Hey, look over there –>
WikiLeaks Reveals ‘AfterMidnight’ & ‘Assassin’ CIA Windows Malware Frameworks
When the world was dealing with the threat of the self-spreading WannaCry ransomware, WikiLeaks released a new batch of CIA Vault 7 leaks, detailing two apparent CIA malware frameworks for the Microsoft Windows platform. Dubbed “AfterMidnight” and “Assassin,” both malware programs are designed to monitor and report back actions on the infected remote host computer running the Windows operating system and execute malicious actions specified by the CIA. Since March, WikiLeaks has published hundreds of thousands of documents and secret hacking tools that the group claims came from the US Central Intelligence Agency (CIA). This latest batch is the 8th release in the whistleblowing organization’s ‘Vault 7’ series.
‘AfterMidnight’ Malware Framework
According to a statement from WikiLeaks, ‘AfterMidnight’ allows its operators to dynamically load and execute malicious payload on a target system. The main controller of the malicious payload, disguised as a self-persisting Windows Dynamic-Link Library (DLL) file and executes “Gremlins” – small payloads that remain hidden on the target machine by subverting the functionality of targeted software, surveying the target, or providing services for other gremlins. Once installed on a target machine, AfterMidnight uses an HTTPS-based Listening Post (LP) system called “Octopus” to check for any schedu led events. If found one, the malware framework downloads and stores all required components before loading all new gremlins in the memory. According to a user guide provided in the latest leak, local storage related to AfterMidnight is encrypted with a key which is not stored on the target machine. A special payload, called “AlphaGremlin,” contains a custom script language which even allows operators to schedule custom tasks to be executed on the targeted system. More detail here.
Meanwhile….
North Korean hacking group is thought to be behind cyber attack which wreaked havoc across the globe
Technical clues suggest North Korean hacking group is behind cyber attack
Ransomware left the NHS crippled with operations cancelled over the weekend
The virus is now thought to have been released by the Lazarus Group
It has already been blamed for a string of hacks dating back to at least 2009
It includes the 2014 attack on Sony that left its network offline for weeks
Okay maybe….while other IT cyber professionals point to Russian thug hackers….
Rex Tillerson last month spoke about a quasi red line with North Korea….when is enough, enough? Well his answer was, ‘we will know it when we see it’.
Nonetheless, what more needs to be known about North Korea that the media is not reporting? Plenty…..
‘Unrestricted Warfare’ (超限战, literally “warfare beyond bounds”) is a book on military strategy written in 1999 by two colonels in the People’s Liberation Army, Qiao Liang (乔良) and Wang Xiangsui (王湘穗). Its primary concern is how a nation such as China can defeat a technologically superior opponent (such as the United States) through a variety of means. Rather than focusing on direct military confrontation, this book instead examines a variety of other means. Such means include using International Law (see Lawfare) and a variety of economic means to place one’s opponent in a bad position and circumvent the need for direct military action.[1] Go here for more information.
This already tells us and the Pentagon, to not trust China….right? So how can we place trust and the burden of dealing with North Korea on Beijing? We cant.
The RGB is the KGB….
The RGB is the North Korean Reconnaissance General Bureau….much like that of the KGB, now in Russia known as the FSB.
In 2015, North Korea spies infiltrated the United Nations agencies including the World Food Program which is a major supplier of food aid to North Korea. Somehow, the Obama White House and other government agencies neglected to take real action on that or even earnestly report it. Prior to that little event, in 2010, the U.S. Treasury via and Obama Executive Order targeted North Korea for proliferation and other illicit activities including arms trafficking, money laundering and smuggling narcotics.
Barack Obama, simply annexed a GW Bush Executive Order adding a few new items noted below:
President Obama also identified the following entities and individual for sanctions by listing them on the Annex to the Order:
· The Reconnaissance General Bureau (RGB), North Korea’s premiere intelligence organization involved in North Korea’s conventional arms trade;
· RGB commander Lieutenant General Kim Yong Chol;
· Green Pine Associated Corporation, a North Korean conventional arms dealer subordinated to the control of the RGB; and
· Office 39 of the Korean Workers’ Party, which provides critical support to North Korean leadership in part through engaging in illicit economic activities and managing the leadership’s slush funds.
