The intrusions at the DNC are noteworthy for the sophistication of the groups behind it. One of the intrusions, by a well-known cyberespionage group called Cozy Bear, appears to have happened in the summer of 2015, according to Crowdstrike‘s CTO and co-founder Dmitri Alperovitch. The second breach, involving another Russian group, Fancy Bear, happened in April this year.
Cozy Bear has been previously associated with attacks on the White House and the US. State Department. The group has also been tied to numerous attacks on US defense contractors, government agencies, financial services companies, technology firms and think tanks, Alperovich said. Fancy Bear, or Sofacy, as the group is also known, is similarly believed responsible for targeted attacks on various government and private sector organizations in multiple countries including the US, Canada, China and Japan, he said.
The two groups did not appear to be collaborating with each other or communicating in any fashion on the DNC attacks. But both targeted the same systems and the same data, employing a variety of sophisticated techniques in the process Crowdstrike’s CTO and co-founder Dmitri Alperovitch said in a blog post.
The Cozy Bear team used a Python-based malware tool dubbed SeaDaddy and another backdoor in Powershell to gain persistence on comprised DNC systems and to remain undetected on them for more than a year. According to Alperovitch, the Powershell backdoor was noteworthy for its use of a one-line command to establish an encrypted connection with command and control servers and for downloading additional modules.
The Fancy Bear group meanwhile used a different malware sample to remotely execute malicious commands on compromised DNC systems, to transmit files and to enable keylogging. The group deployed tactics like periodically clearing event logs and resetting the timestamps in files in an attempt to conceal their activities. More details here from DarkReading.
Gawker: A 200+ page document that appears to be a Democratic anti-Trump playbook compiled by the Democratic National Committee has leaked online following this week’s report that the DNC was breached by Russian hackers. In it, Trump is pilloried as a “bad businessman” and “misogynist in chief.”
The document—which according to embedded metadata was created by a Democratic strategist named Warren Flood—was created on December 19th, 2015, and forwarded to us by an individual calling himself “Guccifer 2.0,” a reference to the notorious, now-imprisoned Romanian hacker who hacked various American political figures in 2013.
The package forwarded to us also contained a variety of donor registries and other strategy files, “just a few docs from many thousands I extracted when hacking into DNC’s network,” the purported hacker claimed over email, adding that he’s in possession of “about 100 Gb of data including financial reports, donors’ lists, election programs, action plans against Republicans, personal mails, etc.”
His stated motive is to be “a fighter against all those illuminati that captured our world.”

The enormous opposition document, titled simply “Donald Trump Report,” appears to be a summary of the Democratic Party’s strategy for delegitimizing and undermining Trump’s presidential aspirations—at least as they existed at the end of last year, well before he unseated a field of establishment Republicans and clinched the nomination. A section titled “Top Narratives” describes a seven-pronged attack on Trump’s character and record.

