On 21 May, Cohen received another letter from Wolfe saying that Cohen had to make a deposition regarding the check. It followed from the letter that Cohen had already refused to make a deposition voluntarily so he had to be summoned to court:
On June 6, 2007, the deposition was scheduled for 3 August at 1350 Broadway, Suite 1407, New York. Cohen was requested to produce the following documents:
Cohen delayed the deposition as much as possible resorting to various tricks. Eventually, he had to appear before the court on September 17, 2007 at the said address in New York. He testified by phone.
However, Cohen did not produce any records or documents and was very laconic answering the questions. He recognized having received a check for $350,000 from Malakhov in January 1999 and confirmed that he had clients from Russia in 1998-1999, but he indicated that he didn’t go to Russia during that period and, to the best of his knowledge, did not send money to Russia or Ukraine from his accounts. Below is Cohen’s testimony, partially abridged:
QUESTION: You are appearing here today as the result of a subpoena duces tecum which was served on you; is that correct?
ANSWER: Correct.
QUESTION: Exhibit A to the subpoena duces tecum requested four categories of documents for you to locate; is that correct?
ANSWER: That’s correct.
QUESTION: Did you perform a diligent search for those documents?
ANSWER: I did.
QUESTION: Did you locate any documents responsive to that subpoena?
ANSWER: No. […]
QUESTION: Can you tell me what type of law your practice included or what types of law your practice included in 1999?
ANSWER: My practice was 90 percent negligence with 10 percent defense. I was also in the Yellow Cab industry. It was defense of the Yellow Cabs that we were operating at the time, and property damage. […]
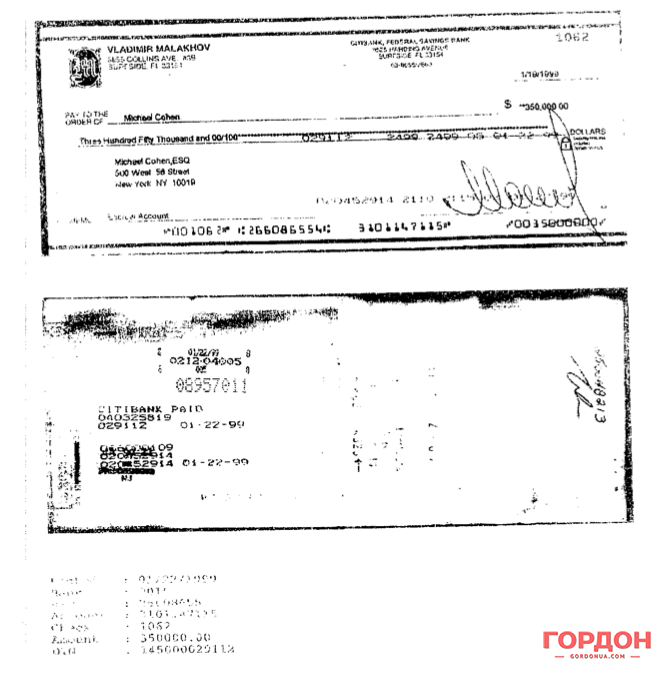
QUESTION: Mr. Cohen, we provided you with a copy of a check that was written in January of 1999 to you by Vladmir Malakhov. Do you have that check?
ANSWER: I do. […]
QUESTION: Mr. Cohen, do you recall receiving this check in 1999?
ANSWER: No.
QUESTION: The search that we discussed earlier, the documents requested on the subpoena duces tecum that was provided for you would have included records relevant to this check. I would like you to confirm that you, therefore, have been able to locate no records that are relevant to this check or related to this check?
ANSWER: Correct.
QUESTION: That would include any records of that check that had been deposited by you or anything else that you might have done with it?
ANSWER: Correct. […]
QUESTION: Mr. Cohen, do you recognize the signature on the check?
ANSWER: No.
QUESTION: You cannot say whether that is or is not your signature?
ANSWER: You asked me the signature. There are two signatures on this check.
QUESTION: I apologize. There is a signature that is the signature of the maker of the check on the front and there is also an endorsing signature on the back. Do you recognize that endorsing signature as your signature?
