Korean Central Television
A test-fire of new ground-to-ground medium long-range strategic ballistic rocket Hwasong-12 was successfully carried out on Sunday by scientists and technicians in the field of rocket research, who are bravely advancing toward a new goal to be proud of in the world, true to the far-sighted idea of Kim Jong Un, chairman of the Workers’ Party of Korea, chairman of the State Affairs Commission of the DPRK and supreme commander of the Korean People’s Army, for building a nuclear power.
Kim Jong Un guided the test-fire on the spot.
Looking at Hwasong-12, he expressed his satisfaction over the possession of another “Juche weapon”, a perfect weapon system congruous with the military strategic and tactical idea of the WPK and the demand of the present times.
The test-fire was conducted at the highest angle in consideration of the security of neighboring countries. The test-fire aimed at verifying the tactical and technological specifications of the newly-developed ballistic rocket capable of carrying a large-size heavy nuclear warhead.
According to the order of Kim Jong Un, the new rocket Hwasong-12 was launched at 04:58 on Sunday.
The rocket accurately hit the targeted open waters 787km away after flying to the maximum altitude of 2 111.5km along its planned flight orbit.
The test-fire proved to the full all the technical specifications of the rocket, which was newly designed in a Korean-style by defence scientists and technicians, like guidance and stabilization systems, structural system and pressurization, inspection and launching systems and reconfirmed the reliability of new rocket engine under the practical flight circumstances.
It also verified the homing feature of the warhead under the worst re-entry situation and accurate performance of detonation system.
Kim Jong Un hugged officials in the field of rocket research, saying that they worked hard to achieve a great thing. And he had a picture taken with officials, scientists and technicians who took part in the test-fire.
Highly appreciating again their devotion for manufacturing the Korean-style medium long-range strategic ballistic rocket, he gave a special thanks to them on behalf of himself.
He said with confidence that the successful test-fire of Hwasong-12, a demonstration of high-level defence science and technology of the DPRK, is of great and special significance for securing peace and stability in the Korean peninsula and the region and is the greatest victory of the Korean people.
He declared that the DPRK is a nuclear power worthy of the name whether someone recognizes it or not. He stressed the DPRK will keep strict control over those engaging themselves in nuclear blackmail with its nuclear deterrence which has been unimaginably and rapidly developed.
The U.S. massively brought nuclear strategic assets to the vicinity of the Korean peninsula to threaten and blackmail the DPRK, but the coward American-style fanfaronade militarily browbeating only weak countries and nations which have no nukes can never work on the DPRK and is highly ridiculous, he said, stressing that if the U.S. dares opt for a military provocation against the DPRK, we are ready to counter it.
The most perfect weapon systems in the world will never become the eternal exclusive property of the U.S., he said, expressing the belief that the day when the DPRK uses the similar retaliatory means will come. He continued that on this occasion, the U.S. had better see clearly whether the ballistic rockets of the DPRK pose actual threat to it or not.
If the U.S. awkwardly attempts to provoke the DPRK, it will not escape from the biggest disaster in the history, he said, strongly warning the U.S. not to disregard or misjudge the reality that its mainland and Pacific operation region are in the DPRK’s sighting range for strike and that it has all powerful means for retaliatory strike.
He gave the scientists and technicians in the field of rocket research the order to continuously develop more precise and diversified nukes and nuclear striking means, not content with the successes, and make preparations for more tests till the U.S. and its vassal forces make a proper choice with reason.
*** 
ATN: North Korea launched a missile in a test early in the morning of May 14, North Korean time. If the information that has been reported about the test are correct, the missile has considerably longer range than its current missiles.
Reports from Japan say that the missile fell into the Sea of Japan after traveling about 700 km (430 miles), after flying for about 30 minutes.
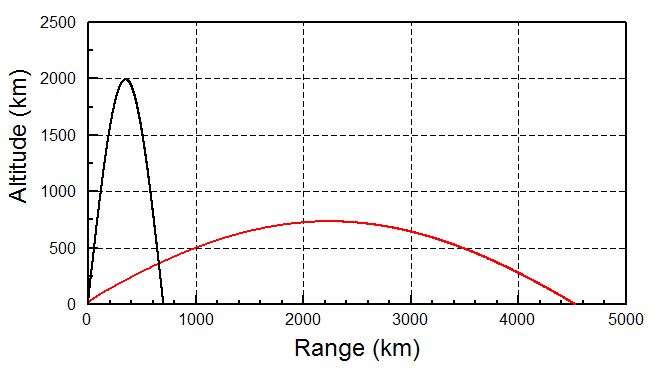
A missile with a range of 1,000 km (620 miles), such as the extended-range Scud, or Scud-ER, would only have a flight time of about 12 minutes if flown on a slightly lofted trajectory that traveled 700 km.
A 30-minute flight time would instead require a missile that was highly lofted, reaching an apogee of about 2,000 km (1,240 miles) while splashing down at a range of 700 km. If that same missile was flown on a standard trajectory, it would have a maximum range of about 4,500 km (2,800 miles).
New press reports are in fact giving a 2,000 km apogee for the test.
This range is considerably longer than the estimated range of the Musudan missile, which showed a range of about 3,000 km in a test last year. Guam is 3,400 km from North Korea. Reaching the US West Coast would require a missile with a range of more than 8,000 km. Hawaii is roughly 7,000 km from North Korea.
This missile may have been the new mobile missile seen in North Korea’s April 15 parade (Fig. 2). It appears to be a two-stage liquid-fueled missile.
Fig. 2 (Source: KCNA)
Fig. 1 The black curve is the lofted trajectory flown on the test. The red curve is the same missile flown on a normal (MET) trajectory.


 Courtesy:
Courtesy: 