The U.S. government has longstanding concerns regarding North Korea’s involvement in a range of illicit activities conducted through government agencies and associated front companies. North Korea’s nuclear and missile proliferation activity and other illicit conduct violate UN Security Council Resolutions 1718 and 1874, and these activities and their other illicit conduct violate international norms and destabilize the Korean Peninsula and the entire region. In signing this Order, President Obama has frozen the property and interests in property of the three entities and one individual listed on the Annex. This Order provides the United States with new tools to disrupt illicit economic activity conducted by North Korea.
As a matter of note, in recent days, Russia has stepped in to offer some diplomatic assistance dealing with North Korea as it appears China is dragging the diplomatic and political anchor dealing with the DPRK. Ah Russia again right? The in depth study is here on North Korea, It includes, history, terror attacks, cyber attacks, assassination attempts, raids and details on unrestricted warfare.
Just for some context, Russia and China have been aiding North Korea for decades…..but has the media done their work to expose this or the State Department? Nope…
You see, General O Kuk ryol and Kim Jong Un both manage Unit 121. Unit 121, is part of the RGB and did the Sony hack, remember that? Well General O, is a graduate of the Mangyongdae Revolutionary School and the Kim Il sung University….but most importantly, he graduated also from Frunze Military Academy in 1962….where is that? Ah….Moscow, and at the time, it was the Soviet Union.

Strategy: Integrate their cyber forces into an overall battle strategy as part of a combined arms campaign. Additionally they wish to use cyber weapons as a limited non-war time method to project their power and influence.
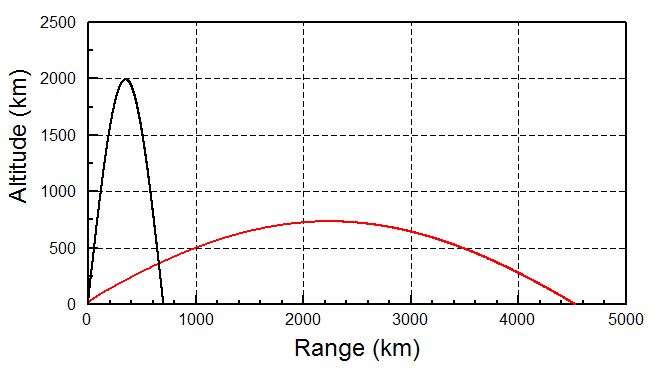
Experience: Hacked into the South Korea and caused substantial damage; hacked into the U.S. Defense Department Systems. More here.
Meanwhile, we also have the Korea Computer Center…there are 9 production facilities and 11 regional centers. However, the KCC also has offices in China, Germany and Syria..further it should be noted that an estimated 10,000 North Korean IT developers operate in China, where it is common that $500.00 of their monthly salary goes back to the North Korean state.
So, we have Syria, Russia, China all colluding with North Korea….Iran is as well but the United Nations too? Yup…
FNC: For more than a year, a United Nations agency in Geneva has been helping North Korea prepare an international patent application for production of sodium cyanide — a chemical used to make the nerve gas Tabun — which has been on a list of materials banned from shipment to that country by the U.N. Security Council since 2006.
The World Intellectual Property Organization, or WIPO, has made no mention of the application to the Security Council committee monitoring North Korea sanctions, nor to the U.N. Panel of Experts that reports sanctions violations to the committee, even while concerns about North Korean weapons of mass destruction, and the willingness to use them, have been on a steep upward spiral.
Fox News told both U.N. bodies of the patent application for the first time late last week, after examining the application file on a publicly available WIPO internal website.