ANSWER: Yes. It could be.
QUESTION: You are not certain whether it is or not?
ANSWER: I don’t know but it could be.
QUESTION: Let me ask you, have you maintained proper records for your trust account at all times since being admitted to the New York bar?
ANSWER: I do. […]
QUESTION: Mr. Cohen, let me ask you what are some of the possible reasons that somebody would have sent a check to your trust account in 1999.
ANSWER: I have no idea. […]
QUESTION: You have no idea why somebody would send a check to your trust account?
ANSWER: I don’t know what this is about. It is from 1999. I have no recollection.
QUESTION: What would the possible reasons have been for your receiving a check addressed to your trust account in 1999? […] Is there any place else, anything else that a check written to your trust account could have represented?
ANSWER: At the time in 1999 I was acting counsel for a fund called the Ukrainian Capital Growth Fund which was also located at this address. […] Other than that, no. I don’t believe anything else.
QUESTION: Is it your testimony that it is possible that a check written to your trust account could have been written for the purpose of being deposited in the Ukrainian Growth Fund?
ANSWER: It is possible.
QUESTION: Did your law practice in 1999 include any other persons including partners, associates or employees?
ANSWER: No.
QUESTION: Other than the Ukrainian Growth Fund were you involved in 1999 in any other business besides the practice of law?
ANSWER: Yes.
QUESTION: What business was that?
ANSWER: The taxicab business in New York City.
QUESTION: That was separate from your practice of law?
ANSWER: Correct. It was — it was operated out of the same building.
QUESTION: What was your responsibility regarding the taxicab business?
ANSWER: I was a principal.
QUESTION: What did the business do?
ANSWER: Operated 260 Yellow Cabs in the City of New York.
QUESTION: I see. Could this check have been in any way related to that business?
ANSWER: […] Yes, it is possible.
QUESTION: Were there other people involved in the taxicab business? […]
ANSWER: Yes.
QUESTION: Who are those people?
ANSWER: I had only one partner. Simon Garber. […]
QUESTION: Did you ever go to Moscow in 1999?
ANSWER: No.
QUESTION: Did you go to Russia in 1999?
ANSWER: No.
QUESTION: Have you ever been to Russia or the Ukraine?
ANSWER: Yes.
QUESTION: Did you go in 1998?
ANSWER: No. […]
QUESTION: Do you recall if you had any Russian clients […]?
ANSWER: Yes.
QUESTION: In 1998 or 1999?
ANSWER: Did I have Russian clients?
QUESTION: Yes.
ANSWER: The answer — this would also include my negligence practice?
QUESTION: Yes. Russian clients, yes, sir.
ANSWER: The answer would be, yes.
QUESTION: Did there come times when you would have to send money in negligence cases or whatever cases to your clients in Russia outside the United States?
ANSWER: No.
QUESTION: Your testimony is you never wired any funds or sent any funds outside of the United States out of your trust account to Russian clients?
ANSWER: Correct.
QUESTION: […] Do you know why this check, number 1062 […] is made to the order of Michael Cohen as opposed to your law firm?
ANSWER: I don’t.
QUESTION: What does that say in the memo? Can you read that in the memo of that check?
ANSWER: It says, “Escrow account.”
QUESTION: Did you have escrow accounts for any sorts of clients in that time?
ANSWER: No.
QUESTION: Are trust accounts sometimes called escrow accounts in New York?
ANSWER: Yes.
QUESTION: Do you have any reason to believe that this was not deposited into your escrow account or your trust account?
ANSWER: I don’t understand your question.
QUESTION: This was deposited, according to the back of the check, into your trust account; is that right?
ANSWER: Correct.
QUESTION: Do you remember a negligence case or any sort of case involving Vladmir Malakhov?
ANSWER: No.
QUESTION: Your testimony is that you don’t know why a Vladmir Malakhov would write you a check for $350,000 in January of 1999?
ANSWER: I don’t recall why.
