Sheesh…..typical for a government contractor and in Iraq.
U.S. Firm in Iraq Overlooks Smuggling, Security for F-16s
WASHINGTON (AP) — The two American investigators felt a sense of foreboding that Sunday as they headed to an emergency meeting with their boss on the Iraqi air base. But they didn’t expect to be surrounded by armed guards, disarmed, detained against their will — and fired without explanation.
It was March 12 — less than two months ago. Robert Cole and Kristie King were in Iraq working as investigators for Sallyport Global, a U.S. company that was paid nearly $700 million in federal contracts to secure Balad Air Base, home to a squadron of F-16 fighter jets as part of the U.S.-led coalition to annihilate the Islamic State.
** Click here for video
Cole and King had spent more than a year together in Iraq investigating all manner of misconduct at Balad and beyond.

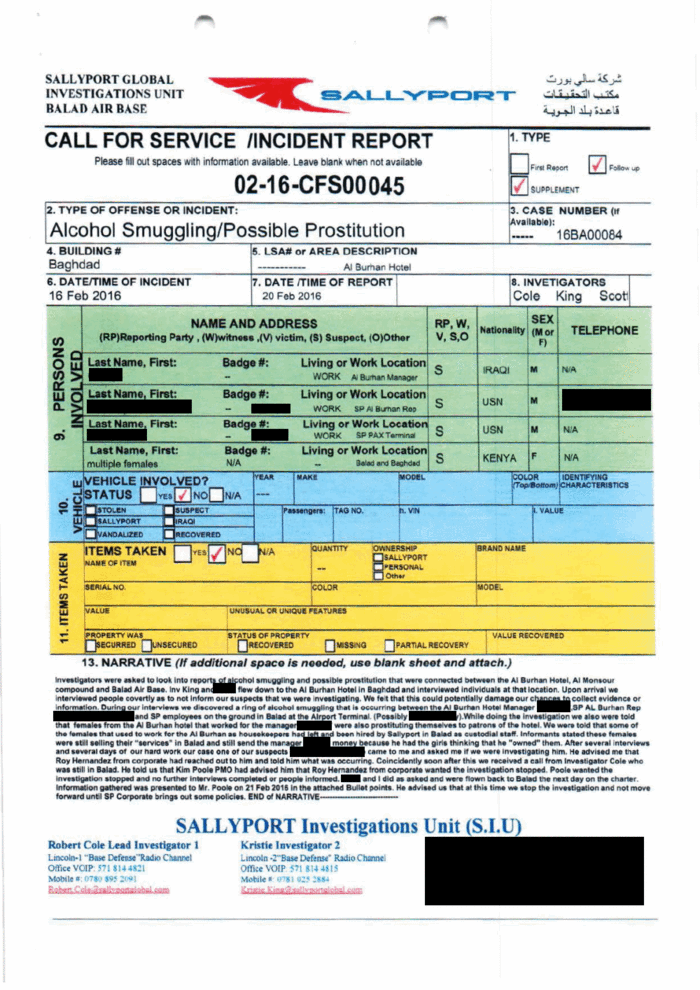
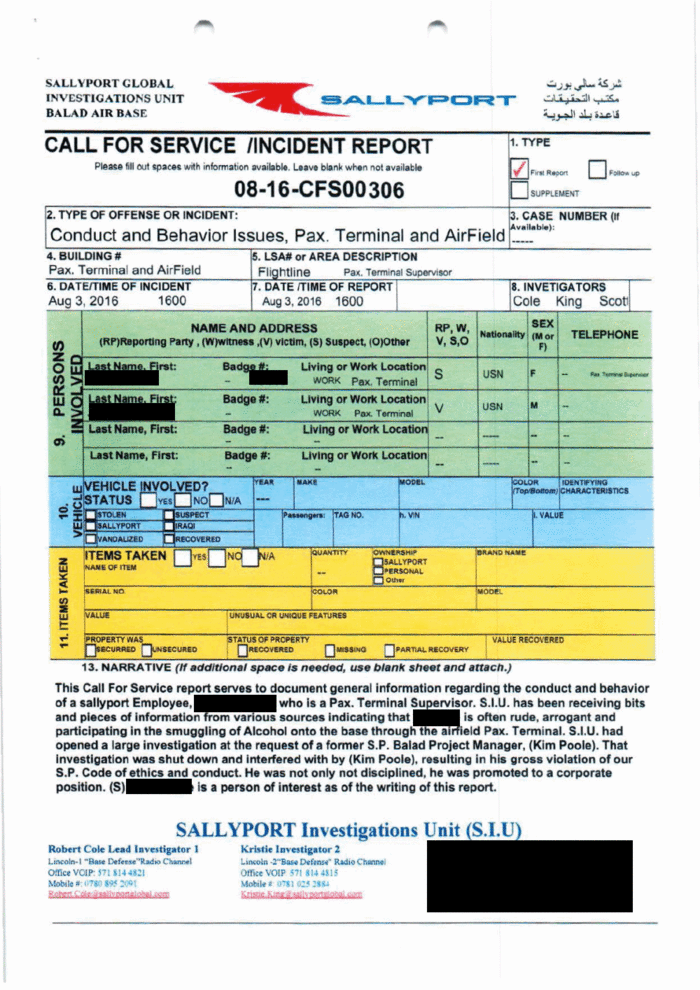
They’d uncovered evidence that Sallyport employees were involved in sex trafficking , they said. Staff on base routinely flew in smuggled alcohol in such high volumes that a plane once seesawed on the tarmac under the weight. Rogue militia stole enormous generators off the base using flatbed trucks and a 60-foot crane, driving past Sallyport security guards.
