Go here for more information on malware affections.
Further, US-CERT, by DHS has this information.
Older machines running XP do not appear to be affected. Meanwhile, about a month ago:
Microsoft responds to NSA’s Windows exploits, urges customers to upgrade to supported versions
Remember, this NSA vault toolkit was stolen, leaked and published by WikiLeaks, Julian Assange. In some cases, it could be a deadly threat to life considering the intrusions into hospitals. The other blame goes to the Russian cyber gang, ShadowBrokers.
Russian-linked cyber gang Shadow Brokers blamed for NHS computer hack
Courtesy: TelegraphUK: Ransom message found on NHS computers
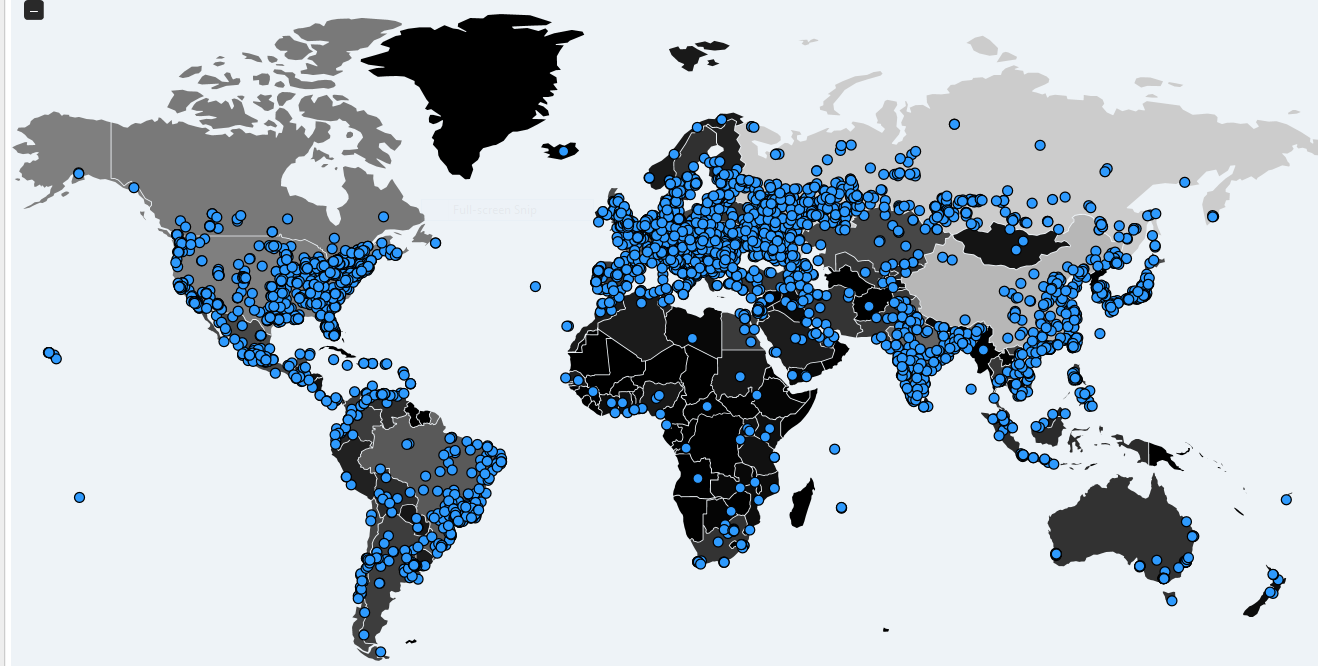
CyberScoop: Large organizations on every continent are being hit by a global campaign of ransomware attacks on Friday, unfortunately, average ransomware demand has increased significantly. Machines are being infected using exploits developed by the U.S. National Security Agency and leaked by the group known as ShadowBrokers, according to authorities.
More than 57,000 detections in 74 countries have been recorded. Russia appears to be the most infected country by far, according to cybersecurity firms Kaspersky and Avast.
The “number [is] still growing fast,” according to Costin Raiu, Kaspersky’s director of research.