QUESTION: The Ukrainian Capital Growth Fund, were those funds commingled with your trust account at your law firm? […]
ANSWER: I do not believe we ever deposited any checks into my escrow account for Ukrainian Capital Growth Fund. It had its own account. […]
QUESTION: Again, does the name Vladmir Malakhov, it doesn’t ring a bell I believe you said earlier?
ANSWER: No.
QUESTION: Mr. Cohen, you indicated that […] you never sent any money outside of the United States to Russia or anywhere else; is that correct?
ANSWER: That would be correct. To the best of my knowledge that is correct.
QUESTION: […] Is it a correct statement that you never in any capacity sent money from one of your business accounts to Russia or the Ukraine?
ANSWER: In what year are we talking?
QUESTION: We are talking around the 1999 time; let’s say, between 1998 and 2000, just to be safe.
ANSWER: I would say, no.
QUESTION: Okay. Again, to just clarify, you testified that money that was deposited into your trust account could conceivably have gone to one of the other types of businesses or one of the other businesses that you were involved with; is that correct?
ANSWER: That is correct. […] It is correct to the extent I don’t recall this transaction.
QUESTION: Right. I am saying hypothetically, given what you know of your practice at the time or what you can recall of your practice at the time, that this is something that could have happened to money that went into your trust account, it could have gone to one of these other businesses that you told us about?
ANSWER: It could have.
QUESTION: Okay. I am also correct in understanding that you do not have any records at all with regard to the other accounts […]?
ANSWER: That is correct.
QUESTION: Do you keep lists of clients per year on your computer, like a client list, something like that, a data base?
ANSWER: I did have, yes.
QUESTION: Would you have a list of clients from, let’s say, 1998 and 1999?
ANSWER: No, sir.
QUESTION: […] You don’t know either why this check was sent to you and where these funds went ultimately out of your trust account; is that a fair statement, sir?
ANSWER: One more time please.
QUESTION: You don’t recall — this is kind of a summary question. You don’t recall why this check was written to you for $350,000 in 1999 and how these funds left your trust account in any way, shape or form?
ANSWER: Clearly Vladmir Malakhov had to have known somebody who I was affiliated to and the only person I can — and I mentioned my partner’s name, Simon Garber, who happens to also be Russian.[…] Somewhere along the line I was asked to hold somebody’s funds for whatever the purpose was, whether it was A, B or C, I don’t know the reasons and I can’t even begin to guess. […] I would probably — the only way I would have received any funds, whether it is $35 or $350,000, is I would have had to have received the same type of instructions from the same person who wrote the check in order to disburse the funds, otherwise, I would have sent it back to the writer. […] That is how I operated my account.
QUESTION: Did you ever ask your partner Simon about this check before this deposition?
ANSWER: I did not. […] Simon Garber is not an attorney. He is my partner in the taxi industry.
QUESTION: Is he still your partner or are you out of the taxi industry now?
ANSWER: I am out of the taxi industry.
QUESTION: Mr. Cohen, real quick. What was the name of the cab business that you were involved with in 1999?
ANSWER: Manhattan Maintenance, Inc.
QUESTION: […] There was no connection between your trust account and the taxicab company; you kept those accounts separate?
ANSWER: Absolutely.
***
As a result of Cohen’s examination, the court concluded as follows:
“Michael Cohen – the payee on the check — repeatedly stated that he has no personal knowledge and no records of any check of $350,000.00 made out to him or to his trust account in 1999. Mr. Cohen is also entirely unaware of the identity of any of the parties or other witnesses in this lawsuit. Mr. Cohen reiterated multiple times that he does not know Defendant Malakhov and does not understand why he would receive a $350,000.00 check from Defendant Malakhov”.
In other words, Cohen refused to share any details of the transaction claiming that he did not know why he had been sent a check for $350,000; he did not remember how he used this money and did not remember who they were intended for and what happened to this $350,000; he was not familiar with and had never contacted Vladimir Malakhov, who wrote the check, though he would normally not have accepted (but did accept) a check for $350,000 from a stranger and would have returned (but did not return) it to the writer.