Managers repeatedly shut down Cole and King’s investigations and failed to report their findings to the U.S. government that was footing the bill, the investigators said.
Right before they were fired, Cole and King had opened an investigation into allegations of timesheet fraud among Sallyport employees. In a call with Sallyport lawyers, they said, they were advised to keep two sets of books about potential crimes and contract violations.
“One for the government to see and one for the government not to see,” King told The Associated Press.
The company said that the investigators misinterpreted the instructions.
In a statement to the AP, Sallyport said it follows all contracting rules at the base, home to the F-16s that are a key to the fight against the Islamic State.
“Sallyport has a strong record of providing security and life support services in challenging war zones like Iraq and plays a major but unheralded role in the war against ISIS,” Chief Operating Officer Matt Stuckart wrote. “The company takes any suggestion of wrongdoing at Balad very seriously.”
More than 150 documents obtained by AP, as well as interviews with more than a half-dozen former or current Sallyport employees, show how a contractor ran amok after being hired for lucrative and essential combat support operations. The investigators and other witnesses describe grave security breaches and illegal schemes that went unreported until the government asked about them.
The point behind requiring contractors to employ their own investigators was to limit the waste and corruption that has marred federal security contracting going back to the aftermath of the Sept. 11 attacks.
The Pentagon’s own auditors, who were frequently on the base 50 miles north of Baghdad, were not told of the serious problems until early this year, a potential violation of law. The Pentagon auditors’ reports, obtained by the AP, detail dozens of more minor infractions. That gap illustrates the limits of U.S. oversight for billions of dollars in contracts run by companies that have cashed in on the fight to protect Americans from extremism.
The Defense Department declined to comment.
The morning of March 12, King had gone to church and was still carrying her Bible when she and Cole walked into the office foyer for the meeting with the boss. To their astonishment, they were immediately surrounded by armed security guards and forced to turn over the 9 mm pistols they both routinely carried on the job.
The boss, David Saffold, informed them they were being fired but wouldn’t say why.
“We knew too much,” King told AP in an interview at her home in Amarillo, Texas. “They want to cover it up and move on because it’s a huge amount of money.”
BODYGUARD OR TERRORIST?
In 2004, Rob Cole was a retired California police officer and licensed private investigator when he decided to go to Iraq for a series of contracting jobs. Like many U.S. contractors working in hazardous regions, he went because the work paid a lot more than he could make back home.
Americans have been at Balad on and off since 2003. Sallyport’s parent company, Michael Baker International, announced in 2014 its subsidiaries had been awarded $838 million for work on the base.
Cole’s first job at Balad was cut short in June 2014, a month after he arrived, when the Islamic State group began sweeping across Iraq and Syria. The extremists ultimately made it to the gates of Balad, which was evacuated.
When the Americans went back, they found a looted base largely under the control of Iranian-backed Shiite militias that were supporting the Iraqi government, according to former employees. A former senior manager told the AP that Sallyport reached an understanding with the militias that they would not enter the flight and residential areas. He declined to be named because he wasn’t authorized to discuss the matter and didn’t want to be blacklisted from future jobs.
