ISIS in America
The report, ISIS in America: From Retweets to Raqqa consists of two parts. The first examines all cases of U.S. persons arrested, indicted, or convicted in the United States for ISIS-related activities. A wide array of legal documents related to these cases provides empirical evidence for identifying several demographic factors related to the arrested individuals. This section also looks at the cases of other Americans who, while not in the legal system, are known to have engaged in ISIS-inspired behavior.
The second part of the report examines various aspects of the ISIS-related mobilization in America. Here the report analyzes the individual motivations of ISIS supporters; the role of the Internet and, in particular, social media, in their radicalization and recruitment processes; whether their radicalization took place in isolation or with other, like-minded individuals; and the degree of their tangible links to ISIS. It concludes with recommendations to combat ISIS recruitment.
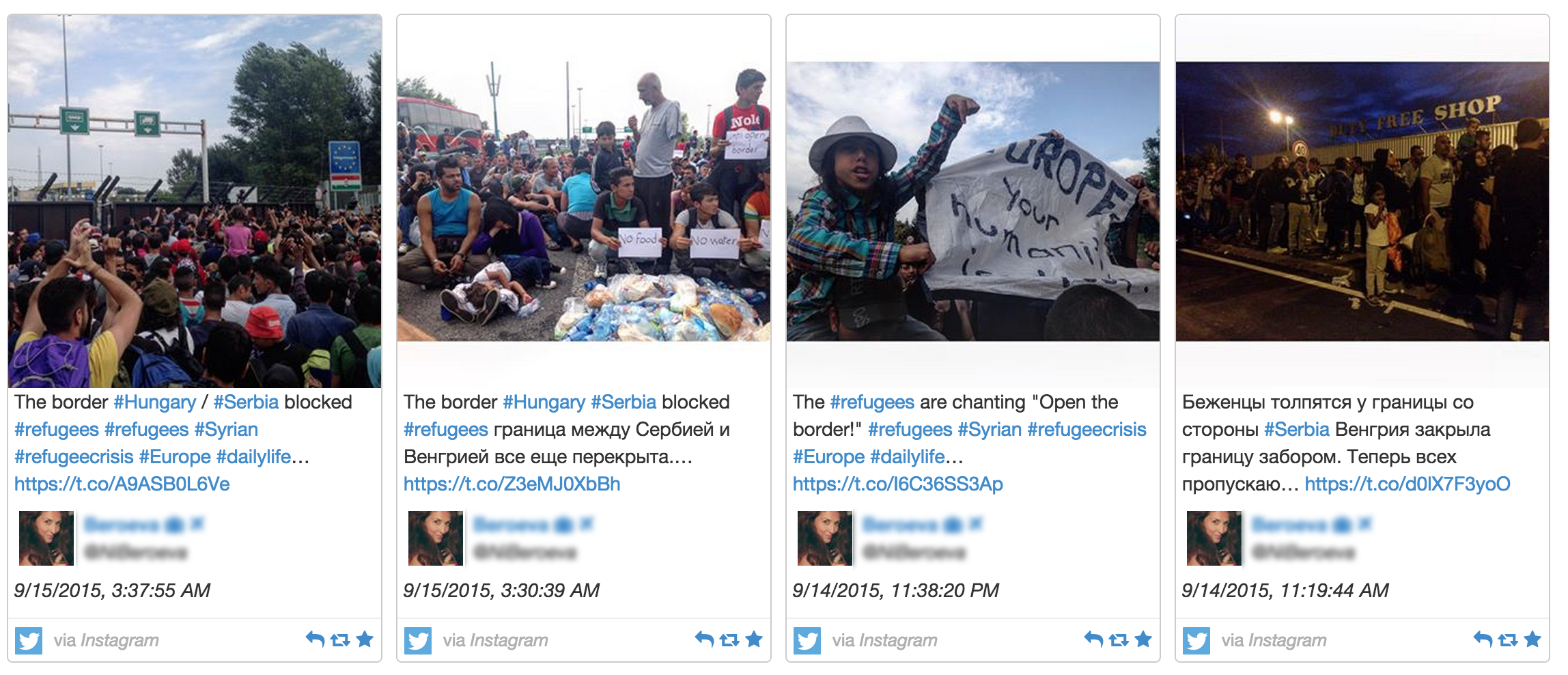
Brussels Is Latest Target in Islamic State’s Assault on West
The Islamic State has also inspired people to carry out attacks. In December, a woman in San Bernardino, Calif., posted her “bayat,” or oath of allegiance, to the Islamic State on a Facebook page moments before she and her husband opened fire in a conference room, killing 14 people.
