In part from HuffPo:
WASHINGTON — The Obama administration has responded to a petition calling on the U.S. to resettle tens of thousands of Syrian refugees within its borders, inviting the man who started the petition to the White House for a meeting.
George Batah, 23, came from Syria in 2013 and now lives in Chicago. He said he started the petition in late August because he felt the United States has a moral obligation to continue being “the leader in refugee resettlement.”
His petition asked the White House to accept at least 65,000 Syrian refugees by 2016. The administration did not commit to that number in its response Thursday, instead reiterating that it intends to bring at least 10,000.
“Under President Obama, the U.S. is the world’s largest donor of humanitarian aid, having contributed $4 billion in aid to date to help meet urgent needs in the most effective way,” the administration wrote. “The President has also directed his Administration to scale up the number of Syrian refugees we will bring to the U.S. next year to at least 10,000.”
How the White House Got Silicon Valley to Take On the Refugee Crisis
After the president’s request, Silicon Valley code writers went to work at record pace.
White House and Silicon Valley Take On Syria Crisis
Bloomberg: Even Jason Goldman, a former senior technology executive at
companies including Twitter, Medium, and Google, was surprised by how quickly some of his former Silicon Valley colleagues were able to answer the call.
Goldman, now sitting in Washington as the first-ever White House chief digital officer, and his colleague Joshua Miller, a former Facebook employee overseeing the Obama administration’s digital products, had gone to work lining up allies for a push to aid the waves of Syrian refugees flooding out of the country a little over a week prior. Now they were staring at donation platforms, crafted from scratch, that were ready to roll out.
“That’s a pretty fast turnaround time to actually build and ship code out into the wild,” Goldman says.
“That’s a pretty fast turnaround time to actually build and ship code out into the wild.”
Jason Goldman, White House chief digital officer
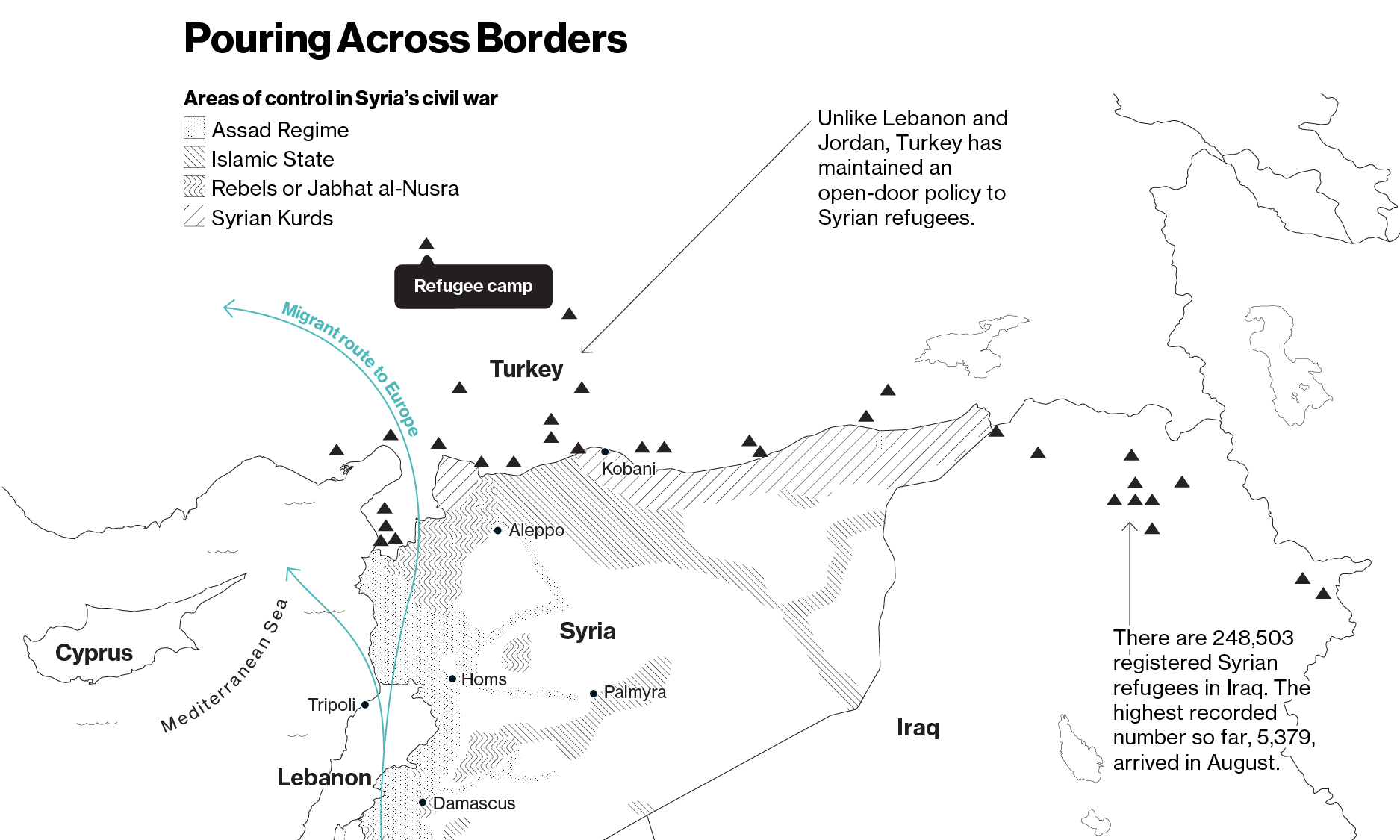
The response—and the equivalent of millions of dollars in donations that resulted—from Kickstarter, Twitter, Airbnb, and Instacart marked a new approach to address what many in the U.S. government view as an intractable crisis. Nearly 12 million Syrians have been displaced by the civil war raging in their country, according to the UN Refugee Agency. Thousands per day are flooding into European nations unequipped to handle the surge.
