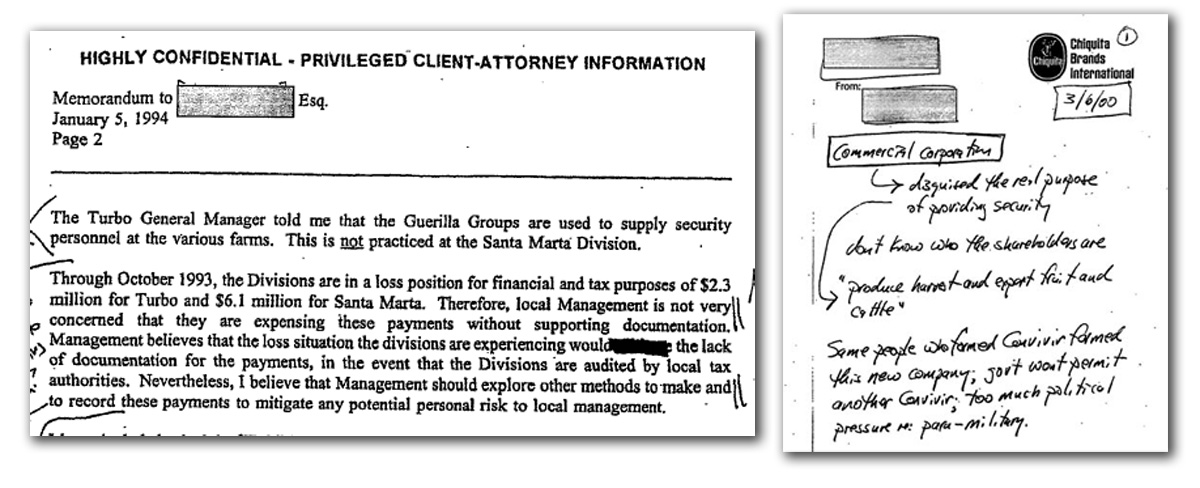
President Trump has conferred to Asian leaders over the matter of North Korea’s missile tests and the threats of a nuclear strike. Many conversations have been filling the phone wires that put President Xi of China in charge of handling Kim Jung Un. Okay, but can or will China do all that is necessary and will it resolve the threat of an escalated war in the region? The answer is unknown.
In part from FNC: U.S. commercial satellite images indicated increased activity around North Korea’s nuclear test site, while Kim has said that the country’s preparation for an ICBM launch is in its “final stage.”
South Korea’s Defense Ministry has said the North appears ready to conduct such “strategic provocations” at any time. South Korean Acting Prime Minister Hwang Kyo-ahn has instructed his military to strengthen its “immediate response posture” in case North Korea does something significant on the April 25 anniversary of its military. North Korea often marks significant dates by displaying military capability.
In a statement released late Friday, North Korea’s Foreign Ministry accused Trump of driving the region into an “extremely dangerous phase” with his sending of the aircraft carrier and said the North was ready to stand up against any kind of threated posed by the United States.
With typical rhetorical flourish, the ministry said North Korea “will react to a total war with an all-out war, a nuclear war with nuclear strikes of its own style and surely win a victory in the death-defying struggle against the U.S. imperialists.”
*** So, China appears to have taken some steps to send North Korea a message like refusing a coal shipment. But was that just a one off tactic? Cutting off oil and gasoline shipments…was that too yet another gesture by China? How about access to banking and ATM machines?
PYONGYANG, North Korea (AP) — No modern airport terminal is complete without an ATM, and Pyongyang’s now has two. But they don’t work — because of new Chinese sanctions, according to bank employees — and it’s not clear when they will.
ATMs are an alien enough concept in North Korea that those in the capital’s shiny new Sunan International Airport have a video screen near the top showing how they work and how to set up an account to use them. The explanatory video is in Korean, but the machines, which are meant primarily for Chinese businesspeople and tourists, don’t give out cash in the North Korean currency.
Humm right? But can we really trust China to go the distance to stop North Korea? I offer this answer…NO.
China has been angry with the United States over deploying the THAAD missile defense system in S. Korea. China is one of the largest know hacking networks in the world…remember that? Alright, how about this lil gem?
***
Researchers claim China trying to hack South Korea missile defense efforts
Deployment of THAAD upsets China, seen as espionage tool.
Sean Gallagher: Chinese government officials have been very vocal in their opposition to the deployment of the Terminal High-Altitude Air Defense (THAAD) system in South Korea, raising concerns that the anti-ballistic missile system’s sensitive radar sensors could be used for espionage. And according to researchers at the information security firm FireEye, Chinese hackers have transformed objection to action by targeting South Korean military, government, and defense industry networks with an increasing number of cyberattacks. Those attacks included a denial of service attack against the website of South Korea’s Ministry of Foreign Affairs, which the South Korean government says originated from China.
FireEye’s director of cyber-espionage analysis John Hultquist told the Wall Street Journal that FireEye had detected a surge in attacks against South Korean targets from China since February, when South Korea announced it would deploy THAAD in response to North Korean missile tests. The espionage attempts have focused on organizations associated with the THAAD deployment. They have included “spear-phishing” e-mails carrying attachments loaded with malware along with “watering hole” attacks that put exploit code to download malware onto websites frequented by military, government, and defense industry officials.
FireEye claims to have found evidence that the attacks were staged by two groups connected to the Chinese military. One, dubbed Tonto Team by FireEye, operates from the same region of China as previous North Korean hacking operations. The other is known among threat researchers as APT10, or “Stone Panda”—the same group believed to be behind recent espionage efforts against US companies lobbying the Trump administration on global trade. These groups have also been joined in attacks by two “patriotic hacking” groups not directly tied to the Chinese government, Hultquist told the Journal—including one calling itself “Denounce Lotte Group” targeting the South Korean conglomerate Lotte. Lotte made the THAAD deployment possible through a land swap with the South Korean government.
APT = Advanced Persistent Threat 10 refers to China as noted here with this summary which was found as early as 2009. In part it includes:
“Operation Cloud Hopper” uses internet addresses also used by the threat actor known in the cybersecurity community as “APT10.” Using a combination of unique hacking tools and open source software, it has attempted to gather information about diplomatic and political organizations, as well as intellectual property, according to the report.
APT10 was identified in a 2013 report by FireEye detailing its use of the Poison Ivy family of malware, which the new report says ceased after FireEye revealed its findings. Also in 2013, FireEye identified APT1, which appears to be Unit 61398 of China’s People’s Liberation Army. The PwC-BAE report notes that the “Operation Cloud Hopper” attacks tend to occur during business hours in China.
Since 2009, APT10 has been observed to target mostly government and U.S. defense organizations, but now “has almost certainly been undertaking a global operation of unprecedented size and scale targeting a number of MSPs,” the report says.