The couple did not appear to have been directed by the Islamic State, but seemed to have been inspired by the group’s instructions for supporters to attack Western targets.
Whether inspired or coordinated, these attacks have drawn attention to the growing number of civilian deaths caused by the group outside of Iraq and Syria. The Islamic State has a history of attacking mosques, hotels, busy city streets and other civilian targets in mostly non-Western countries. The civilian death toll outside Iraq and Syria has risen to more than 1,000 since January 2015.

* inciting regional conflict with attacks in Iraq and Syria;
* building relationships with jihadist groups that can carry out military operations across the Middle East and North Africa;
* and inspiring, and sometimes helping, ISIS sympathizers to conduct attacks in the West.
ISIS Declares Provinces Across the Region
Countries where ISIS has declared provinces
“The goal,” Ms. Gambhir said, “is that through these regional affiliates and through efforts to create chaos in the wider world, the organization will be able to expand, and perhaps incite a global apocalyptic war.”
Major ISIS Attacks
Descriptions of the Major Attacks
| Date | Location | Details | |
|---|---|---|---|
| Mar. 22, 2016 Belgium |
Belgium | A series of deadly terrorist attacks struck Brussels, with two explosions at the city’s main international airport and a third in a subway station at the heart of the city, near the headquarters complex of the European Union. More » | |
| Mar. 19, 2016 Turkey |
Turkey | A suicide bombing on Istanbul’s busiest thoroughfare killed three Israeli citizens and an Iranian. Two of the Israelis held dual Israeli-American citizenship. More » | |
| Mar. 4, 2016 Yemen |
Yemen | Gunmen killed 18 people at a nursing home founded by Mother Teresa and run by Christian nuns. More » | |
| Jan. 29, 2016 Yemen |
Yemen | A bomb-packed car driven by a suicide attacker exploded at a checkpoint near the presidential palace in the southern city of Aden, killing at least eight people. More » | |
| Jan. 14, 2016 Indonesia |
Indonesia | ISIS claimed responsibility for explosions and gunfire that rocked central Jakarta, killing at least two civilians. More » | |
| Jan. 12, 2016 Turkey |
Turkey | A Syrian suicide bomber set off an explosion in the historic central districtof Istanbul, killing 10 people and wounding at least 15 others, in an attack the Turkish government attributed to ISIS. More » | |
| Jan. 11, 2016 France |
France | A teenager attacked a Jewish teacher with a machete in Marseille, and afterward told the police that he had carried out the attack in the name of God and the Islamic State. | |
| Jan. 8, 2016 Egypt |
Egypt | Gunmen reportedly carrying an ISIS flag opened fire at a Red Sea resort, injuring at least two tourists. More » | |
| Jan. 7, 2016 Egypt |
Egypt | ISIS claimed responsibility for an attack on a hotel in Cairo near the Giza Pyramids. No one was hurt. More » | |
| Jan. 7, 2016 Pennsylvania |
Pennsylvania | A man shot and wounded a Philadelphia police officer sitting in a patrol car in the name of Islam and the Islamic State, police said. More » | |
| Jan. 4, 2016 Libya |
Libya | Islamic State militants attempted to capture an oil port along Libya’s coast, in fighting that left at least seven people dead. | |
| Dec. 7, 2015 Yemen |
Yemen | The Islamic State claimed responsibility for a car bomb that killed a provincial governor and eight of his body guards. More » | |
| Dec. 2, 2015 California |
California | A married couple shot and killed 14 people in San Bernardino, Calif. The FBI is investigating the shooting as an act of terrorism inspired by ISIS. More » | |
| Nov. 26, 2015 Bangladesh |
Bangladesh | ISIS claimed responsiblity for an attack on a Shiite mosque during evening prayer in which gunmen opened fire on worshipers with machine guns, killing one man and injuring three others. More » | |
| Nov. 24, 2015 Egypt |