The first is the argument that “Trump has no core”:
One thing is clear about Donald Trump, there is only one person he has ever looked out for and that’s himself. Whether it’s American workers, the Republican Party, or his wives, Trump’s only fidelity has been to himself and with that he has shown that he has no problem lying to the American people. Trump will say anything and do anything to get what he wants without regard for those he harms.
Second, that Trump is running a “divisive and offensive campaign”:
There’s no nice way of saying it – Donald Trump is running a campaign built on fear-mongering, divisiveness, and racism. His major policy announcements have included banning all Muslims from entering the U.S., and calling Mexican immigrants “rapists” and “drug dealers” while proposing a U.S.-Mexico border wall. And Trump’s campaign rallies have become a reflection of the hateful tone of his campaign, with protestors being roughed up and audience members loudly calling for violence.
Third, Trump is a “bad businessman”:
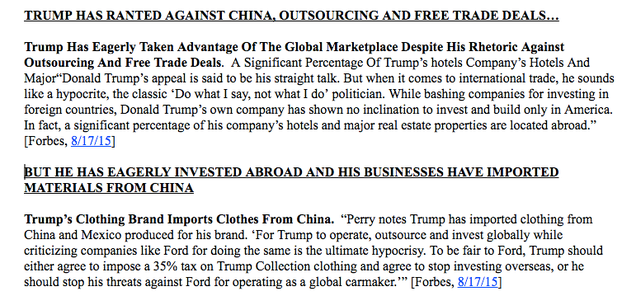
Despite Trump’s continual boasting about his business success, he has repeatedly run into serious financial crises in his career and his record raises serious questions about whether he is qualified to manage the fiscal challenges facing this country. Trump’s business resume includes a long list of troubling issues, including his company’s record of forcing people from their homes to make room for developments and outsourcing the manufacturing of his clothing line to take advantage of lower-wage countries like China and Mexico. His insight about the marketplace has proven wrong many times, including in the run-up to the Great Recession. And Trump’s record of irresponsible and reckless borrowing to build his empire – behavior that sent his companies into bankruptcy four times – is just one indication of how out-of-touch he is with the way regular Americans behave and make a living, and it casts doubt on whether he has the right mindset to tackle the country’s budget problems.
Fourth, Trump espouses “dangerous & irresponsible policies”:
Trump’s policies – if you can call them that – are marked by the same extreme and irresponsible thinking that shape his campaign speeches. There is no question that Donald Trump’s rhetoric is dangerous – but his actual agenda could be a catastrophe.
Fifth, in classically corny Democratic Party style, Donald Trump is the “misogynist in chief”:
Through both his words and actions, Trump has made clear he thinks women’s primary role is to please men. Trump’s derogatory and degrading comments to and about women, as well as his tumultuous marriages, have been well publicized. And as a presidential candidate, Trump has adopted many of the backwards GOP policies that we’ve come to expect from his party.
Sixth, Donald Trump is an “out of touch” member of the elite:
Trump’s policies clearly reflect his life as a 1-percenter. His plans would slash taxes for the rich and corporations while shifting more of the burden to the shoulders of working families. He stands with Republicans in opposing Wall Street reform and opposing the minimum wage. Trump clearly has no conception of the everyday lives of middle class Americans. His description of the “small” $1 million loan that his father gave him to launch his career is proof enough that his worldview is not grounded in reality.
The seventh strategy prong is to focus on Trump’s “personal life,” including that “Trump’s Ex-Wife Accused Him Of Rape,” which is true.
What follows is roughly two hundred pages of dossier-style background information, instances of Trump dramatically changing his stance on a litany of issues, and a round-up of the candidate’s most inflammatory and false statements (as of December ‘15, at least).
It appears that virtually all of the claims are derived from published sources, as opposed to independent investigations or mere rumor. It’s also very light on anything that could be considered “dirt,” although Trump’s colorful marital history is covered extensively:

The DNC hack was first revealed Tuesday, when the cybersecurity firm CrowdStrike announced it had discovered two hacking collectives, linked to Russian intelligence, inside the DNC network after the DNC reported a suspected breach. In a blog post, the company identified the groups as “COZY BEAR” and “FANCY BEAR”—two “sophisticated adversaries” that “engage in extensive political and economic espionage for the benefit of the government of the Russian Federation.”
The hackers were able to access opposition files and may have been able to read email and chat traffic, but did not touch any financial, donor, or personal information, the DNC said Tuesday. However, the user who sent the files to Gawker refuted that claim, writing, “DNC chairwoman Debbie Wasserman Schultz said no financial documents were compromised. Nonsense! Just look through the Democratic Party lists of donors! They say there were no secret docs! Lies again! Also I have some secret documents from Hillary’s PC she worked with as the Secretary of State.”
Among the files sent to Gawker are what appear to be several lists of donors, including email addresses and donation amounts, grouped by wealth and specific fundraising events. Gawker has not yet been able to verify that the Trump file was produced by the DNC, but we have been able to independently verify that the financial documents were produced by people or groups affiliated with the Democratic Party.
Also included are memos marked “confidential” and “secret” that appear to date back to 2008, and pertain to Obama’s transition into the White House, and a file marked “confidential” containing Hillary’s early talking points, at least some of which ended up being repeated verbatim in her April, 2015 candidacy announcement.
Finally, there is a May, 2015 memo outlining a proposed strategy against the field of potential GOP candidates. Donald Trump, who had not yet officially announced his candidacy, does not appear in the document.
The purported hacker writes “it was easy, very easy” to hack and extract thousands of files from the DNC network, “the main part” of which he or she claims are in the custody of Wikileaks. He or she also appears to have sent the documents to The Smoking Gun, which posted about the dossier earlier today.
Warren Flood did not immediately return a request for comment. DNC Press Secretary Mark Paustenbach was not able to immediately confirm the authenticity of the documents, but the party is aware that they’re circulating.

