But Obama and Kerry told us they could….is there more than one version of the JCOA?
As the Trump administration calls for stricter monitoring of the Iranian nuclear agreement, officials in Iran insist they are complying with its terms and will not allow international inspectors into military sites.
Iran, which agreed in 2015 to grant inspectors broad access to nuclear-related facilities in exchange for the removal of severe economic sanctions, accuses President Trump of trying to sabotage what he has called the United States’ “worst deal.”
Trump has argued that Iran is violating the agreement struck under President Obama, although he has offered no evidence to support his claim and his administration has twice certified to Congress that Iran is in compliance.
But Trump administration officials looking for a way to increase pressure on Iran have begun to zero in on military facilities that they say could be used for nuclear-related activities barred under the agreement.
The IAEA, in its most recent report in June, said Iran was meeting its obligations under the pact. Experts say inspectors rely on intelligence reports and other information to determine whether sites they have not visited are being used for potentially illicit purposes. More here.
*** What about those snapback sanctions Obama told us about? The NYT’s wrote that the snapback sanctions were easy. What is the response of those American lobby groups that Obama hired on behalf of the Iran deal.

***
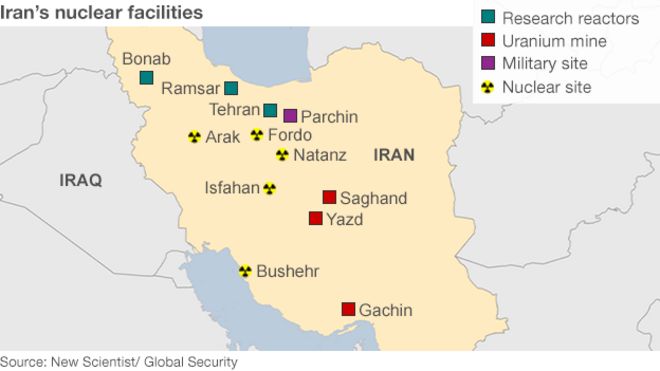 photo and more on each location courtesy of BBC
photo and more on each location courtesy of BBC
Inspectors with the International Atomic Energy Agency, the United Nations organization tasked with monitoring Iran’s nuclear facilities, have not requested access to military sites since the agreement went into effect, according to experts monitoring the process.
The Russian Deputy Foreign Minister refers to Section T – while ignoring that, as the Former Deputy Director General of the IAEA, Olli Heinonen notes, the IAEA has the authority under UN Security Council resolution 2231 to request access to sites and equipment associated with Section T.
This resolution “requests the Director General of the IAEA
to undertake the necessary verification and monitoring of Iran’s
nuclear-related commitments for the full duration of those commitments under
the JCPOA.” In addition, the resolution states: “The International Atomic
Energy Agency will be requested to monitor and verify the voluntary
nuclear-related measures as detailed in this JCPOA.”
An excerpt from his article follows the TASS item.]Fuss around IAEA inspections of Iranian military facilities contrived –
Russian diplomat
If the other participants are eager to discuss the issue, Moscow “will be
ready to discuss it” presenting its stance, Sergei Ryabkov said
Russian Politics & Diplomacy
October 22, 0:10 UTC+3
http://tass.com/politics/971962
MOSCOW, October 22. /TASS/. Certain countries substitute notions in talks on
expanding inspections of the International Atomic Energy Agency (IAEA) at
the Iranian military facilities creating contrived fuss around the issue.
However, Russia says that the IAEA is not authorized to carry out such
inspections, Russian Deputy Foreign Minister Sergei Ryabkov told TASS on
Saturday.“I would like to say absolutely clear and directly that acquiring some false
topicality the theme of the IAEA work on Section T (about Iran’s military
facilities – TASS) of the Joint Comprehensive Plan of Action (JCPOA) over
the Iran nuclear program has no topicality for us although it is a talking
point now,” he said.In particular, Moscow says that the IAEA “has not been authorized to carry
out such inspections and cannot be tasked because Section T highlights the
issues out of the agency’s competence,” Ryabkov said.“Nevertheless, we can hear another thing. As in the issue of the Iran
missile program, some of our counterparts prefer to call black white and
vice versa,” the high-ranking diplomat said. “We cannot get them to
understand this evident logic and obvious truth.”“Since they are insisting, we say if you cannot do without discussions on
the theme, it should be raised at the Joint Commission when the next session
is convened,” Ryabkov said.If the other participants are eager to discuss the issue, Moscow “will be
ready to discuss it” presenting its stance, he said.JPCOA and US
On July 14, 2015, Iran and six international mediators (the United Kingdom,
Germany, China, Russia, the United States, and France) reached a deal on
Iran’s nuclear program. On January 16, 2016, the parties to the deal
announced beginning of its implementation. Under the deal, Iran undertakes
to curb its nuclear activities and place them under total control of the
International Atomic Energy Agency (IAEA) in exchange of abandonment of the
sanctions imposed previously by the United Nations Security Council, the
European Union and the United States over its nuclear program.Last week, US President Donald Trump announced Washington’s new strategy
against Teheran. Thus, it says that the United States will seek to offset
Iran’s destabilizing influence and will call on the international community
to get consolidated for exerting pressure on Iran’s Islamic Revolutionary
Guard (IRGC, Iran’s most powerful security and military organization). Apart
from that, the US blacklisted the IRGC as an organization supporting
terrorism. Donald Trump refused to confirm Iran observed the agreement on
the nuclear program and promised changes to the document.
========================
Verifying Section T of the Iran Nuclear Deal: Iranian Military Site Access
Essential to JCPOA Section T Verification
by David Albright and Olli Heinonen
August 31, 2017
http://isis-online.org/isis-reports/detail/verifying-section-t-of-the-iran-nuclear-deal
…
The IAEA has the authority under UN Security Council resolution 2231 to
request access to sites and equipment associated with Section T. This
resolution “requests the Director General of the IAEA to undertake the
necessary verification and monitoring of Iran’s nuclear-related commitments
for the full duration of those commitments under the JCPOA.” In addition,
the resolution states: “The International Atomic Energy Agency will be
requested to monitor and verify the voluntary nuclear-related measures as
detailed in this JCPOA.”
…
Recommendations
The United States should assemble, if it has not already done so, its own
lists of equipment and locations relevant to Section T. It should also
prepare lists suitable for sharing with the IAEA or Joint Commission.
Similarly, U.S. allies should share relevant information with the IAEA. If
it has not done so, the IAEA should create a baseline of Section T
activities and equipment.The United States and its allies should press the IAEA to develop and
establish an effective, credible verification regime under Section T that
includes requests to access military sites. The United States and the EU3
should also raise Section T and the likely need for approvals of such
equipment and activities by Iran at the next Joint Commission meeting.
Toward that goal, Iran should declare to the IAEA its sites and equipment
subject to Section T verification and approvals.
========
Olli Heinonen is Former Deputy Director General of the IAEA and head of its
Department of Safeguards. He is a Senior Advisor on Science and
Nonproliferation at the Foundation for Defense of Democracies.







 Mikerin
Mikerin

