, its budgeted end-strength of 475,000 soldiers by Sept. 30, the end of fiscal 2016.
Without congressional or Defense Department intervention, the drawdown will continue for two more years, with end strength hitting 460,000 soldiers in 2017, and 450,000 in 2018.
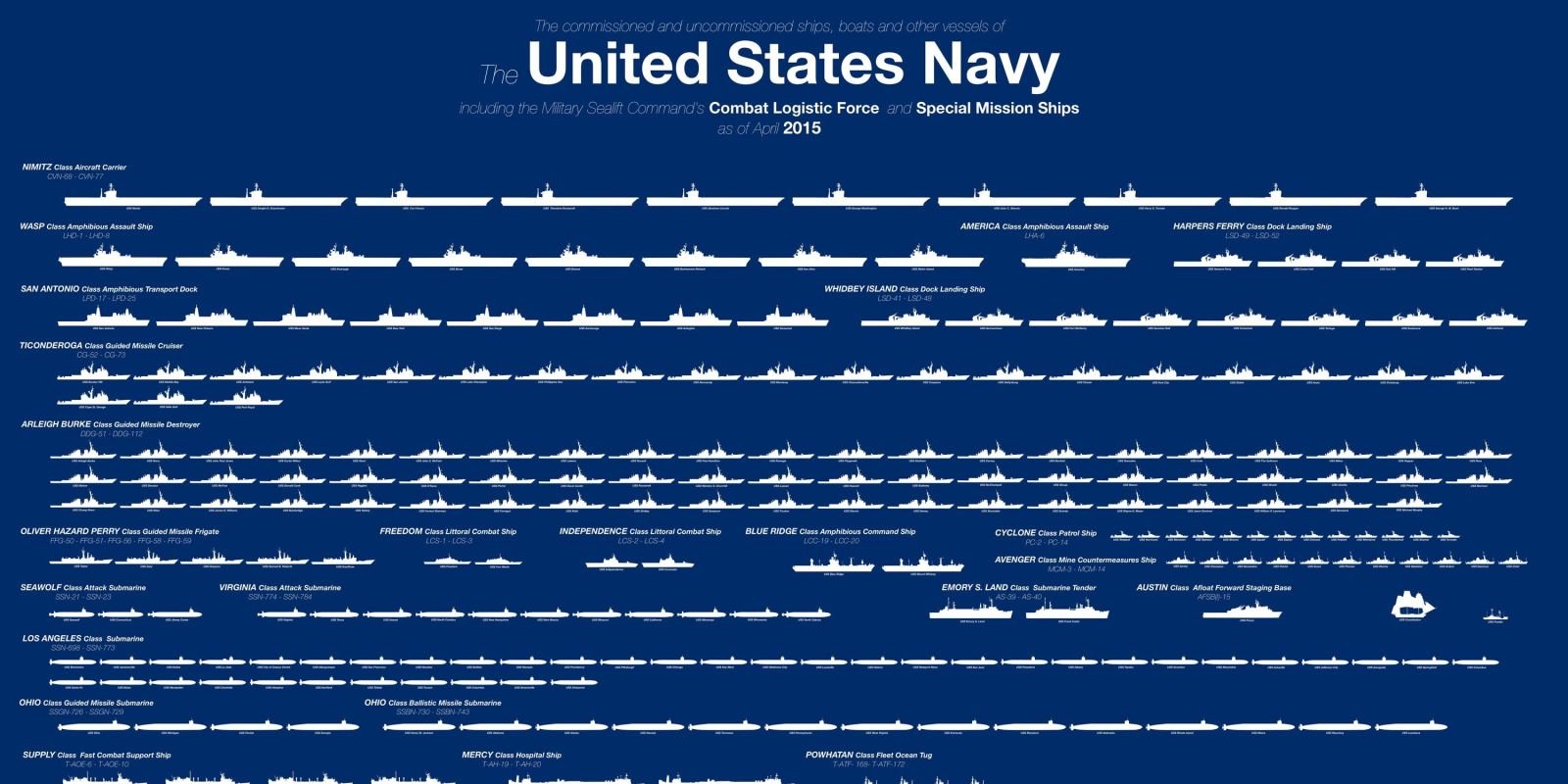
The United States Navy is a powerhouse. The fleet consists of roughly 430 ships in active service or reserve. The vessels run the gamut from the massive Nimitz-class aircraft carrier, which stretches more than 1,000 feet, to the Los Angeles-class submarine that slithers 900 feet below the ocean surface. The graphic below shows all the commissioned and noncommissioned ships of every size as of April 2015. The ships are organized by size, from the humongous aircraft carriers at the top to the smaller ships at the bottom.
Donald Trump wants to increase America’s military force in the Asia-Pacific
DONALD Trump’s administration has given its strongest indication yet that the United States will increase America’s military force against China.
Rudy Giuliani, the president-elect’s frontrunner for secretary of state, has revealed Mr Trump intends to prioritise building a “gigantic” military force to overthrow China’s ambitions in the Pacific.
Speaking to global business leaders in Washington yesterday, Mr Giuliani said the United States would raise its number of troops to 550,000, instead of shrinking it to 420,000.
He also said they intended to take their navy up to 350 ships, instead of going down to 247. It currently has around 280.
