The two faced dragon….tie to really recalibrate the relationship between the United States and China AGAIN….Previously n this website, I have discussed not only by a post but several times on radio about how the former intelligence/snooping base owned by Russia in Cuba known as the Lourdes SIGINT station was sold to China….no one in media or the national security realm seems to give it much attention…but now…we have an additional problem with China and that is the Bahamas.
How about the largest Chinese embassy in the world with hundreds of Chinese intelligence officers deployed there…..
In part from FNC:
“The People’s Republic of China has been making diplomatic, economic and even military and quasi-military inroads into the Caribbean, South and Central America for the past couple of decades,” retired Rear Adm. Peter Brown, former Homeland Security advisor to President Donald Trump, told Fox News Digital.
Brown pointed to the rise in dual-use infrastructure projects along the Bahamas coastline, which is located just 50 miles off the coast of Florida.
“It doesn’t take a lot of imagination for the People’s Republic of China to use its commercial footprint in the Bahamas to monitor, exploit and perhaps even do worse to [the] U.S.,” he said. Pointing to the Chinese-controlled British Colonial Hotel in Nassau, Bahamas, Brown said that its location directly across from the U.S. Embassy could give way to intelligence gathering on U.S. personnel.
The hotel is owned by a Chinese company, Chow Tai Fook Enterprises, which has raised geopolitical concerns given its location. Fox News Digital has reached out to the British Colonial Hotel for comment.
China has invested heavily in the Bahamas through a range of additional high-profile projects, including a $40 million grant for a national stadium, a $3 billion mega-port in Freeport, and $40 million for the North Abaco Port and Little Abaco Bridge.
In 2019, now-Secretary of State Marco Rubio warned in a Miami Herald op-ed that the devastation caused by the natural disaster could create an opening for the People’s Republic of China to use aid as a Trojan horse to gain a foothold near American shores.
“By targeting the Bahamian government in this period of crisis, Beijing would be making the same opportunistic play to access critical foreign infrastructure,” Rubio wrote in 2019. “But in this case, the national security threat is especially perilous, as it would give China a foothold just 50 miles from the coast of Florida.”
***
How about another look at things in the Caribbean…Chinese expansion

China’s Influence in the Caribbean:
China is a member of both the Inter-American Development Bank (IDB) and the Caribbean Development Bank (CDB) and an observer at the Organization of American States (OAS). Alongside Italy and Germany, China is the third largest shareholder at the CDB with 5.6% of overall shares, exponentially higher than the majority of Caribbean countries.
The People’s Republic of China’s (PRC) engagement in the Caribbean has largely focused on investments in infrastructure and developing trade relationships. As of 2022, ten Caribbean countries have signed up to Belt and Road (BRI) – Cuba, Jamaica, Dominican Republic, Antigua & Barbuda, Dominica, Barbados, Grenada, Trinidad & Tobago, Guyana, and Suriname.
The PRC is working towards diminishing the region’s ties to Taiwan as the region contains the largest bulk of Taiwan’s diplomatic allies. Today, St. Lucia, St. Vincent and the Grenadines, St. Kitts and Nevis, Haiti, and Belize remain the only Caribbean nations that recognize Taiwan.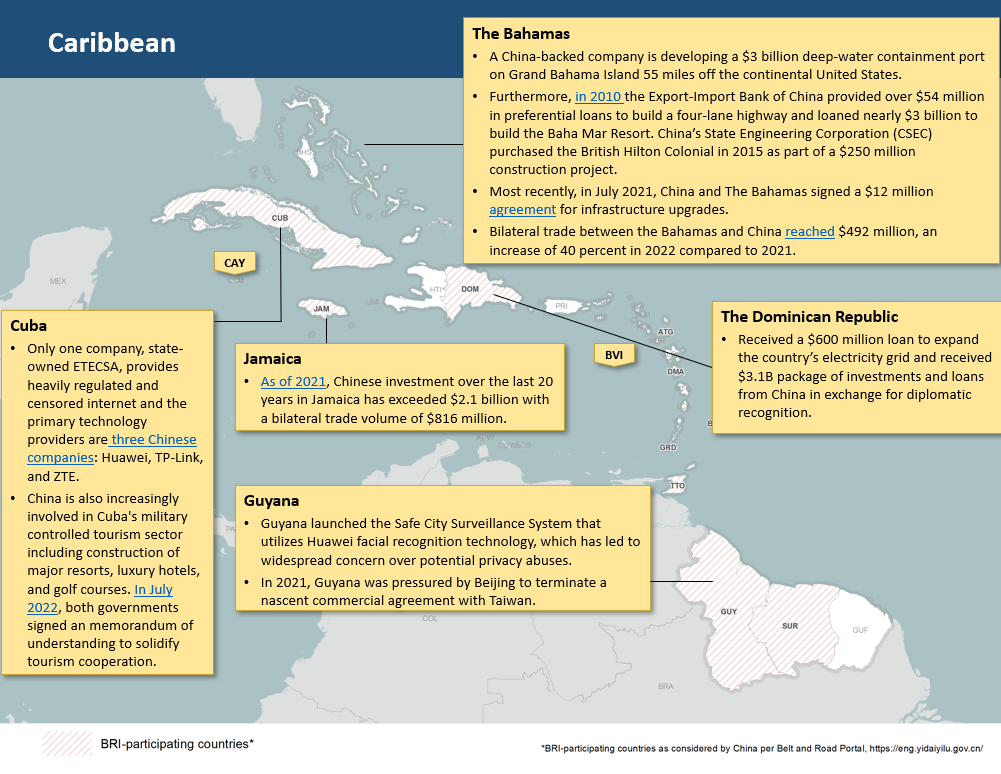
China’s Trade and Economic Investment in the Caribbean
While the Caribbean’s trade with China has grown at a slower pace than overall trade with the region, it increased from $1 billion in 2002 to $8 billion in 2019, with an estimated $6.1 billion in Chinese exports and $1.9 billion in imports.
China is a major trading partner of Cuba’s and Chinese businesses are involved in the Cuba’s telecommunications, tourism, mining, and energy sectors.
Cuba is highly dependent on China and ongoing economic challenges resulted in the reconstructing of an estimated $4 billion in debt to China in 2011 and another restructuring in 2015. For more reading click here.






 .
. 