Information on the website indicates that North Korea started the international patent process on Nov. 1, 2015 — about two months before its fourth illegal nuclear test. The most recent document on the website is a “status report,” dated May 14, 2017 (and replacing a previous status report of May 8), declaring the North Korean applicants’ fitness “to apply for and be granted a patent.”
CLICK HERE FOR THE STATUS REPORT
During all that time, however, the U.N.’s Panel of Experts on North Korea “has no record of any communication from WIPO to the Committee or the Panel regarding such a serious patent application,” said Hugh Griffiths, coordinator of the international U.N. expert team, in response to a Fox News question.
The Panel of Experts has now officially “opened an investigation into this matter,” he said.
“This is a disturbing development that should be of great concern to the U.S. administration and to Congress, as well as the U.S. Representative to the U.N.,” William Newcomb, a member of the U.N. Panel of Experts for nearly three years ending in 2014, told Fox News.
Said an expert familiar with the sanctions regime: “It undermines sanctions to have this going on. The U.N. agencies involved should have been much more alert to checking these programs out.”
Questions sent last week to the U.S. State Department about WIPO’s patent dealings with North Korea had not been answered before this story was published.
For its part, a WIPO spokesperson told Fox News by email, in response to the question of whether it had reported the patent application to the U.N. sanctions committee, only that the organization “has strict procedures in place to ensure that it fully complies with all requirements in relation to U.N. Security Council sanction regimes.”
The spokesperson added that “we communicate with the relevant U.N. oversight committees as necessary.”
But apparently, help with preparing international patent applications for a sanctioned nerve gas “chemical precursor” does not necessarily count as grounds for such communication, if the Panel of Experts records are correct.
This is by no means the first time that WIPO, led by its controversial director general, Francis Gurry, has flabbergasted other parts of the U.N. and most Western nations with its casual and undeclared assistance, with potential WMD implications, to the bellicose and unstable North Korean regime.
And, as before, how the action is judged may depend upon razor-thin, legalistic interpretations of U.N. sanctions law on the one side vs. staggering violations of, at a minimum, common sense in dealing with the unstable North Korean regime, which among other things has never signed the international convention banning the development, production, stockpiling and use of chemical weapons.
While the patent process went on at WIPO, that regime has conducted five illegal nuclear tests — two in the past year, while the patent process was under way — and at least ten illegal ballistic missile launches since 2016, while issuing countless threats of mass destruction against its neighbors and the U.S.
In 2012, Fox News reported that WIPO had shipped U.S.-made computers and sophisticated computer servers to North Korea, and also to Iran, without informing sanctions committee officials.
The shipments were ostensibly part of a routine technology upgrade. Neither country could obtain the equipment on the open market, and much of it would have required special export licenses if shipped from the U.S.
The report kicked off an uproar, but after a lengthy investigation, the U.N. sanctions committee decided that the world organization’s porous restrictions had not been violated, while also noting WIPO’s defense that as an international organization, it was not subject to the rules aimed at its own member states.
Nonetheless, the investigators declared that “we simply cannot fathom how WIPO could have convinced itself that most Member States would support the delivery of equipment to countries whose behavior was so egregious it forced the international community to impose embargoes.”
The investigators also declared that “WIPO, as a U.N. agency, shares the obligation to support the work of other U.N. bodies, including the Sanctions Committees,” and that in response to the furor, WIPO had “implemented new requirements to check on sanctions compliance in advance of program implementation.”
There is no doubt about the banned nature of sodium cyanide — which can also be used to produce deadly cyanide gas, another weapon of mass destruction.
The chemical appears on a Security Council list of “items, materials, equipment, goods and technology” related to North Korea’s “other weapons of mass destruction programs” beyond nuclear weapons, which first appeared after U.N. Security Council resolution 1718 was approved in 2006.
That resolution, voted after North Korea conducted its first nuclear test, ordained that member states “prevent the direct or indirect supply, sale or transfer” to the regime known as the Democratic People’s Republic of Korea, or DPRK, of the listed items “which could contribute to DPRK’s nuclear-related, ballistic missile-related or other weapons of mass destruction-related programs.”