“At 350, China can’t match us in the Pacific. At 247 ships, we can’t fight a two-ocean war; we gave up the Pacific. If you face them with a military that is modern, gigantic, overwhelming and unbelievably good at conventional and asymmetric warfare, they may challenge it, but I doubt it.”
He said the expansion would allow the US to fight a “two-ocean war”.
This presents a more assertive foreign policy than the world ever heard from Mr Trump in the lead-up to election with regards to China.
While the South China Sea remains one of the world’s most tense geopolitical regions, the celebrity billionaire was careful to keep his remarks on it to a minimum in the lead-up to the US election.
Experts have told news.com.au Mr Trump has always been set on building the US’s military presence.
“It’s likely that America will have a lot more military muscle under his presidency,” said Macquarie University Security Studies analyst Adam Lockyer. “While we can’t get ahead of ourselves, much of that will likely go into the Asia-Pacific region, because China’s a major challenger.
“On one hand they’re paying less diplomatic and critical attention to the region, but on the other they’re building more military presence in the region.”
That said, Mr Giuliani’s remarks suggest Mr Trump’s administration will be more hawkish than expected.
It was expected that Mr Trump would retreat from the disputed region, in line with his pledge to prioritise domestic issues and retreat from foreign affairs.
“Trump has a far more isolationist outlook than Clinton or Obama, but at the same time, if he had his own way, he’d be far more focused on domestic policy and domestic security, including things like terrorism and immigration,” Dr Lockyer said.
Judging by this announcement, the Trump administration may take a more hawkish approach after all.
WILL THIS ACTUALLY HAPPEN?
The Trump administration will face significant financial hurdles if it does take on this ambitious military program.
Asia-Pacific security expert Jingdong Yuan from the Centre For International Security Studies told news.com.au said it was achievable. He said Mr Trump will be able to work with the Republican-controlled Congress to do away with the sequester process that automatically cut $500 billion in defence over a decade.
But it could be relatively difficult for the incoming government to direct too much of its financial focus to defence.
“US defence spending as a percentage of GDP and government spending is at a historical low, especially after the wars in Afghanistan and Iraq,” said Dr Yuan.
“At the same time, entitlement spending, such as social security and medicare cannot be cut, and increase year by year, and federal government deficits of over $18-19 trillion make it difficult to spend more in discretionary areas such as defence.
“So Trump need to find the money to support his ambitious military programs. We will see.”
He also said that neither the United States nor China are being realistic when it comes down to it.
“Beijing and Washington will have to work on their differences while at the same time work together on things they both agree.
“This is a very complex relationship and neither America’s will to remain predominant nor China’s desire for a Sino-centric order in Asia are realistic.
“Indeed, if they both pursue these extreme goals, conflict will become more likely and it will be deeply destabilising for the region — Australia included.”
WHAT DOES ALL THIS MEAN FOR AUSTRALIA?
Defence Industries Minister Christopher Pyne says the planned expansion would create “remarkable opportunities” for Australia’s defence industry.
In a speech to be given at a Submarine Institute of Australia conference today, Mr Pyne will announce that the US expansion could offer a historic opportunity for Australia’s defence industry.
“To give you an understanding of the scale of this increase, it includes 50,000 more army troops, 70 new naval warships, 100 air force planes and a dozen new marine battalions,” Mr Pyne will say. “This represents around half a trillion US dollar increase to the US defence budget over the next decade.
“This result could bring with it remarkable opportunities for the Australian defence industry and, thanks to the foresight of the Turnbull government, Australia is well positioned to grasp those opportunities.”
Yesterday, Mr Pyne told The Australian the country will take a “similar focus” to the United States in terms of its defence policy.
“At a time when the US is expanding capability, we are similarly focused. As we have demonstrated throughout the year, the government is putting defence at the very centre of our national policy agenda.”
Mr Giuliani acknowledged the Trump administration hopes to engage with China on economic issues, such as trade.
Yesterday, he told The Wall Street Journal the team wants to reset relations with both China and Russia.
But Mr Trump intends to label China a “currency manipulator” after taking office, which economic analysts say will likely contribute to rising tensions between the two countries.
Chinese media has taken a hostile response to Mr Trump’s more outlandish comments on the country during his campaign.
In May this year, the then-presidential candidate accused China of “raping” the United States economically, and vowed to impose a 45 per cent tariff on Chinese imports.
An article published in the country’s nationalistic newspaper The Global Times this week warned the Chinese government will be forced to “take a tit-for-tat approach” if the president-elect persisted with the trade war.
“If Trump wrecks Sino-US trade, a number of US industries will be impaired. Finally the new president will be condemned for his recklessness, ignorance and incompetence and bear all the consequences.”
This trade war may also present problems for Australia. China and the United States are our first and third largest trading partners respectively, and such an action could trigger a trade war if Beijing were to retaliate, which would directly impact these relationships.
All this said, Dr Yuan says it’s still too soon to panic over what the Trump administration may or may not do.
“The election fog is still here and we need time and information to get more realistic and accurate assessments,” he said.
“I remain cautiously optimistic.”
****
At issue with China is the waterway dispute instigated by China.
 CNN
CNN