We will help Mr. Cohen recall what happened to the check for $350,000 back in 1999, who this money belonged to, and what happened to it then, relying on testimony of Mr. Cohen himself, who relaxed at the end of the examination and said,
“The only way I would have received any funds, whether it is $35 or $350,000, is I would have had to have received the same type of instructions from the same person who wrote the check in order to disburse the fund”.
Cohen’s only inaccuracy was that the person who gave him instructions regarding the disbursement of the funds was not the same person who wrote the check, it was not Malakhov.
$350,000 transferred to Michael Cohen was intended for one of the leaders of the Izmaylovskaya Organized Crime Group (OCG) Vitaly Yuryevich Buslaev nicknamed Buslay (born in 1965). The police records of 1996 describe him as follows:
“The group has one leader – Oleg Ivanov, 55 years old, born in Kazan. However, the Izmaylovskaya OCG is not governed by leaders, as in other groups, but rather by “kingpins”. There were five of them – Victor Nestruev (“Boy”), Sergey Trofimov (“Trofim”), Vitaly Buslaev (“Buslay”), Anton Malevsky (“Anton”), and Aleksandr Derbyshev. Anton Malevsky was the most famous. It was partly because he had been detained by the police with arms several times, but he managed to evade responsibility. Some sources interpret it in such a way that Anton was taken “under the wing” of special services and started cooperating with them”.
Buslaev lived in Moscow. In the early 2000s, he worked for Private Security Company Vityaz-AK, which is often a legal disguise of criminal activities. At the same time, Buslaev was the director general of three companies: OOO (limited liability company) Bazagaza, ООО Dormidont Rielt, and OOO Legenda Project Group. In turn, Legenda Project Group owned ООО Great Hotel Moscow and ООО Great Hotel Suzdal. Great Hotel Moscow lies 200 meters from the Kremlin Troitskaya Tower. The hotel overlooks the Kremlin, and the territory of the hotel is guarded by the Federal Security Service of the Russian Federation. The owners of Legenda Project Group got the hotel from a confidant of the Rotenberg brothers, who are close to Putin. A partner of Legenda Project Group was the owner of Metropol Hotel Mikhail Slipenchuk, a billionaire and a member of the State Duma of the Russian Federation in 2011-2016, who has co-owned Great Hotel Moscow and Great Hotel Suzdal since 2015.

Veliy Hotel in Moscow located at 10 Mokhovaya Street. Фото: maps.google.com
Buslaev’s name was also mentioned in relation to the murder of the journalist Georgiy Gongadze in Ukraine. However, apart from a mention of Buslaev’s name as a mastermind of the murder in a phone conversation, there has been no more evidence of his complicity in the crime and no new information has become available ever since.
Within Buslaev’s current activity, very much is linked to big business in Russia, big Russian businessmen and the Rotenberg brothers, Putin’s partners. However, back in 1996, Buslaev was only in the beginning of his way to the top. The money he wanted to spend on buying property in the USA – it’s hard to judge whether legal or illegal because any money in Russia was illegal then – belonged to Buslaev. In January that year, he came to Miami with his 22-year-old girlfriend Yulia Fomina and found property in the building at 16711 Collins Avenue, Miami Beach, Florida, which he bought a bit later for $473,900 in cash. The payments were made in 1996 in three instalments: $96,000 on 18 February, $48,000 on 18 April, and the rest $329,000 on 29 November, including $324,040.64 that was transferred to the account of Florida building owners by telex.

Boris and Arkady Rotenberg, Russian businessmen, who, according to the mass media, are Russian President Vladimir Putin’s close friends. Фото: EPA
Actually, the apartment had not been built yet. The multi-story building was under construction, but it was already advertised in Moscow. Many of Buslaev’s and Fomina’s friends bought uncompleted apartments in that building. In February 1996, Buslaev and Fomina returned to Moscow. According to Yulia, they had an accident then. Fomina was seriously injured because she went out of the car after the accident and was run down by a passing car. She spent almost a month in hospital. Buslaev was not injured. In March, Buslaev and Fomina came to the USA again and spent there five months until September 1996. It seems that Buslaev was hiding from something, which is why he stayed in the USA for so long.
