Graphic on the estimated global atomic weapons stockpile
After almost five years of difficult negotiations, Russia and China moved to a new level of arms trade in 2015. Russia finally agreed to sell China 24 Sukhoi‑35 (Su-35) combat aircraft and four S-400 SAM systems for approximately USD $7 billion. These are currently among the most advanced weapons Russia produces. This agreement marked a turning point. It was the first significant sale of Russian major weapons to China since the mid-2000s, representing a sizeable addition to Russia’s total annual value of arms exports, which has hovered between USD $13.5 billion and USD $15 billion in recent years.
The agreement could herald a new phase of large sales of Russia’s most sophisticated arms to China. However, it could also be viewed as a last chance for Russia to gain some income from arms sales to China before the latter becomes self-sufficient. The first scenario would fit the picture of warming Russian–Chinese relations, following the crisis in Ukraine. The second scenario is more tightly bound to Russian financial hardships and the difficulties in its arms industry since 2015. This sale could well be the last chance for Russia to engage in a major sale of military equipment to China. At the same time as the Su-35 and S-400 are due for delivery, China will be introducing its own more advanced Jian-20 (J-20) combat aircraft, as well as its own advanced jet engines, large transport aircraft, helicopters and long-range SAM systems—many of which are on a par with or even better than Russian systems.
When it comes to the arms trade, China has not only learned from Russia, but succeeded in challenging it. Given its financial and defence industrial base, China is likely to have more chances to develop new military technologies than Russia. China’s electronics, composites, advanced materials and shipbuilding industries are all more advanced than those in Russia. The size of the Chinese economy means that it has many more resources and much more manpower to invest in research and development. Thus, it is more than likely that China’s military technology will surpass that of Russia on all levels. More detail and history here.
SEOUL, July 7 (Yonhap) — South Korean President Moon Jae-in sought to rally support from other global leaders Friday in condemning North Korea for its recent missile provocation and ridding the communist state of its nuclear ambitions, his presidential office Cheong Wa Dae said.
“It is not a scheduled topic for discussion, but as president of the Republic of Korea I cannot but talk to you about another serious challenge that urgently requires the joint interest and action of the G20,” the South Korean president said in the Leaders’ Retreat on the sidelines of the Group of 20 summit held in Hamburg, Germany, referring to South Korea by its official name.
“And that is North Korea’s nuclear and missile provocations,” he added, according to a script of his remarks released by Cheong Wa Dae.
Moon’s remarks came after the communist North launched what it claimed to be its first intercontinental ballistic missile (ICBM) earlier in the week, prompting fresh condemnations from Seoul and its allies.
In a three-way meeting with U.S. President Donald Trump and Japanese Prime Minister Shinzo Abe in Hamburg on Thursday, the South Korean leader was joined by his U.S. and Japanese counterparts in calling for stronger sanctions by the international community to bring North Korea to a dialogue table to discuss its denuclearization.
“To resolve the North Korean nuclear issue that has become a global threat, the international community will have to put enhanced pressure on North Korea,” partly by issuing a new U.N. Security Council resolution, Moon told other G20 leaders at their retreat.
“By doing so, we must make the North Korean regime realize that its nuclear arms and missiles will never guarantee its existence and come to the dialogue table,” he added.
The South Korean president also rallied support for what he called the “clear determination” of G20 leaders to jointly address the issue at their gathering this week, apparently seeking a joint reaction or a statement from the global leaders condemning the North’s missile provocations.
“I ask for you, G20 leaders’ full interest and support,” he said.
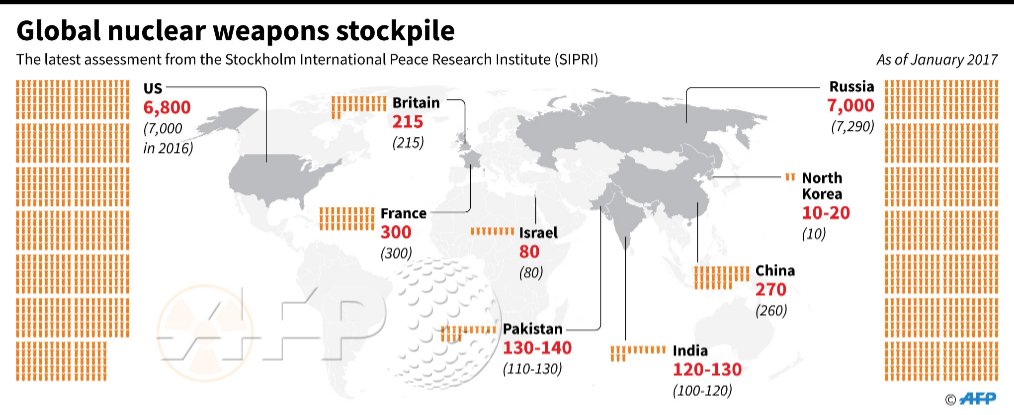
Kim Jong Un’s Big Nuclear Push Is Closing In on America
Bloomberg: Kim Jong Un has sped up North Korea’s nuclear program since he took power in late 2011, testing more powerful weapons and developing longer-range missiles to carry them. On July 4, North Korea said it had successfully test-fired an intercontinental ballistic missile called the Hwasong-14, a claim that brings the isolated state closer to its aim of building a device capable of hitting the U.S. mainland with a nuclear warhead. The United Nations Security Council will hold an emergency meeting later Wednesday after the U.S. confirmed North Korea’s rocket launch was its first intercontinental ballistic missile.
Still, the launch risks a serious escalation with North Korea’s neighbors and the U.S. over its weapons program. The regime is thought to possess rockets that can hit South Korea and Japan with as many as 20 atomic bombs. More here with graphics.
***
Meanwhile:
According to Reuters, Moscow said it believes North Korea fired an intermediate-range ballistic missile on Tuesday.
The Trump administration has confirmed it was, in fact, a longer-range intercontinental missile that has the potential to reach the U.S.
“Therefore we are not in a position to agree to this classification on behalf of the whole council since there is no consensus on this issue,” the email said.
U.S. Ambassador to the United Nations Nikki Haley criticized Russia’s reluctance to recognize North Korea launched an intercontinental missile capable of reaching the U.S. according to experts, a threshold North Korea has not reached before.
“If you need any sort of intelligence to let you know that the rest of the world sees this as an ICBM, I’m happy to provide it,” she told the Security Council on Wednesday.
Security Council resolutions have to be agreed to by all 15 members.
Reuters reported it’s uncertain if the U.S. will negotiate with Russia to adjust the resolution.


 Starsalliance
Starsalliance