The White House has directed more than $4.5 billion to aid refugees, and pledged last month to allow and additional 10,000 into the U.S. next year. Still, the metastasizing crisis has up to this point far outweighed the global response. The U.N. Refugee Agency estimates the awareness level in the U.S. sits at 4 percent.
“We don’t have refugees in our backyard, we don’t have camps, we don’t have refugee camps on our soil so a lot of the American public doesn’t have a full understanding of what is going on,” says Jennifer Patterson, USA for UNHCR, the UN non-profit arm tasked with raising money and awareness for refugees. “The scope is really enormous right now.”
That was part of the calculation behind a few lines in President Barack Obama’s September speech to the United Nations General Assembly—a call not just to world leaders to address the crisis, but also private industry. Goldman and his team were looped into the call by National Security Council staff in the lead up to the remarks and went to work.
Within a week of Obama’s speech, Kickstarter had partnered with UNHCR to launch a first-of-its-kind non-profit campaign on the platform. Obama and Samantha Power, the U.S. ambassador to the UN, kicked in videos to help. More than $1 million was raised in less than 24 hours. Instacart linked up with UNHCR to create an option for its online shoppers to also purchase meals for refugee families. Airbnb pledged housing credits to aid workers in the region and matched any donations from its online community. Twitter launched its donation product early to ease the fundraising process on the platform for non-governmental organizations.
White House officials acknowledge that the start-up driven campaigns are far from the, or even a major piece of the, solution to the crisis. But along with driving donations and awareness, there are plans to make the idea a permanent model going forward. Other companies are preparing to launch similar initiatives, Patterson says.
“Really what we were doing here was just using the White House convening power to say, look, this is a real problem out in the world,” Goldman says. “Here’s how to think about it, here’s organizations you can work with, find the right fit for your product and you and your users and really step up and be involved.”