Egypt | ISIS militants attacked a hotel in the northern Sinai Peninsula, killing at least seven people. | |
| Nov. 18, 2015 France |
France | A teacher at a Jewish school in Marseille was stabbed by three people who appeared to profess support for ISIS. More » | |
| Nov. 13, 2015 France |
France | President François Hollande blamed the Islamic State for terrorist attacks across Paris that killed more than 100 people. The Islamic State claimed responsiblity. More » | |
| Nov. 12, 2015 Lebanon |
Lebanon | ISIS claimed responsiblity for a double suicide bombing that ripped through a busy shopping district at rush hour, killing at least 43 people. More » | |
| Nov. 4, 2015 Egypt |
Egypt | ISIS’s Sinai affiliate claimed responsiblity for a suicide bombing that killed at least four police officers. More » | |
| Nov. 4, 2015 Bangladesh |
Bangladesh | ISIS claimed responsibility for a stabbing and shooting that left one police officer dead and another wounded. More » | |
| Oct. 31, 2015 Egypt |
Egypt | An ISIS affiliate in Sinai claimed responsiblity for the downing of a Russian passenger jet that killed all 224 people on board. More » | |
| Oct. 30 Turkey |
Turkey | ISIS militants killed two Syrian anti-ISIS activists. | |
| Oct. 24, 2015 Bangladesh |
Bangladesh | ISIS claimed responsiblity for bombings that killed one person and wounded dozens more during a procession commemorating a Shiite Muslim holiday. More » | |
| Oct. 10, 2015 Turkey |
Turkey | Two explosions killed more than 100 people who had gathered for a peace rally in Turkey’s capital. Turkish officials believe ISIS is responsible. More » | |
| Oct. 6, 2015 Yemen |
Yemen | A series of bombings in Yemen’s two largest cities killed at least 25 people. More » | |
| Oct. 3, 2015 Bangladesh |
Bangladesh | ISIS claimed responsibilty for the shooting death of a Japanese man riding a rickshaw. More » | |
| Sep. 28, 2015 Bangladesh |
Bangladesh | ISIS claimed responsiblity for the shooting death of an Italian aid worker. More » | |
| Sep. 24, 2015 Yemen |
Yemen | At least 25 people were killed when two bombs went off outside a mosque during prayers to commemorate Eid al-Adha, a major Muslim holiday. More » | |
| Sep. 18, 2015 Libya |
Libya | Militants loyal to the Islamic State attacked a prison inside a Tripoli air base. More » | |
| Sep. 17, 2015 Germany |
Germany | An Iraqi man was shot dead after he stabbed a policewoman in Berlin. | |
| Sep. 2, 2015 Yemen |
Yemen | Yemen’s ISIS affiliate claimed responsibility for two bombings at a mosque that killed at least 20 people. More » | |
| Aug. 26, 2015 Egypt |
Egypt | The Sinai Province of the Islamic State group claimed responsibility for three gunmen who shot and killed two police officers. | |
| Aug. 21, 2015 France |
France | A gunman opened fire aboard a packed high-speed train traveling from Amsterdam to Paris, wounding several passengers before he was tackled and subdued by three Americans. | |
| Aug. 20, 2015 Egypt |
Egypt | An ISIS affiliate claimed responsibility for bombing a branch of the Egyptian security agency. More » | |
| Aug. 12, 2015 Egypt |
Egypt | An ISIS affiliate said it had beheaded a Croatian expatriate worker because of Croatia’s “participation in the war against the Islamic State.” More » | |
| Aug. 7, 2015 Saudi Arabia |
Saudi Arabia | ISIS claimed responsibility for a suicide bombing at a mosque that killed at least 15 people, including 12 members of a Saudi police force. More » | |
| Jul. 20, 2015 Turkey |
Turkey | A Turkish citizen believed to have had ties to ISIS killed at least 32 people at a cultural center. More » | |
| Jul. 16, 2015 Egypt |
Egypt | In what appeared to be the first attack on a naval vessel claimed by Sinai Province, the ISIS affiliate said it destroyed an Egyptian naval vessel and posted photographs on social media of a missile exploding in a ball of fire as it slammed into the vessel. More » | |
| Jul. 11, 2015 Egypt |