Hospitals across England were forced to divert emergency patients, according to the National Health Service. Other hospitals are asking patients to avoid coming in except for emergencies, news reports said.
In Spain, victims including the telecommunications company Telefónica told employees to shut down machines and networks in an effort to stop the spread of the malware. Other victims include Gas Natural and Iberdrola, an electric utility firm.
The ransomware campaign is caused by “exploiting the vulnerability described in bulletin MS17-010 using EternalBlue / DoublePulsar,”Spain’s Computer Emergency Readiness Team explained on Friday. “Infection of a single computer can end up compromising the entire corporate network.”
EternalBlue and DoublePulsar are code names for NSA hacking tools used to infect thousands of machines around the world since the NSA tools leaked in April.
That description from Spanish authorities and the work of several researchers point directly to NSA tools hacked and leaked by ShadowBrokers. The patch that Microsoft published in March assigned the designation MS17-010 to the vulnerability.
A widespread “bloodbath” from criminals has been expected by experts since the leak.
The ransomware “infects the machine by encrypting all its files and, using a remote command execution vulnerability through SMB, is distributed to other Windows machines on the same network. Microsoft published the vulnerability on March 14 in its bulletin and a few days ago a proof of concept was released that seems to have been the trigger of the campaign.” SMB is Microsoft’s Server Message Block protocol for network file sharing.
The attacks in different countries have been linked to the same group, according to the Financial Times.
The U.S. Department of Homeland Security is “coordinating with our international cyber partners” in Europe and Asia, a spokesperson told CyberScoop. “The Department of Homeland Security stands ready to support any international or domestic partner’s request for assistance. We routinely provide cybersecurity assistance upon request, including technical analysis and support. Information shared with DHS as part of these efforts, including whether a request has been made, is confidential.”
Security researcher Kevin Beaumont advised patching machines immediately:
** Kevin Beaumont?Verified account @GossiTheDog5 hours ago
Confirmed – wcry ransomware spreading across Europe uses EternalBlue/MS17-010/SMB. PATCH NOW EVERYWHERE.
Spanish authorities confirmed the ransomware is a version of WannaCry (also known as WannaCrypt0r), according to the National Cryptology Center. In Spain, the newspaper El Mundo is reporting that “early indications point to an attack originating in China.”
“Given the rapid, prolific distribution of this ransomware, we consider this activity poses high risks that all organizations using potentially vulnerable Windows machines should address,” a spokesperson from the cybersecurity firm FireEye told CyberScoop. “Organizations seeking to take risk management steps related to this campaign can implement patching for the MS17-010 Microsoft Security bulletin and leverage the indicators of compromise identified as associated with this activity.”
FireEye has yet to see a U.S.-based company be affected by the ransomware worm.
An estimated 25 health facilities in London and across England have been hit, according to the NHS. St Bartholomew’s Hospital in London, one of the victims, received warnings earlier this year that computers using Windows XP were vulnerable, reported the technology news site the Inquirer. Increasingly, some infected hospitals are not accepting phone calls or internet communications. The Derbyshire Community Health Services NHS Trust has reportedly shut down all of its IT systems.
“At this stage we do not have any evidence that patient data has been accessed,” an NHS statement said. “We will continue to work with affected organizations to confirm this.”
East and North Hertfordshire NHS trust, a hospital just north of London, publicly acknowledged “a major IT problem” that is “believed to be caused by a cyber attack.”
“The trust is postponing all non-urgent activity for today and is asking people not to come to A&E – please ring NHS111 for urgent medical advice or 999 if it is a life-threatening emergency,” according to a statement. “To ensure that all back-up processes and procedures were put in place quickly, the trust declared a major internal incident to make sure that patients already in the trust’s hospitals continued to receive the care they need.”
News of the English hospitals being hit with ransomware spread quickly among doctors and hospital employees, including in a widely shared message from an English doctor now making the rounds on social media.
**
If.ra? @asystoly6 hours ago Why would you cyber attack a hospital and hold it for ransom? The state of the world
“So our hospital is down,” the doctor wrote. “We got a message saying your computers are now under their control and pay a certain amount of money. And now everything is gone.”