Fomina came to the USA for the third time by herself around October 1996. Buslaev remained in Russia. The completed apartment in Florida was bought by him in the very end of November 1996, but Buslaev did not have a chance to live in it because he could not get an entry visa to the USA due to suspected connections with the Russian organized crime.
Yulia did not work in the U.S. and lived at the expense of Buslaev, who generously supported her. She had countless money. According to witnesses and Yulia herself, she lived a luxurious life. She had a two-car parking at her building in Miami. One car was an Aston Martin, and, as a rule, the other was a Mercedes. Yulia often went to Russia and Europe visiting, among others, Buslaev (according to her, they last met in 2004) and travelled in the USA. As Yulia testified on March 22, 2006, all her expenses were covered by “her friend” Aleksandr Varshavsky, Buslaev’s friend, a businessman working in car industry, with whom Buslaev had a system of mutual settlements. According to Yulia, Buslaev was also engaged in car industry. The relationships between Yulia Fomina and Varshavsky were so close that he became the only person whose phone number was indicated in the Emergency Resident Information.
According to Yulia’s testimony, she did not know how Buslaev transferred money to her because all her accounts and finances were managed by Varshavsky’s secretary Svetlana Gerus. All Yulia Fomina had to do was sign checks and not ask any questions. And she seems not to have been asking them.

The house at 16711 Collins Avenue, Miami Beach, commissioned in 1996. Фото: miamiresidence.com
Some years later, these questions were asked by the U.S. prosecutor’s office to Varshavsky himself. Varshavsky owned at least two car businesses in the USA (Avilon Group and New York Motors) and a Mercedes and Ford dealer network in Moscow. In December 2013, a court in New Jersey initiated criminal case against Varshavsky accusing him of income concealment and tax evasion in 2008-2012. The transactions that gave rise to American investigators’ suspicions included the transfer of $30 million from Russia to the U.S. account of New York Motors on March 18, 2008; transfer of $7.2 million from Russia to the account of Avilon Group in 2009 for the purchase of a Bombardier jet; transfer of $22 million to the account of the same company in 2010 after the sale of the jet. On September 22, 2010, another $5 million was transferred to Varshavsky’s account in the USA from Moscow.
In June 2011, Varshavsky bought an apartment in a luxurious skyscraper at 25 Columbus Circle in New York for $20.5 million in cash ($24.3 were transferred to the account of his New York company for real estate transactions European Realty). It appears that Buslaev and Fomina’s friend Aleksandr Varshavsky was dealing with big money.
But then, in late 1998, there came the August crisis in Russia and the instability of the ruble, which dropped several-fold, and Buslaev needed dollars so he decided to mortgage the property purchased in Yulia’s name and get $350,000 out of the property. On January 4, 1999, Yulia Fomina signed documents acknowledging the receipt of a $455,030 loan from Malakhov and the transfer of the Miami condo into the ownership of Lyudmila Malakhova (Vladimir Malakhov’s wife) as a security of the loan. On 11 January, the documents were forwarded by her attorney to Malakhov’s agent Paul Theofanous
On 19 January, Malakhov sent a check for $350,000 to the indicated address to the American lawyer Michael Cohen. According to several witnesses, including Theofanous, the rest of the money (approximately $105,000) was given by Malakhov to Yulia Fomina and Buslaev in cash, though the parties to the transaction – both on Fomina’s and on Malakhov’s side – avoided answering questions about the cash during the litigation. It is clear why: the transfer of large amounts of money in cash could constitute a violation of the American tax legislation though Malakhov honestly earned his money as a hockey player. According to his tax returns, he earned $18,465,346 between 1999 and 2004.
Having given $350,000 to Cohen for Buslaev and additional money in cash to Fomina, Malakhov fulfilled his obligations towards Buslaev. Buslaev’s apartment remained as a security, and it couldn’t disappear. But how could Buslaev in Moscow get the money transferred to Cohen in New York?