It also declared that “all member states shall prevent any transfers to the DPRK by their nationals or from their territories, or from the DPRK by its nationals or from its territory, of technical training, advice, services or assistance related to the provision, manufacture, maintenance or use of the items” listed.
Additionally, it demanded a freeze by U.N. member states or all “funds, other financial assets and economic resources” that could be used in the mass destruction-related programs.
CLICK HERE FOR RESOLUTION 1718
A subsequent Security Council resolution, 2270, in 2016 broadened things by declaring that “economic resources” referred to in Resolution 1718 “includes assets of every kind, whether tangible or intangible, movable or immovable, accrual or potential, which potentially may be used to obtain funds, goods or services” by DPRK.
This may open up another controversial aspect of the cyanide patent application, since, along with its mass-destructive uses, the chemical is considered the most common agent in the extraction of gold from ores and concentrates.
Further, according to the North Korean application to WIPO, the new process it wants to make ready for international patenting is a lower-cost process that produces ultra-high-grade product.
CLICK HERE FOR THE PROCESS APPLICATION DESCRIPTION
In WIPO’s response to Fox News, the agency’s spokesperson emphasized that “WIPO is not a patent-granting authority. Its role in handling these applications is to ensure that they conform to the procedural requirements” of the 152-member Patent Cooperation Treaty, or PCT, “and to publish them in accordance with the provisions of the treaty.” North Korea is a PCT signatory.
Translation: WIPO is merely a neutral, technical pass-through mechanism. As the spokesperson put it: “The decisions concerning whether or not to ultimately grant the patent are the sole purview of each jurisdiction where protection is being sought, in accordance with national law.”
While that may be true, it is also true, according to the WIPO website, that the U.N. agency gives those who use its services a lot of financially meaningful help.
That starts with the fact that by filing an international filing application with the agency, you have to pay only one fee rather than more than 150 to get an application acceptable in all PCT countries (which include the U.S. as one of the treaty’s biggest users).
WIPO also provides one-stop research on whether a patent overlaps with those elsewhere, and offers the possibility of widespread dissemination and publicity — i.e., stimulating demand, and thus at least the potential for sanctions-breaking in any subsequent licensing the North Korean patent.
Igniting controversy has been a characteristic of Director General Gurry’s reign — indeed, even before he first took WIPO’s top executive office in 2008.
In 2015, the U.N.’s watchdog Office of Internal Oversight Services (OIOS) was asked by WIPO’s own General Assembly chair to investigate Gurry for allegedly ordering, in 2008, break-ins of the offices of staffers to seek DNA evidence that they wrote anonymous letters against him. Gurry was WIPO’s No. 2 at the time.
A year later, after much byzantine maneuvering, a heavily redacted version of the report declared that “while there were indications that Mr. Gurry had a direct interest in the outcome of the DNA analysis, there is no evidence that he was involved in the taking of DNA samples.”
But the same document also found that Gurry had bent the organization’s rules and steered a sensitive cyber-security contract to a business acquaintance, , something alleged by one of Gurry’s former top deputies, James Pooley.
Under Gurry, WIPO also has been the only U.N. agency ever sanctioned by the U.S. State Department, on the grounds that it failed to adopt “best practices” in ethics and whistle-blower standards — a punishment first meted out by the pro-U.N. Obama administration in September 2015.
Among the whistle-blowers who say they were forced to leave WIPO during Gurry’s tenure for drawing attention to the agency’s previous computer shipments to North Korea is Miranda Brown, formerly Gurry’s senior strategic advisor.
Brown has repeatedly asked for her reinstatement at the WIPO, and just as often has been turned down by Gurry’s office.

 C
C

 Adm. Harry Harris, head of the U.S. Pacific Command, addresses the Lowy Institute think tank in Sydney last December. | AFP-JIJI
Adm. Harry Harris, head of the U.S. Pacific Command, addresses the Lowy Institute think tank in Sydney last December. | AFP-JIJI