Egypt | ISIS claimed responsibility for an explosion outside the Italian Consulate’s compound in downtown Cairo that killed one person. More » | |
| Jul. 1, 2015 Egypt |
Egypt | Militants affiliated with the Islamic State killed dozens of soldiers in simultaneous attacks on Egyptian Army checkpoints and other security installations in Egypt’s northern Sinai Peninsula. More » | |
| Jun. 26, 2015 Tunisia |
Tunisia | At least one gunman disguised as a vacationer attacked a Mediterranean resort, killing at least 38 people at a beachfront hotel — most of them British tourists — before he was shot to death by the security forces. More » | |
| Jun. 26, 2015 Kuwait |
Kuwait | A suicide bomber detonated explosives at one of the largest Shiite mosques in Kuwait City during Friday Prayer. More » | |
| Jun. 17, 2015 Yemen |
Yemen | An ISIS branch claimed responsibilty for a series of car bombings in Sana, the capital, that killed at least 30 people. More » | |
| Jun. 9, 2015 Egypt |
Egypt | ISIS’s Sinai province claimed responsibility for firing rockets toward an air base used by an international peacekeeping force. | |
| Jun. 5, 2015 Turkey |
Turkey | An explosion at a political rally in the predominantly Kurdish city of Diyarbakir killed two people and wounded more than 100. Turkish officials have said ISIS was behind the attack. More » | |
| Jun. 5, 2015 Turkey |
Turkey | Two bombs killed three people at a rally for the pro-Kurdish Peoples’ Democratic Party, or H.D.P. | |
| Jun. 3, 2015 Afghanistan |
Afghanistan | ISIS is suspected of beheading 10 members of the Taliban. More » | |
| May. 31, 2015 Libya |
Libya | A suicide bomber from an ISIS affiliate killed at least four Libyan fighters at a checkpoint. More » | |
| May. 29, 2015 Saudi Arabia |
Saudi Arabia | One week after a similar attack in the same region, a suicide bomber dressed in women’s clothing detonated an explosive belt near the entrance to a Shiite mosque, killing three people. More » | |
| May. 22, 2015 Yemen |
Yemen | ISIS claimed responsibility for a bomb attack on a Shiite mosque that injured at least 13 worshipers. | |
| May. 22, 2015 Saudi Arabia |
Saudi Arabia | In what appeared to be ISIS’s first official claim of an attack in Saudi Arabia, a suicide bomber detonated an explosive at a Shiite mosque during midday prayer, killing at least 21 and injuring 120. More » | |
| May 18 Turkey |
Turkey | A bomb detonated at the pro-Kurdish Peoples’ Democratic Party, or H.D.P. | |
| May. 18, 2015 Turkey |
Turkey | Militants detonated a bomb at office of the pro-Kurdish Peoples’ Democratic Party, or H.D.P. | |
| May. 3, 2015 Texas |
Texas | Two men who reportedly supported ISIS and were later acknowledged by ISIS as “soldiers of the caliphate” opened fire in a Dallas suburb outside a Prophet Muhammad cartoon contest. More » | |
| Apr. 30, 2015 Yemen |
Yemen | One of ISIS’s Yemen affiliates released a video showing the killing of 15 Yemeni soldiers. | |
| Apr. 27, 2015 Bosnia and Herzegovina |
Bosnia and Herzegovina | A gunman attacked a police station. | |
| Apr. 19, 2015 Libya |
Libya | ISIS released a video of militants from two of its Libya affiliates killing dozens of Ethiopian Christians, some by beheading and others by shooting. | |
| Apr. 12, 2015 Libya |
Libya | ISIS’s Tripoli affiliate claimed credit for a bomb that exploded outside the Moroccan Embassy. | |
| Apr. 12, 2015 Egypt |
Egypt | ISIS militants killed at least 12 people in three separate attacks on Egyptian security forces. More » | |
| Apr. 12, 2015 Libya |
Libya | ISIS’s Tripoli affiliate claimed responsibility for an attack on the South Korean Embassy that killed two local police officers. More » | |
| Apr. 8, 2015 Saudi Arabia |
Saudi Arabia | Gunmen opened fire on a police patrol, killing two officers. | |
| Apr. 5, 2015 Libya |
Libya | ISIS killed at least four people in an attack on a security checkpoint. | |
| Apr. 4, 2015 Afghanistan |