When Cohen testified in 2007 that he did not know Malakhov and did not transfer money to Russia he probably told the truth, though he left room for maneuver by saying “to the best of my knowledge”. Cohen’s money laundering scheme was different. Indeed, money did not leave the USA. Cohen received money to one of his accounts, confirmed its receipt, and then the owner of the money (Buslaev in this case) received $350,000 in Russia from a different person, who had to get $350.000 out of Russia. After Buslaev’s confirmation that the money was received in Russia, Cohen released $350,000 to American accounts indicated by the client in Moscow. As a result of this simple transaction, Buslaev received absolutely clean $350.000, most likely in cash; Cohen transferred absolutely clean $350.000 received from the hockey player Malakhov to some other American accounts, where this money further stayed absolutely clean because they had not crossed the border and never raised suspicions of the U.S. Internal Revenue Service and the FBI. Mostprobably, Cohen did all this for an interest because it is unlikely that he did this for free.
Since Cohen refused to provide the court with any records, statements or documents, it remains to be guessed what interest he earned from laundering money, as what Attorney Cohen did was classical money laundering.
It is hard to say how numerous Michael Cohen’s clientele was. There have been many Russian natives among his friends since long ago. It is neither good nor bad in itself. But a person, who has recently become the American president’s personal attorney, finds himself in a special situation because he is obliged to give answers to many natural questions posed by the public and the U.S. law enforcement agencies.
Michael Cohen married the Ukrainian citizen Laura Shusterman. Laura’s father, Fima Shusterman, was born in1945 and has property and investments in the USA. Michael himself once tried to set up business with ethanol (alcohol) in Ukraine but seemed to hand over this business to his brother Bryan. Bryan was also married to a citizen of Ukraine, Oksana Oronova. Bryan’s businesses include the production of ethanol in Ukraine. On March 2, 2017, Oksana Oronova’s 69-year-old father Aleksandr Oronov, who was involved in organizing a meeting between the Ukrainian deputy Artemenko and Michael Cohen concerning Artemenko’s peaceful plan, which was handed to Michael Flynn, the then National Security Advisor of President Trump, was found dead in New York.
Epilogue
Buslaev and Fomina did not return the 1999 debt to Malakhov, and the Malakhovs had to sell the mortgaged property (the condo was sold for $415,000) to return the money. In 2006, Yulia Fomina tried to win back the apartment bought to her by Buslaev by court action; however, after spending several years (the litigation ended in 2011) and around $100,000, she lost the case. The legal costs were covered by her new friend Oleg Lazanovich, an emigrant from Kyiv and the owner of MBT Wine & Spirit (liquor business), who lives in Miami in the same building at 16711 Collins Avenue.
In March 2006, Vladimir Malakhov bought a new condo in Trump Place in Miami at 18101 Collins Ave. The apartment is valued at $1.5 million today.
On March 3, 2010, Malakhov brought an action against the American attorney Michael Cohen laying an accusation that the check for $350,000 written by him on January 19, 1999 was not transferred to anyone, but remained deposited on Cohen’s account. Malakhov claimed back $350,000 plus interests and legal costs.
On April 12, 2010, Malakhov suddenly withdrew his suit without any explanations, thus putting an end to this intriguing detective story about $350,000 received by Trump’s personal attorney suspected of illegal connections with Russia.
More here. Has anyone heard from the African American community on this issue at all?
More here from CS Monitor.





 You think American universities are Marxist? Check out this professor. If you can stand it, check out the video below.
You think American universities are Marxist? Check out this professor. If you can stand it, check out the video below. In this photo released by the Syrian official news agency SANA, Syrian President Bashar al-Assad meets with Australian professor Tim Anderson and a delegation including academics, researchers and activists in Damascus in 2013.
In this photo released by the Syrian official news agency SANA, Syrian President Bashar al-Assad meets with Australian professor Tim Anderson and a delegation including academics, researchers and activists in Damascus in 2013.  Sydney University senior lecturer Tim Anderson (centre) believes Bashar al-Assad has been framed.
Sydney University senior lecturer Tim Anderson (centre) believes Bashar al-Assad has been framed. 