Cole, now 62, returned to Balad in May 2015, as Sallyport was preparing for the arrival of American F-16s sold to the Iraqi government. Sallyport’s mission, along with its parent company, was to keep the base operating smoothly, train the Iraqis, and most importantly maintain security on the base, where thousands of Iraqis and hundreds of contractors work.
The federal contract required investigations into potential crimes and violations involving the company’s work at Balad. That was Cole and King’s assignment.
“They wanted someone to be competent enough to process an investigation, if there was a crime, or if someone turned up dead,” King said. “The way it was put to me: If someone turned up with a knife in their back, who are you going to call?”
From the start, it was clear that much was awry on the base. Despite the urgency of fighting IS, the delivery of the F-16s had been delayed by months amid security concerns. It would be catastrophic if IS seized the base and its multimillion-dollar jets.
On July 13, 2015, four F-16s flew in from Arizona, the first of 36 fighter jets that the U.S. planned to deliver.
Brett McGurk, then the U.S. deputy envoy for the international coalition against IS, hailed the arrival in a tweet.
“After years of preparation & training in the U.S., Iraqi pilots today landed the 1st squadron of Iraqi F16s in #Iraq,” he wrote.
The first security breach came in less than 24 hours: A long black skid mark on the tarmac was reported. It stopped about 45 yards from the nose of one of the fighter jets. A truck had plowed through a rope barrier in the “no-go” zone, where lethal force is authorized to protect the planes. For more than 10 minutes, no one even responded as the vehicle drove away, according to reports citing surveillance video.
That turned out not to be a terrorist. But Cole says the out-of-control truck was a harbinger. He noted the lax protection for the F-16s in his report and forwarded it to the chief of security, Steve Asher. Under the requirements of the contract, Cole’s report should have then made its way to the Pentagon. But he says Asher kept a lid on the incident.
Three months later, in October 2015, Cole reported another security breach, the theft of a Toyota SUV that Sallyport had assigned to bodyguards to drive VIPs around the base. Cole eventually uncovered a plot by three Iraqi Sallyport staff working with a dangerous Iran-backed militia, known as Kataib Imam Ali.
The Shiite militia was an ongoing headache, politically connected and operating outside the law, with sidelines in theft and gunrunning. It has ties to the leader of the umbrella militia Popular Mobilization Forces, which is on the U.S. list of designated terrorists.
To Cole’s astonishment, the prime suspect threatened to join the militia during his interrogation. He was a Sallyport bodyguard. In fact, the investigators later found a photo of him on his Facebook page, dressed in black militia garb and a patch indicating his allegiance to the group.
He is “viewed by the Investigations Unit as a hard-core recruit to become a terrorist who poses a serious threat to all personnel on this base,” Cole wrote in another report.
The Toyota was recovered within a few days, but Cole was ordered off the case. In an interview with AP, the former senior manager defended the company’s order, saying negotiations with the militias were highly sensitive and had to be handled with Iraqi cooperation. Still, the suspect was supposed to be banned from the base, and Cole later saw the man walking around freely.
GUMMY BEARS SOAKED IN VODKA
The longer Cole was on the base, the more he suspected that management was turning a blind eye to criminal activity.
On the books, Balad is a dry base, where alcohol is restricted. But in reality the booze was everywhere and everyone knew it. Finding out how it got there led to more troubling questions.
A Sallyport employee who worked in the air terminal reported in late 2015 that co-workers were involved in a smuggling scheme. They were bringing in cases and cases of water bottles filled with liquor that they’d sneaked onto planes flying in from Baghdad.
According to investigative documents and people who watched the smuggling in action, three empty suitcases would routinely be loaded onto a flight to Baghdad. Each time, the bags came back with plastic water bottles filled with liquor. When they were unloaded, the bags were not searched but taken directly outside to be picked up — a serious security risk in a war zone.
“You could be putting a bomb in there,” said one former employee who witnessed the smuggling. “You’ve got people just going rogue.” He spoke only on condition of anonymity because he didn’t want to imperil his new job with a different overseas contractor.
Steve Anderson, who worked on flight logistics, says he was pressured to sign off on faked flight manifests that omitted passenger names and falsified the weight of cargo to cover for the alcohol smuggling and other infractions — a violation of international flight regulations. The planes were getting so weighed down he was worried about flight safety.
“They were playing Russian roulette with the passengers’ lives — including mine,” Anderson said.



 The RegisterUK
The RegisterUK


 NBCBoston
NBCBoston