Afghanistan | The Afghan vice president accused ISIS of kidnapping 31 civilians in February. | |
| Apr. 2, 2015 Egypt |
Egypt | Sinai’s ISIS affiliate killed 13 people with simultaneous car bombs at military checkpoints. More » | |
| Apr. 1, 2015 Turkey |
Turkey | Militants killed a Syrian teacher in Turkey. | |
| Mar. 20, 2015 Yemen |
Yemen | An ISIS affiliate claimed responsibility for coordinated suicide strikes on Zaydi Shiite mosques that killed more than 130 people during Friday Prayer. More » | |
| Mar. 18, 2015 Tunisia |
Tunisia | ISIS claimed responsibility for an attack on a museum that killed 22 people, almost all European tourists. More » | |
| Feb. 20, 2015 Libya |
Libya | ISIS’s Derna affiliate claimed responsibility for three car bombs that killed at least 40 people. More » | |
| Feb. 15, 2015 Libya |
Libya | ISIS released a video that appeared to show its militants in Libya beheading a group of Egyptian Christians who had been kidnapped in January. More » | |
| Feb. 15, 2015 Denmark |
Denmark | A Danish-born gunman who was inspired by ISIS went on a violent rampage in Copenhagen, killing two strangers and wounding five police officers. More » | |
| Feb. 3, 2015 Libya |
Libya | ISIS militants were suspected of killing 12 people, including four foreigners, in an attack on an oil field. More » | |
| Jan. 29, 2015 Egypt |
Egypt | ISIS’s Sinai affiliate claimed responsibility for coordinated bombings that killed 24 soldiers, six police officers and 14 civilians. More » | |
| Jan. 27, 2015 Libya |
Libya | ISIS’s Tripoli affiliate claimed credit for an armed assault on a luxury hotel that killed at least eight people. It was the deadliest attack on Western interests in Libya since the assault on the American diplomatic mission in Benghazi. More » | |
| Jan. 23, 2015 Lebanon |
Lebanon | ISIS attacked an outpost of the Lebanese Armed Forces. | |
| Jan. 16, 2015 Bosnia and Herzegovina |
Bosnia and Herzegovina | An attacker killed an imam at a mosque. | |
| Jan. 12, 2015 Libya |
Libya | ISIS’s Tripoli affiliate said they were holding 21 Egyptian Christians captive. More » | |
| Jan. 11, 2015 France |
France | A video surfaced of Amedy Coulibaly, one of three gunmen who attacked the newspaper Charlie Hebdo, declaring allegiance to ISIS. More » | |
| Jan. 6, 2015 Turkey |
Turkey | Suicide bomber injured two people at a police station. | |
| Dec. 22, 2014 France |
France | A van plowed into an outdoor Christmas market in Nantes. More » | |
| Dec. 21, 2014 France |
France | A French citizen of Algerian and Moroccan descent drove into pedestrians in Dijon, wounding 13 people. More » | |
| Dec. 15, 2014 Australia |
Australia | A gunman who said he was acting on ISIS’s behalf seized 17 hostages in a Sydney cafe. More » | |
| Nov. 22, 2014 Saudi Arabia |
Saudi Arabia | A Danish executive was shot in his car. A group of ISIS supporters later claimed responsibility. | |
| Oct. 23, 2014 New York |
New York | A hatchet-wielding man charged at four police officers in Queens. ISIS said the attack was the “direct result” of its September call to action. More » | |
| Oct. 22, 2014 Canada |
Canada | An Islamic convert shot and killed a soldier who was guarding the National War Memorial in Ottawa, stormed Canada’s parliament and fired multiple times before being shot and killed. More » | |
| Oct. 20, 2014 Canada |
Canada | A 25-year-old man who had recently adopted radical Islam ran over two soldiers near Montreal, killing one. More » | |
| Sep. 24, 2014 Algeria |
Algeria | Militants kidnapped and beheaded a French tourist shortly after the Islamic State called on supporters around the world to harm Europeans in retaliation for airstrikes in Iraq and Syria. More » | |
| Sep. 23, 2014 Australia |
Australia | An 18-year-old ISIS sympathizer was shot dead after stabbing two counterterrorism officers outside a Melbourne police station. More » |


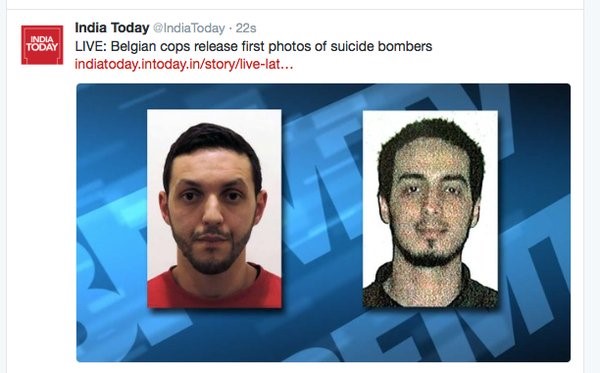
 From airport security camera.
From airport security camera.